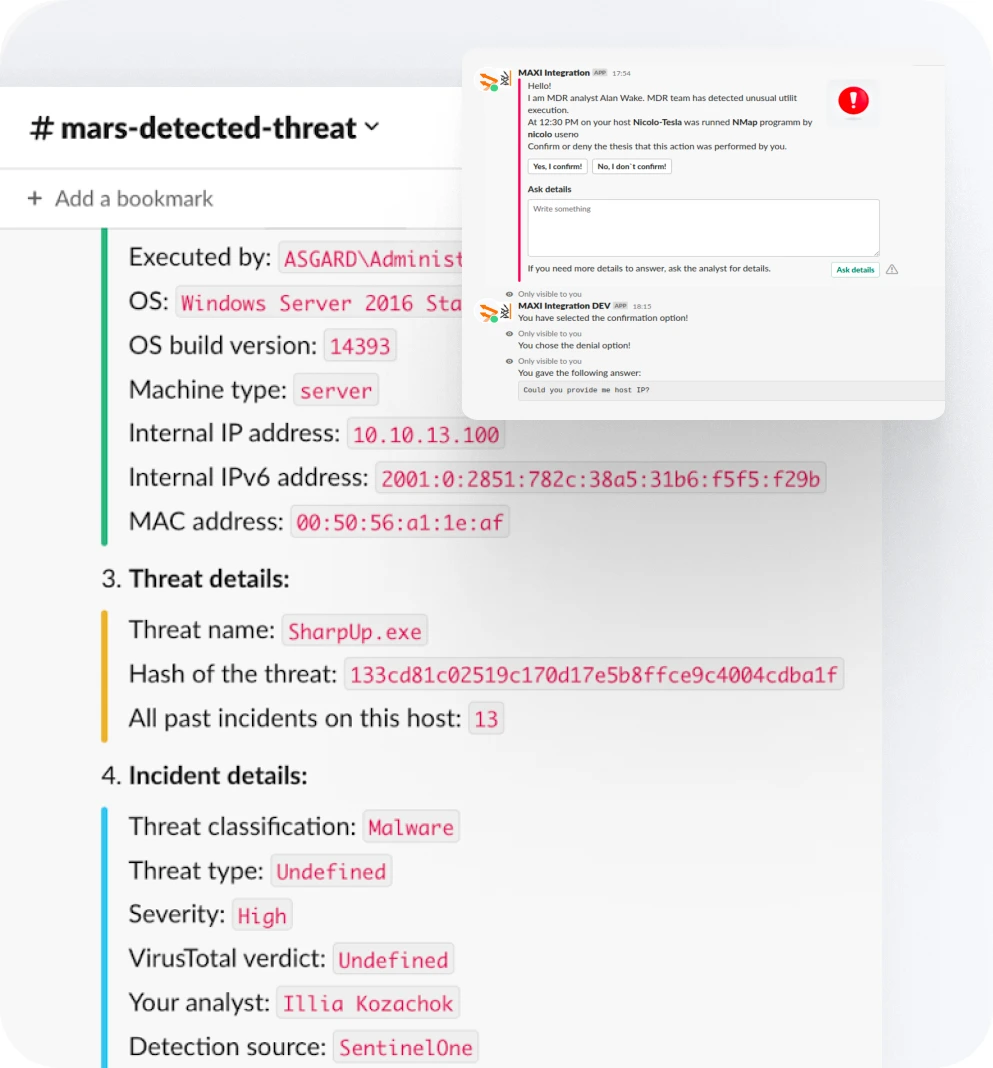
Monitor potential weaknesses with a FREE External Vulnerability Scan
Navigating risk management becomes easy with the UnderDefense MAXI platform.
We automate your routine tasks and regularly update what you need to fix and how.

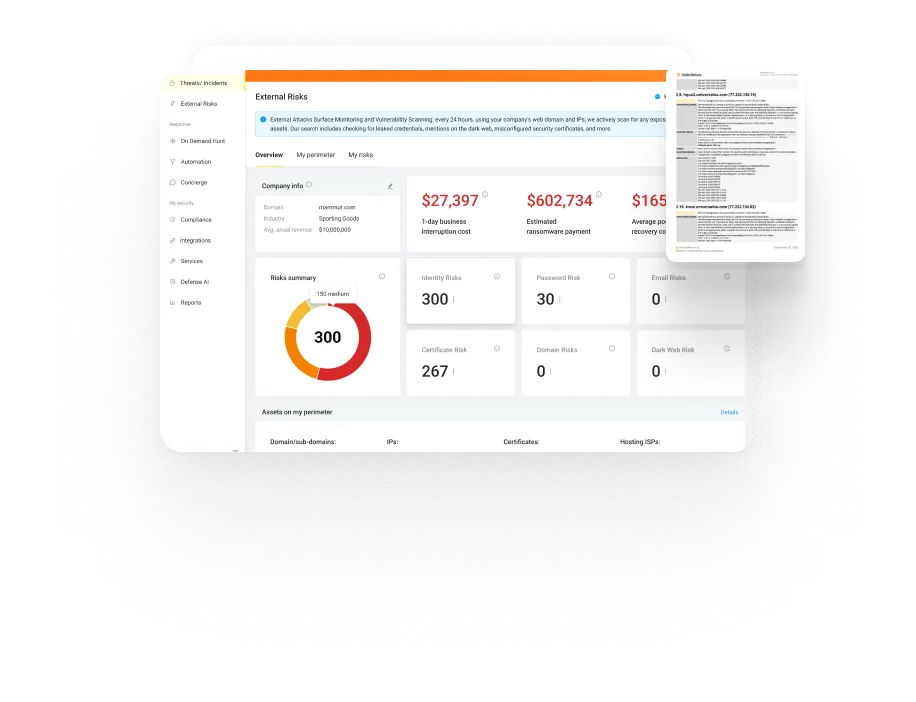
Easy navigation with External Risks Dashboard
There you will find all vital information on your domain: risk summary, estimates of 1-day business interruption, ransomware payment and post-breach recovery cost.
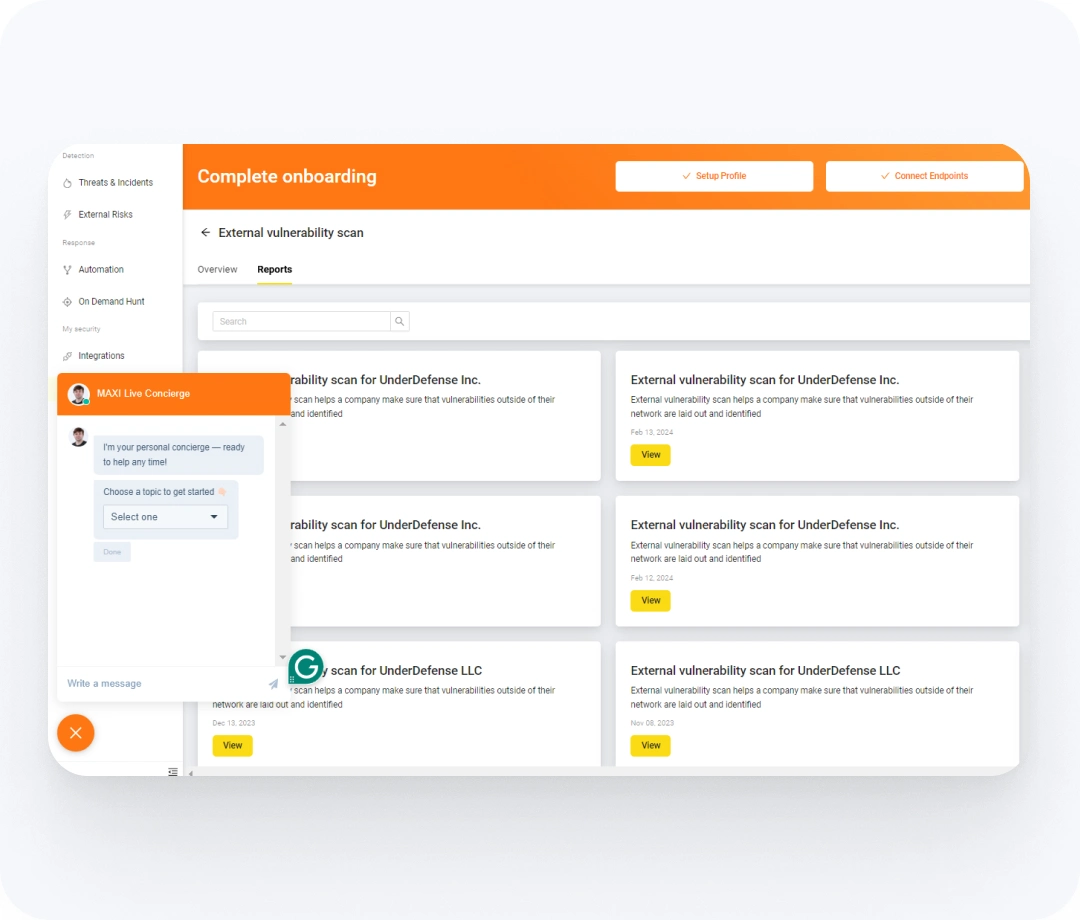
Our Concierge Service is available 24/7 and ready to help with remediation guideline or explain the dashboard indicators.
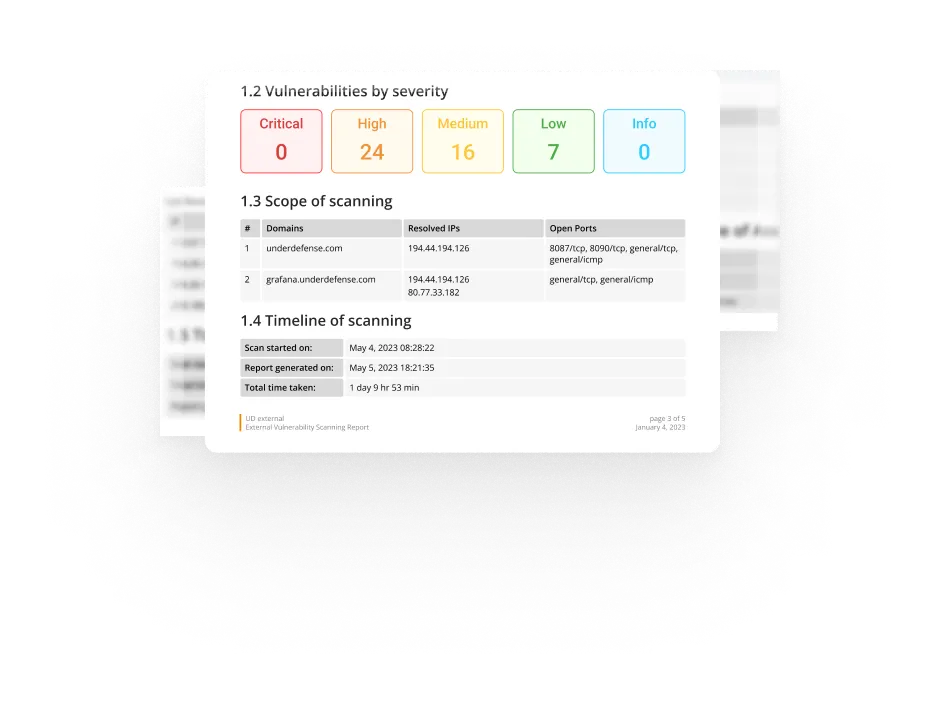
Find your scan results in a comprehensive Report
We deliver a thorough report, so all vulnerabilities are grouped by severity level with remediation guidelines. It equips your IT team with actionable steps and informs C-levels about the actual threats.

Penetration Testing
With UnderDefense goes beyond the reach of regular scans, uncovering potential weaknesses in your infrastructure and system and providing a more comprehensive security picture.
Our ethical hackers simulate real-world attacks to see how vulnerability chains can be exploited to harm your business. After that, we provide expert consulting on remediation to ensure all gaps are patched.
Learn MoreLearn how to automate routine tasks and regularly receive updates on what you need to fix and how.
Scan Now FreeQ1 What is the difference between External Vulnerability Scanning and Penetration Testing?
EVS offers limited research and represents only the first noninvasive step of Penetration Testing. It doesn't uncover complex vulnerabilities or how attackers might use them. Start with Scan for a quick overview, then consider Penetration Testing for deeper assessments or after security incidents.
Q2 What does the external vulnerability scanner service cover?
The scanner covers the following:
- Public-facing assets, specifically up to 10 IP addresses connected to your organization’s domain.
- Vulnerability identification: the scan checks for known misconfigurations and open port weaknesses that bad actors could exploit.
- Severity scoring: vulnerabilities are prioritized based on their potential impact and exploitability, helping you focus on the most critical issues first.
- Basic remediation guidance: You will receive advice on addressing vulnerabilities that have been found.
Q3 Is external vulnerability scanning really free?
Yes, this is considered a basic scan of external assets, allowing you to understand your security posture. We offer paid Penetration Testing, a controlled cyberattack simulation on your networks, as a next step that provides in-depth scanning, detailed reports, and further remediation assistance.
Q4 Will I receive a report afterward?
Yes, after the free cybersecurity risk assessment is done, you will receive a detailed report containing all findings via email. It’s also available in two tabs, ‘Reports’ and ‘Services’ in UnderDefense MAXI, with detailed information, including technical descriptions, scope, risk severity, and timeline.
Q5 What happens after the external scanning?
After the scan, you can choose any of the following approaches:
- Address found vulnerabilities: Use the report to prioritize and patch the identified weaknesses using your internal security resources.
- Consult with our security expert: Seek professional advice and assistance with remediation or further penetration testing.
- Schedule a Penetration Test: Upgrade to a more comprehensive service that allows business owners to assess the hackability of their networks, systems, processes, and people and take the necessary actions to prevent that.