We comprehensively audit your infrastructure, ensuring all defects are addressed for enhanced security and reliability.

Detect security vulnerabilities, fix them, and achieve your business goals
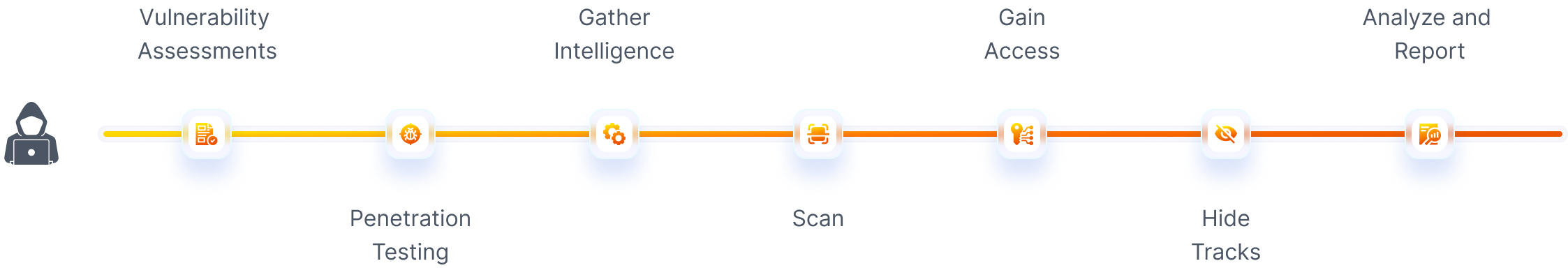
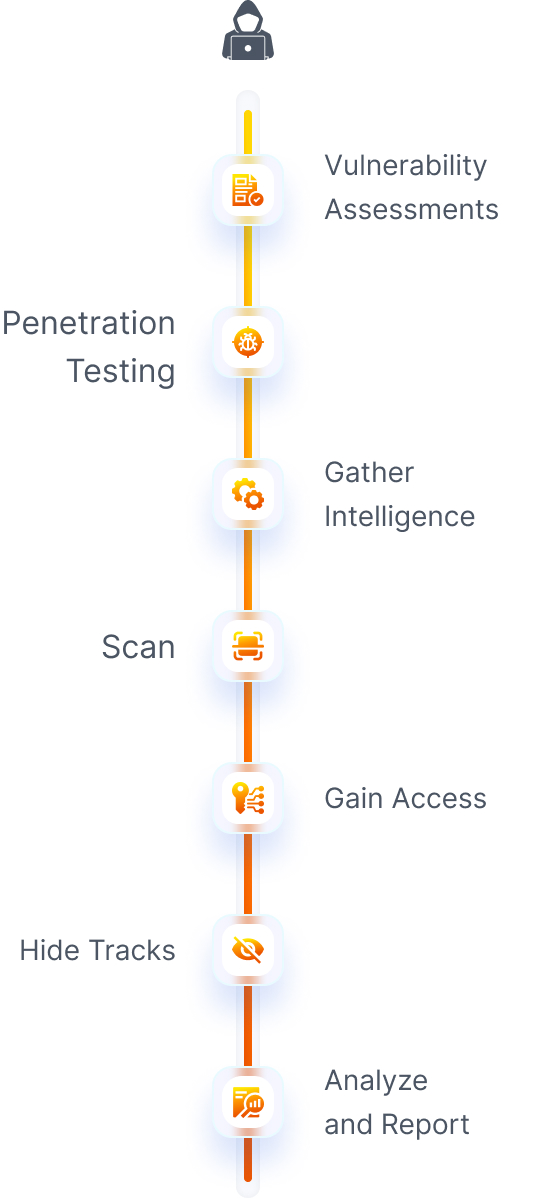
What do ethical hackers do?
Exclusive ethical hacking reports by UnderDefense delivered with unmatched detail and value
Types of ethical hacking services we provide
Need Help Choosing the Right One?
Talk to ExpertProfessional hacking services tailored for your protection
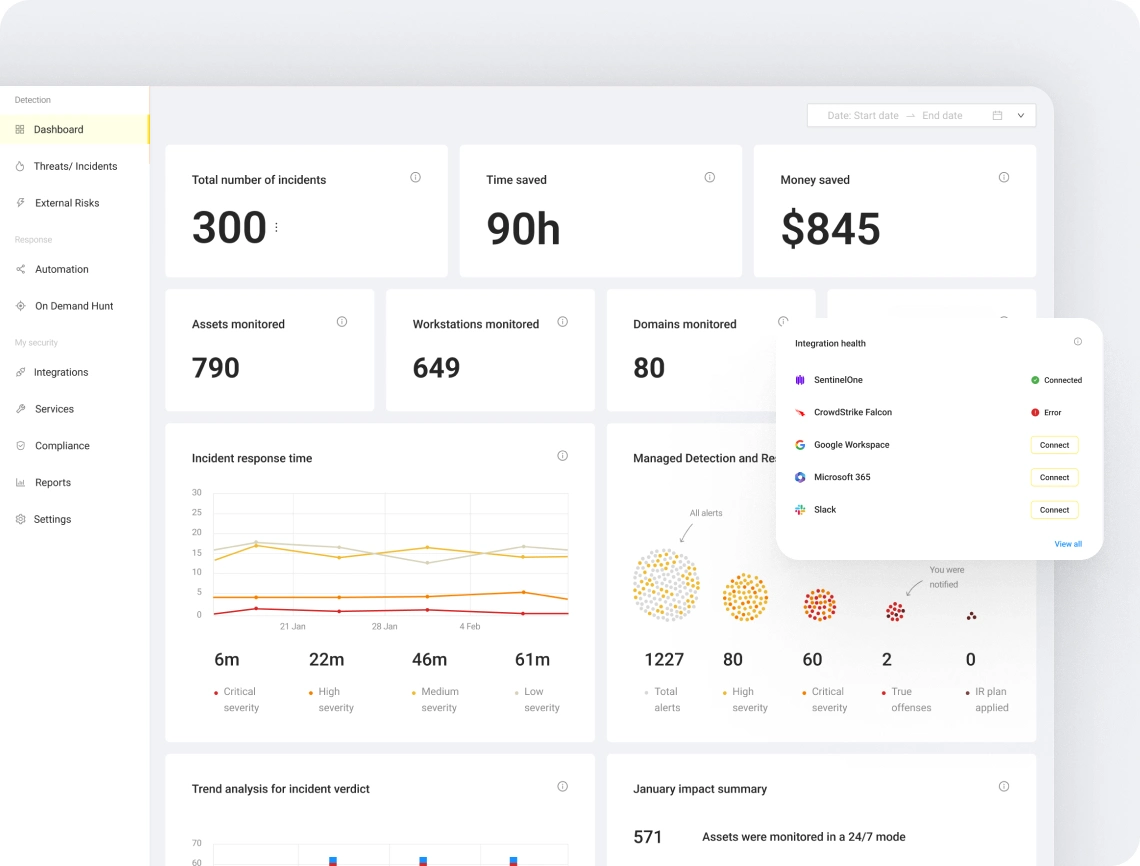
Total security with UnderDefense MAXI platform: consolidated defenses, enterprise-grade protection, and unparalleled value
- See the bigger picture: Conduct a comprehensive analysis of your external risks, proactively identifying and mitigating threats.
- Effortless compliance: Stay ahead of industry regulations with streamlined compliance management.
- Centralized reporting: Consolidate all your penetration testing reports in one place for easy access and historical reference.
- Unwavering vigilance: Enjoy 24/7 monitoring and automatic adjustments to your security perimeter, ensuring constant protection.
clients say
UnderDefense Helps Industry Leader Fortify Security After Azure AD Phishing Breach
CASE STUDYUnderDefense Helps Industry Leader Fortify Security After Azure AD Phishing Breach...
UnderDefense Initiates Proactive Threat Hunting and Detects Hidden Threats in the Client’s Environment
CASE STUDYUnderDefense Initiates Proactive Threat Hunting and Detects Hidden Threats in the...
Azure Security Through a Pentester’s Lens: 10 Best Practices to Fix Most Common Entry Points & Misconfigurations
Detecting Invisible: passwords stealers on MacOS with blind EDR
Learn how to detect stealthy macOS threats that bypass even the most advanced EDR systems…