In the ever-evolving cybersecurity landscape, Security Operations Centers (SOCs) find themselves at the frontline of defense, facing an unprecedented number of alerts. This surge leads to alert fatigue and employee burnout and poses the risk of critical alerts slipping through the cracks. In response to these challenges, SOC automation emerges as a critical solution.
We have the answers
This article delves into the why, what, and how of SOC automation and introduces SOC playbooks as solutions for organizations seeking an effective path to holistic and automated protection.
What is a SOC playbook?
A Security Operations Center (SOC) playbook is a detailed guide crafted to assist security analysts in effectively addressing and managing cybersecurity incidents. It is a roadmap that outlines the recommended procedures, tools, and collaboration strategies to employ during an incident. Playbooks provide a standardized and reproducible approach to incident response.
Why do you need SOC playbooks?
SOC playbooks are an integral component of modern cybersecurity. They play a crucial role in streamlining workflows within SOCs. Playbooks are needed when dealing with routine tasks, high alert volumes exceeding human capacity, and at all other stages.

These statistics paint a bleak picture, but automation playbooks are a beacon of hope in the storm. By strategically automating specific tasks, SOC teams can reclaim control, boost efficiency, and strengthen organizational defenses.
Automation is not a luxury for SOC, it’s a necessity. It is not about replacing analysts but about empowering them to focus on the strategic tasks that truly make a difference in your security posture. Below we list seven benefits for SOC resulting from automated security:
1.Addressing false positives and saving resources
SOC analysts are bombarded with thousands of alerts daily, making it impossible to manually review and investigate each one effectively. While security platforms may struggle to filter out many false positives, automated playbooks efficiently process and close such instances. This capability significantly alleviates the workload on the SOC team. Additionally, playbooks decrease MTTR by optimizing the allocation of human and financial resources.
2. Alleviating alert fatigue and burnout
Alert volume leads to alert fatigue, where analysts become numb to warnings and overlook critical threats. Automation takes over SOC Tier 1 responsibilities, allowing analysts to focus on more strategic tasks. Playbooks handle routine actions, reducing the burden on SOC analysts. Regular adjustments and checks in playbooks ensure operations remain effective and up-to-date.
3. Minimizing human error
Manual analysis is prone to human errors, such as overlooking subtle anomalies or misinterpreting data. These errors may have significant consequences, leading to missed threats and security breaches. Well-crafted automation substantially reduces the chances of errors, elevating the accuracy and reliability of security operations.
4. Simplifying scalability
With the increasing attack surface and complexity of threats, relying solely on human analysts hinders the ability to scale security operations effectively. Automation allows for faster and more efficient responses to security incidents, regardless of their scale or frequency.
5. Accelerating alert analysis and response
Playbooks streamline alert analysis, integrating diverse context sources to expedite threat response. This efficiency saves time on both full and partial analyses, empowering analysts to process a higher volume of alerts effectively.
6. Optimizing threat management
Automation catalyzes fast and effective threat containment and isolation, supported by structured playbooks that provide a methodical approach to neutralizing threats. This streamlined process accelerates threat detection and response by analyzing real-time data from diverse sources and empowers analysts to dedicate more time to proactive threat hunting. It enhances the overall security posture by identifying and neutralizing potential threats before they escalate.
7. Enabling additional actions
Playbooks empower SOC teams to take additional actions, including rollback procedures and facilitating a comprehensive and orchestrated response to security incidents. Also, they can promptly notify clients in case of a security incident, enhancing transparency and communication with stakeholders.
And we have experts and tools ready
What security processes can be automated?
Regarding SOC automation, the possibilities are vast, and the potential benefits are significant. Here are some SOC workflows that can be effectively automated:
- Threat intelligence enrichment: Use automation to gather, analyze, and synthesize data from various sources, including security logs, vulnerability reports, threat feeds, and open-source intelligence.
- Analysis: Based on the gathered information, playbooks can close an alert if it is not identified as a genuine threat.
- Remediation: If a threat is confirmed, automation playbooks notify a human analyst or attempt to take corrective actions.
- Vulnerability management: Automate scanning, prioritization, and remediation of vulnerabilities to reduce exposure.
- Real-time anomaly detection: Utilize AI and machine learning to identify unusual activities across data sources.
Doing it right: effective implementation of SOC automation
The selection of workflows that should be automated directly depends on your needs and priorities. Start by identifying your biggest pain points and resource constraints, then introduce automation that addresses those challenges.
Implementing SOC automation requires a strategic and well-defined approach. You should establish clear objectives, ensuring that automation aligns with your overall cybersecurity strategy.
Here are some essential tips for success:
- Start small and scale gradually. Don’t try to automate everything at once. Begin with low-risk tasks and gradually expand as you gain confidence and experience.
- Integrate with your existing tools. Don’t create islands of automation. Choose solutions that integrate seamlessly with your existing SIEM, SOAR, and other security tools.
- Focus on efficiency, not replacement. Automation is not about replacing analysts; it’s about freeing them from tedious tasks so they can focus on strategic analysis and threat hunting.
- Test and refine your automation regularly. No automation is perfect. Regularly test your playbooks and procedures, and refine them as needed to ensure they remain current and effective.
Explore advanced strategies for effective SOC automation, including the transformative impact of SIEM correlation rules in our blog.
UnderDefense MAXI – a safe path to automation
While automating your SOC is crucial, navigating the process can be daunting. That’s where UnderDefense MAXI comes in. It’s a comprehensive security automation platform that provides a safe and controlled environment to address specific SOC needs without jeopardizing your production environment. From automating routine tasks to orchestrating complex incident response workflows, UnderDefense MAXI stands out as a trusted ally in the pursuit of SOC excellence.
With UnderDefense MAXI, you can:
- Deploy pre-built automation playbooks for common tasks like log analysis and alert triage
- Develop and test your playbooks in a sandbox environment
- Integrate with leading security tools to create a unified automation ecosystem
- Gain insights and optimize your automation with real-time reporting and analytics
UnderDefense MAXI offers:
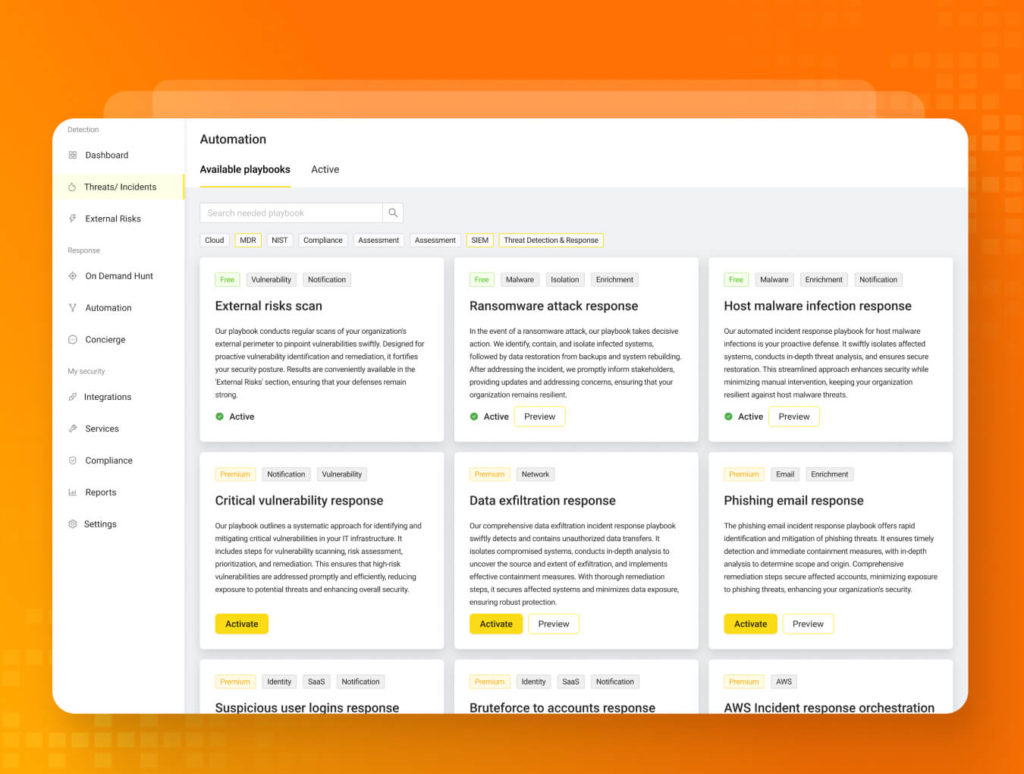
- Ready-made fully automated playbooks:
- External perimeter monitoring and management
- Ransomware attack response
- Host malware infection response
- Custom playbooks (available upon request):
- Critical vulnerability response
- Data exfiltration response
- Phishing email response
- Suspicious user login response
- Bruteforce to accounts response
- AWS incident response orchestration
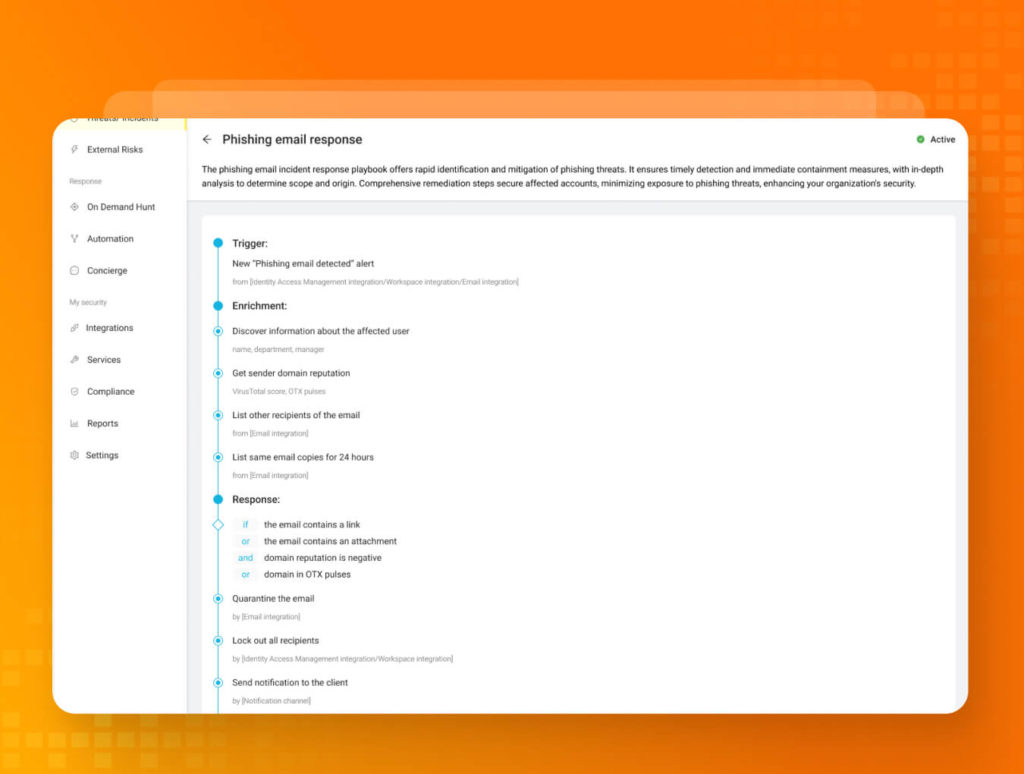
Phishing attacks: a defense template example
Phishing attacks remain a pervasive and potent danger. One concrete example that illustrates the power of cybersecurity automation is the implementation of a phishing email response playbook. It offers rapid identification and mitigation of phishing threats, ensuring immediate detection and containment measures, with in-depth analysis to determine scope and origin. Comprehensive remediation steps secure affected accounts, minimizing exposure to phishing threats and enhance your organization’s security.
Below is a sample phishing automation template showcasing an enrichment phase with seamless integration of related services. This is followed by a response phase designed to save analysts’ time and topped off with notifications in the UnderDefense MAXI chat and to your email. That’s the power of streamlined phishing automation at your fingertips.
Conclusion
Strengthening your security operations center with automation playbooks is a proactive step toward bolstering your organization’s cyber resilience. Implementing a strategic plan that includes tailored playbooks can enhance your SOC’s efficiency, reduce response times, and maximize your defenses. Contact us today for a free consultation and see how we can take your SOC to the next level.
















