MANAGED SOC
Unleash the power of Managed SOC
We stop breaches. Really!
Get a fully-fledged managed SOC or save your in-house SOC from the hassle and headache of dealing with Tier 1 responsibilities.
Supercharge your business with compliance and security. Get contexted answers from experts who hunt for threats 24/7.

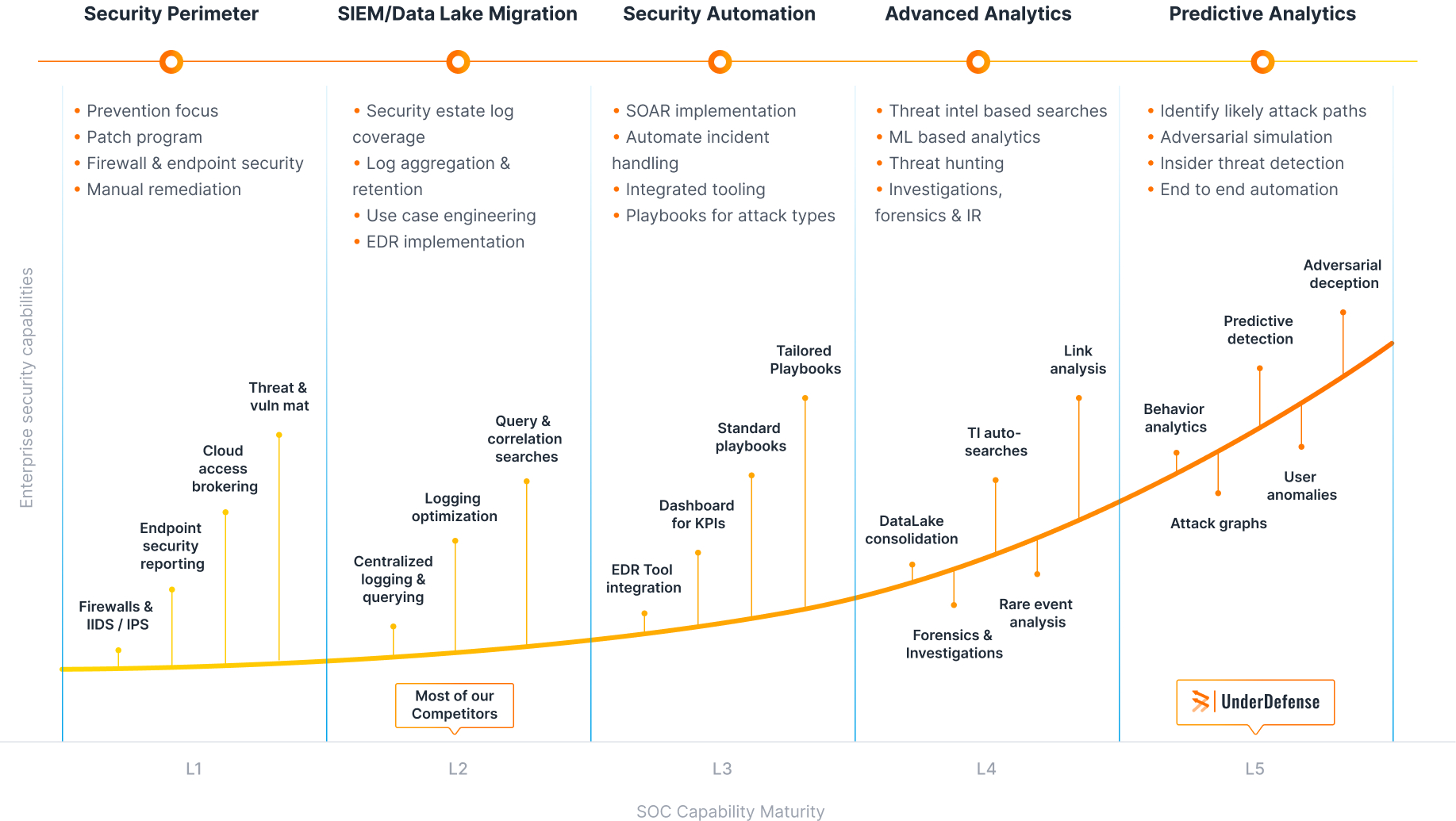
Building and managing your own SOC is tough because
UnderDefense SOC:
managed services by the numbers
In the Global SOC battle, out of 184 Splunk’s BOSS of the SOC participants
Return on investment over 3 years
To detect and enrich threat details enabling an analyst to initiate manual triage
Accurate detection rate to filter out misleading alerts in our SOC and point your attention to real threats
Co-managed SOC team makes top-rated security tools work at their maximum capacity
See All Integrations
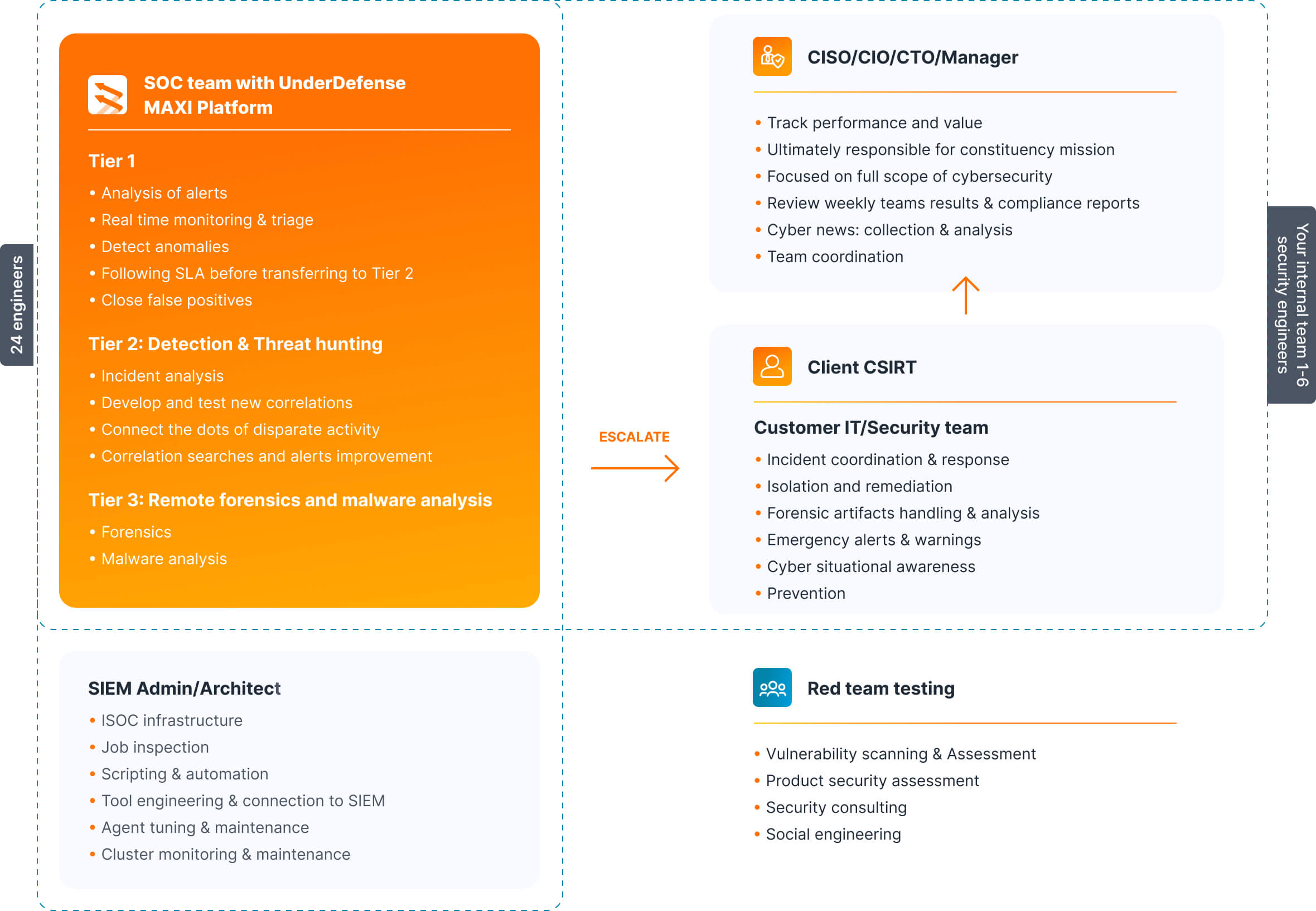
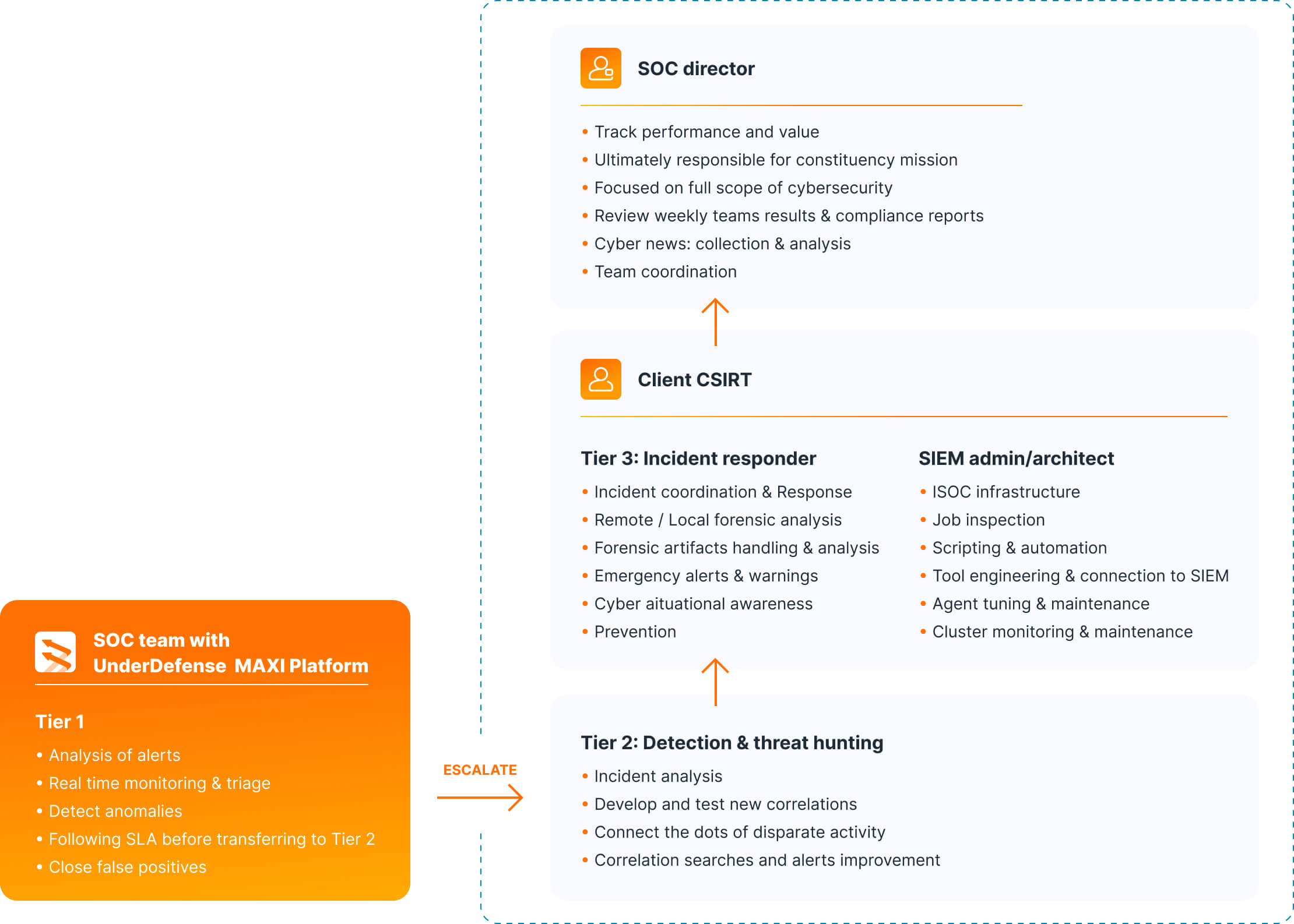
We seamlessly integrate with your operations, leveraging the robust capabilities of the UnderDefense MAXI MDR platform. We identify and mitigate risks in real time, minimizing the impact on your organization. Count on us not only as your SOC but as a partner in elevating your defense mechanisms.
We serve as your Tier 1 SOC analyst with the UnderDefense MAXI MDR platform, filtering through the noise and presenting only true, confirmed offenses. We cover you 24/7, so your team must only act when critical situations arise. This keeps your highly motivated and skilled security experts fresh and focused, ready to tackle the most pressing threats.
Not sure where to begin?
- UnderDefense MDR Monthly Report 2023
- [SOC] MDR Monthly Report 2023
- [R&D] MDR Monthly Report 2023

clients say
Experts. Finalists.Winners.
Frequently asked questions
What is a managed SOC?
A managed security operations center is a service-based business approach where a company delegates all or part of SOC functions to an external managed SOC service provider. The main drivers for managed security services (SOC-as-a-Service) are cost saving, talent shortage, and proliferated use of the cloud.
What does a SOC monitor?
SOC teams leverage various technologies and tools to cover an organization's entire IT ecosystem and ensure its security 24/7. They monitor network activity, event logs, telemetry data, system signals, and endpoint events.