In the modern interconnected world, where threats are constantly evolving, securing your external network is paramount. Malicious actors continue to probe organizations’ defenses by fostering their tactics, creating advanced tools, and finding new vulnerabilities to exploit.
Being one of the leaders in pen testing services, we proceed to introduce you to the world of pentests and explain their differences and advantages for business. This guide will explain what external network penetration testing is, how it can benefit your company, and what you need to know to perform it right.
The average cost of a data breach exceeds $3.8M.
Find business vulnerabilities and how they may be exploited before criminals do.
Table of Contents
- What is external network penetration testing?
- The importance of external penetration testing for business
- Pentest how-to: external penetration testing checklist
- What should be included in the external network pen test report?
- External penetration testing cost considerations
- External vs. internal penetration testing: which is better for your organization?
- Conclusion
What is external network penetration testing?
Traditionally, we start with the definition, similarly to other articles related to network penetration testing.
External network penetration testing is a simulated cyberattack performed from the outside of an organization to evaluate its external networks, web apps, and systems and uncover existing vulnerabilities. This type of assessment aims to identify and address potential entry points for malicious actors attempting unauthorized access. All the results are mainly transformed into a report with recommendations for security improvements, empowering management teams to enhance their defenses and prevent data breaches.
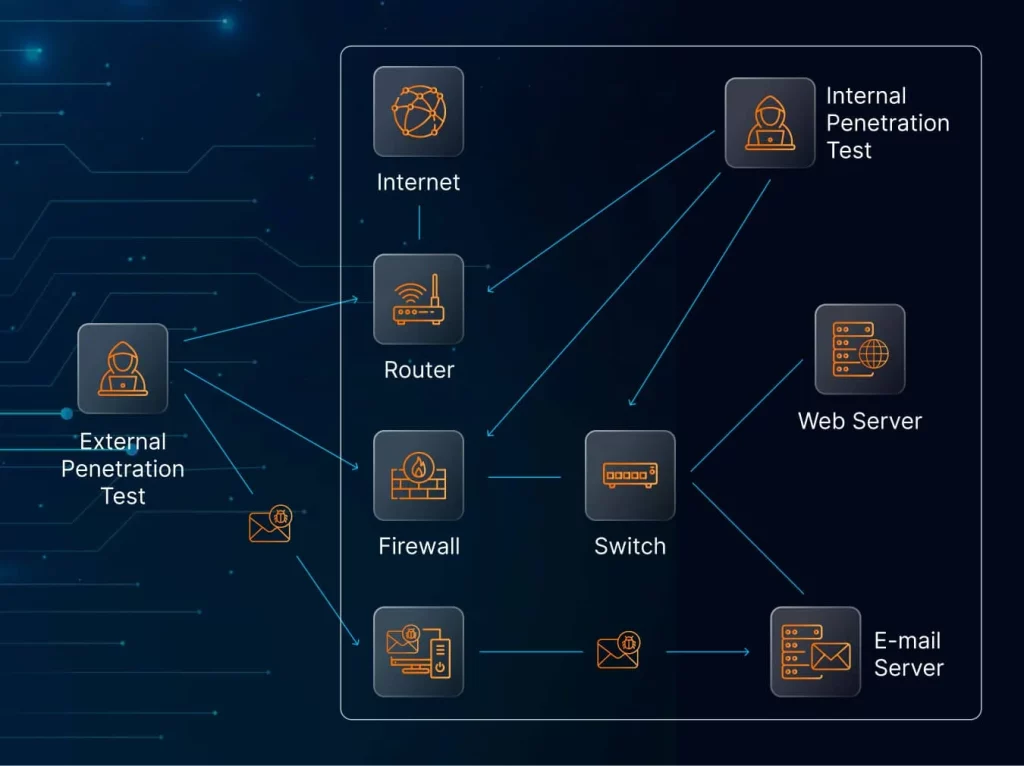
The importance of external penetration testing for business
Now that we’ve answered the common question “what is external penetration testing”, let’s discuss why management teams can hardly ignore this service in present conditions.
In a nutshell, external pen testing helps unleash weaknesses that used to go unnoticed. Using these findings companies can maintain a robust security posture and prepare for the ever-evolving threat landscape. Below we list other benefits of external penetration testing for business stakeholders:
- Mitigating risks. This type of penetration test identifies and rectifies vulnerabilities in a company’s external infrastructure before cybercriminals can capitalize on them. This proactive approach keeps potential threats at bay, preventing data breaches and reputational damage.
- Compliance and regulations. Many industries and regions have stringent cybersecurity requirements. External penetration testing aids in compliance by demonstrating an enterprise’s commitment to proactive security measures. Failure to meet these standards can lead to fines and legal repercussions.
- Safeguarding reputation and trust. A security breach can erode customer trust and harm an organization’s reputation. External penetration testing prevents breaches by identifying existing security weaknesses. It shows customers and partners that a company takes data protection seriously, fostering trust and confidence.
- Incident preparedness. Cyberattacks can strike at any moment. External penetration testing not only uncovers security gaps but also assesses their potential impact. This information is invaluable for developing effective incident response plans, and minimizing damage during a security breach.
In summary, external penetration testing is an essential cybersecurity practice that proactively mitigates risks, ensures compliance, protects reputation, and prepares organizations for potential threats. By investing in external pen testing, organizations can maintain a strong security posture and secure their external-facing systems and networks.
Let’s see if you’ll withstand our ethical hacking attacks
Pentest how-to: external penetration testing checklist
To avoid chaos and get the benefits mentioned above, we recommend that you plan the test flow and map out your expectations. Broadly speaking, external pentest can be divided into six stages, namely:
- Scoping and planning. Before conducting an external penetration test, define the scope of the assessment. Determine which systems and assets should be evaluated, set goals, and establish a testing plan.
- Reconnaissance. This phase involves gathering information about the target organization, such as IP addresses, domain names, and publicly available data. This information will help ethical hackers understand the attack surface.
- Vulnerability analysis. Identify and assess vulnerabilities in the external infrastructure. This includes vulnerability scanning and manual penetration testing to discover weaknesses.
- Exploitation. In this stage, white hat hackers attempt to exploit identified vulnerabilities to gain unauthorized access or control over systems. This simulates real-world attack scenarios.
- Post-exploitation. If successful, ethical hackers examine the extent of access gained and assess the potential impact of a breach. This helps organizations understand the severity of vulnerabilities.
- Reporting. All the findings are included into a detailed report. It should also list current vulnerabilities, explain their impact, and cover recommended remediation steps. This report is crucial for addressing security gaps and hardening a security posture.

These external penetration testing steps are the main ones. However, their number may vary depending on the scale and specific requirements of the client.
What should be included in the external network pen test report?
As we’ve already mentioned, a network penetration test report is a crucial deliverable that provides valuable insights into an organization’s cybersecurity posture. It serves as a comprehensive record of the findings, vulnerabilities, and recommendations for improving corporate defenses. Creating an effective network pen test report is essential for both the testing team and the stakeholders to get a full picture of the security landscape. So, let’s discuss what should be included in a network pen test report:
- The executive summary is an especially valuable section for non-technical stakeholders, such as executives and managers, who need a quick understanding of the penetration test’s outcomes without delving into technical details. Usually, it offers a high-level overview of the following:
- Objectives of the test, for instance as assessment of the organization’s external network security.
- Methodology or brief description of the testing approach and methods used.
- Key findings summary highlighting the most critical vulnerabilities and their potential impact.
- The introduction section provides more context to the readers, like explaining the reasons for conducting the network penetration test and the scope of the assessment. It sets the stage for what follows in the report and helps stakeholders understand the test’s purpose. So, it covers:
- The scope by clearly defining what was tested, including systems, applications, and network segments.
- Testing goals to remind readers of the test’s objectives.
- The methodology section details the specific techniques and tools used during the penetration test. This section should provide a transparent view of how the testing was conducted to ensure the test’s repeatability and credibility.
- Scanning and enumeration describing how the assessment began, including information gathering and enumeration phases.
- Vulnerability assessment explaining how vulnerabilities were identified, including automated scanning and manual testing.
- Exploitation details in those cases when vulnerabilities were successfully exploited, describing the employed methods.
- Post-exploitation covering any actions taken after gaining access to systems to assess the extent of the breach.
- Findings and vulnerabilities are the heart of the report. This section should present detailed information about each discovered vulnerability, including:
- Vulnerability name/ID to clearly identify the vulnerability for reference.
- Description explaining the vulnerability, its nature, and how it could be exploited.
- Severity level or severity score (e.g., CVSS score) of each vulnerability.
- Evidence proving the vulnerability’s existence, such as screenshots, log files, or other relevant data.
- Recommendations include clear and actionable guidance on how to remediate the vulnerability.
- Impact describing the potential consequences of the vulnerability, including its business impact and how it may affect confidentiality, integrity, and availability.
- The risk assessment section consolidates and summarizes the risks associated with the identified vulnerabilities. This can help organizations prioritize remediation efforts based on the potential impact of each vulnerability. It may also include the next information:
- Risk matrix to illustrate the severity of vulnerabilities.
- Risk ranking to make it easier for stakeholders to prioritize and focus resources on the most critical issues.
- A remediation plan should comprise clear and actionable steps for addressing the identified vulnerabilities, including immediate mitigation and a timeline for full remediation. It ensures the following:
- Prioritization to highlight which vulnerabilities should be addressed first based on their risk and potential impact.
- Responsibilities and assigned ownership of remediation tasks to specific individuals or teams.
- Timeline with established deadlines for implementing fixes and retesting.
- Conclusion summarizes the key findings and recommendations, emphasizing the critical nature of the security issues discovered during the penetration test. It may also offer a brief recap of the overall state of the organization’s network security.
- Appendices include any additional information that supports the findings or methodology. This may include raw data, detailed technical descriptions of vulnerabilities, or logs generated during the penetration test.
- Signature and approval from both the testing team and the client’s representatives should end the report. This formalizes the acceptance of the findings and the responsibility for addressing them.
As you can see, a well-structured network penetration test report is a vital tool for enhancing an organization’s cybersecurity posture. It provides a comprehensive understanding of vulnerabilities, their potential impact, and actionable recommendations for improvement. With the key elements outlined above, organizations can make informed decisions to enhance their network security and protect against evolving cyber threats.
External penetration testing cost considerations
Are you interested in external penetration testing services, but first want to know how much it will cost? Well, let’s explore together. But, before we begin, it’s worth noting that the cost of an external pen test can vary greatly, depending on several factors:
- The scope and complexity of your external infrastructure play a significant role in price formation. The more systems, apps, and services that need penetration testing, the higher the cost. Additionally, evaluating complex architectures or intricate web applications may require specialized skills and increase the price.
- The depth of the assessment is another factor. A basic scan for known vulnerabilities will be less expensive than a comprehensive test that includes manual testing and attempts to exploit vulnerabilities. Deeper penetration testing provides a more accurate picture of security but comes at a higher cost.
- The qualifications and experience of the testing team also impact costs. Admittedly, seasoned penetration testers with specialized skills command higher fees. But their expertise can lead to more thorough and accurate assessments. So, this is something we don’t recommend saving on if you want high-quality outcomes.
- Frequency of testing also influences the final estimate. Regular tests are essential for maintaining security, but quarterly or monthly assessments may require a larger budget compared to annual ones.
While the cost of external penetration testing is a consideration, it’s crucial to view it as an investment in cybersecurity. In 2023, the average cost of a data breach in the United States has reached $9.48 million according to Statista. We need to admit that it far exceeds the cost of testing.
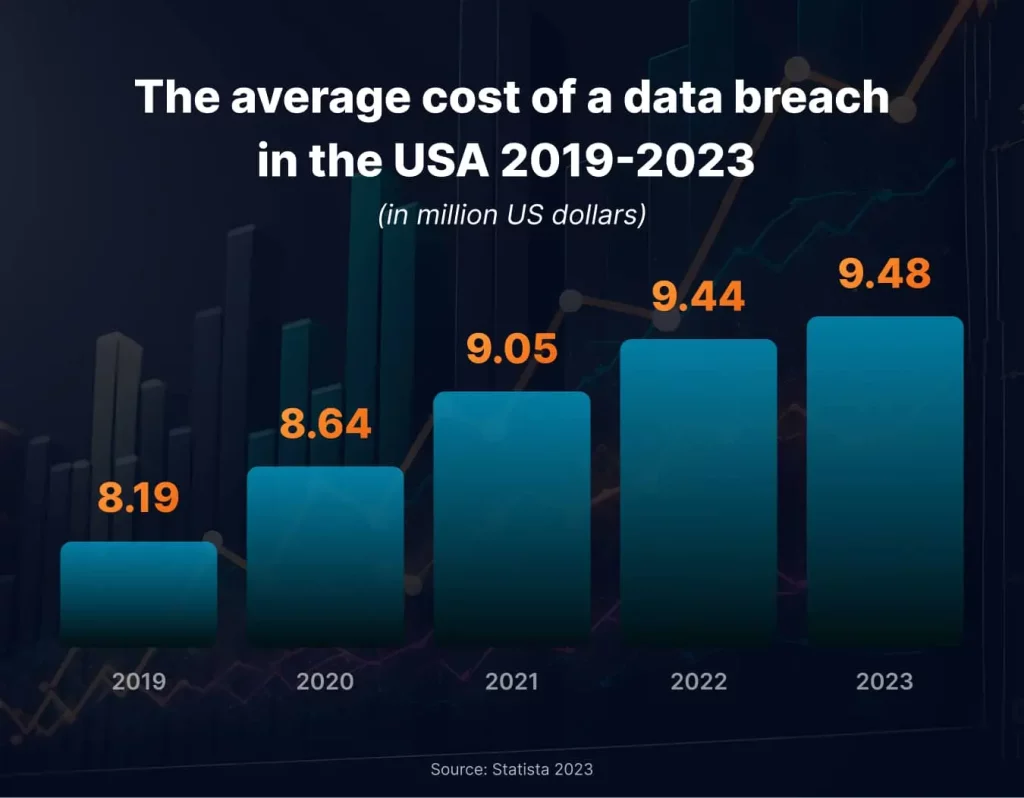
With that said, the initial goal is to identify and mitigate vulnerabilities proactively, protecting your organization from potentially catastrophic cyberattacks. Therefore, budgeting for external penetration testing is a prudent strategy to ensure the ongoing security of your external-facing systems and data.
External vs. internal penetration testing: which is better for your organization?
If you’re looking for an in-depth comparison of two service types, we recommend that you read our latest internal vs. external penetration testing article. But broadly speaking, both internal-external infrastructure penetration testing approaches are crucial for the development of a strong security posture as they unleash even minor weaknesses in different parts of your digital ecosystem.
External network penetration testing | Internal network penetration testing |
An external pentest tries out existing perimeter security to discover vulnerabilities in public-facing assets, like sites, web apps, FTP servers, and more. | An internal pentest highlights insider threats, like risky employees. It helps assess what a hacker could achieve with primary access to your network. |
External penetration testing is recommended if:
| Internal penetration testing is recommended if:
|
As you can see, the difference between external vs internal penetration testing is obvious, as external penetration testing focuses on the perimeter and public-facing systems. Meanwhile, internal penetration testing assesses internal network security. Consequently, it isn’t about whether to choose an external or internal pentest, as they are both essential for comprehensive business protection.
Being prudent makes all the difference
Conclusion
External network penetration testing is a vital component of any organization’s cybersecurity strategy, but only if it’s conducted properly. So, choosing a service provider, ensure the company has the necessary certifications, plus experience and knowledge of specific methodologies and compliance standards you are obliged to follow. If you are looking for a professional, in-depth external network pentest, you can get it from UnderDefense.
UnderDefense pentest team has the ideal combination of business and technical competencies and in-depth practical skills making it one the best in the field. In 2023, we bagged 4th place out of over 185 participating teams in Splunk’s highly competitive Boss of the SOC challenge. Our ethical hackers offer a one-step-ahead penetration testing service to identify your vulnerabilities, mitigate risks, and effectively prevent breaches. Contact us today for a free quote based on your actual needs and expectations.
















