Penetration Testing Services
The Best Defense Starts With Knowing the Gaps
See deeper into your security with penetration testing services done by award-winning experts. We know how to hack and defend.
Use our offensive and defensive expertise to get the most comprehensive report covering all your vulnerabilities and actionable steps to remediate them.
Request a PentestTry a better way to do pen testing services
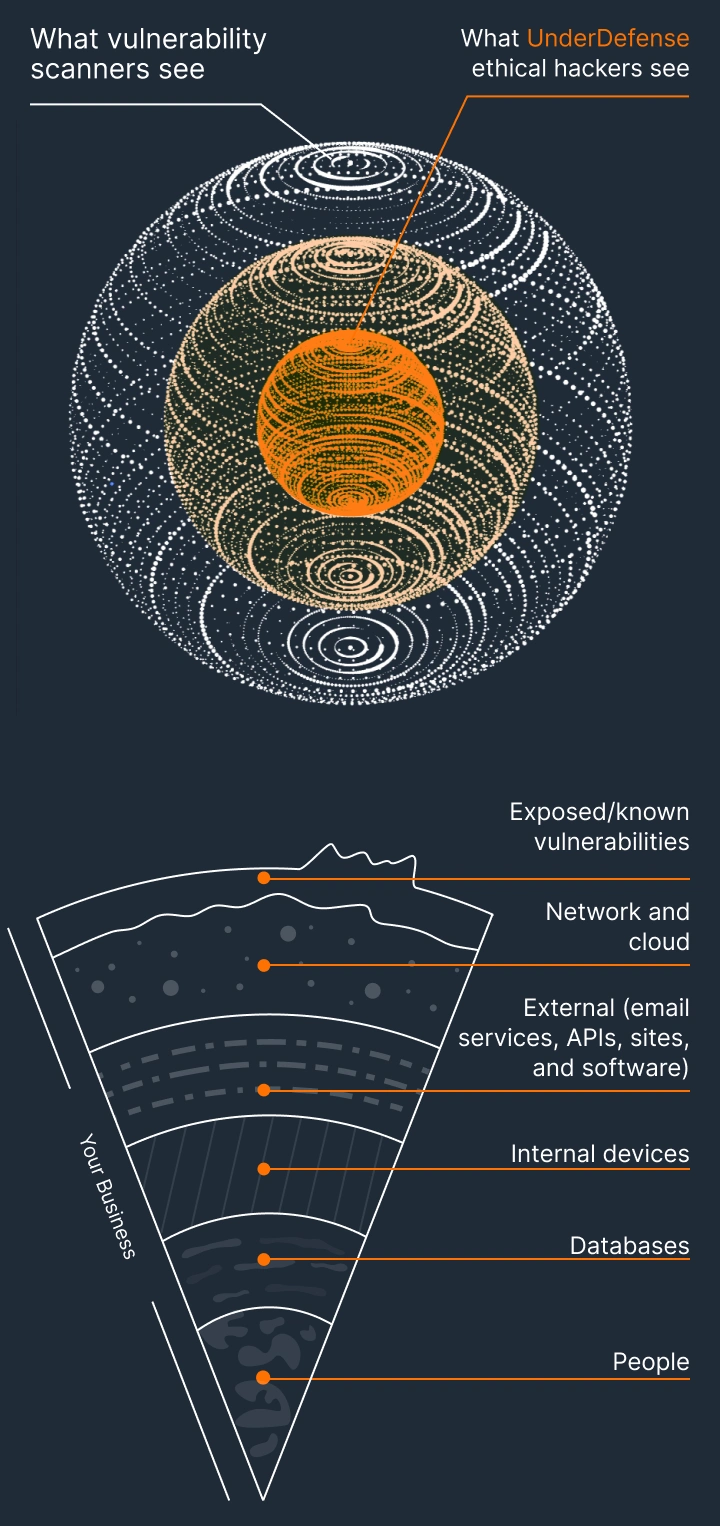
With UnderDefense you see more than scanners do
Your trusted partner for all types of cyber security testing services
Tests annually
Vulnerabilities detected per year
Weeks an average pentest lasts
Expect personalized cyber security penetration testing services
Not sure what type of security testing service you need?
We go beyond traditional pen testing services
Access the all-in-one UnderDefense MAXI platform
Create a free UnderDefense MAXI account and improve your business security immediately by:
- Conducting a comprehensive analysis of your external risks
- Staying compliant with strict industry regulations and standards
- Collecting all your penetration testing reports in one place
- Monitoring and adjusting your security perimeter 24/7
Why 500+ companies
have chosen UnderDefense
“Immediate value. Very professional approach.
Fast, efficient, and easy to work with."
— These are just a few phrases business leaders use to describe their experience with UnderDefense.
Read more stories from our customers and find out why organizations call UnderDefense mission-critical to their cyber protection.
Best CyberSecurity Provider 2022
on Clutch
Splunk Boss of the SOC 2023
out of 182 teams
Average rating on Gartner Peer Insights for MDR Services
Our awards and certifications
Get tested. Verified. Trusted.
Frequently asked questions
What is penetration testing?
What's the difference between penetration testing services and vulnerability assessment?
How much does a penetration testing service cost?
How long does a penetration test take?
On average, cyber security testing services take around 3 working weeks, depending on the size and complexity of an organization. A typical timeline for a pentest includes the following stages:
- Planning. Together with you, we define and document test objectives, scope of work, start date, and engagement model for the pen test as a service team.
- Reconnaissance. Depending on the selected pen testing as a service methodology, we collect the necessary information regarding targeted apps and infrastructure, roles, credentials, business logic, and more.
- Vulnerability discovery and exploitation. Our ethical hackers manually test the defined assets to identify security weaknesses, gaps in design and architecture, and process loopholes. They exploit all the discovered vulnerabilities to evaluate the risk level of each issue and potential harm to the business.
- Reporting. The UnderDefense pen testing team creates a detailed report on all the findings, including all the evidence and artifacts like videos and screenshots. Additionally, our experts prepare a list of tactical recommendations on how to solve each vulnerability quickly and effectively. The working results are presented to the client.
- Free post-remediation testing. When all the improvements and changes are made, our ethical hackers are ready to check fixed vulnerabilities and retest the targeted assets. Upon completing the assessment, you get a professional attestation letter confirming your security rating.
How often should penetration tests be conducted?
When can you start pen testing?
What methodologies for a pentest as a service do you use?
Do you store the results of penetration services?
Things to check out
UnderDefense Helps Industry Leader Fortify Security After Azure AD Phishing Breach
CASE STUDYUnderDefense Helps Industry Leader Fortify Security After Azure AD Phishing Breach...
UnderDefense Initiates Proactive Threat Hunting and Detects Hidden Threats in the Client’s Environment
CASE STUDYUnderDefense Initiates Proactive Threat Hunting and Detects Hidden Threats in the...
Azure Security Through a Pentester’s Lens: 10 Best Practices to Fix Most Common Entry Points & Misconfigurations
Detecting Invisible: passwords stealers on MacOS with blind EDR
Learn how to detect stealthy macOS threats that bypass even the most advanced EDR systems…