UNDERDEFENSE CYBERSECURITY SOLUTIONS
Automate Incident Response
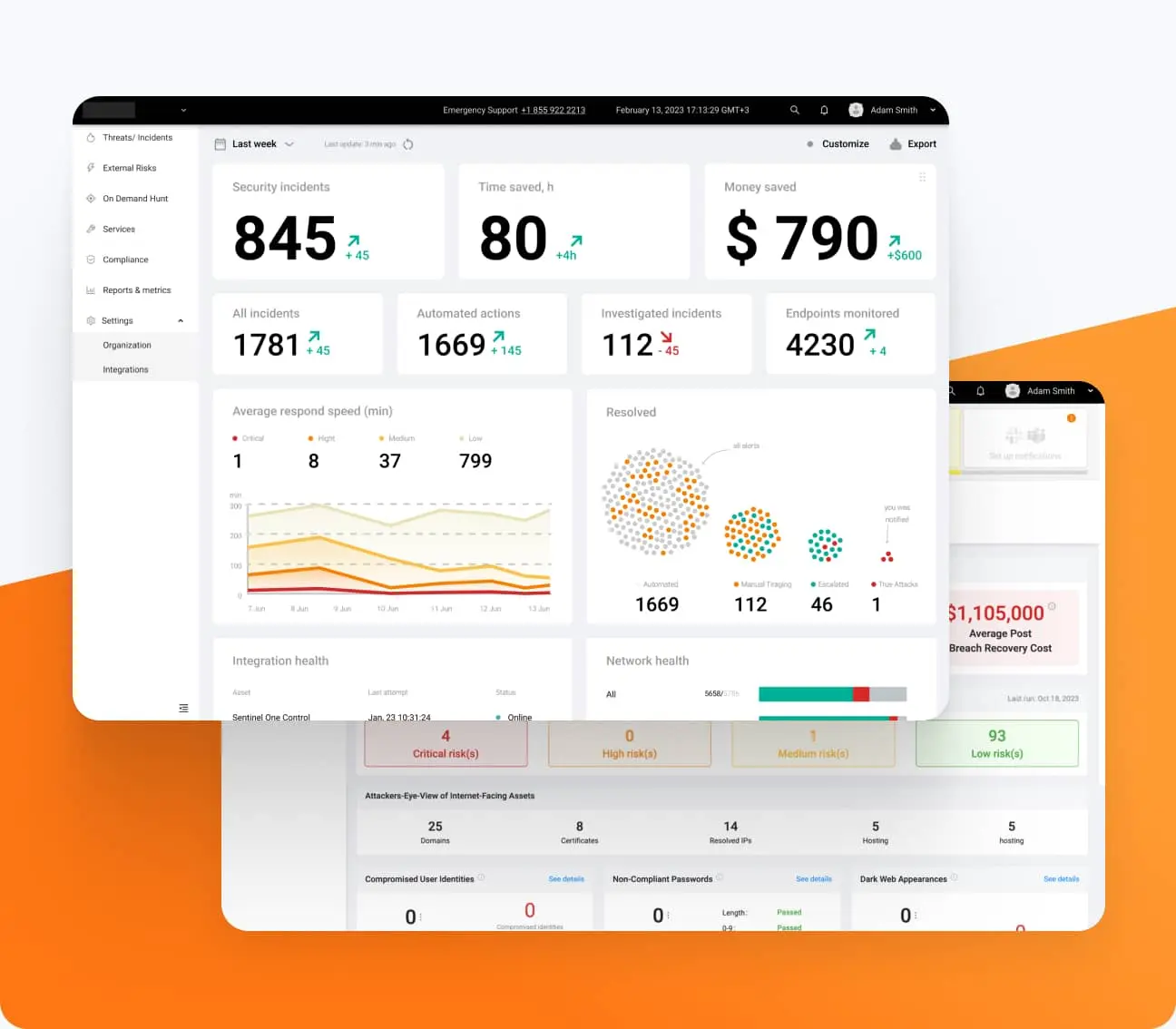
The next-gen security automation is now accessible to any business size and maturity level. Streamline your incident response process across your on-prem, hybrid, and cloud environments with the UnderDefense MAXI automated capabilities.
Of alerts missed during manual investigation
Of manual incident response processes can be automated
Is the average hourly cost of downtime
From overwhelmed to full 24/7 control
Centralize and automate your security operations in one place
How it works
How it works
Experts. Finalists.Winners.
Not sure where to begin?
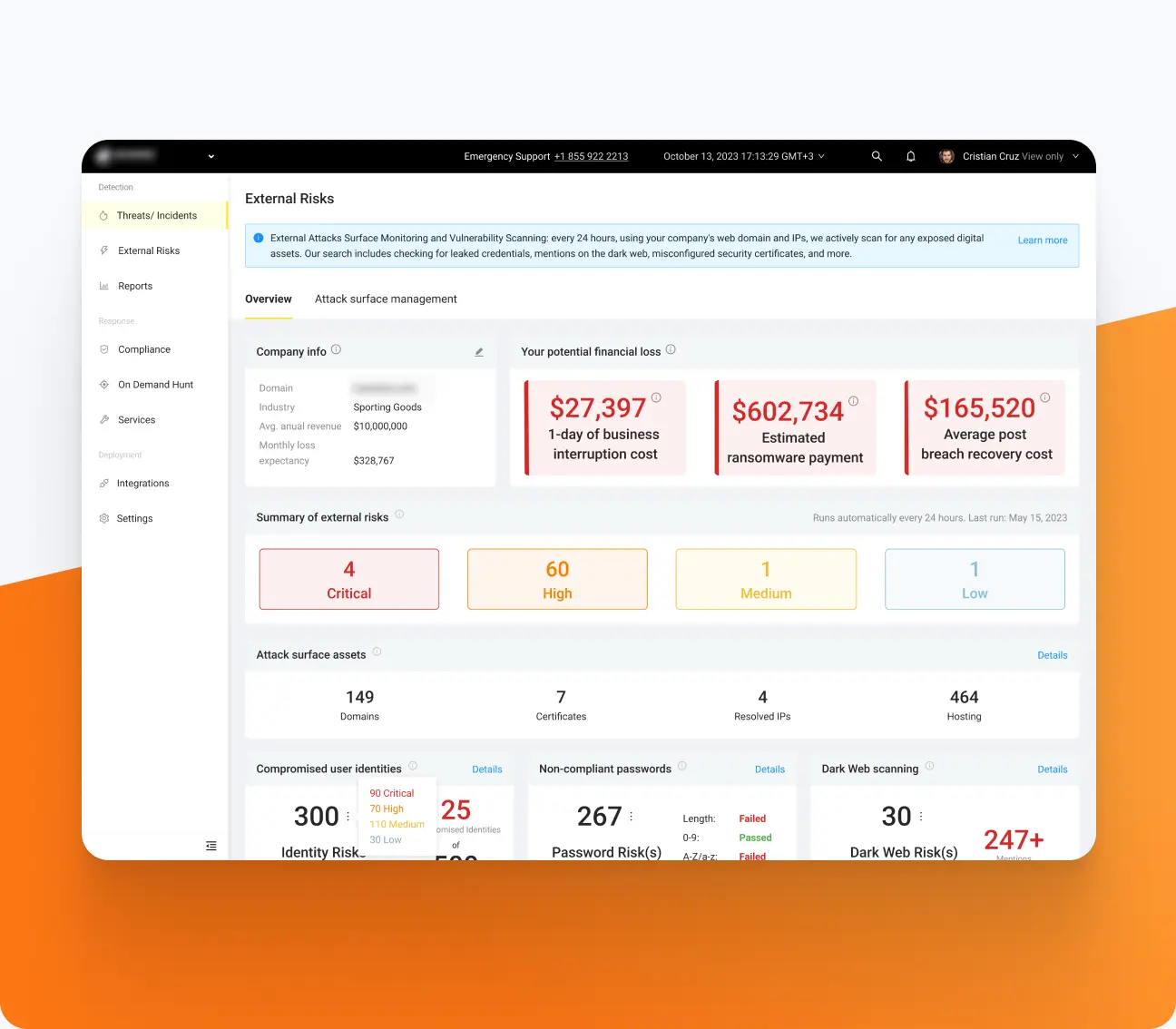
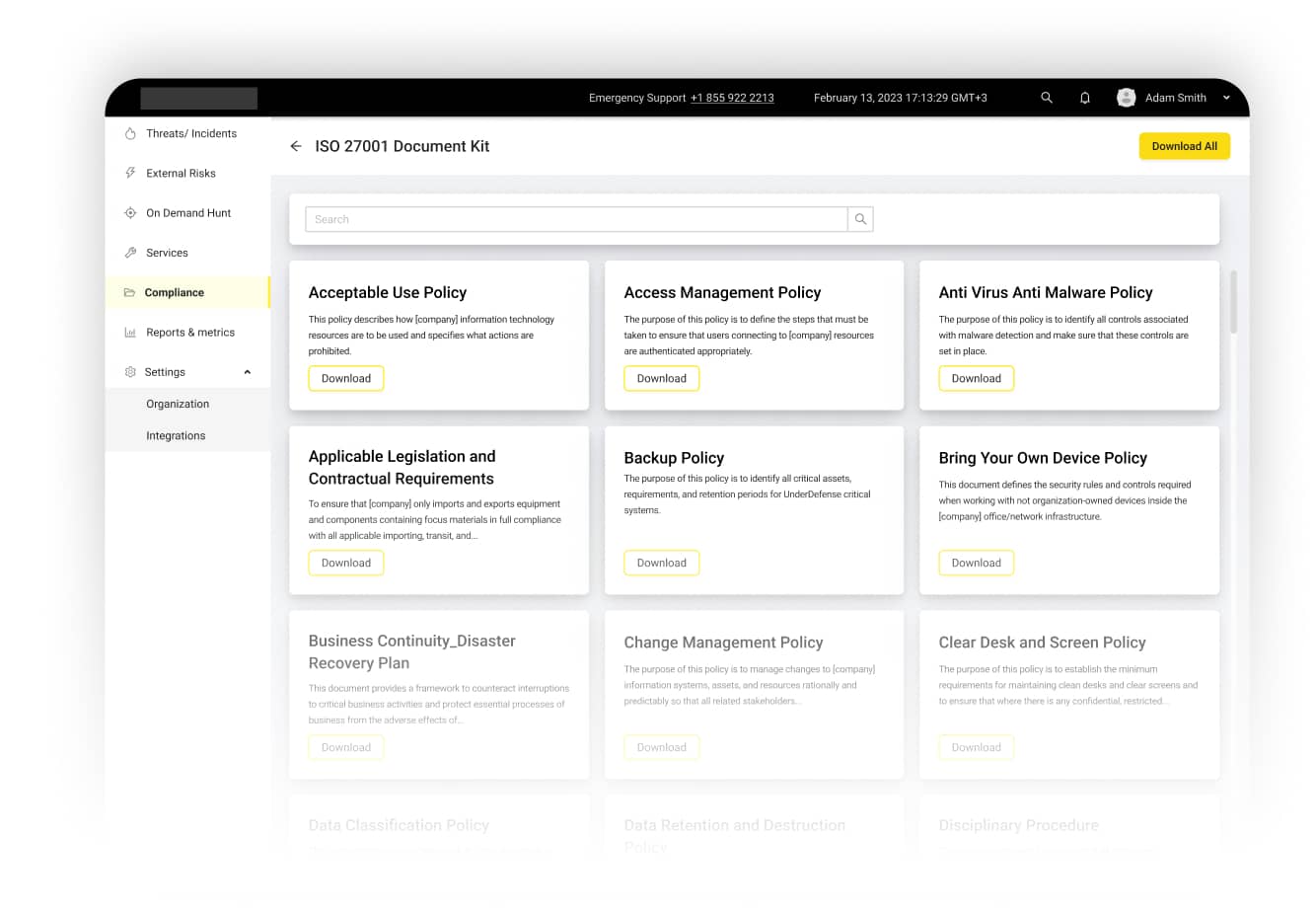
Start with assessing your exposure to existing risks using the UnderDefense MAXI platform. Register for free and connect your EDR, SIEM, and other sensors to collect and analyze all your logs in one place. Gain immediate insights into your appearance on the dark web, password leaks, user identity risks, and more.
clients say