In a Nutshell
Understanding how an attacker can take advantage of network vulnerabilities is vital when it comes to the SOC team’s quick response time. Instead of only establishing processes to satisfy MITRE ATT&CK mapping, it is imperative to align with the MITRE ATT&CK framework. Otherwise, your team of SOC analysts will be overwhelmed by attempts to predict the attacker’s moves.
Out-of-the-box tools often overlook pitfalls and generate numerous false positives. Consider a scenario where your SOC team faces 1,000 alerts, with only 2% being genuine threats. Now, imagine that number escalating to 10,000 alerts per day. Identifying real threats would become a time-consuming challenge.
Whether you have an in-house SOC team or an MSSP providing services for SIEM management, we understand the challenges you face.
Our track record speaks for itself – by constantly updating and fine-tuning our correlation rules, we have:
- successfully reduced the implementation time for new clients from 7 days to an impressive 1 day
- significantly improved response times
42% faster for critical threats
29% faster for high-level threats
We have the answers
Introduction
In cybersecurity, SIEM (Security Information and Event Management) plays a crucial role as a centralized database that correlates information from various sources. Its primary function is to collect and analyze data to identify patterns and generate threat notifications.
Correlation rules in SIEM are the backbone of this process, acting as indicators that trigger alerts when specific patterns are identified. These rules help analysts explore the vast amount of data and focus on actionable insights, enhancing the overall efficiency of threat detection.
While most legacy SIEMs are focused on alerts and anomalies, they are not aimed at putting together the pieces to identify the actual threat hidden behind multiple correlated alerts. Overall, the way SIEM is configured will determine the workload of your team and the speed of incident response. It is impossible to build a strong defense without considering the MITRE ATT&CK framework.
Most modern providers often mark their cybersecurity solutions as all-inclusive. However, customization is often necessary to align them with specific business requirements and existing security infrastructure.
Aligning with the MITRE ATT&CK framework goes beyond simple mapping and focuses on identifying real threats and attack stages for an actionable response. By doing so, organizations can move beyond a high volume of individual alerts and focus on identifying and addressing the real threat chains that are aligned with the attack stages defined by MITRE ATT&CK.
The problem
Why SIEM pre-built correlation rules are not enough
Default SIEM systems provide a starting point for security operations, but they often require customization and fine-tuning to align with an organization’s specific security requirements, industry regulations, and unique IT environment. Both MSSPs and in-house SOC teams may need to configure additional correlation rules, customize dashboards and reports, integrate with existing security tools, and define specific alerting and response workflows.
Here is a list of challenges you may face when using default SIEM settings:
- Rule duplication and incomplete coverage: Default correlation rules often serve similar purposes, causing redundancy and inefficiency. Additionally, these rules may not adequately cover all tactics and techniques employed by malicious actors, leaving potential blind spots in threat detection.
- Quantity over quality: While additional sources of correlation rule databases exist, they often prioritize quantity over quality. These sources offer a vast number of rules, but their effectiveness and relevance may be questionable. Basic correlation rules provided by default SIEM systems have limited coverage of MITRE tactics/techniques, primarily detecting only simplistic attacks.
- High False Positives: Enabling numerous correlation rules often leads to a significant number of false positives. Dealing with them consumes valuable time and resources.

- Time-consuming onboarding: Configuring and fine-tuning multiple correlation rules for each new client (for MSSP) or your own environment requires a considerable amount of time and effort. This delays the onboarding process and hinders the quick deployment of effective security measures.
- Inconsistent rule updates: In the case of in-house SOC teams working with a single system, updating rules may be more manageable compared to MSSPs handling multiple clients. Modifications to correlation rules for one environment do not automatically propagate to other domains. It requires additional investment in terms of time, resources, and effort.
- Lack of Continuous Improvement and Optimization: SIEM systems provide initial rules based on general patterns and known threats, they often lack the capability to iteratively refine these rules based on customer feedback, incident response data, and threat intelligence. As a result, there is a higher risk of false positives and missed detections, as the rules may not effectively capture the organization’s unique threat landscape.
The problems of SIEM Implementation and Maintaining
Problem | In-House SOC Team | MSP/MSSP |
Rule duplication and incomplete coverage | ||
Quantity over quality | ||
High False Positives | ||
Time-consuming new client onboarding | ||
Inconsistent rule updates | ||
Continuous process improvement and optimization |
While correlation rules serve as a starting point, they mostly offer minimal output out of the box. Consequently, relying solely on the default correlation rules provided by SIEM vendors can limit the system’s effectiveness, and lead to missed incidents or inability to address the unique infrastructure of individual clients.
How UnderDefense solved the problems
As an MSSP we have encountered the same challenges such as rule duplication, incomplete coverage, high false positives, and time-consuming onboarding.
The UnderDefense SOC team decided to refine and optimize our SIEM implementation as a part of our Managed Detection and Response (MDR) package and managed SIEM service.
While pre-built rules are a solid foundation, we recognized the need to fine-tune and augment them to align with the specific requirements of our clients.
We focused on two key objectives:
- Improving existing correlation rules
- Streamlining their implementation for both existing and future clients
To kick-start our initiative, we evaluated the effectiveness of 500 out-of-the-box correlation rules provided by SIEM vendors. They served as a foundation but needed fine-tuning and aligning with the specific requirements of our clients. Through careful analysis and leveraging our expertise, as well as MITRE ATT&CK framework, we updated the existing list of SIEM correlation rules and created 275 new rules to bolster threat detection capabilities.
Type | Platform | Rules |
Endpoint | Windows/AD | 96 |
Linux/Unix | 47 | |
Cloud | AWS | 48 |
Azure | ||
GCP | ||
Network | 38 | |
Other (Google Workspace, Azure AD, Okta) | 46 | |
Total | 275 | |
Benefits our clients gained of customized rules for increased performance
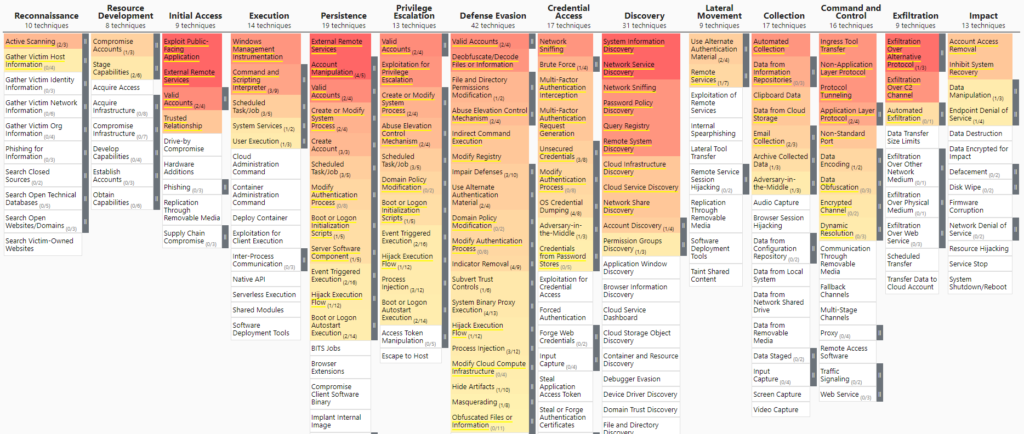
MITRE ATT&CK framework coverage
Before: 20% MITRE ATT&CK framework coverage
Now: 90% MITRE ATT&CK framework coverage
As vendors claim, default MITRE SIEM rules are designed to provide broad coverage across various environments. However, based on our experience, this can lead to a higher number of false positives due to the inclusion of generic and less-relevant alerts.
Out-of-the-box MITRE ATT&CK framework coverage
On the other hand, customer-mapped rules help reduce the noise generated by irrelevant or non-actionable alerts, allowing security teams to prioritize and focus on genuine threats.
By implementing customized rules, we have covered approximately 90% of the MITRE ATT&CK framework and effectively eliminated false positives. We have also significantly improved our response time to threats, reduced the workload on analysts, and accelerated our incident response.
Additionally, we prioritize the performance and coverage of our correlation rules through comprehensive testing. Leveraging tools like Atomic Red, which simulates attacker techniques and tactics, we validate the effectiveness of our rules in detecting potential threats.
Reduced client onboarding time (correlation rules setup and fine-tuning stage)
Before: 7–10 days for onboarding and tech setup
Now: 1–2 days for onboarding and tech setup
We have significantly reduced the onboarding time for new clients by up to seven times. Previously, the process would take approximately 7–10 days, but now we have streamlined it to just 1–2 days. This improvement allows us to quickly set up and configure the necessary systems and security measures, enabling our clients to benefit from our services and protection in a much shorter timeframe.

Accelerated threat response time
Results:
response time to critical severity alerts reduced by 42%
response time to high severity alerts reduced by 29%
With our improved capabilities, we have achieved an average detection and response time of 11 minutes (as compared to 19 min) for threats classified as critical, and 29 minutes (as compared to 41 min) for threats classified as high. This rapid response time enables us to swiftly mitigate potential damages and minimize the impact of security incidents on the client’s organization. By promptly identifying and addressing these threats, we can effectively protect the systems, data, and assets, ensuring the resilience and security of any organization.
Simplified implementation for our existing and future clients
Before: rules were manually changed for clients` specific requirements
Now: rules are automatically updated and applied to all clients
We developed a smooth transition plan for our existing clients who initially subscribed to our services using the default rules. Leveraging our knowledge base, we introduced a one-click mechanism to switch from the old rules to our enhanced set effortlessly. This seamless implementation allows us to quickly upgrade the threat detection capabilities for all existing clients without manual and individual rule changes.
Our approach extends to our future clients as well. By integrating our customized correlation rules into our standard MDR package, we offer a powerful feature that new clients should be aware of. This ensures that from the outset, they benefit from an advanced SIEM implementation that leverages our refined rule set, providing an enhanced level of protection.
Unique aspects that set UnderDefense apart from the competition
- UnderDefense MAXI Platform: Our security-as-a-service platform provides a revolutionary solution for managing your organization’s security that offers 24/7/365 end-to-end protection, detection, and response to safeguard your organization against evolving cyber threats. You can gain visibility into security events, access real-time dashboards and reports, and collaborate seamlessly with our team to address security challenges effectively.
- A Broad Spectrum of Cybersecurity Services: UnderDefense offers a full range of 24/7 managed detection and response (MDR) services, including penetration testing, virtual CISO, and incident response service. This ensures continuous threat detection, rapid incident response, and proactive security measures.
- Vendor Agnostic Approach: Unlike many competitors, UnderDefense is vendor-agnostic. This allows us to work with various security tools and solutions from different vendors, ensuring customized and effective security solutions that align with each client’s specific needs.
- Tailored Solutions: UnderDefense takes a personalized approach to MDR services. We understand each client’s unique requirements, infrastructure, and desired security coverage. Our team customizes the services to provide optimal security outcomes, considering factors such as risk tolerance, compliance needs, and business objectives.
- Reseller Partnership Opportunities: UnderDefense offers partnership opportunities for reselling its MDR services. This enables businesses to extend their portfolio of security offerings, leverage our expertise, and provide their clients with top-notch MDR solutions, enhancing their overall cybersecurity posture.
- Resource optimization: It is a crucial aspect of efficient system design and operation. Avoiding the creation of heavy, overengineered rules is indeed a good approach to prevent overwhelming instance resources.
Being prudent makes all the difference
Conclusion
Implementing a SIEM solution is an important step toward enhancing an organization’s security posture. While starting with built-in rules and collecting and processing data is better than nothing, taking it to the next level requires a strategic approach.
Customizing and enriching correlation rules become essential for delivering top-notch security services, ensuring maximum threat detection efficacy, and minimizing the risk of missing critical incidents.
UnderDefense offers a powerful innovative approach to SIEM correlation rules which is integrated into our MDR package. With a centralized knowledge base, rigorous testing, and streamlined onboarding, we deliver comprehensive cybersecurity services, ensuring maximum value for our clients.
If you’re interested in joining us as a partner, we invite you to explore our partnership opportunities or get in touch with our sales team for more detailed information. We’re excited to discuss the potential opportunities and benefits of partnering with us, and we look forward to hearing from you. Together, we can create a successful and mutually beneficial partnership and revolutionize your defense against the ever-growing threat landscape.
Take advantage of this exciting opportunity—Trust UnderDefense to provide unparalleled protection for your digital assets.
Contact us today to learn more!