In 2022, 83% of organizations experienced at least one data breach. These statistics published by IBM in the Cost of Data Breach Report once again prove that business security is a relative term. It is no longer a question of whether you will be hacked but a question of when.
The average cost of a data breach exceeds $3.8M.
Find business vulnerabilities and how they may be exploited before criminals do.
The truth is that many of those breaches could have been prevented. Professional penetration testing services are the most effective way to do that, as they allow you to discover gaps before cybercriminals exploit them. So, we start a series of articles focused on pentests to tell you more about types of penetration testing, specifics, and benefits to your business.
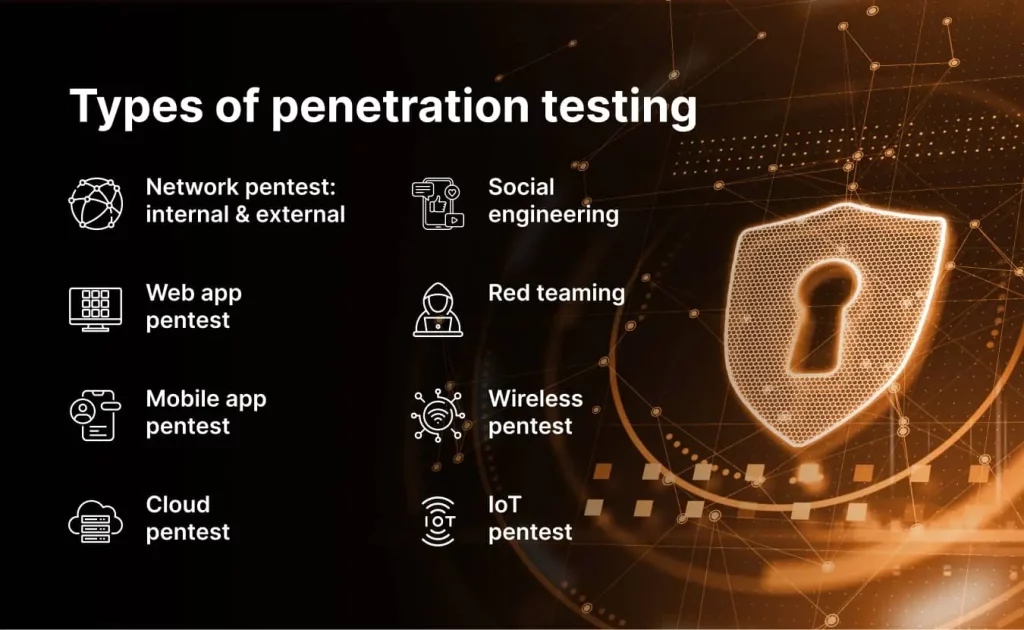
Network penetration testing will open the series. We will start the article with the basics, proceed with pentest types, and finish with tips on choosing a good network provider. Are you with us? Keep reading.
What is network penetration testing?
Network penetration testing is a proactive cybersecurity assessment procedure. It involves engaging authorized experts to simulate cyberattacks and detect vulnerabilities within your computer network or system.
The primary objective is to reveal security weaknesses and flaws before malicious individuals can exploit them. Penetration testers adhere to a structured methodology and create comprehensive reports that often include remediation tips. This practice is vital for strengthening network security and safeguarding digital assets.
Why network security is important for modern businesses
As we’ve answered the common question “what is penetration testing in network security”, let’s see why it’s critical for and what benefits it has to offer.
Nowadays, organizations increasingly rely on computer networks to conduct their operations, the need to safeguard sensitive data and maintain the integrity of systems has never been more crucial. Network security serves as the first line of defense against multiple cyber threats, ranging from data breaches to malicious attacks.
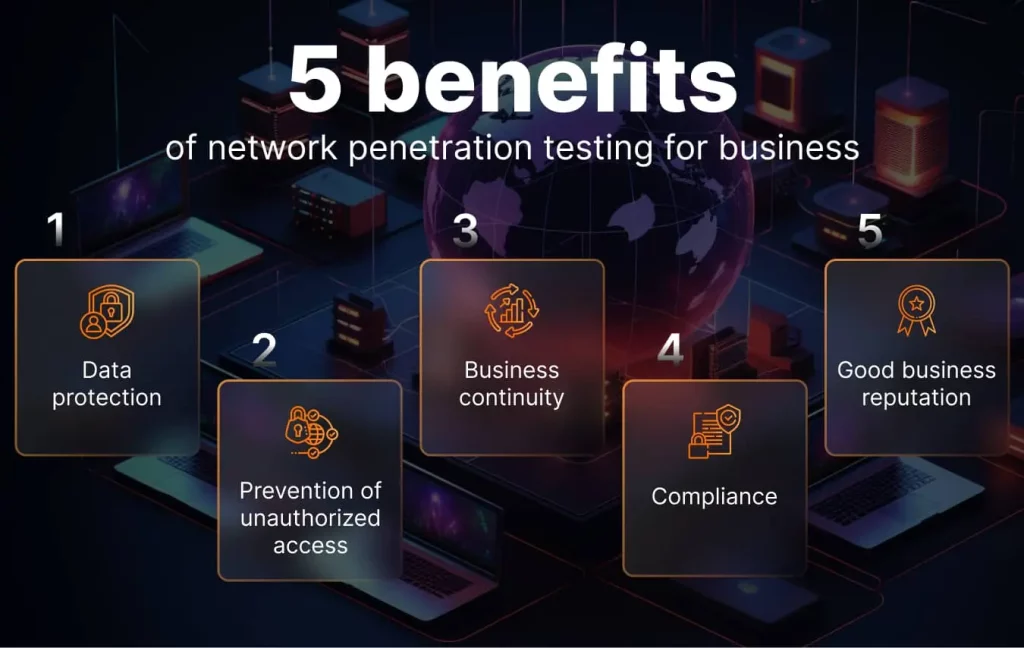
Based on our experience, below we list five key points emphasizing the importance of network security in modern business environments. Moreover, they will show how network security helps companies protect valuable data, prevent unauthorized access, ensure business continuity, comply with legal requirements, and maintain trust and reputation.
- Data protection. Network security is crucial for sensitive data protection. It ensures that confidential information, such as customer data, financial records, and intellectual property, remains protected from unauthorized access or theft. This point is essential for maintaining the trust and loyalty of customers and business partners.
- Preventing unauthorized access. Network security measures, including firewalls, authentication protocols, and access controls, prevent unauthorized users from infiltrating a network. By implementing strong authentication mechanisms and strict access policies, organizations ensure that only authorized personnel have access to critical resources.
- Business continuity. Network security helps prevent downtime and service interruptions caused by cyberattacks or malware infections. By mitigating the risk of disruptions, organizations can maintain their operations and minimize financial losses.
- Compliance and legal requirements. Many industries have strict regulatory requirements related to data security and privacy. Network security measures help organizations comply with these regulations, avoiding legal issues and potential fines. Compliance also demonstrates a commitment to protecting customer information.
- Reputation and customer trust. A network security breach can result in a tarnished reputation and eroded customer trust. Customers expect their data to be handled responsibly, and a security breach can lead to loss of confidence. Maintaining strong network security safeguards an organization’s reputation and customer relationships.
Top 3 objectives of network penetration testing
In general, there are dozens of reasons to conduct network penetration testing and check your preparedness for the ever-evolving threat landscape. But we want to highlight the top three goals of network pentest and they are the following:
- Vulnerability identification: The primary goal of network penetration testing is to identify vulnerabilities within a company’s network infrastructure. This includes identifying weaknesses in network configurations, software, and hardware that could potentially be exploited by malicious actors. By uncovering these vulnerabilities, organizations can take proactive steps to address and remediate them before they are exploited by cybercriminals.
- Security control evaluation: Network penetration testing assesses the effectiveness of existing security controls and measures in place. It helps organizations determine whether their firewalls, intrusion detection systems, access controls, and other security mechanisms can withstand real-world attacks. This evaluation provides valuable insights into areas where security controls may need improvement or adjustment.
- Risk assessment and prioritization: Another key objective is to assess the overall risk posture of the network. Penetration testers assign risk levels to identified vulnerabilities based on their potential impact and likelihood of exploitation. This assessment enables organizations to prioritize remediation efforts and focus on addressing the most critical vulnerabilities first. By effectively prioritizing vulnerabilities, organizations can allocate resources more efficiently to enhance their overall security posture.
Types of network penetration testing
As we’ve already covered what network pentest is and why it is important, let’s move on to discuss its main types and specifics.
Network penetration testing can take various forms, depending on the scope and purpose of the assessment. The most popular types are internal and external penetration tests. In this article, we will briefly cover the differences between these two options. But we suggest reading a detailed comparison of internal vs external penetration testing if you want to know all the nuances.
Currently, many executives find it challenging to distinguish between an internal and external penetration test and often struggle with deciding which one to opt for. Both follow a structured process, ensuring a comprehensive evaluation of your network’s security posture. These processes encompass a series of steps, from the initial pre-engagement phase to the final reporting and remediation stage. Whether you’re focused on safeguarding external or internal assets, the testing process remains consistent, with tailored scopes and objectives to suit your specific needs.
Let’s see if you’ll withstand our ethical hacking attacks
The introduction to external network penetration testing
External network penetration testing is critical to securing your organization’s digital assets. This form of testing simulates attacks originating from outside your organization, just as real-world cybercriminals would target your external-facing components, such as web servers, firewalls, and public-facing applications.
During an external network penetration test, security experts adopt the mindset of malicious hackers to assess your network’s vulnerabilities from an external perspective. This assessment includes:
- Web application testing: Evaluating web applications for vulnerabilities like SQL injection, cross-site scripting (XSS), and insecure authentication mechanisms.
- Firewall testing: Assessing the effectiveness of your firewall configurations in blocking unauthorized access.
- Open port scanning: Identifying open ports and services exposed to the internet, which could be potential entry points for attackers.
- Social engineering: Testing susceptibility to phishing attacks and other social engineering tactics.
The insights gained from external network penetration testing are invaluable in strengthening your outer defenses. Proactively identifying and addressing vulnerabilities can prevent cybercriminals from exploiting weaknesses in your internet-facing infrastructure.
The introduction to internal network penetration testing
While external testing focuses on the perimeter defenses, internal network penetration testing takes a closer look at vulnerabilities that may exist within your network’s internal infrastructure. This form of service assesses the potential risks associated with unauthorized access from within the organization, such as employees, contractors, or other trusted entities.
Key aspects of internal network penetration testing include:
- Segmentation testing: Evaluating the effectiveness of network segmentation to prevent lateral movement within the network. Testers check whether a compromised system can access sensitive areas.
- Access controls: Identifying weaknesses in user access controls and permissions, ensuring that individuals only have access to resources necessary for their roles.
- Credential testing: Assessing the strength of passwords, password policies, and authentication mechanisms to prevent unauthorized access.
- Application security: Examining internal applications, databases, and services for vulnerabilities that could be exploited by attackers with insider access.
Internal network penetration testing helps organizations maintain trust within their network environments. By uncovering vulnerabilities that might be exploited by insiders or through compromised systems, you can strengthen internal controls and prevent data breaches or unauthorized access to critical resources.
In summary, external network penetration testing secures your organization’s external-facing components, while internal network penetration testing focuses on vulnerabilities within your internal infrastructure. Together, these approaches provide a holistic view of your network’s security, helping you fortify defenses and stay ahead of cyber threats.
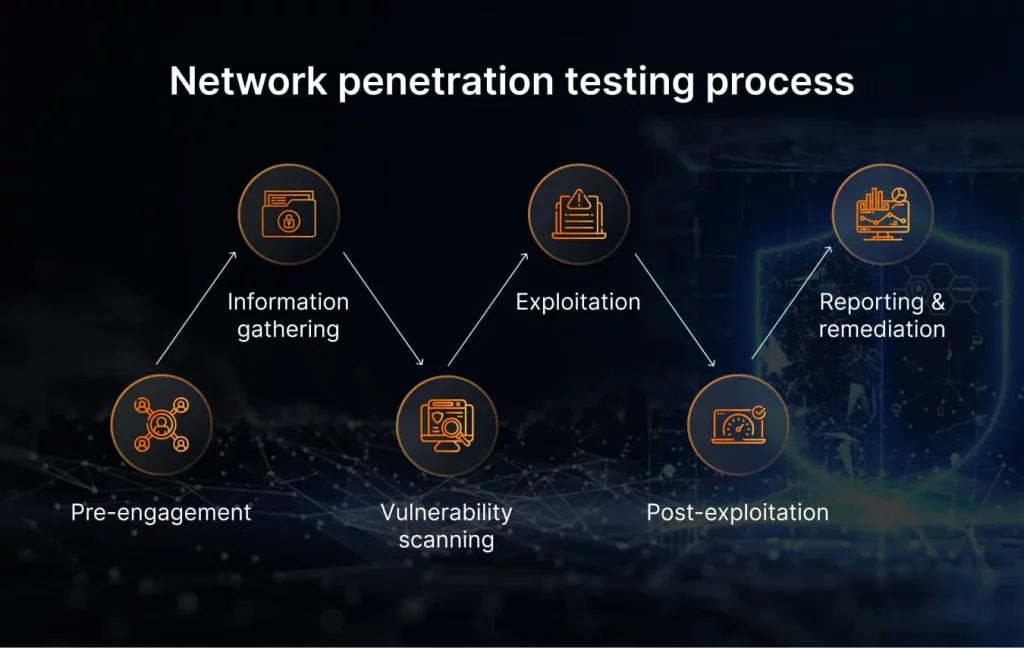
6 steps of a network penetration testing process
It doesn’t matter what type of service you choose—internal, external, or both—a structured and systematic approach is crucial for the success of network penetration testing. The process typically includes:
- The pre-engagement phase involves defining the scope, objectives, and rules of engagement for the penetration test. Clear communication with all stakeholders is essential.
- Information gathering is when testers collect information about the target network, such as IP addresses, domain names, and network configurations. This phase lays the groundwork for subsequent testing.
- Vulnerability scanning using automated tools to discover known vulnerabilities in the network. This helps testers identify potential weak points that attackers might exploit.
- Exploitation is when testers attempt to exploit vulnerabilities to gain unauthorized access to the network. Successful exploitation reveals the severity of the vulnerability.
- Post-exploitation is performed inside the network, and, at this stage, testers explore the extent of the breach. They evaluate the network’s resilience and assess the potential damage an attacker could cause.
- Reporting and remediation is the final step. Testers create a comprehensive report that highlights identified vulnerabilities, their severity, and recommendations for remediation. Later, it serves as a roadmap for improving network security.
As you can see, a network pentest report is the most valuable outcome of the whole service that can help you strengthen your security posture and continue growing with confidence. So, what should a good report include? Let’s find out together.
You have the right to know
What should be included in a network pen test report?
A comprehensive network penetration testing report is a crucial deliverable that encapsulates the findings, insights, and recommendations resulting from the evaluation of an organization’s network security. Crafting an effective report is essential not only for demonstrating the value of the assessment but also for guiding remediation efforts and future security strategies.
- Executive summary. The report should begin with a concise executive summary, summarizing the key findings, critical vulnerabilities, and overall risk assessment in non-technical language. This section provides a high-level overview for executives and stakeholders.
- The scope and objectives section clearly outlines the effort and goals of the penetration test. It describes the methodologies and testing techniques employed to achieve the stated purposes, ensuring transparency and clarity.
- Methodology. This block provides details on the testing methods, including specialized tools or techniques, explaining how the testing was conducted, both from an external and internal perspective, if applicable.
- Detailed findings. Vulnerabilities discovered during the testing process are listed in this section. All the findings are usually categorized by severity, with clear explanations of the potential impact.
- Exploitation scenarios describe the specific strategies or techniques used to exploit vulnerabilities. They include evidence of successful exploitation to illustrate the real-world risks.
- The risk assessment section includes the likelihood and potential impact of each identified vulnerability. Usually, testers use a standardized risk rating system to prioritize issues.
- Recommendations are actionable and prioritized remediation tips prepared for your IT team. Each recommendation should include specific steps for mitigation, allowing the organization to address vulnerabilities effectively.
- Technical details are often provided for security teams. They may include screenshots, network diagrams, and logs to assist in understanding the vulnerabilities and their exploitation.
- Appendices include any supplementary information that may be helpful for you, such as raw scan data, configuration files, or additional technical documentation.
- Conclusions summarize the overall security posture of the network, taking into account the findings, risk assessments, and the effectiveness of existing security controls.
- The roadmap covers the ongoing improvement, highlighting areas that need immediate attention and those that can be addressed over time. It helps organizations prioritize their security efforts.
- Compliance and regulatory considerations. This block communicates how the network penetration test aligns with industry-specific compliance requirements or regulatory standards if applicable.
- Review and approval sections ensure that the report has undergone appropriate validation by the testing team and relevant stakeholders.
A well-structured and informative network penetration testing report is a valuable tool for organizations to understand their security posture, prioritize remediation efforts, and develop a robust cybersecurity strategy. It serves as a roadmap towards a more secure network environment, helping organizations proactively defend against cyber threats.
How to choose a network penetration testing provider
Are you ready to test your network? Selecting the right network penetration testing provider is the final and most critical step for any organization seeking to enhance its cybersecurity defenses. That’s why we’ve created a must checklist to help you make a good choice:
- Experience and expertise: Evaluate the provider’s experience in the field. Look for a track record of successful tests and expertise in your industry. Well-seasoned providers understand the nuances of various systems and can adjust assessments to your needs.
- Certifications and accreditation: Verify that the provider owns relevant certifications such as Certified Information Systems Security Professional (CISSP) or Certified Ethical Hacker (CEH). Additionally, ensure they comply with industry standards and regulations.
- Methodologies: Understand the provider’s penetration testing methodologies. They should employ recognized frameworks like OWASP, NIST, or OSSTMM to ensure thorough, standardized assessments.
- Transparency: Clear and open communication is crucial. The third party should be willing to discuss their methodologies, reporting format, and any potential conflicts of interest. Transparency builds trust in the testing process.
- References and case studies: Request feedback and case studies from clients to gain insights into the provider’s capabilities and the real-world outcomes of their work.
- Reporting quality: Assess sample reports to ensure they are clear, well-documented, and actionable. Reports should not only identify vulnerabilities but also provide remediation guidance.
- Data handling: Discuss how sensitive data will be handled during the assessment to maintain strict confidentiality and data protection standards.

Selecting the right network penetration testing provider requires careful consideration of these factors. By choosing a provider with the right experience, expertise, and commitment to collaboration, you can ensure a thorough assessment of your network security and the development of a robust cybersecurity strategy.
Being prudent makes all the difference
Final thoughts
If you’re looking for an experienced and trustworthy provider for a network penetration test, you’ve come to the right place. UnderDefense is one of the leaders in the field. We reaffirm the status annually by participating in Splunk’s highly competitive Boss of the SOC challenge. In 2023, the UnderDefense elite team bagged 4th place out of over 185 participating teams.
UnderDefense ethical hackers have the perfect combination of business and technical competencies and in-depth practical skills. All of that allowed us to develop a creative approach to network security penetration testing and a distinctly individualized methodology. We offer a one-step-ahead service to track your organization’s vulnerabilities and effectively prevent breaches. Contact us today for a free quote aligned with your needs and expectations.
















