Webinar
Detecting invisible:
passwords stealers on MacOS with blind EDR
Learn how to detect stealthy macOS threats that bypass even the most advanced EDR systems. Join Andrew Hural and elite Threat Hunters to understand:
- Why macOS is not immune to password stealers and account takeovers.
- How attackers exploit stolen credentials to infiltrate systems undetected.
- Practical strategies to detect and mitigate these elusive threats.

Speaker
Recommended for:
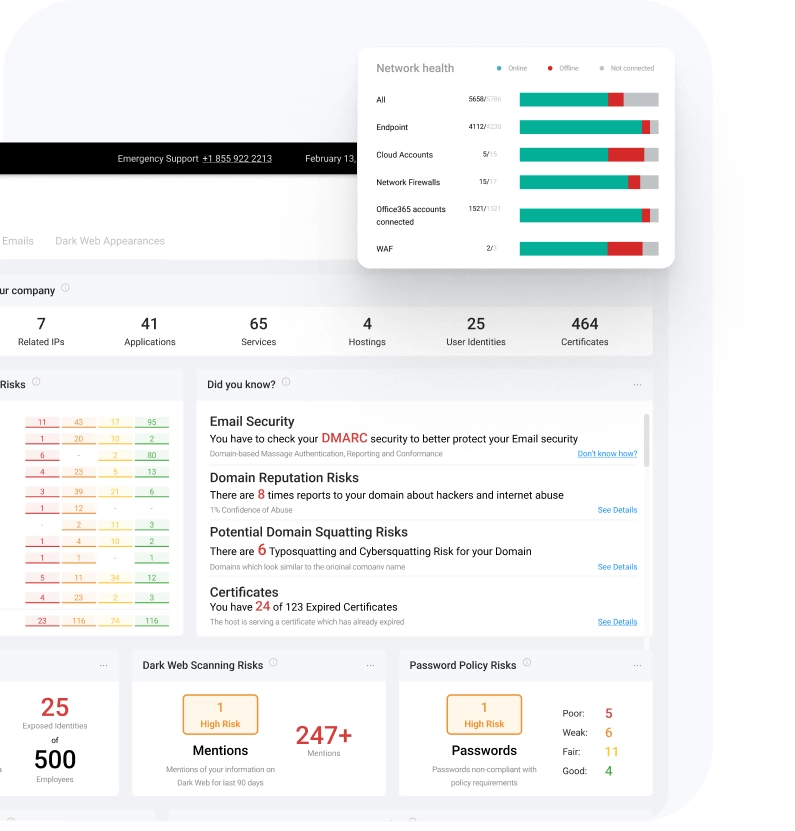
- Check what our SOC team sees and how they are protecting your business against advanced cyberattacks
- Have absolute control over your environment settings
- Use pre-defined or create custom incident response playbooks
- Get expert advice 24/7
- Assess your cybersecurity effectiveness and create informative reports for the management team






