Your One-Stop Shop for Better, Easier, and Faster Cybersecurity
Meet the UnderDefense MAXI MDR + SOAR security-as-a-service platform backed by our 24/7 concierge team for your ultimate business protection at every step of the way
Security-as-a-Service Platform
One platform. All things cybersecurity
UnderDefense MAXI is a holistic Security-as-a-Service platform that provides comprehensive coverage at every step of the way: from early risk discovery and compliance to incident response automation and round-the-clock 24/7 protection with MDR.
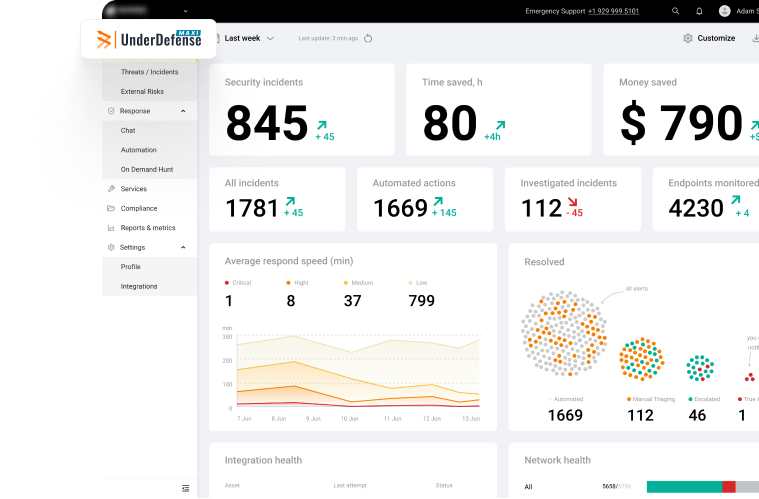
A full stack of cybersecurity services to solve your security challenges
Use a holistic set of cybersecurity services offered by a reputed provider with much experience in cybersecurity without any mediators or outsourcers
Forever-free compliance certification kit
Sign up for UnderDefense MAXI platform and download our forever-free SOC 2 and ISO 27001 certification kit to make preparations for compliance audits easy and efficient.
Sign Up and Download
I want to...
Goals you encounter on your path to achieving 24/7 business protection. Now resolved.
Protect my cloud (AWS, Microsoft, GCP, Kubernetes)
Become compliant
Protect against ransomware
Manage my SIEM / EDR
Protect my Office 365/ Google Workspace / G Suite
Automate incident response
Eliminate alert fatigue
Get a SOC overnight and a 24x7 MDR
Get real-time security ROI reports
Pentest my applications and infrastructure
Buy security tools I need
Protect against supply chain attacks
Make my legacy tools work together like an orchestra
Access 24/7 dark web monitoring / External surface monitoring
Evaluate risks and protect my external exposure
Perform attack surface analysis and management
Why 500+ companies
have chosen UnderDefense
“Immediate value. Very professional approach.
Fast, efficient, and easy to work with."
— These are just a few phrases business leaders use to describe their experience with UnderDefense.
Read more stories from our customers and find out why organizations call UnderDefense mission-critical to their cyber protection.
Best CyberSecurity Provider 2022
on Clutch
Splunk Boss of the SOC 2023
out of 182 teams
Average rating on Gartner Peer Insights for MDR Services
Enhance your defenses, accelerate detection and response
UnderDefense combines cutting-edge technologies, own innovative SECaaS platform, and 24/7 next-gen SOC to address your most pressing IT security concerns.
Ensure end-to-end monitoring and instant response for your cloud, on-premise, and hybrid environments regardless of scale and complexity.
Contact us
Things to check out
Penetration Testing Report: Free Template and Guide
Do you need a pentest but are worried about deciphering the report? Are you seeking a pentest...
Azure Security Through a Pentester’s Lens: 10 Best Practices to Fix Most Common Entry Points & Misconfigurations
Despite Azure's impressive features, it's important to note that it's still susceptible to...
Azure Security Through a Pentester’s Lens: 10 Best Practices to Fix Most Common Entry Points & Misconfigurations
Detecting Invisible: passwords stealers on MacOS with blind EDR
Learn how to detect stealthy macOS threats that bypass even the most advanced EDR systems…
Outsourced SOC vs. In-House SOC: Making the Right Choice
Let's talk
All the conversations are always held by humans and never by bots. We appreciate your interest in UnderDefense.
You will hear back from us shortly.
















