UNDERDEFENSE CYBERSECURITY SOLUTIONS
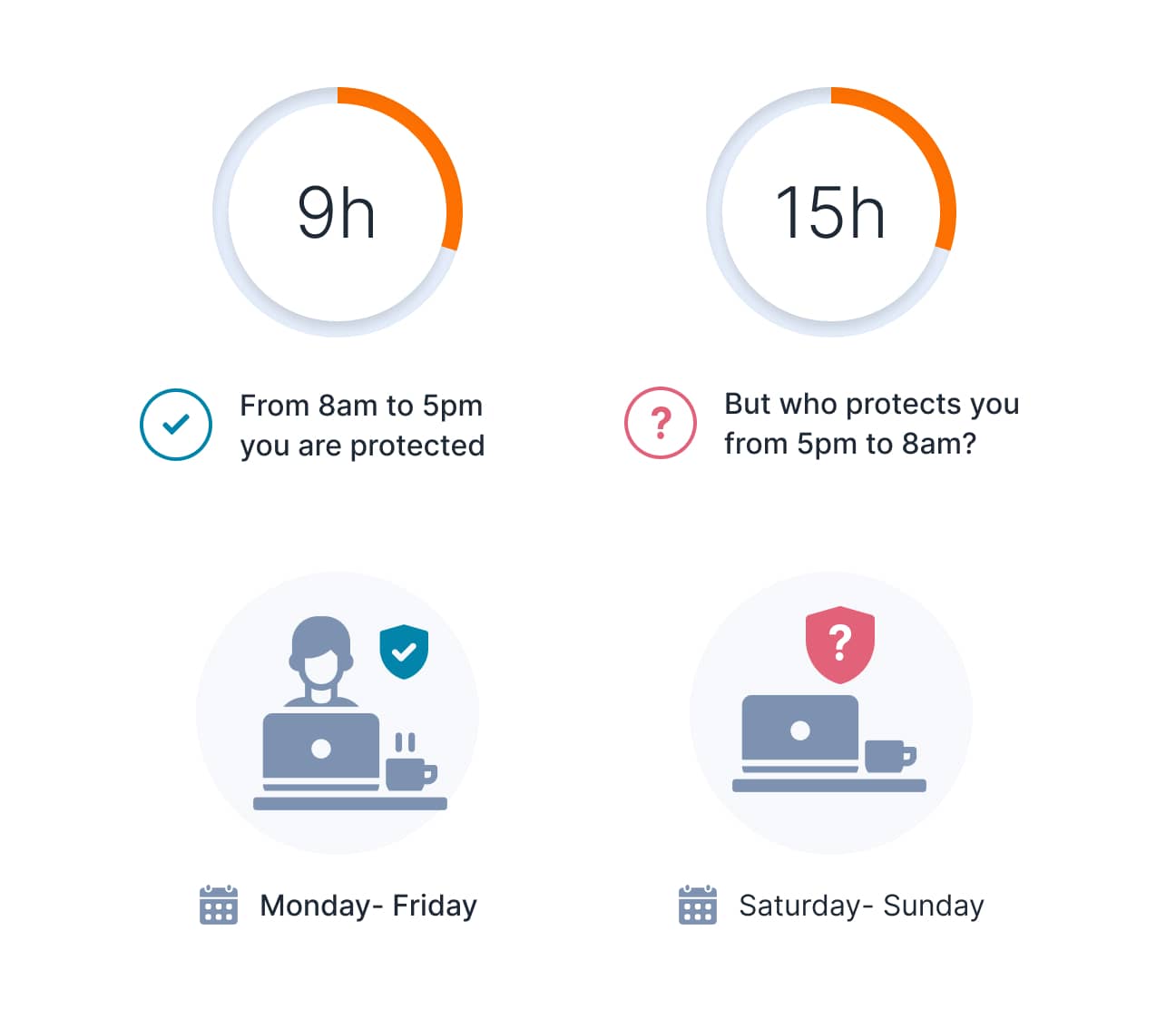
Build advanced threat prevention
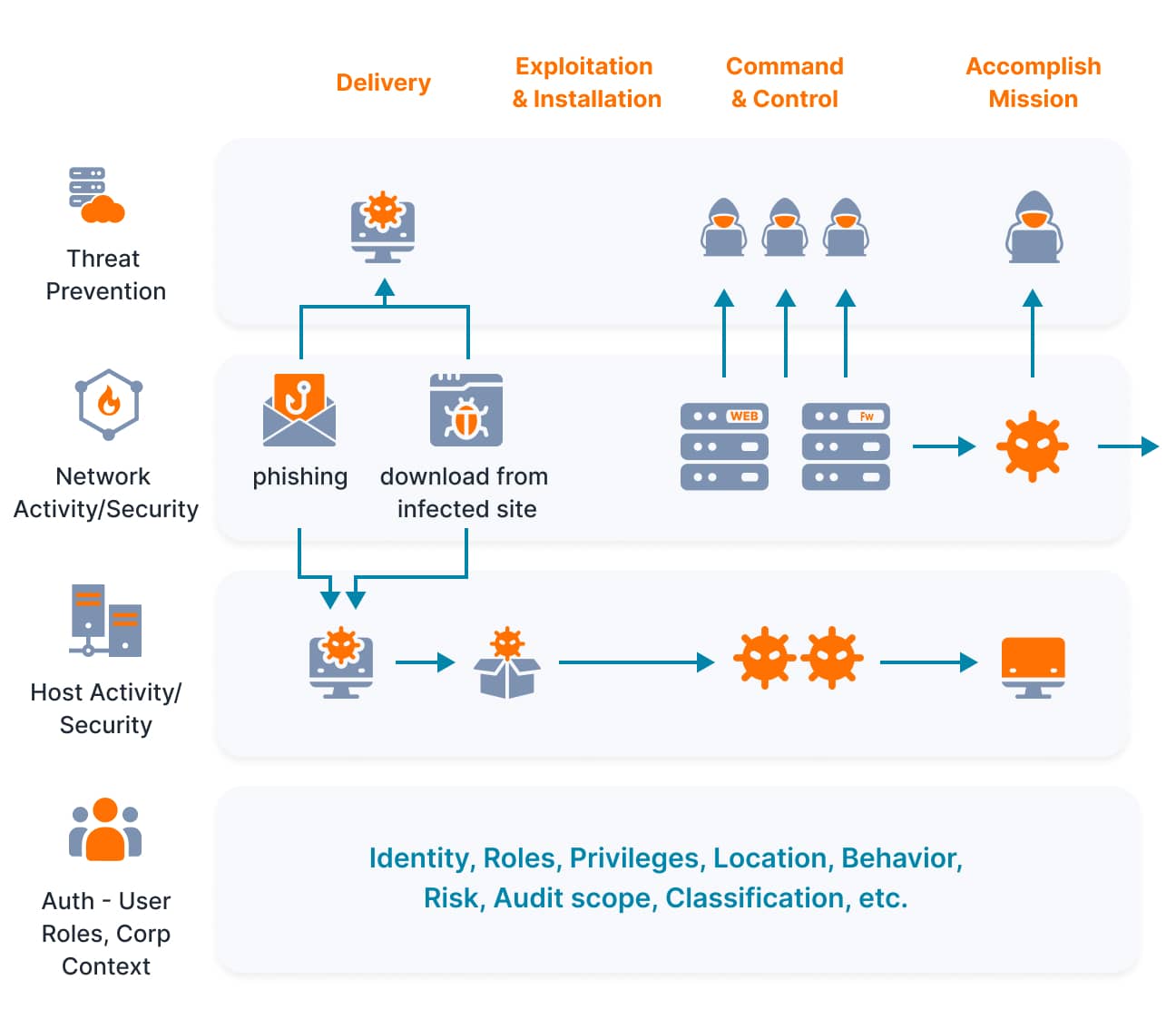
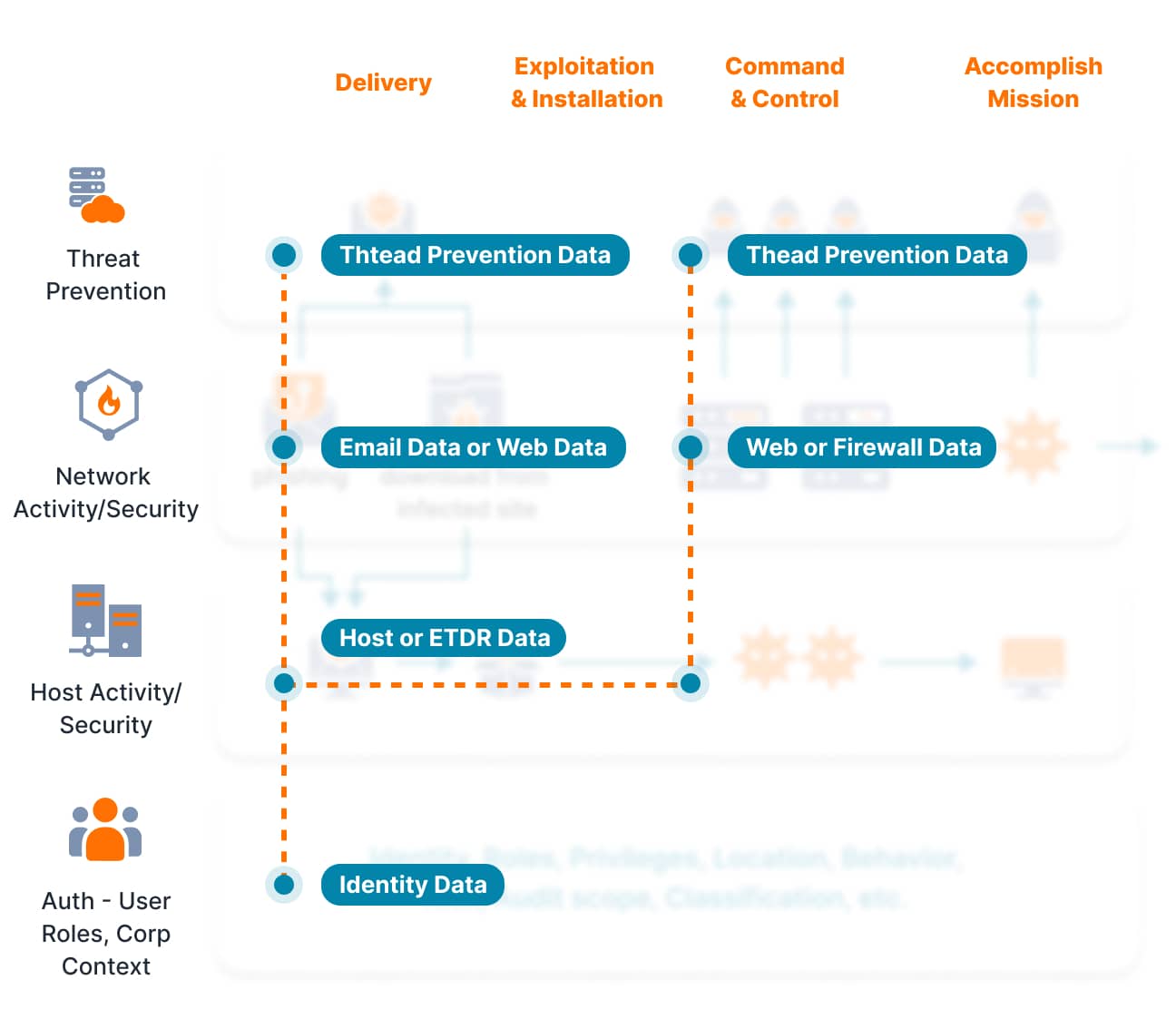
Automatically filter out false positives to detect genuine threats and prevent them from becoming devastating incidents. Aggregate, correlate, and context all your threat signals using UnderDefense MAXI - a single platform to reduce alert fatigue, accelerate investigations, and know what happens in your IT environment 24/7
Alert noise reduction
MITRE ATT&CK framework coverage
Reduction of security team workload
Achieve streamlined,in-depth control over your security
Benefit from integrated, multilayered business protection
How it works
How it works
Experts. Finalists.Winners.
Not sure where to begin?
Start with assessing your exposure to existing risks using the UnderDefense MAXI platform. Register for free and connect your EDR, SIEM, and other sensors to collect and analyze all your logs in one place. Gain immediate insights into your appearance on the dark web, password leaks, user identity risks, and more.
clients say