Even the most experienced SOC team can feel overwhelmed. Security Operations Centers (SOCs) are the war room against cyberattacks, but manual processes can leave even seasoned analysts struggling. Sifting through endless logs, delayed incident response and scalability issues are all too common frustrations.
You know the challenges firsthand. But what if there was a way to work smarter, not harder? Security Operations Center tools (SOC tools) can be your secret weapon.
You deserve transparency
Get a Free Security Assessment
This article dives deep into the most effective SOC tools and technologies, exploring how they can transform your SOC’s effectiveness and help you:
- Conquer alert fatigue: Automate manual log analysis and investigation with SOC automation tools, freeing you to focus on strategic threats and investigations.
- Become a threat hunter: Leverage real-time threat identification and continuous monitoring capabilities offered by many SOC tools and technologies to detect and neutralize attacks before they cause damage.
- Respond like a champion: Streamline incident response with automated workflows and collaboration features found in leading SOC software, minimizing downtime and impact.
- Scale with confidence: Handle increasing data volume and complexity easily using the right SOC tools. Ensure your SOC remains effective as your organization grows.
The best SOC automation tools for business: top recommendations
1.Threat intelligence platforms (TIPs)
The best thing about TIPs is their focus on enriching and visualizing data. Instead of just presenting raw information, TIPs excel at connecting and adding context, giving a deeper understanding of potential threats. They simplify complex data by transforming it into clear dashboards and reports, thus making it easier for decision-makers to comprehend the overall threat landscape.
TIPs collect and aggregate threat data from various sources, including:
- Open-source intelligence (OSINT): News, social media, and hacker forums offer valuable insights into attacker tactics and chatter.
- Commercial threat feeds: Real-time updates on known vulnerabilities, malware signatures, and emerging threats.
- Internal threat data: Your security incidents, logs, and observations.
The best threat intelligence platforms are VirusTotal, Cisco Talos, Microsoft Defender Threat Intelligence, AlienVault Open Threat Exchange (OTX), AbuseIPDB, and OpenTAXII.

2. Endpoint detection and response (EDR) tools
EDRs monitor endpoints, such as laptops and servers, for malicious activity. You can also use them to investigate and respond to incidents. EDRs offer a significant advantage compared to traditional antivirus software, and here is why:
- Behavioral analysis: They monitor and analyze how files and applications behave, looking for suspicious activities like unauthorized access, registry modifications, or suspicious network connections.
- Centralized management: You can easily manage and monitor EDRs across all your endpoints from one central console, providing a holistic view of your security posture.
The best EDR tools are CrowdStrike Falcon Insight, SentinelOne Singularity Platform, Microsoft Defender, Elastic, and Qradar EDR.

3. Extended detection and response (XDR) tools
XDR is the big brother of EDR. While EDR focuses on individual endpoints like laptops and servers, XDR takes a broader and more integrated approach. Here’s what makes XDR unique:
- Combining data from multiple sources: EDR looks at endpoints, but XDR pulls in data from your entire security stack and gives a complete picture of what’s happening in your network, not just isolated bits and pieces.
- Correlating events: Instead of just seeing individual alerts, XDR connects the dots between them. It identifies patterns and suspicious activities that might go unnoticed, like malware communicating with a strange server or unusual login attempts across multiple devices.
- Automating response: XDR doesn’t just sit back and raise alarms. It can automatically trigger predefined actions depending on a threat type, like isolating infected devices or blocking suspicious network traffic. It saves time and prevents attackers from wreaking havoc.
The best XDR tools are CrowdStrike Falcon XDR, Palo Alto Networks Cortex XDR, Trend Micro Vision One, Cisco XDR, and SentinelOne Singularity Platform.

4. Security information and event management (SIEM) tools
SIEMs offer a centralized platform for monitoring and managing security-related information from various sources within an organization’s IT environment. They collect and analyze data from multiple security sources, such as firewalls, intrusion detection systems, and endpoint security solutions. You can use this data to identify suspicious activity and potential threats. SIEM tools play a crucial role in cybersecurity by doing the following:
- Log collection: Aggregating log data from various network devices, systems, and applications.
- Normalization and correlation: Identifying patterns and anomalies by mapping diverse data into a standard format.
- Alerting and notification: Generating real-time alerts for suspicious activities, enabling prompt investigation.
- Compliance management: Assisting in meeting regulatory requirements with reporting and auditing capabilities.
- User and entity behavior analytics: Investigating user and entity behavior to detect anomalies or signs of compromise.
The best SIEM tools are Splunk, IBM QRadar SIEM, LogRhythm SIEM, Securonix Unified Defense SIEM, and Elastic SIEM.

5. Digital forensics and incident response (DFIR) tools
DFIR encompasses digital forensics, which focuses on collecting and analyzing digital evidence. It also includes incident response, which involves a systematic approach to managing and mitigating security incidents as a part of an incident response plan. It aims to uncover the root causes of incidents, assess the extent of the compromise, and develop strategies to contain and remediate the impact on information systems and data. DFIR tools offer many advantages, including the following:
Explore Top-Rated SOC Tools Now
We have experts and tools ready
- Automated data collection and advanced analysis (memory analysis, malware detection, and root cause investigation)
- Evidence integrity for the court through secure storage and chain of custody tracking
- Proactive threat hunting
- Incident response coordination
- Faster containment and eradication
- Reduced investigation time
- Improved security posture
The best DFIR tools are OpenText EnCase Forensic, Autopsy, The Sleuth Kit, Wireshark, Mandiant’s Redline, Exterro Forensic Security Toolkit (FTK), Cellebrite UFED (Universal Forensic Extraction Device), and Sysmon.

6. Vulnerability scanners
Vulnerability scanners are designed to scan for known software vulnerabilities that attackers could exploit. The advantages they offer are the following:
- Better visibility: They provide a comprehensive overview of security weaknesses across your IT infrastructure, including networks, systems, and applications.
- Improved threat detection and prioritization: They continuously scan your environment for known vulnerabilities and provide detailed reports on their severity, exploitability, and potential impact.
- Enhanced threat hunting and incident response: They can be integrated with other security tools to provide valuable insights for threat hunting and incident response. By analyzing vulnerability data alongside other security events, SOC teams can identify patterns and connections that might be missed.
- Reduced remediation time: They provide information on how to remediate identified vulnerabilities, saving SOC teams valuable time and effort.
- Improved compliance: Many regulations and compliance frameworks require organizations to check their systems regularly. Vulnerability scanners help SOCs demonstrate compliance by providing audit-ready reports on identified vulnerabilities and their remediation status.
- Cost-effectiveness: They are a worthwhile investment compared to the potential costs of a successful cyberattack.
The best vulnerability scanners are Tenable, Qualys, Greenbone, and Rapid7 InsightVM.

7. Asset inventory management tools
Asset inventory management involves systematically tracking and monitoring an organization’s assets. It includes both physical assets, such as hardware devices and equipment, and digital assets, like software licenses and virtual resources. The process typically includes identifying, recording, and updating asset information throughout its lifecycle. This type of software is crucial for optimizing resource utilization, ensuring compliance, and enhancing overall security.
Effective asset inventory management offers several advantages:
- Enhanced threat detection and response: You can quickly identify impacted systems, trace attack paths, and understand the potential scope of a breach. Knowing the criticality of your assets (e.g., server vs. printer) and their associated vulnerabilities helps you prioritize patching and mitigation efforts.
- Reduced workload: Automation tools can automatically discover and update asset information, freeing analysts’ time for more strategic tasks like threat analysis and incident response.
- Data-driven insights: Information derived from asset inventory data can guide the development of security policies and inform risk assessments.
- Improved auditability: A well-maintained inventory provides a documented record of your assets, which is helpful for internal audits and external compliance checks.
- Reduced shadow IT: By identifying unmanaged devices and unauthorized software, you can minimize the risks associated with shadow IT.
The best asset inventory management tools are Ivanti, Freshservice, and Asset Panda.

8. Cyber asset attack surface management (CAASM) tools
CAASM tools empower IT and security teams to obtain a comprehensive overview of internal and external assets. They seamlessly integrate with existing tools and consolidate data. With CAASM solutions, you can:
- Gain total visibility, leaving no room for hidden vulnerabilities.
- Identify the scope of vulnerabilities across your entire digital landscape.
- Analyze and prioritize threats and understand their severity and potential impact.
- Direct resources toward addressing the most critical threats first, ensuring maximum effectiveness.
- Take decisive action to patch vulnerabilities, implement security controls, and mitigate risks.
- Enhance cyber security by continuously monitoring and analyzing your attack surface and anticipating potential threats before they strike.
- Mitigate risks associated with shadow IT by identifying unmanaged devices and unauthorized software.
The best CAASM tools are Lansweeper, Axonius Platform, Armis Centrix, and runZero.

9. ATT&CK Powered Suit
The MITRE ATT&CK® knowledge base is a globally accessible, free, open-source framework that catalogs cyber adversaries’ tactics, techniques, and procedures (TTPs). Meanwhile, ATT&CK Powered Suit, a free Chrome extension, brings the power of this knowledge base to your browser, offering essential threat intelligence to defense tools. Privacy is prioritized, with no data collection or sharing. With multilingual support, it serves a global audience and keeps them ahead in the dynamic cyberthreat landscape with regular updates. It helps you:
- Instantly find information about ATT&CK techniques, groups, software, and more.
- Streamline research by copying snippets to a notebook and exporting selected techniques to ATT&CK Navigator.
- Increase efficiency by using context menus, omnibar support, and other features to access information quickly.
Configuration challenges with tools used by SOC analysts
Getting your SOC toolset up and running can be a battlefield. Below, we will list some common enemies you should be aware of:
- Misconfigurations can leave gaps in your defenses or trigger false alerts, creating noise instead of clarity.
- False positives can become a problem. Like a paranoid guard, new tools may flag every activity as threats, wasting your time and resources.
- Normalization & data processing require specific skills and expertise. Different tools speak different languages, so integrating and standardizing their data can be a complex puzzle.
Creating and scaling SOC is an ongoing battle. But with the right tools and strategies, you can turn it into a well-informed and vigilant business defender ready to face any digital foe.
Critical considerations for choosing the right Security Operations Center software
By carefully considering your needs, vulnerabilities, and budget, you can select the best SOC tools to strengthen your security posture and protect the organization from cyberattacks. Here are some essential factors to keep in mind when choosing tools for the security operations center:
- Company’s size and complexity: Large organizations with complex IT environments will need more robust and comprehensive tools.
- Budget: SOC tools can range in price from free options to enterprise-grade solutions that cost hundreds of thousands annually.
- In-house expertise: If you have a team of experienced security analysts, you can get by with fewer or less-featured options. However, if your team is smaller or less experienced, you may need to invest in more user-friendly or automated solutions.
A strategic approach to SOC tool implementation is not just about acquiring technology. It’s about creating a harmonious symphony across a security tech stack to protect organizations from an ever-changing threat landscape. By carefully planning, selecting, and integrating the right solutions, you can transform your security posture, achieve better visibility, and optimize resource utilization.
UnderDefense MAXI: your all-seeing SOC eye
Tired of juggling multiple SOC tools? UnderDefense MAXI is not just another platform but an innovative powerhouse that brings all your security tools together. Whether you’re using EDR, XDR, SIEM, or others, UnderDefense MAXI seamlessly integrates with your existing security stack. We understand the language of these tools, decipher their insights, and transform their data into actionable intelligence for you.
With UnderDefense MAXI, you get:
- A centralized security management dashboard to see everything in one place.
- Advanced analytics to correlate data from multiple tools and identify complex threats hiding in the noise.
- An AI-powered threat hunter to unleash real offense before it causes havoc.
- A security orchestra conductor to automate tasks, coordinate responses, and watch your SOC team’s efficiency soar.
- Your compliance confidante in meeting industry standards efficiently, thanks to built-in compliance kits and expert guidance.
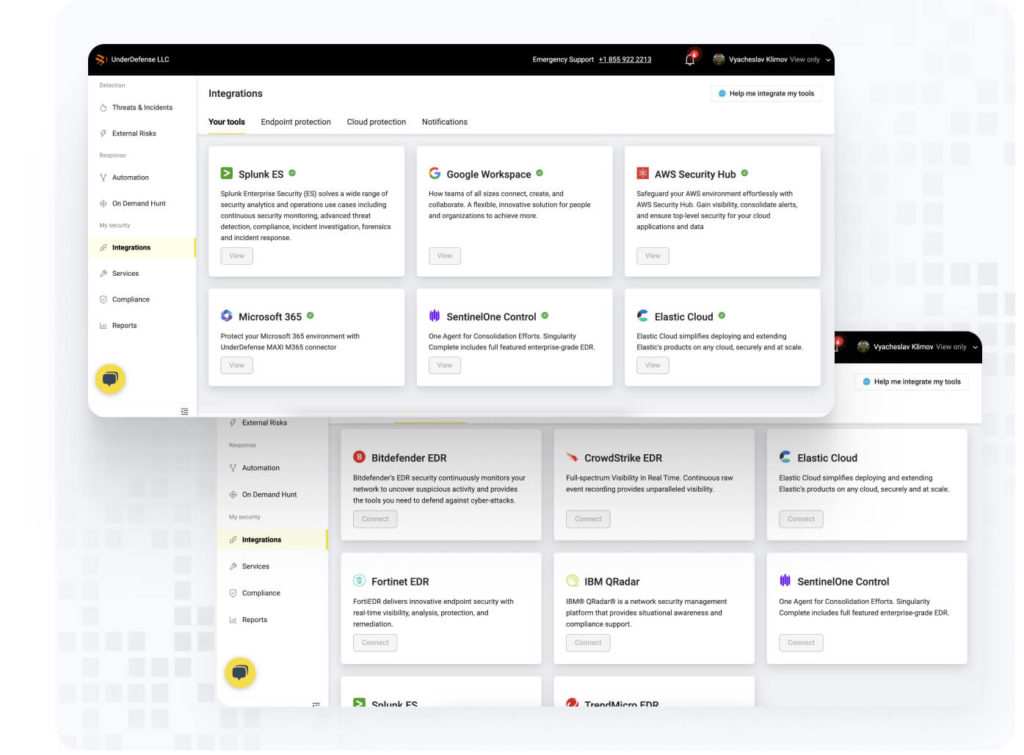
You can watch expert tutorials on how to connect SentinelOne agent and Splunk to UnderDefense MAXI easily and quickly.
Partner with us to safeguard your operations
Get a Free Managed SOC Consultation
Managed SOC (SOC-as-a-Service)
The UnderDefense’s managed SOC, or SOC-as-a-Service, is a crucial element of our 24×7 turnkey MDR offering. It effectively unifies human intelligence with cutting-edge AI technologies, propelling security to new heights.
This service is exclusively designed for organizations with limited security expertise or budget constraints and those ones preferring to entrust security responsibilities to a third party. It ensures a robust and comprehensive security approach.
Take the next step in securing your organization. Contact our team today to experience the future of cybersecurity.
Author: Hlib Yevtushenko
Principal Threat Response Architect at UnderDefense
















