CASE STUDY
UnderDefense Initiates Proactive Threat Hunting and Detects Hidden Threats in the Client’s Environment
Background
The Challenge
Despite using MDR services, well-configured tools, and advanced cybersecurity measures, our client faced a series of attacks on their cybersecurity infrastructure that exceeded the capabilities of standard correlation rules.
The situation unfolded during a proactive threat hunting session conducted by analysts from UnderDefense. They detected successful VPN login attempts from locations not typical for the client, such as Finland, Lithuania, Russia, and Britain. It raised concerns and triggered a more in-depth investigation into the nature and extent of the attacks.
The investigation discovered that the malicious actors had executed brute-force attacks on default accounts (helpdesk, security, admin, guests, test, and support). Despite robust defense measures, they exploited account security misconfigurations, which posed a critical risk and provided attackers with a direct route to the client’s core environment. It left minimal time for SOC detection and even less time for the security team to respond. The adversaries gained access to an internal network remotely through downloaded VPN clients. They used a web portal to access a desktop client with a preconfigured VPN gateway address. Besides, hackers accessed real accounts by figuring out their easily predictable passwords.
After gaining access to the internal network, one unclassified malicious actor effectively scanned the client’s intranet, gathering information for future attacks. Moreover, three unclassified actors successfully accessed the system using weak passwords, raising concerns about other vulnerable users across public resources.
Unfortunately, the correlation rules, designed to identify brute force attacks, failed to detect the malicious logins due to their low intensity and frequency. The attackers successfully guessed the password within a few tries and enabled unauthorized access, avoiding detection.
Although the current defense systems suggested all was well, they also exposed the constraints of automated tools. This incident highlighted the importance of securing VPN access and the potential risks associated with compromised accounts.
Challenges | Results |
|
|
|
|
About the client
Headquarters:
547
Key Results
6
The Solution
After collecting evidence, the UnderDefense team launched a comprehensive investigation and promptly informed the client. The objective was to grasp the incident’s nature, identify the compromised account, and understand the access method used by the malicious actor. Due to outdated account types, identifying users and their origin — local or domain — became crucial.
Below you can see the chronological sequence of events outlining the key actions taken to address the problem.
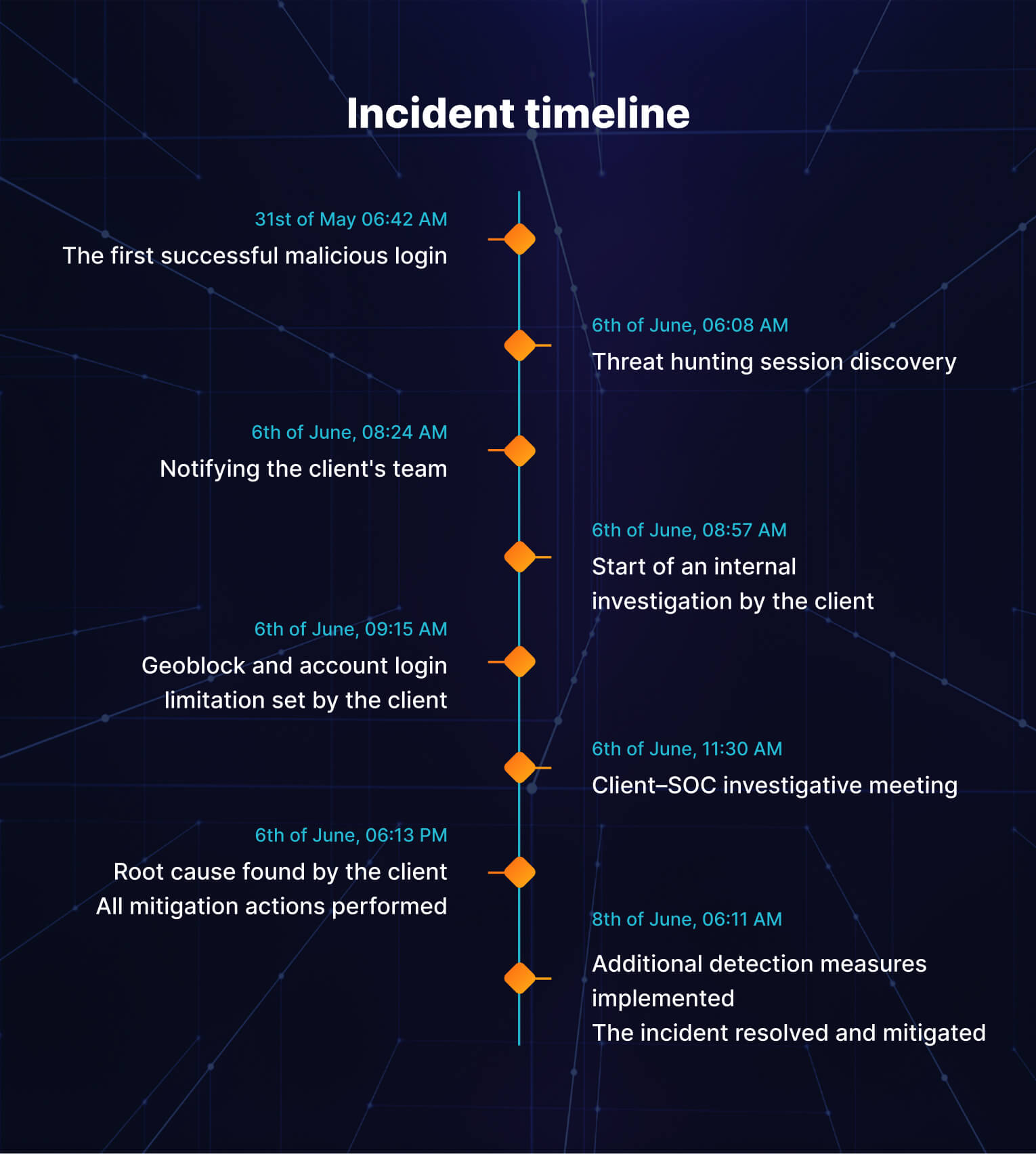

Outcomes
Account audit
Regular domain account audits are essential for identifying and deactivating old or unnecessary accounts. Leveraging the KnowBe4 PET tool enhances this process by detecting unused Active Directory accounts, uncovering security misconfigurations, and identifying weak passwords.
Offboarding process
A procedure that ensures employee accounts are immediately closed when they leave the company. It reduces the risk of lingering access points.
Internal password assessments
Regular assessment to identify weak passwords and replace them with strong ones to bolster overall password security.
Multifactor authentication
MFA implementation adds an extra layer of protection, making it more challenging for unauthorized access.
Password policies
Establishing and enforcing password policies that define criteria for password strength and regular updates. Also, a strong password policy on the VPN gateway is necessary for both local and domain users.
New correlation rules
Additionally, the UnderDefense team has created new correlation rules on our end. Such an approach helps regulate and automatically detect similar issues, streamlining the resolution process without requiring manual intervention.
Take control of your business security, before hackers do.






