For today’s organizations, a robust Security Operations Center (SOC) is no longer a luxury but a necessity. In the face of escalating cyber threats and an expanding attack surface, the need for 24/7 vigilance and proactive defense has never been greater.
And we have experts and tools ready
Statistics paint a dark picture: a 2023 report by IBM found that the average cost of a data breach reached a record high of $4.45 million, while Verizon’s Data Breach Investigations Report examined 23,896 incidents and 5,212 confirmed security breaches in 2022 alone.
But when it comes to building your SOC, a crucial question arises: in-house or outsourced? While both options offer distinct advantages, the decision isn’t always clear-cut. Budgetary constraints, talent acquisition challenges, and evolving threats paint a complex landscape, leaving many businesses navigating a labyrinth of options.
This article will navigate you through the topic and dig into the merits of in-house and outsourced SOC options, equipping you with the knowledge to make the right decision.
Challenges of building an in-house SOC
Our first article on building a SOC focused on the main steps you need to take and the basic requirements for small and mid-sized businesses. Now, we will dig deeper into this topic, starting with the list of challenges you might face by deciding to build an in-house security hub. After that, we will discuss the cost of SOC to start its operation and keep it going.
So, there are three main challenges that make building your own SOC tough:
- Resource constraints
- Talent acquisition and retention: Hiring and keeping skilled cybersecurity professionals is costly and competitive, especially for smaller organizations. Also, recruiting takes a lot of time to find the right people with the right skills.
- Budget limitations: Building and maintaining an effective SOC requires significant technological, staffing, and training investments. The budget and annual salary may vary depending on your company’s and staff’s geographical location. We have learned that the usual staff turnover rate is about two years, which puts additional strain on the company.
- Scalability: SOCs can struggle to adapt to sudden spikes in workload or evolving threats, requiring additional resources and planning. It also cannot expand as fast as a company because of talent shortage in the market.
- Operational challenges
- Alert fatigue: SOC analysts can be overwhelmed by the sheer volume of security alerts, which leads to missed threats or delayed responses. Every breach requires additional modifications or reconfigurations in procedures, which takes a toll on staff and causes exhaustion.
- 🞄 False positives: Filtering false positives from real threats is time-consuming and resource-intensive. The time wasted on verifying false threats adds up to operational costs.
- Integration issues: Integrating different security tools and data sources is complex and requires specialized expertise. You need to hire a professional with the knowledge and experience to build a well-functioning security infrastructure where every component is completing each other.
- Organizational challenges
- Compliance requirements: Meeting industry regulations and compliance standards adds additional complexity and workload.
- Limited information sharing: Information sharing and collaboration between IT, security, and other departments can be hampered by siloed structures.
- Metrics and reporting: Measuring the effectiveness of an in-house SOC and demonstrating its ROI is difficult. The value needs to be clearly articulated through regular reports.

While an in-house SOC offers potential customization and tailoring strictly to your business objectives, the long list of challenges can be intimidating. From recruiting skilled analysts to managing ever-evolving threats, the endeavor can quickly overwhelm internal resources. Let’s discuss another important matter – the budget costs of keeping SOC running.
Calculating your SOC costs
Understandably, it’s hard to underestimate the mentioned challenges you face once you come to the decision to build a SOC. Also, there is even more to that. We have prepared a breakdown of the annual expenses SOC requires. A good ballpark figure would be $1,950,000 for a mid-sized organization, including:
- $850,000 for security tools like endpoint protection, Cloud SIEM, and a log management solution.
- $950,000 for full-time employees’ compensation.
- $150,000 for operational expenses, including implementing and maintaining a hub.

However, every business has additional needs depending on the industry requirements, the size of the attack surface, the number of endpoints, and the expected level of protection. Only security experts, after a thorough assessment, can give you a more precise figure.
The ultimate goal is to build both operationally and cost-effective internal SOC, and as we see, there are a lot of factors to weigh in. Finally, you must compare the time and money investment you are ready to make with the level of SOC your organization needs. Hiring an experienced vendor that offers SOC-as-a-Service can be the best solution for small or mid-size companies and enterprises.
Expanding or augmenting your SOC
What does make one SOC stand out among the others? The first thing that comes to mind is the maturity level. Imagine a ladder leading to peak cybersecurity awareness. Each rung on this ladder represents a maturity level, marking the SOC’s capability to identify, analyze, and address threats. These levels offer a framework for self-assessment and, crucially, choosing the right security partner.
There are primarily five maturity levels:
- Security Perimeter: Basic security measures with reactive incident response.
- SIEM/Data Lake Migration: Basic detection capabilities and incident response plans.
- Security Automation: Proactive monitoring and basic threat hunting alongside improved incident response.
- Advanced Analytics: Advanced threat detection, automation, and threat hunting with well-defined processes and continuous improvement.
- Predictive analytics: Fully optimized SOC with mature threat hunting, intelligence-driven security, and proactive engagement against advanced threats.
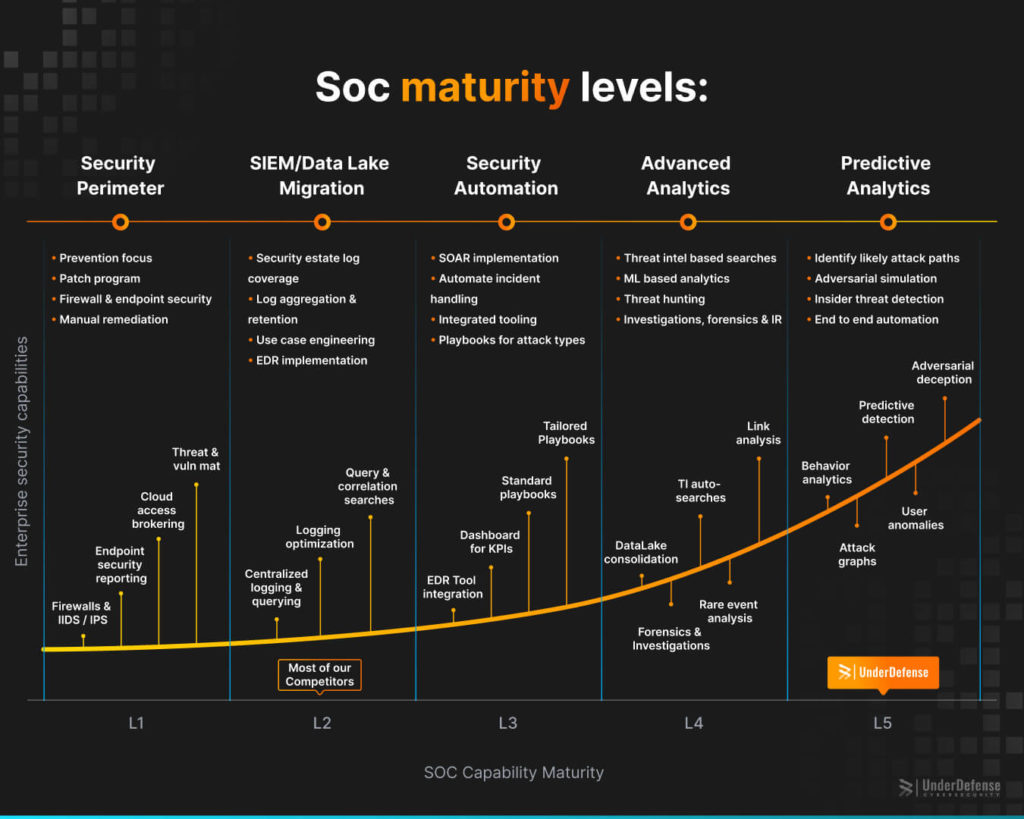
Imagine hiring a team of highly trained security professionals operating at the pinnacle of cybersecurity expertise. That’s what choosing a Level 5 SOC like UnderDefense offers. It took us six years, with 110 people, to reach L5, and it was a tough journey.
By outsourcing SOC responsibilities to a Level 5 SOC by UnderDefense, you ascend the maturity ladder, achieving a proactive and resilient security posture. Think of it as having a team of elite cybersecurity warriors guarding your digital assets 24/7.
Recognizing that different organizations face varying threats, we provide alternatives for more customized, scalable approaches to SOC as a Service. Whether you need a fully managed SOC, an extension to your in-house team, or a hybrid solution, we tailor our services to fit your specific needs.
We also can empower your cybersecurity defenses by acting as your internal SOC 24/7. We seamlessly integrate with your operations, leveraging the robust capabilities of the UnderDefense MAXI MDR platform. We identify and mitigate risks in real-time, minimizing the impact on your organization. Count on us not only as your SOC but as a partner in elevating your defense mechanisms.
Even the most seasoned SOC teams face limitations. Alert fatigue, resource constraints, and evolving threats can strain their ability to provide comprehensive security. This is where augmenting your SOC with UnderDefense MAXI comes in.
Think of your SOC as a security team. Now, imagine adding:
- Tier 1 SOC analysts: the UnderDefense MAXI platform filters through alerts, highlighting only true threats and minimizing fatigue. Your team stays fresh and focused.
- Advanced threat hunters: UnderDefense experts actively hunt sophisticated attacks, uncovering those that might slip past your existing defenses.
- 24/7 coverage: Never miss a critical event, even when your internal team is off-duty.
- Expertise on demand: Tap into UnderDefense’s knowledge and experience to bolster your team’s capabilities.
But don’t just take our word for it. Consider the following ROI:
- Reduced downtime from breaches.
- Lowered fines and compliance costs.
- More efficient resource allocation.
Augmenting your SOC isn’t a luxury, it’s an investment in the future of your security. With UnderDefense MAXI, you gain the edge you need to stay ahead of ever-evolving threats.
Navigating the complex world of security isn’t easy, especially when it comes to Managed SOC. Remember, a robust security posture is attainable, regardless of your expertise. By seeking guidance and exploring options, with UnderDefense as your partner, the journey toward robust security becomes simpler, smoother, and, ultimately, more successful.
Usually, vendors offer SOC as a stand-alone service or as a part of a package that can be integrated into your security stack. In other words, you can avoid lacking human resources, limited budget, misconfigured tools, and excess false positives. Let’s see the main advantages of Managed Detection and Response (MDR) in the example of UnderDefense.
Buy our MDR solution to ensure business security, resilience, and compliance without spending a fortune
UnderDefense MDR as a complex solution
Certain capabilities of MDR and SOC are overlapping, especially in terms of threat hunting, monitoring, and response. But, when you are in a position to weigh in budget and time options with the desirable results, not even mention challenges along the way, an experienced vendor can be the right choice. And here comes various market options, where it is really important to choose solutions with a suitable maturity level and a provable track record of wins.
MDR by UnderDefense has not only the features we mentioned but also means opting for a reliable, innovative, and client-focused SecOps partner dedicated to fortifying your digital defenses effectively. In this case, a SOC is the piece of the complex mechanism, which is MDR, and by signing up for it, you get in return full security coverage.
What makes UnderDefense MDR special and mostly valuable:
- Comprehensive coverage.
Unlike a traditional MSSP focused on specific areas, UnderDefense offers a holistic approach. We provide end-to-end coverage, from proactive threat hunting to 24/7 monitoring, ensuring that every aspect of your digital landscape is safeguarded. - Proactive threat detection.
UnderDefense goes beyond reactive measures. We actively search for the proverbial “needle in the haystack” using a combination of AI technology and expert analysis to identify potential threats before they escalate. - Tailored approach to attack types.
Recognizing that different organizations face varying threats, we provide alternatives for more customized, scalable approaches to SOC. Whether you need a fully managed SOC, an extension to your in-house team, or a hybrid solution, we tailor our services to fit your specific needs. - Increased awareness of the cost of inaction.
Many organizations invest in cutting-edge tools but struggle with routine tasks, leading to gaps in security. Our services address this by taking on the routine, allowing your team to focus on strategic initiatives. - Mastered tools integration process.
Our team excels in integrating seamlessly with your existing security stack. We transform disparate tools into a harmonious orchestra, creating a unified defense that eliminates siloed data and prevents missed threats. - Incident response excellence.
Our incident response capabilities are unparalleled. We take on the heavy lifting, ensuring that your security team can focus on high-impact work that drives the business forward. Our approach also includes proactive incident response planning and tabletop exercises. - Identity-focused security.
Understanding the critical role of employees in security, we integrate with communication platforms like Slack and Teams to provide real-time notifications to your staff. It ensures that employees are informed and empowered to respond appropriately to potential threats. - Conducting security training for employees.
We recognize the importance of educating security professionals and decision-makers. Through awareness campaigns and detailed explanations, we bridge the gap in understanding.

You saw what SOC or MDR provided by the vendor can give in terms of security coverage for the organization. These are well-trained and fully functioning teams of professionals ready to take over. It is also a valid reason that could tip the scales against starting from zero with building a SOC.
We’ve explored the intricacies of both in-house and outsourced Security Operations Center models, including what UnderDefense MDR empowering has to offer. Understanding the potential for agility and expertise with outsourced solutions opens a new way to strengthen your security stack. It also includes obvious benefits such as control and fast customization compared to building your own team.
The decision is only yours, and you should meticulously consider budget, resources, and your unique security needs when making the choice.
Final thoughts
Entrusting your security to an external provider requires careful evaluation. Can you find a trusted partner with a proven track record and expertise aligned with your specific threatscape? Are you comfortable handing over sensitive data and control measures? How will you ensure seamless integration with your existing infrastructure and processes?
The truth is, there’s no right answer. The ideal choice rests on a nuanced understanding of your organization’s unique strengths, weaknesses, and risk profile. Building a comprehensive, effective SOC demands significant investment, not just financially but also in time, expertise, and ongoing maintenance. That’s why signing up for a managed SOC service can be the fastest and easiest way to secure your organization’s data and IT infrastructure.
Understandably, there might be doubts about whether the vendor is trustworthy enough to commit to. Before doing so, you need to decide if the managed SOC aligns with all your needs and budget. Consulting with UnderDefense security experts can help you in navigating the SOC dilemma. Contact us today to choose the best approach for your organization.
Get a detailed estimate of your business security scope and timeline
















