Managed Detection and Response
Managed Detection
and Response (MDR)
Not all MDR solutions are created equal. Get complete 24/7 control across your environment, leverage the full potential of the tools you already own, and respond to threats faster with automation with MDR by UnderDefense.
Get a DemoWhy we are different
UnderDefense seamlessly integrates into your existing security stack and manages it efficiently and effectively 24/7.
We proactively hunt for threats across your cloud, on-premise, and hybrid environments regardless of scale and complexity.
Challenges you face on your way to 24/7 business protection. Now solved
Lack of human resources
Limited budgets and unclear pricing
Misconfigured tools
Overloaded with false positives team
Neutralize threats in minutes, not hours
Speed up your response to all types of cyber threats—both known and unknown—using our in-house built threat response prioritization engine. Benefit from a robust set of detection and correlation rules, seamless process automation from immediate detection to efficient remediation. Make use of our custom playbooks for a smoother, more efficient threat response strategy.
Build better, faster, and easier cybersecurity with UnderDefense MDR solutions
24/7 continuous business protection across all environments
UnderDefense MAXI platform to resolve incidents faster with automation
Intelligent use of tools you already have
Advanced flexibility in cooperation models
Cutting-edge in-house developments
Expert-driven threat hunting and mitigation
How it works
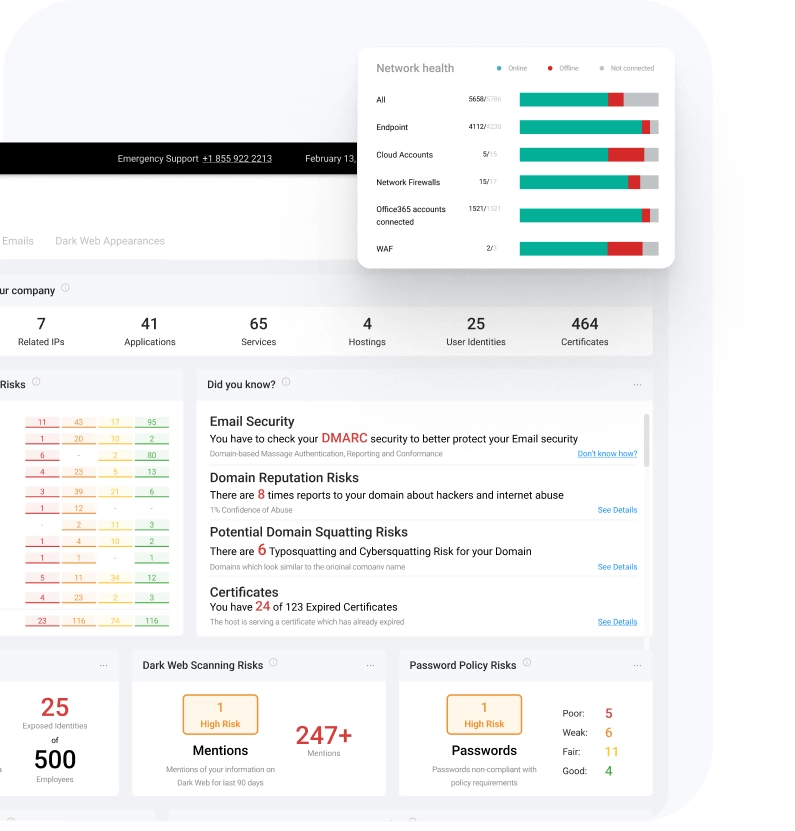
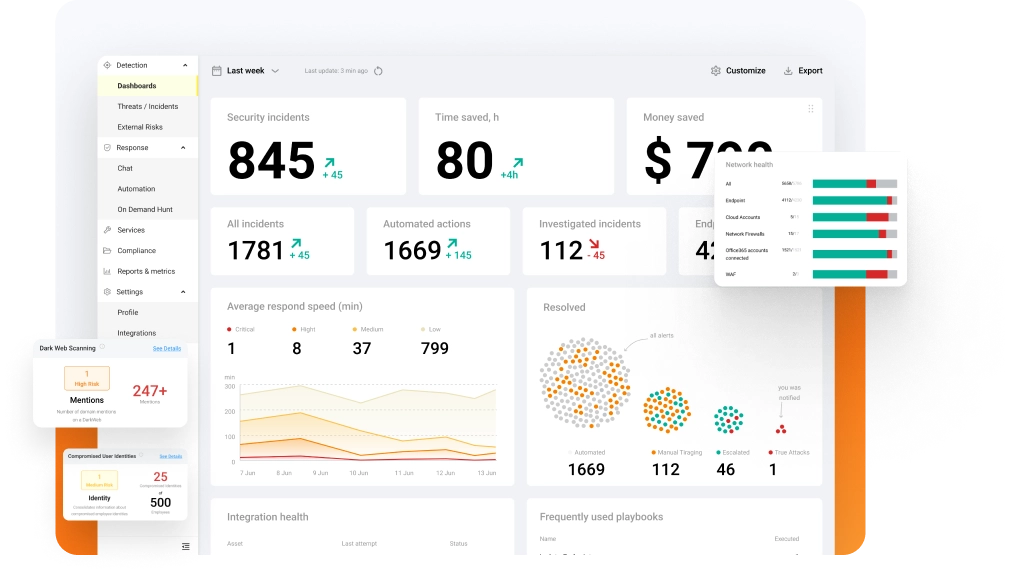
Get full transparency and control with UnderDefense MAXI platform
- Check what our SOC team sees and how they are protecting your business against advanced cyberattacks
- Have absolute control over your environment settings
- Use pre-defined or create custom incident response playbooks
- Get expert advice 24/7
- Assess your cybersecurity effectiveness and create informative reports for the management team
All-in-one MDR security for all your environments and assets
Why 500+ companies
have chosen UnderDefense
“Immediate value. Very professional approach.
Fast, efficient, and easy to work with."
— These are just a few phrases business leaders use to describe their experience with UnderDefense.
Read more stories from our customers and find out why organizations call UnderDefense mission-critical to their cyber protection.
Best CyberSecurity Provider 2022
on Clutch
Splunk Boss of the SOC 2023
out of 182 teams
Average rating on Gartner Peer Insights for MDR Services
Frequently asked questions
What is managed detection and response (MDR)?
How much does the managed detection and response services (MDR) cost?
What is the UnderDefense MAXI platform?
How do I purchase the UnderDefense MAXI platform?
UnderDefense offers a freemium model. You can start with a sign-up and get immediate access to many valuable features, including:
- 360° security assessment
- Forever-free certification kits
- AWS cloud security assessment
- On-demand threat hunting
But we don’t stop here. UnderDefense MAXI grows with you, supporting you at every step of the way. Benefit from a modular, fully integrated suite of cybersecurity solutions and add advanced tools for your end-to-end business protection on the go. Create your free account today and see where better and easier cybersecurity happens.
As an MDR provider, what data will you see in my environment and have access to?
Things to check out
Penetration Testing Report: Free Template and Guide
Do you need a pentest but are worried about deciphering the report? Are you seeking a pentest...
Azure Security Through a Pentester’s Lens: 10 Best Practices to Fix Most Common Entry Points & Misconfigurations
Despite Azure's impressive features, it's important to note that it's still susceptible to...
Azure Security Through a Pentester’s Lens: 10 Best Practices to Fix Most Common Entry Points & Misconfigurations
Detecting Invisible: passwords stealers on MacOS with blind EDR
Learn how to detect stealthy macOS threats that bypass even the most advanced EDR systems…










