CASE STUDY
UnderDefense Helps Industry Leader Fortify Security After Azure AD Phishing Breach
Background
The Challenge
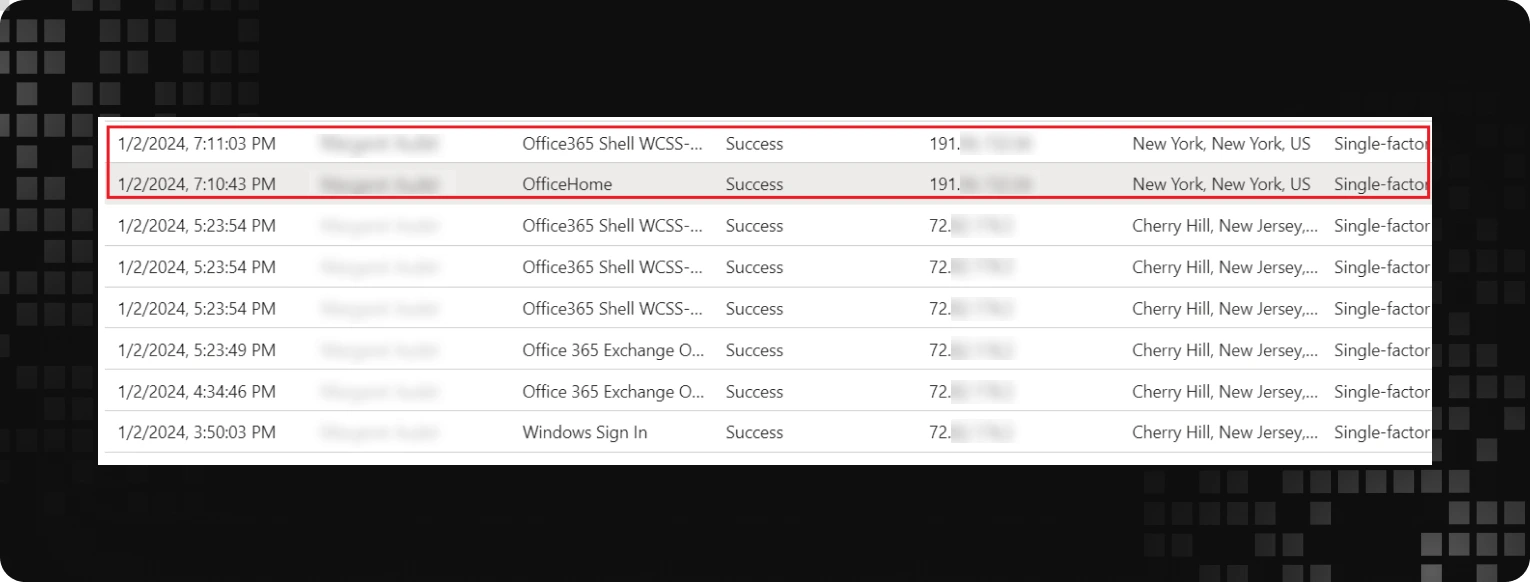
- Incident out of SOC monitoring scope: The client’s existing security setup, including the partnership with the UnderDefense SOC team, did not include logging of Microsoft 365 activity. This limitation hindered our SOC team’s detection and response capabilities, making it more difficult to identify suspicious behavior or unauthorized access attempts in real time.
- Lack of awareness of Azure AD risks: The client lacked awareness of how attackers could breach their Azure AD environment and the associated risks.
- Risks to contracts, emails, and communication: The client was unaware of the potential risks to their contracts stored in SharePoint, sensitive emails, and communication with partners and customers within Azure AD.
Challenges | Results |
Lack of knowledge on how to react to phishing incidents and how to identify their origin and fully remediate them | Provided DFIR where identified who and how exactly was breached, explained the attack timeline to the client, and eradicated hackers’ way into Azure AD. Otherwise, the hackers would have had unrestricted access to the CEO’s account, including all files and emails. |
Azure AD environment was not secured with Conditional Access, device management, and strong MFA policies | Provided a list of improvements and tailored recommendations on why and how to implement the policies. Now the client is fully secured from attacks based on password guessing and much less vulnerable to all kinds of Azure AD phishing attacks. |
Azure AD environment was not monitored for anomalies in real-time | Increased SOC monitoring scope to include Azure AD environment protection, with an ability to detect anomalous logins and unconfirmed privileged actions. |
About the client
Headquarters:
New Jersey, USA
Marketing insurance and financial services products
20-50
$2000000
AWS (CloudTrail, EC2, RDS, VPCFlow, WAF)
Fortigate
Web Servers
166
Infrastructure:
100% Cloud
Internal IT Security Team:
1 person
0 (not in the monitoring scope)
Multiple Production Servers
Key Results
100%
Of production servers protected 24/7
Less than 30 min
Response to the client’s request
The Solution
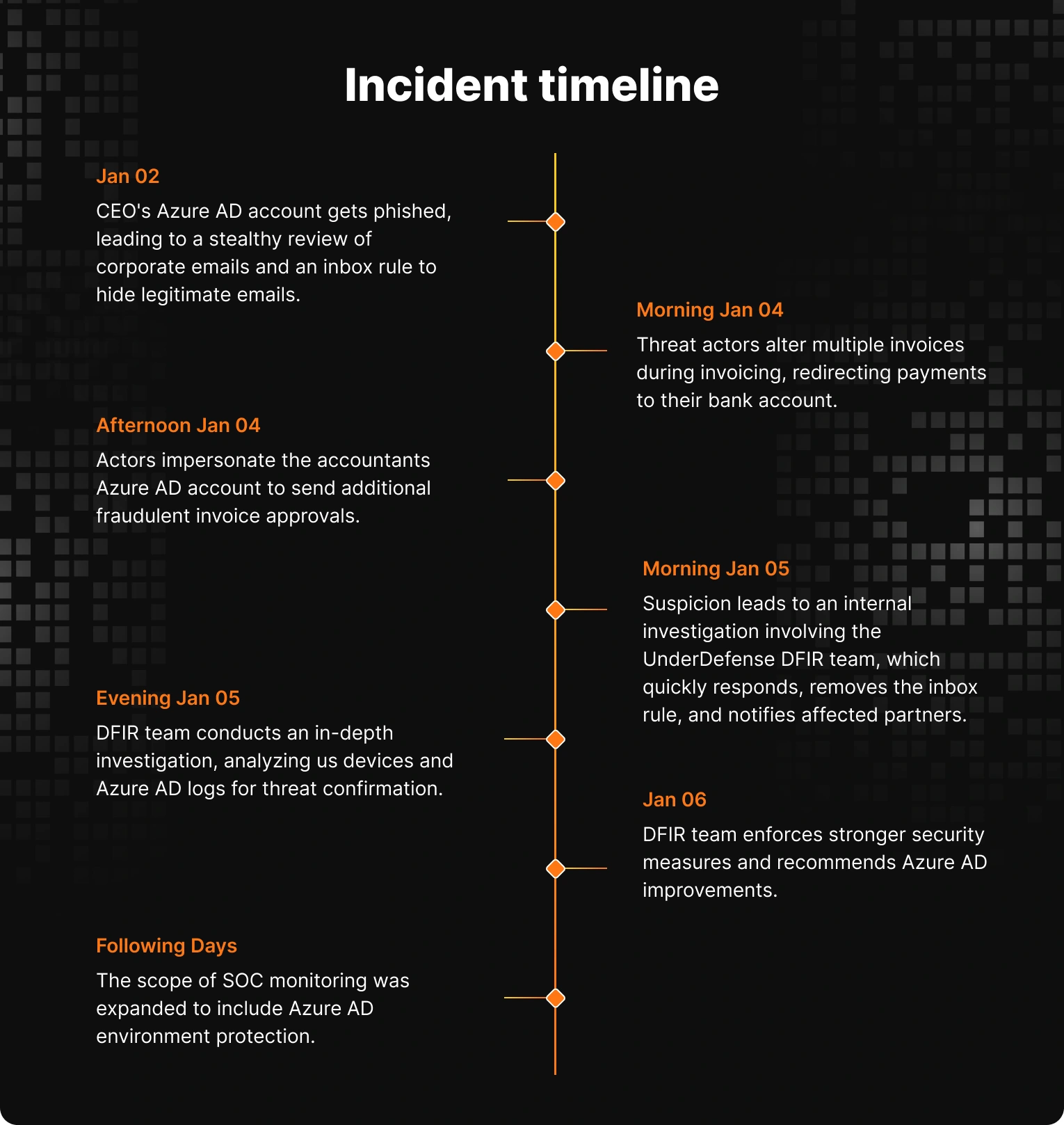
- Phishing attack and unauthorized access: Threat actors successfully phished the CEO’s Azure AD account, taking advantage of the absence of multi-factor authentication (MFA). They then initiated a stealthy review of corporate emails, setting the stage for their malicious activities.
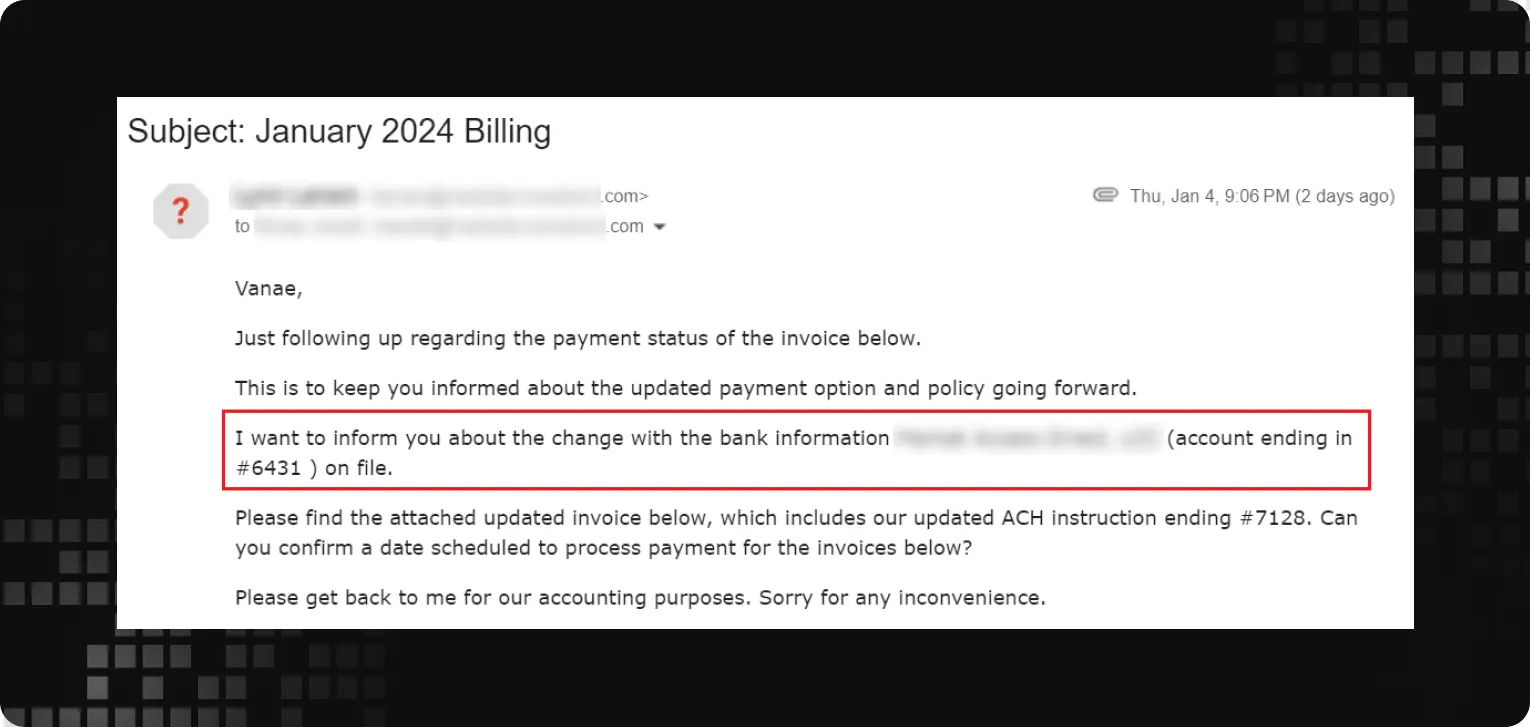
- Stealthy manipulation and fraudulent invoices: The threat actors patiently waited for the invoicing period, where they covertly altered multiple legitimate invoices, redirecting payments to their bank account. They impersonated the accountant’s Azure AD account to cover their tracks, sending additional invoice approval confirmations.
- Internal investigation and DFIR engagement: Suspicion among invoice recipients sparked an internal investigation, which quickly escalated to involve the UnderDefense DFIR team. We quickly investigated the activity, removing the malicious inbox rule and evicting the attackers from the CEO’s account.
- Forensic examination and remediation: Our DFIR team conducted a thorough forensic examination, onboarding users’ devices and Azure AD audit logs into our forensics solution. This allowed us to confirm the origin of the threat and assess potential breaches of other identities or assets. Additionally, we enforced stronger security measures for affected and privileged accounts and recommended multiple Azure AD improvements to bolster defenses.
- Improved preparedness and reduced risks:Thanks to our rapid response and comprehensive remediation efforts, the client emerged better prepared to handle similar incidents. By addressing Azure AD security configuration flaws and increasing the scope of SOC monitoring to include Azure AD environment protection, we significantly reduced the risks of Azure AD account compromise moving forward.

Outcomes
Fortified Azure AD security
Rapid Incident Response
Empowered workforce
Take control of your business security, before hackers do.