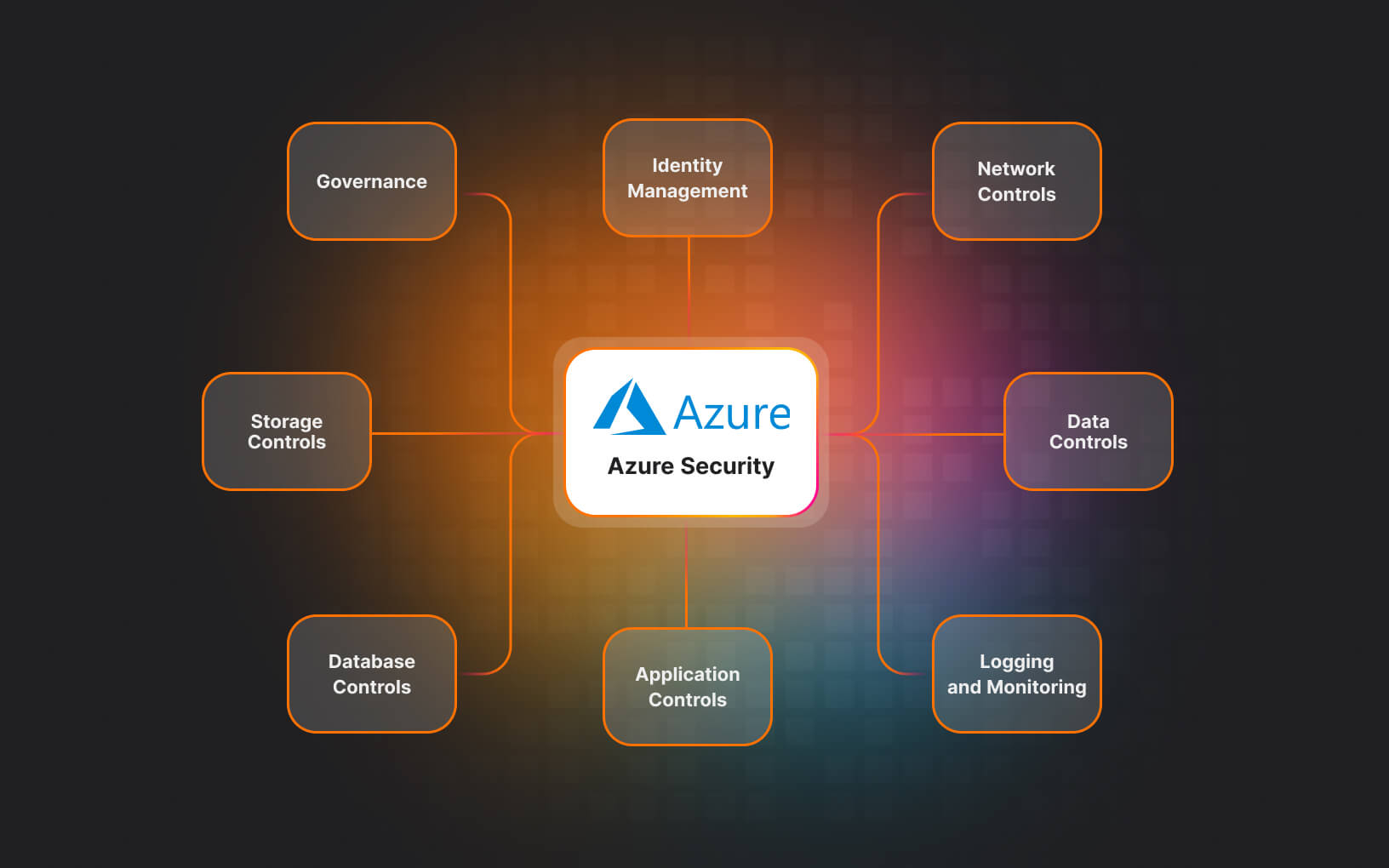
Despite Azure’s impressive features, it’s important to note that it’s still susceptible to hacking, as evidenced by our 80% success rate during pentesting engagements. Our experienced pentesters at UnderDefense have observed that Azure’s complexity can inadvertently create vulnerabilities. However, we still recognize and appreciate Azure’s versatility and strength. Our advice is to remain vigilant, regularly assess for security weaknesses, and promptly address any issues.
Join us as we explore these insights, find solutions, and work together to strengthen our Azure defenses.
Table of Contents
- The most common issues we discovered during real-world hacking exercises
- Lesson #1: Strengthen your gates: the risks of weak password policies
- Lesson #2: Now lock those doors: missing MFA enforcement
- Lesson #3: Quest for guests: managing long-term tenants external access
- Lesson #4: Sharing != Caring (Public M365 groups)
- Lesson #5: Guard the vault: monitor data sharing to protect your assets (sensitive data storage in SharePoint)
- Lesson #6: Keep your access to yourself: protect your users from malicious apps
- Lesson #7: First steps to Zero Trust: Conditional Access Policies
- Lesson #8: Take it with a grain of salt: intune enrollment of non-compliant devices
- Lesson #9: How your past affects your future (support of legacy auth methods that allow MFA bypass)
- Lesson #10: Advanced Azure and M365 protection: active security monitoring through pre-built and custom rules
- UnderDefense MAXI: Simplifying Azure security with comprehensive SECaaS solutions
The most common issues we discovered during real-world hacking exercises
Lesson #1: Strengthen your gates: the risks of weak password policies
Why is it important?
When a company moves from an on-prem Active Directory installation to a Hybrid one, users gain additional functionality and have their passwords synchronized from self-hosted AD to the cloud. However, it also means that any password like “qwerty123 ” is also synchronized, and therefore, anybody with web access can brute force such passwords and gain the initial foothold. The on-prem password policy is migrated to the cloud and overwrites the default Azure complexity policy. Whatever was present in the local network (like six characters, no complexity, and no history) is compelling in the cloud.
Recommendations:
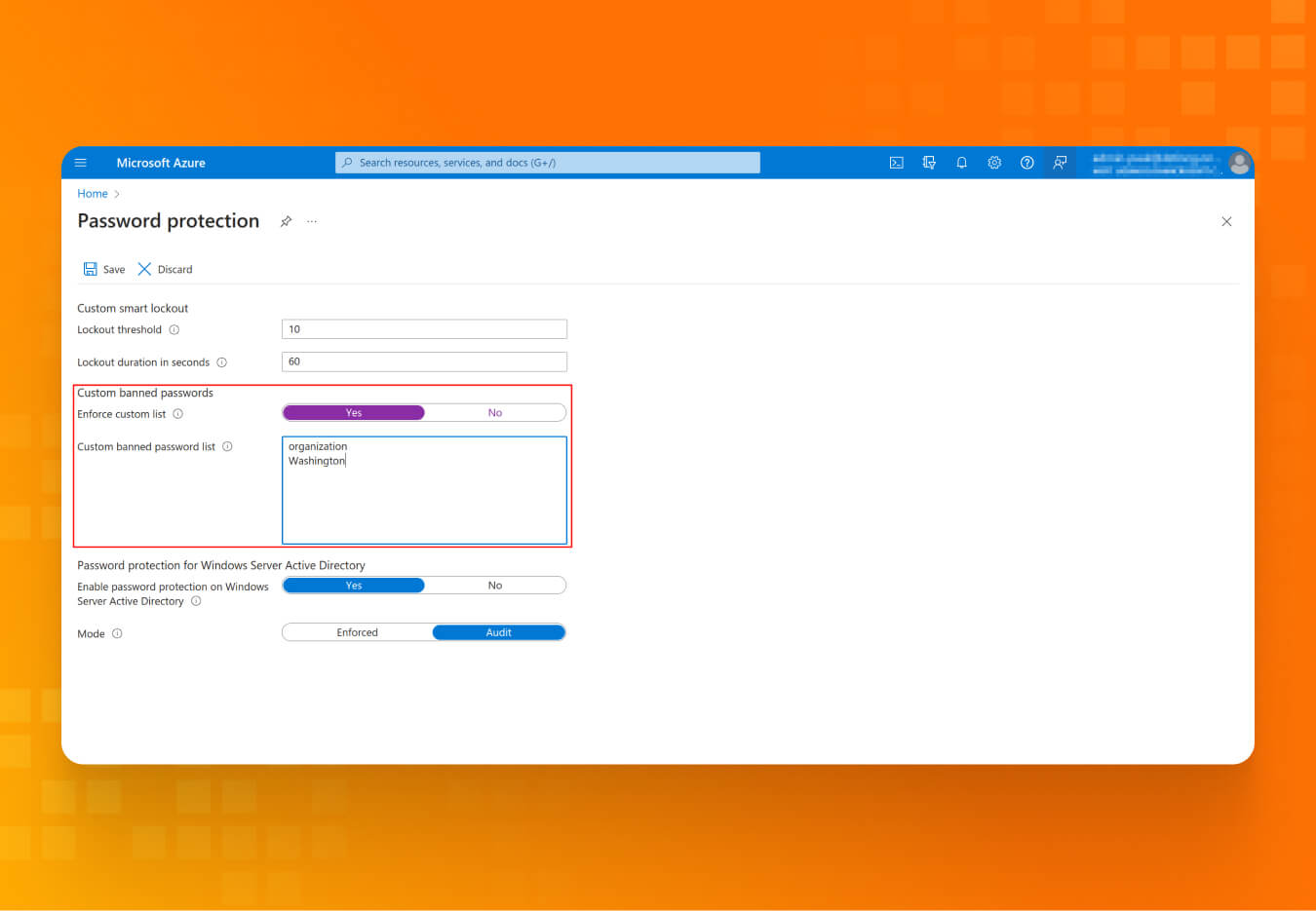
- Configure the on-prem Password Policy on your Domain Controller, as it takes precedence over the Cloud-native Password Policy. Ensure that Complexity and Length settings of at least 14 characters are set.
- To get an audit perspective on users using common words and company names in passwords, you can set a custom list of banned passwords in the “Password protection” menu.
- “Password protection” helps administrators prevent users from using breached or leaked passwords. However, to fully enjoy the benefits of cloud administration and password protection, you must enable the Password Writeback and Self-service password reset settings.
Lesson #2: Now lock those doors: missing MFA enforcement
Why is it important?
Since password leaks are common now and organizations must ensure multi-factor auth policies, enrolling all users to use MFA is beneficial. Although some MFA methods are safer than others, using at least some 2-step verification is still helpful to prevent simple brute-forcing attacks.
Recommendations:
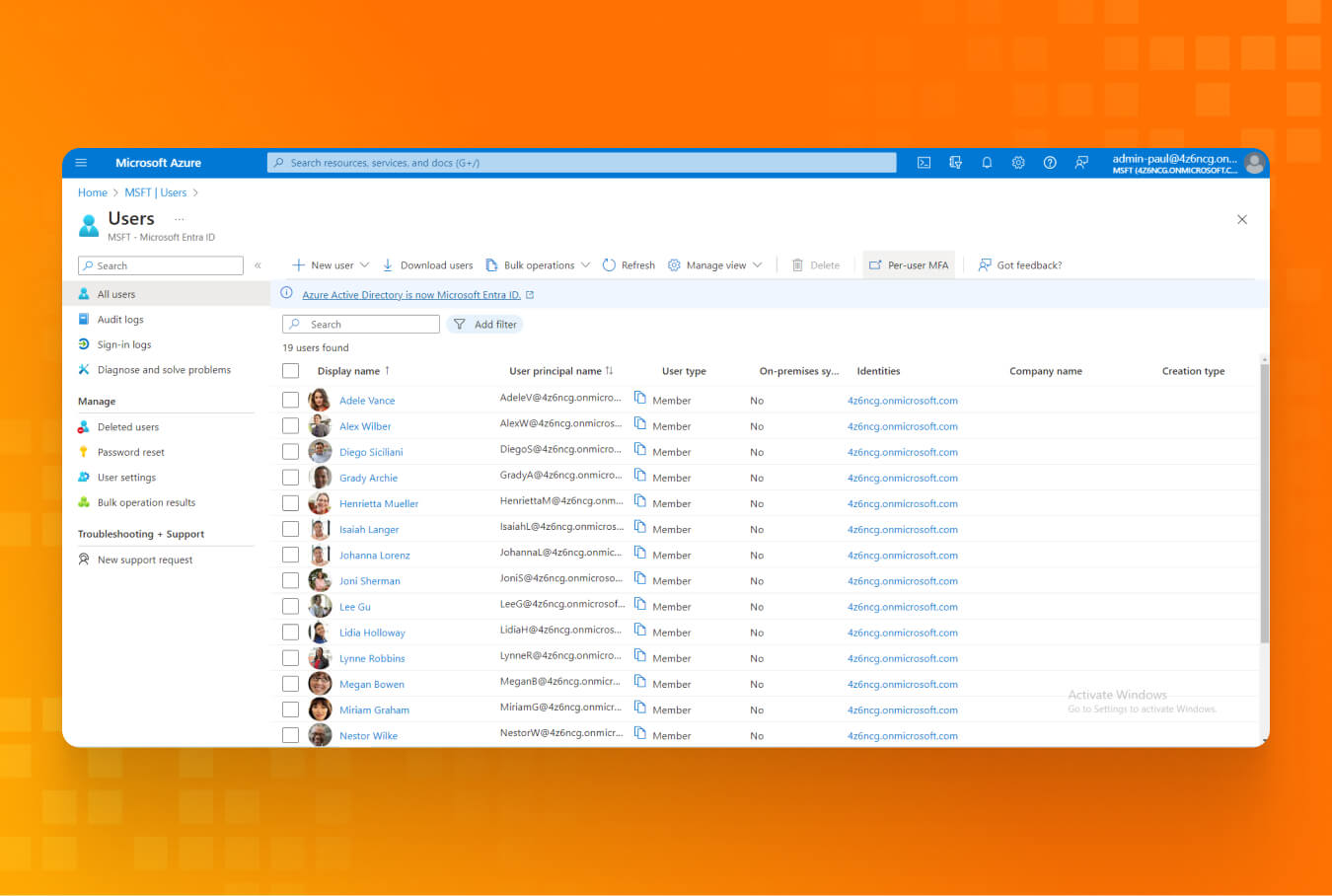
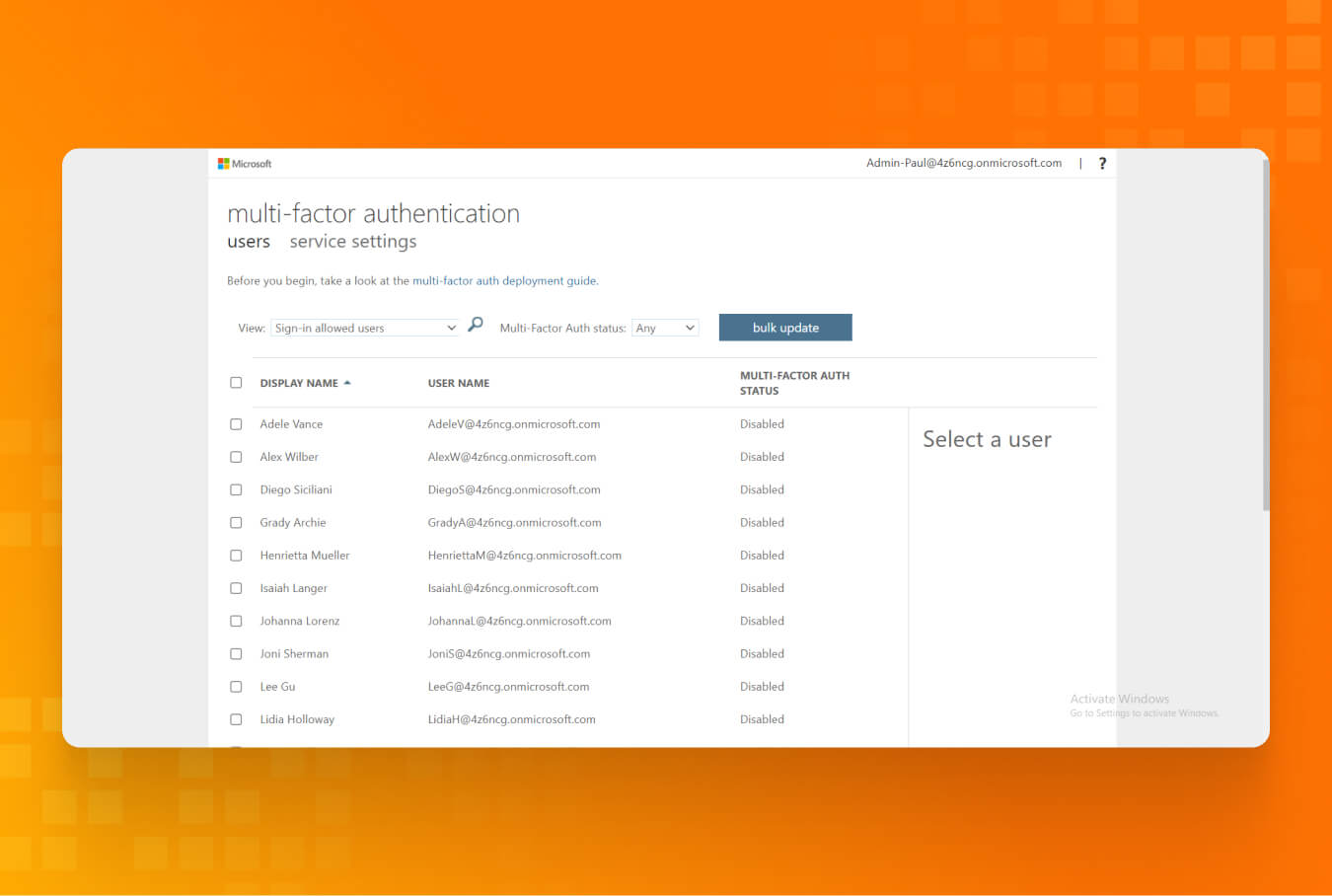
- Browse the “Users” blade in Entra ID and select “Per-user MFA” in the top-right corner.
- After that, you will be redirected to view all your users. This way, you can enroll all of them to use MFA.
- Use Conditional Access Policies (recommended by Microsoft way) to automate this enrollment process.
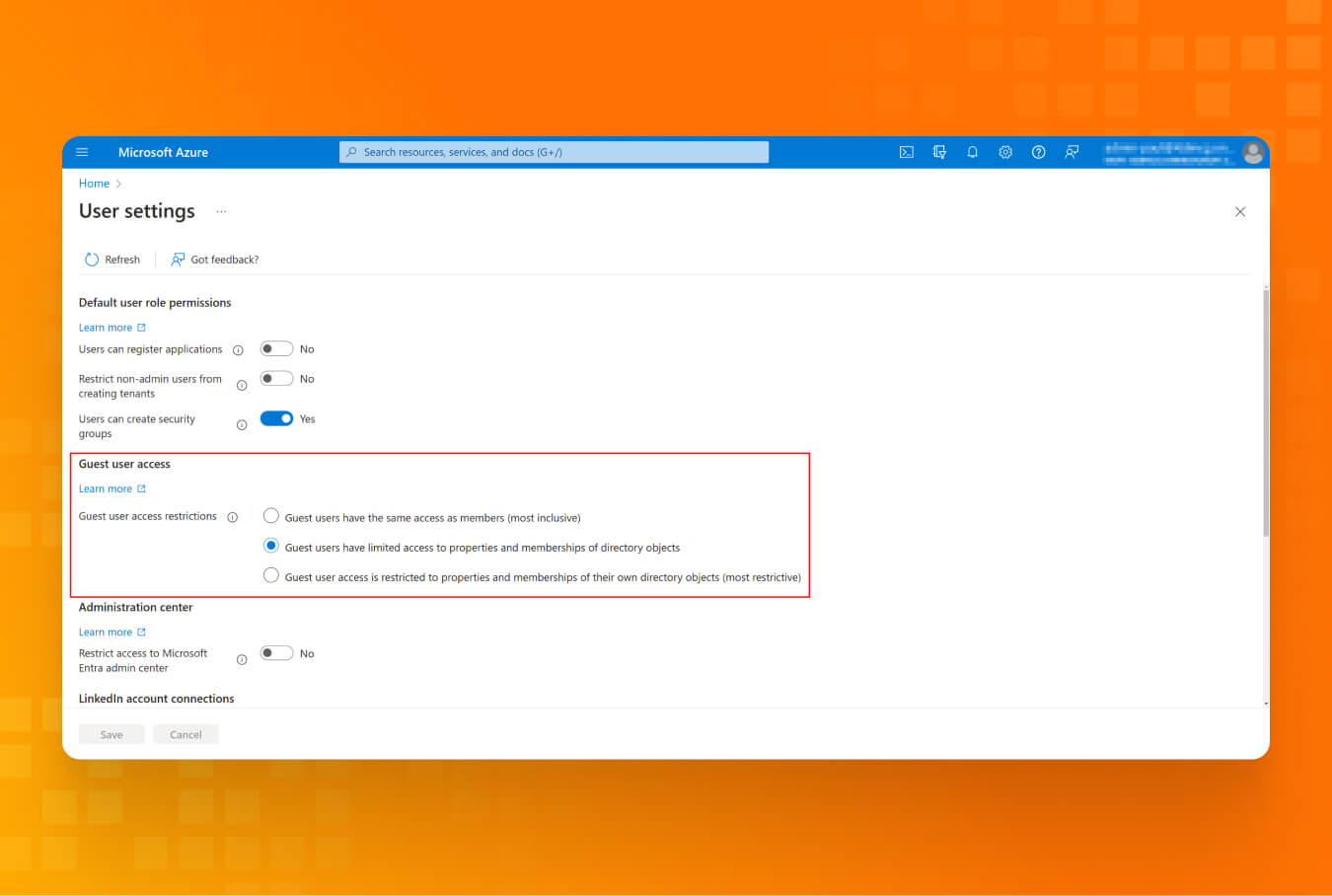
Lesson #3: Quest for guests: managing long-term tenants external access
Why is it important?
When dealing with third-party contractors and wanting all communication in Teams, you are likely adding them as guest users to your Teams channel. However, guest users can write in your MS Teams channel and enumerate users in your tenant. Default settings allow guest users to use MS Graph API to get the group’s membership by username and members of those groups. Therefore, the chain is repeatedly abused from group enumeration to user enumeration.
Recommendations:
- Review guest users present in the tenant once a month and delete accounts if they are no longer needed. (Azure CIS compliance)
- To limit access of guest-level users, select the most restrictive option in the “User settings” menu. This way, you can still add guest users to your tenant, but they won’t be able to enumerate all tenant users and groups.
- Optionally, you can create an “Access Review” for one month and send it to relevant administrators for review.
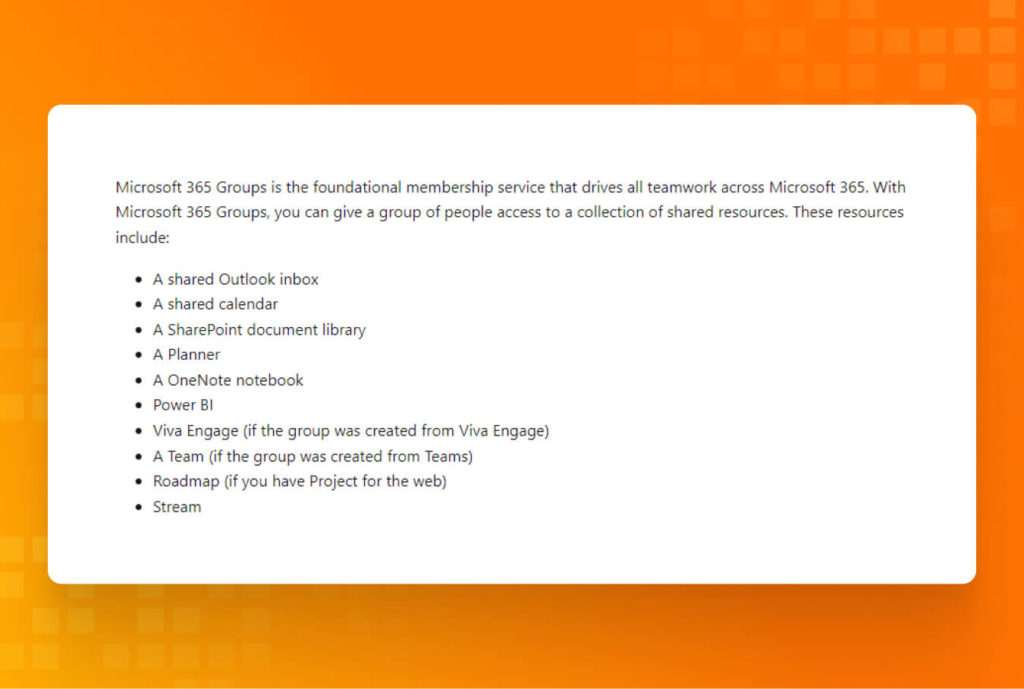
Lesson #4: Sharing != Caring (Public M365 groups)
Why is it important?
Microsoft Azure Entra ID has two group types: Security and M365. By default, when creating a M365 group, there is an option to make it public or private, public being the default value. In Microsoft’s understanding, the public is any user of the same organization who can access data shared in such a group, either stored in SharePoint or shared Outlook email. Thus, when an M365 group, let’s say for accountants, is created, anybody in the tenant can access all shared data, starting from emails and ending with sensitive files attached to those emails.
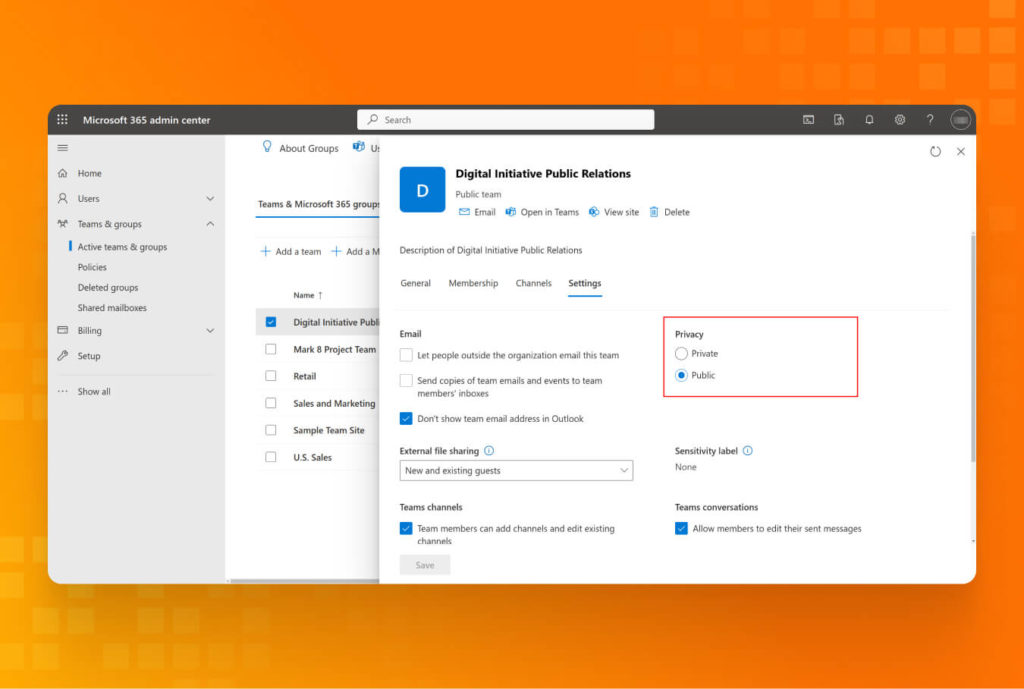
Recommendations:
- To change group privacy settings, go to Microsoft Admin Center on the web
- Under “Teams & groups,” you will find the “Active teams & groups” submenu. There, you can adjust privacy from Public to Private.
Lesson #5: Guard the vault: monitor data sharing to protect your assets (sensitive data storage in SharePoint)
Why is it important?
When performing penetration testing in the Azure environment, we often deal with enormous amounts of files stored in SharePoint. And since we are limited in time and mainly interested in sensitive business data, PII, passwords, and pre-defined objectives, we can use the built-in search function to process files quickly. SharePoint has an excellent OCR (Optical Character Recognition), which significantly helps with screenshots and photos of employees’ desks. Therefore, we can search not only in text files but in pictures too.
Recommendations:
- Regulate the entire employee life cycle. Create a workbook with clearly defined internal procedures for granting access to new employees and revoking it when an individual leaves. Communicate that to the staff and ensure strict adherence to the rules. Documented procedures are among the most critical elements of your Entra ID and Microsoft 365 security checklist.
- Ensure that the principle of least privilege is enforced. Such an approach guarantees that users get only the permissions necessary for their specific roles. It minimizes the risk of unauthorized access to sensitive data and its sharing.
- Also, we recommend configuring Microsoft’s built-in DLP solution.
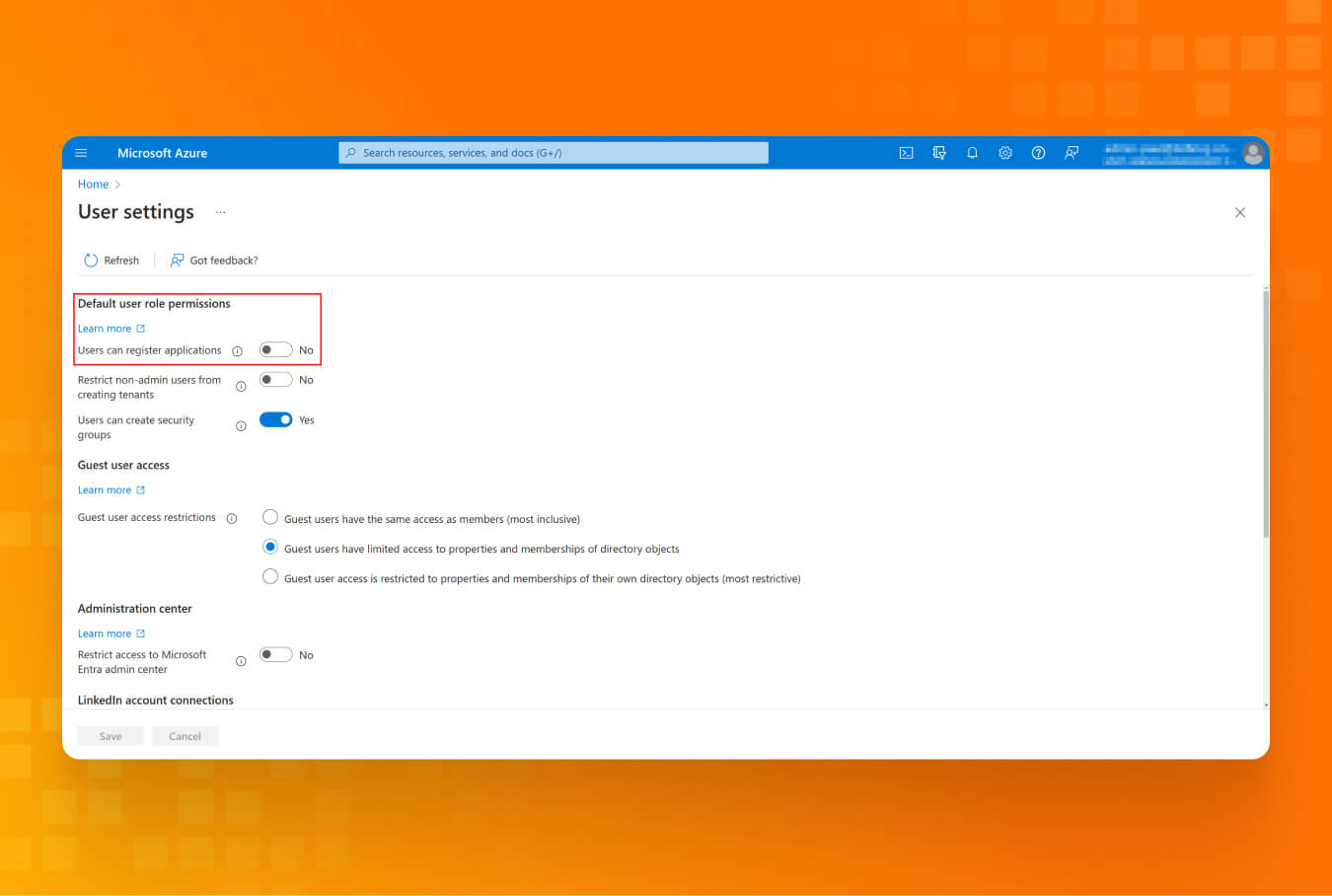
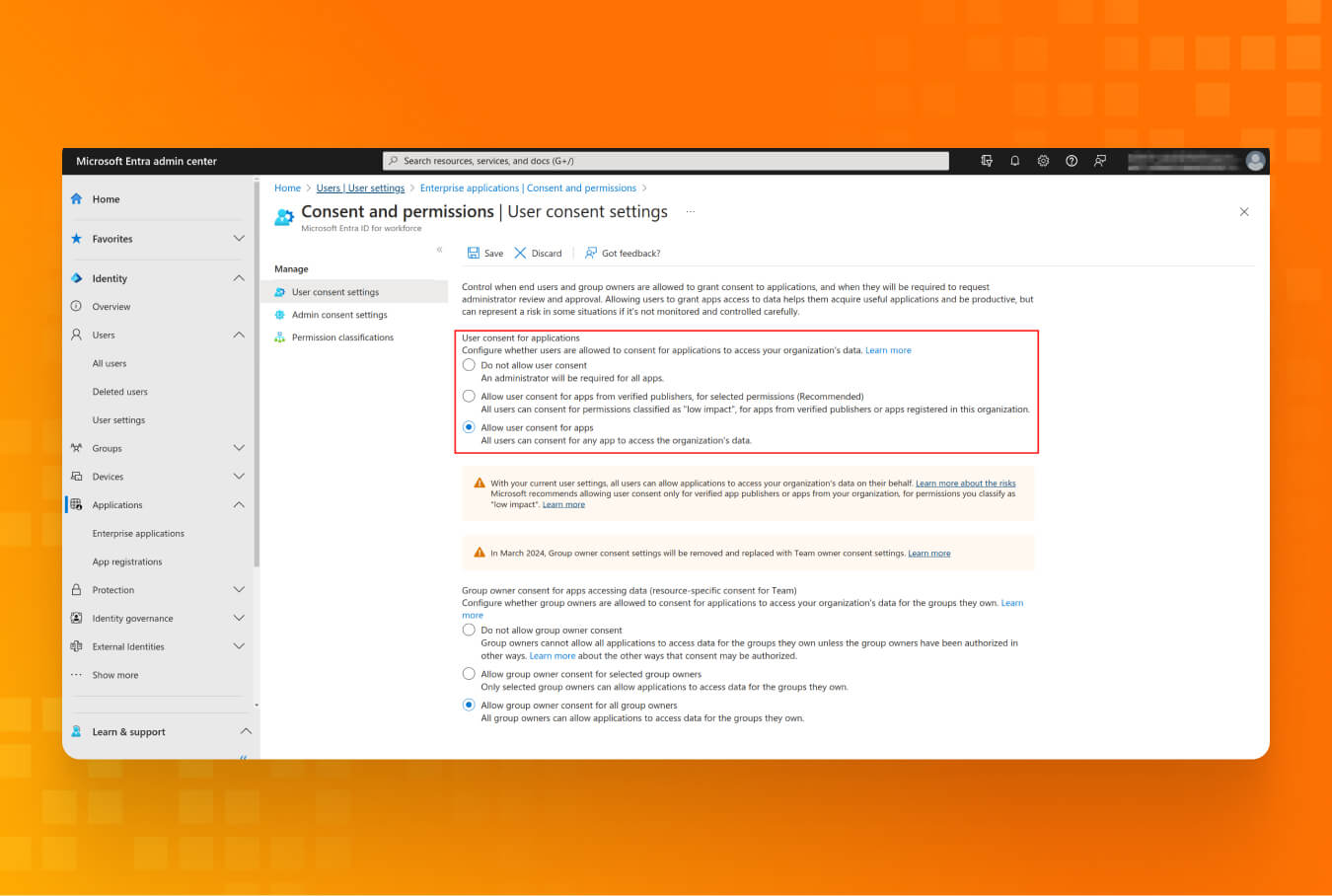
Lesson #6: Keep your access to yourself: protect your users from malicious apps
Why is it important?
The user consent setting allows users to select what apps they can enroll in and whether the admin has to approve those applications. Azure/Entra ID application can use granted access with a Service Principal account, so if the application is granted permission to read and write to mail, it can easily be abused to run a phishing campaign. That’s why it’s better to limit the application used by the tenant.
Recommendations:
- Under “User Settings,” remove permission for users to register applications.
- Go to the “Applications” blade in the Microsoft Entra admin center. Under Consent, settings select either “Allow user consent for apps from verified publishers” or “Do not allow user consent” (the most restrictive option).
- Optionally, you can set up an Admin Consent workflow. It will ensure that any time a user tries to grant access that requires admin approval, the administrator is notified and can decide whether or not to grant that permission.
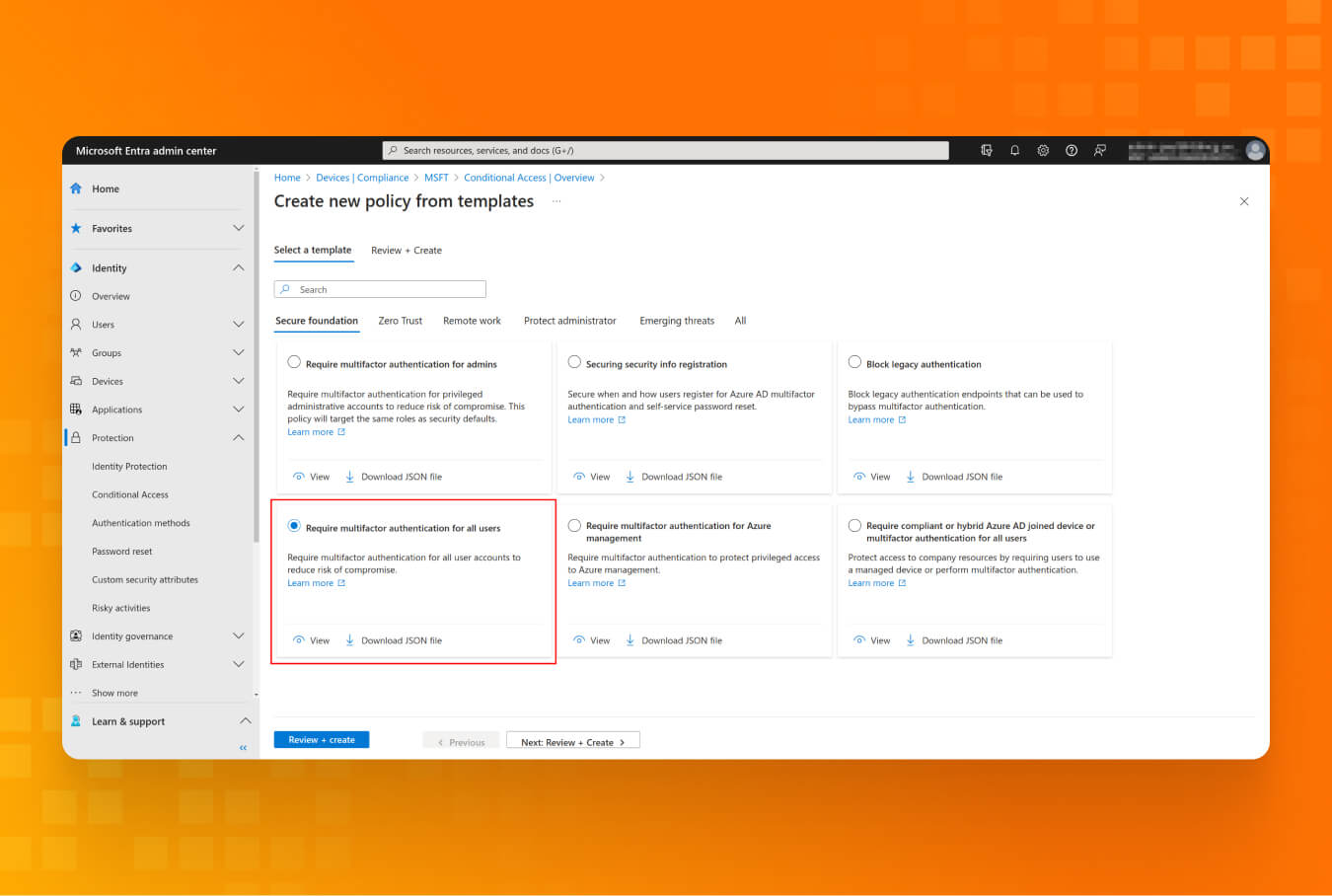
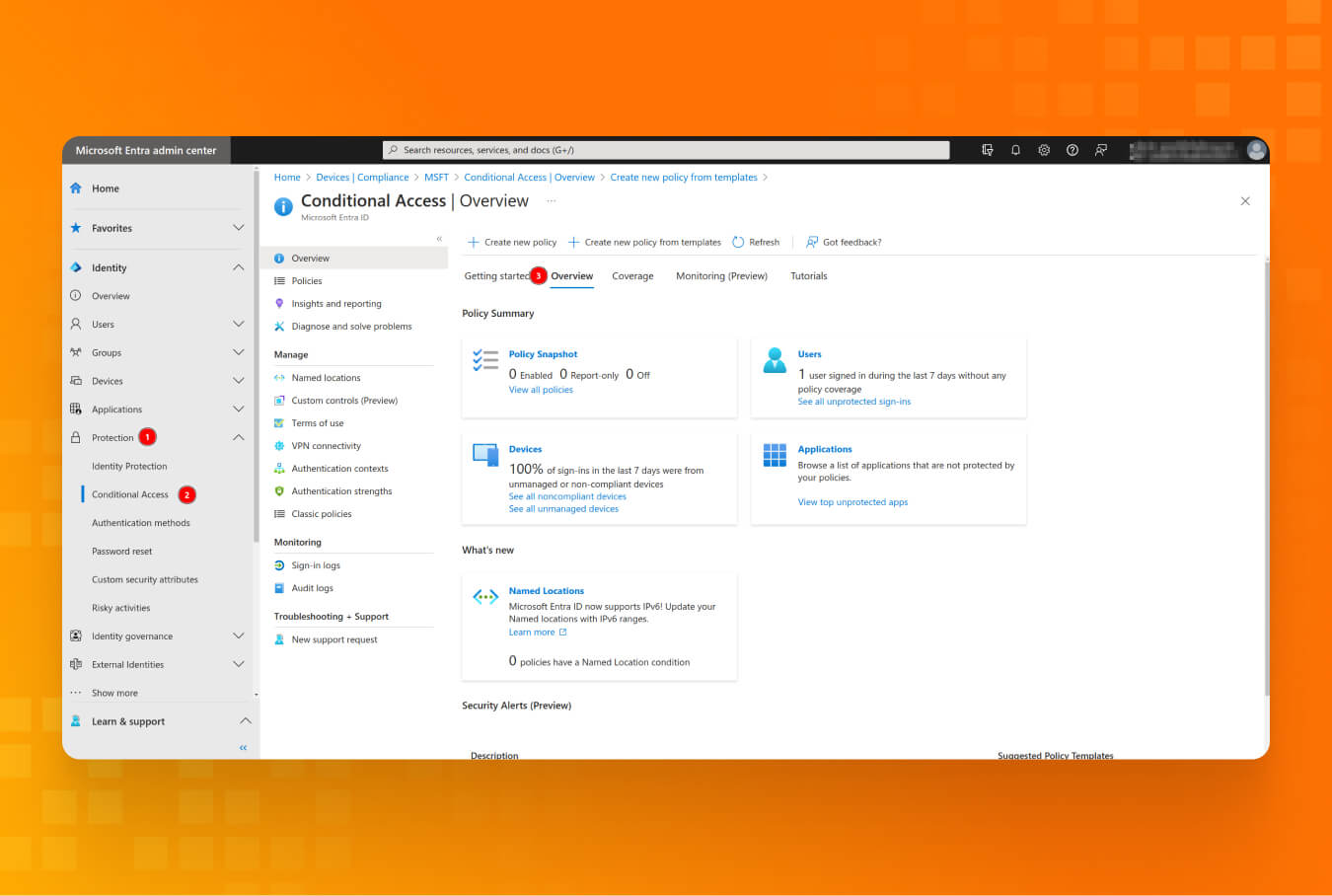
Lesson #7: First steps to Zero Trust: Conditional Access Policies
Why is it important?
Essentially, CA Policies are if-then statements that help to protect certain parts of your infrastructure. For example, using the CA Policy, you can require trusted locations for security information registration, ensuring that organization-managed devices are used for specific applications. However, CA Policies can also introduce a way for the attacker to exploit your environment. Let’s say the admin might’ve created a conditional access policy that checks for trusted office IP addresses, and if that matches, the MFA check is skipped. Using that knowledge, attackers may persist in the network using only the usernames and passwords of compromised users and not having to enroll any MFA devices.
Recommendations:
- Review the CA Policies in the Microsoft Entra admin center to ensure they meet security best practices and your organization’s needs.
- Start with report-only mode if you want to implement a new policy from the template or self-written. It will show any gaps or overlaps that may impact your business workflow.
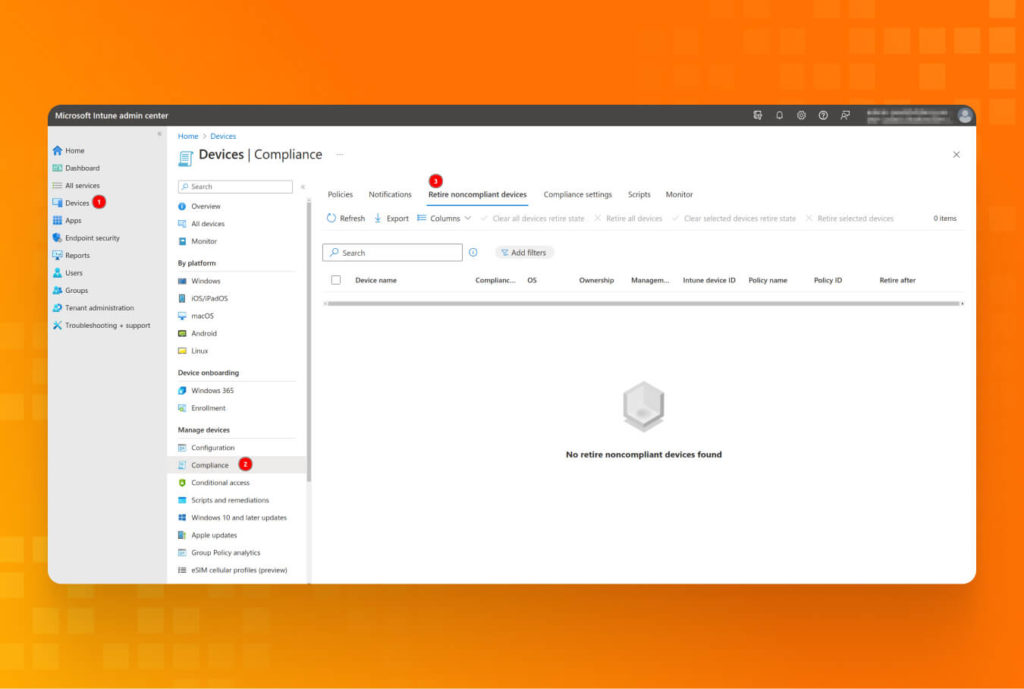
Lesson #8: Take it with a grain of salt: intune enrollment of non-compliant devices
Why is it important?
Suppose the device is not compliant (for example, it has outdated Windows, improper tooling installed, etc.). In that case, it should be assumed to be compromised and not trusted (as should all related user credentials).
Recommendations:
- Constantly monitor for any non-compliant device in the tenant.
- Choose from Microsoft-approved options:
- Send a notification email to the end user about the device status and what your organization proposes to do to remediate the issue.
- Remotely lock the noncompliant device. It prompts the user to enter the PIN or password, but the device will remain noncompliant.
- The best solution is to retire the device:`Add device to retire list: When this action is performed on a device, the device is added to a list of retired, noncompliant devices in the Intune admin center. Go to Devices > Compliance and select the Retire noncompliant devices tab to view the list. However, the device isn’t retired until an administrator explicitly initiates the retirement process. When an admin retires the device from that list, retirement removes all company data off the device and removes that device from Intune management.`
Lesson #9: How your past affects your future (support of legacy auth methods that allow MFA bypass)
Why is it important?
If your organization has a long history with Azure services and has SMTP enabled, be aware that this protocol doesn’t have any way to validate a user’s MFA and bypasses it completely. This legacy auth, combined with the attacker’s ability to brute force or gain credentials in some other way, can lead to an initial foothold in your tenant. Starting on October 1, 2022, Microsoft began to disable Basic Authentication and form legacy methods permanently, and only SMTP is still present.
Recommendations:
Depending on the readiness of your organization to give up on using legacy auth methods, you can choose one of two options:
- Indirectly block legacy authentication: Given that Microsoft Entra ID applies policies with grant controls to all client applications so that legacy authentication-based sign-ins that can’t satisfy the grant controls are blocked. So, it gets blocked because legacy auth doesn’t support sending MFA, device compliance, or join state information to Microsoft Entra ID.
- Directly block legacy authentication: Under the Microsoft Entra admin center, you can find the “Protection” blade and create new Conditional Access Policies from the template or self-written.
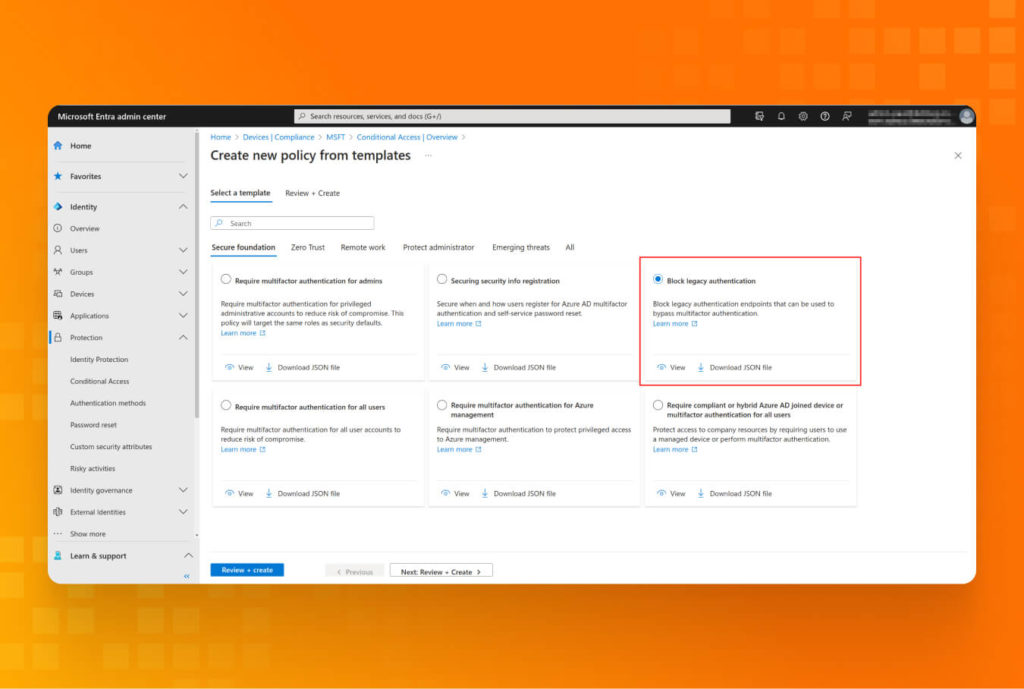
Lesson #10: Advanced Azure and M365 protection: active security monitoring through pre-built and custom rules
Why is it important?
Learning the previous nine lessons from the provided security checklist and following the recommendations will help you proactively protect the Azure environment against various threats. However, if you want to take security to the industry’s best practices and shift to a proactive mode, you’ll benefit from learning another advanced-level lesson.
Azure Entra ID offers numerous prebuilt security rules, settings, and default combinations that cover a wide range of security scenarios and can complement existing monitoring processes in your environment. By using them, you’ll benefit from a completely different level of protection that helps control the overall activity in your Azure environment, detect potential threats, and mitigate them as quickly as possible. Sounds great, right?
But that’s not all. Creating and implementing custom rules based on audit logs can provide additional Azure data security benefits. This approach can help you monitor more advanced cases and respond quickly to more complicated threats.
Recommendations:
- Require administrators to do multifactor authentication. Privileged accounts should always be protected first.
- Require all users to register for multifactor authentication, thus ensuring that brute force attacks won’t be successful.
- Require users to do multifactor authentication when necessary by using Conditional Access Policies and making life easier.
- Block legacy authentication protocols to minimize the risk of MFA bypass that might take place.
- Protect privileged activities like access to the Azure portal. You can even prompt users to reauthenticate for high-risk actions; this way, you ensure that an attacker cannot change the environment even after a successful phishing attempt and token stealing.
- Utilize a SIEM solution, or UnderDefense managed SIEM service to track alerts and logs consistently and constantly with state-of-the-art detection rules.
UnderDefense MAXI: Simplifying Azure security with comprehensive SECaaS solutions
Need help securing your Azure environment?
At UnderDefense, we’ve experienced the challenges of securing Azure environments firsthand. That’s why we developed UnderDefense MAXI, our comprehensive solution tailored to your Azure security needs. Our team of seasoned security professionals brings deep Azure expertise, providing round-the-clock threat detection and response to keep your environment safe. With UnderDefense MAXI and our dedicated security specialists, you can confidently navigate Azure security complexities, protecting your valuable data and applications around the clock.
In addition to the UnderDefense MAXI platform, we offer various services to address multiple cybersecurity needs for Azure customers:
- Managed Detection and Response (MDR) for Azure: UnderDefense offers turnkey MDR solutions tailored for Azure, ensuring 24/7 monitoring of your digital environment. Our expert team watches over your systems, quickly identifying and neutralizing any suspicious activity to mitigate potential threats immediately.
- Managed SIEM: We seamlessly integrate SIEM solutions with your infrastructure, granting real-time visibility into your security landscape. At UnderDefense, we particularly favor Azure Sentinel as our SIEM choice, given its native integration with Azure’s security infrastructure. Leveraging Azure Sentinel and our automation capabilities strengthens incident response for customer IT teams, enabling proactive threat detection and timely, effective responses.
- Managed Azure-based SOC: UnderDefense delivers managed SOC services, offering continuous monitoring, threat detection, and incident response for cloud-native environments. Our dedicated SOC team works tirelessly to safeguard your digital assets and ensure rapid response to emerging threats.
- Penetration Testing and Hack-testing your Azure deployment: Our penetration testing services simulate real-world cyberattacks to identify vulnerabilities and weaknesses within your systems. Conducting thorough assessments, we help you bolster your defenses and enhance your overall security posture.
- Incident Response in the Azure cloud: In the event of a security incident, UnderDefense provides rapid incident response services, minimizing the impact and quickly restoring normal operations. Our experienced incident response team guides you through the mitigation process, ensuring minimal disruption to your business.
- Azure Security Monitoring: We offer comprehensive cloud security monitoring services, specializing in platforms like Microsoft Azure, AWS, and GCP.
- Compliance Services: UnderDefense simplifies the complex compliance process by offering tailored services and consulting. Whether it’s SOC2, ISO 27001, or industry-specific regulations, our experts ensure you meet all obligations while maintaining robust security practices.
Author: Pavlo Fedorenko
Penetration Tester at UnderDefense