In today’s ever-evolving threatscape, organizations should proactively assess and fortify their defenses against not only external but also internal risks. That’s where internal network penetration testing comes into use and adds great value. This type of testing continues our series of articles dedicated to penetration testing services and if you want to know what it is, what it includes, and how it can benefit your business, keep reading.
The average cost of a data breach exceeds $3.8M.
Find business vulnerabilities and how they may be exploited before criminals do.
Table of Contents
- What is internal penetration testing?
- The importance of internal penetration testing services for business
- Pentest how-to: internal penetration testing checklist
- What should be included in an internal penetration test report?
- Top 8 factors affecting internal penetration testing cost
- What’s the difference between internal vs. external penetration testing
- Conclusion
What is internal penetration testing?
First things first, let’s start with the definition. Being a part of network penetration testing services, internal penetration testing is a systematic and controlled process of simulating cyberattacks from within an organization’s network. It involves authorized security experts attempting to exploit vulnerabilities in the internal infrastructure, systems, and applications.
The importance of internal penetration testing services for business
Why is this type of service especially important today? The primary goal is to identify weaknesses before malicious actors can exploit them. Internal penetration testing is a fundamental cybersecurity practice that empowers companies to evaluate their internal networks, systems, and applications to discover vulnerabilities and security gaps. Here’s why it’s crucial:
- Detecting insider threats: Internal pen tests help identify vulnerabilities that malicious insiders or compromised accounts can exploit, to neutralize them immediately.
- Security awareness: Such services promote a culture of cybersecurity awareness, making employees more vigilant and security-conscious.
- Compliance: Many regulatory bodies mandate internal pen testing to ensure adherence to industry standards and best practices.
- Risk reduction: Proactive vulnerability identification reduces the risk of data breaches, financial losses, and reputational damage.
- Control validation: It validates the effectiveness of security controls, policies, and procedures, uncovering overlooked weaknesses.
- Lateral movement prevention: This type of service helps identify and close pathways attackers can use to move within the network, to minimize potential damage.
As you can see, internal penetration testing now is not just another item in the compliance to-do list, but a fundamental pillar of robust cybersecurity.

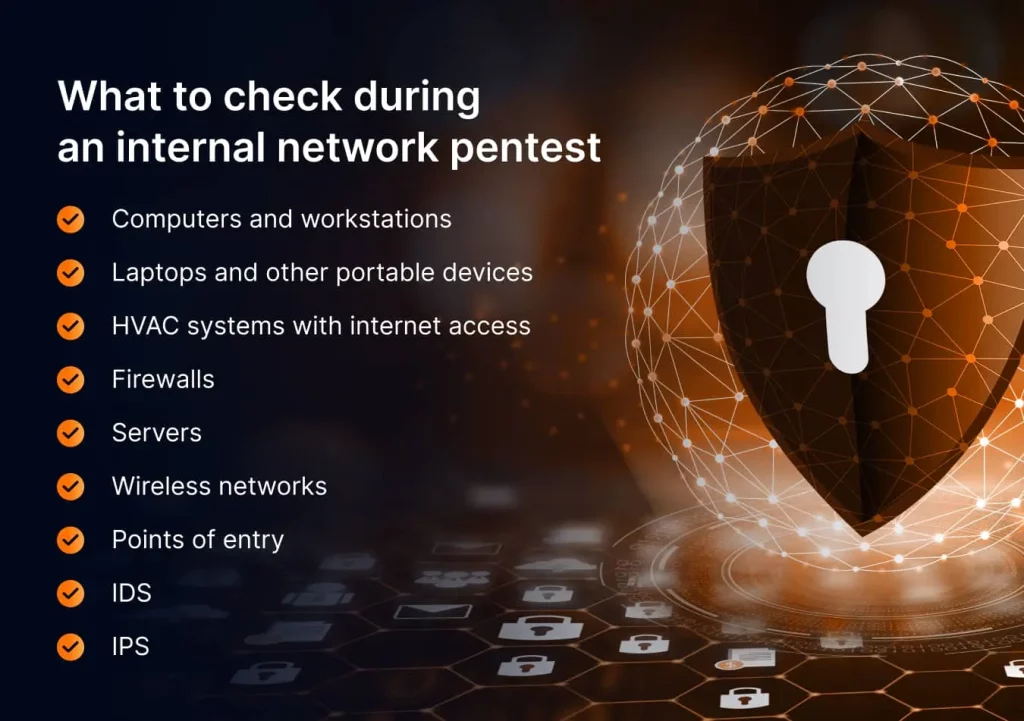
Pentest how-to: internal penetration testing checklist
Preparing for an internal network penetration test, start with a comprehensive checklist describing what should be done at each step. We list the most critical steps and considerations:
- Clearly outline the goals and objectives of the internal pen test. Determine what assets, systems, and applications will be assessed.
- Identify the scope of the test, including which network segments or departments will be assessed. Specify what penetration testing methodology will be used (black box, white box, or gray box).
- Obtain written consent from the organization’s leadership and ensure that legal and ethical considerations are addressed.
- Gather information about the internal network, such as IP addresses, domain names, and potential entry points.
- Identify vulnerabilities, misconfigurations, and weaknesses in the internal network and its components.
- Try to exploit the identified vulnerabilities to assess the potential impact of an attack.
- Document all findings, including vulnerabilities, their severity, and recommended remediation steps. Provide a detailed report to the organization’s stakeholders.
- Collaborate with the organization to prioritize and remediate the identified vulnerabilities promptly.
- Conduct follow-up tests to ensure that vulnerabilities have been effectively solved.
You can take this internal infrastructure penetration testing checklist as a basis and adjust or expand it to your needs and expectations. But most importantly, by doing so you won’t miss anything crucial and guarantee an informative report for your further cybersecurity improvement initiatives.
Let’s see if you’ll withstand our ethical hacking attacks
What should be included in an internal penetration test report?
As we’ve already mentioned, an internal penetration test report is a crucial deliverable that provides organizations with valuable insights into the security of their internal network, systems, and applications. Here’s what should be included in an internal penetration test report:
- The executive summary provides a high-level overview of the penetration test results, including key findings, their severity levels, and potential impact on the organization’s security posture.
- The scope and methodology section details the scope of the penetration test, specifying which systems, applications, and network segments were assessed. It also specifies what testing methodology was used, i.e. black box, white box, or gray box, to provide transparency.
- The vulnerability assessment block covers all identified vulnerabilities, including their severity levels (e.g., critical, high, medium, low), and provides a brief description of each. Penetration testing providers often categorize vulnerabilities based on their potential impact and exploitability.
- Exploitation details describe how vulnerabilities were exploited during the penetration test, including the techniques and tools used by ethical hackers to help organizations understand the attack vectors.
- The risk assessment section assesses the overall risk associated with the identified vulnerabilities. It explains the likelihood of exploitation and the potential impact on the organization’s operations, data, and reputation.
- Recommendations for remediation include clear and practical steps for addressing each issue. They allow you to prioritize your next actions based on the severity of vulnerabilities and potential impact.
- Technical details are mainly created for tech-savvy teams and stakeholders to provide them with detailed information about the vulnerabilities, including proof-of-concept (PoC) exploit code, affected systems, and remediation advice.
- The compliance and regulatory alignment section highlights any compliance-related findings and explains how the penetration test aligns with regulatory requirements and industry standards, if applicable.
- Appendices usually include supplementary information such as network diagrams, configuration details, and additional technical data that supports the findings and recommendations.
- The conclusion summarizes the key takeaways from the penetration test, reiterates the importance of addressing vulnerabilities, and emphasizes the organization’s commitment to improving security.
A well-structured internal penetration test report not only highlights vulnerabilities but also guides companies in mitigating them effectively. So, it can serve as a roadmap to enhance the cybersecurity posture and implement remediation measures effectively.
Top 8 factors affecting internal penetration testing cost
The price of internal network penetration testing may vary depending on multiple factors. Below we will cover the most common ones to make it easier for you to analyze cost estimates and plan the budget:
- The scale and complexity of your internal network significantly impact the cost. For instance, a large, intricate network with numerous systems and apps will require more time and resources, resulting in a higher cost.
- Testing methodology, whether it’s a black, white, or gray box, also influences the final estimate. A white box penetration test may be more expensive compared to a black box since it requires more time, specific tech skills, and a high level of expertise.
- The skills and expertise of the penetration testing team matter. Highly experienced professionals may charge higher rates, but their effectiveness and speed can result in a more insightful report and considerable cost savings in the long run.
- Reporting, remediation, and other post-test activities contribute to the overall cost. However, don’t give up on these important steps and consider allocating a budget to them.
- Compliance requirements and certain regulatory standards may require additional penetration testing activities and so add to the service price tag. However, compliance is a mandatory condition for business existence and growth in many industries.
- Customization of penetration testing strategies or methods to align with your security objectives and risk profile may result in higher costs.
- The geographic location of the internal penetration testing provider has a direct influence on the estimate due to differences in labor rates and market competitiveness. Organizations in urban areas may charge more than those in less densely populated regions.
- Advanced testing tools and technologies may increase upfront costs but in turn, provide more accurate results and potentially reduce long-term security expenses.
To sum up, it doesn’t matter whether you will conduct internal penetration testing using your in-house resources or engaging a third party. In any case, it is a value-enhancing investment in the cybersecurity strategy of any organization, regardless of its size and maturity level as it helps identify existing weaknesses, solve them proactively, and safeguard against insider threats.
What’s the difference between internal vs. external penetration testing
Comparing internal vs. external penetration testing may be confusing. However, each service is a critical component of a robust cybersecurity strategy, serving certain purposes.
Internal penetration testing involves the evaluation of an organization’s internal network, systems, and applications to uncover vulnerabilities. The primary objective is to identify weaknesses that could be exploited by insiders or external attackers who have already got inside the network. This service helps companies detect and mitigate insider threats, strengthen internal security controls, and ensure compliance with regulatory requirements. It’s particularly important for protecting sensitive data and systems within an enterprise.
External penetration testing, on the other hand, focuses on assessing the security of an organization’s external-facing assets, including websites, servers, and networks. The goal is to identify gaps that external attackers could exploit to gain unauthorized access. This type of penetration testing service is vital for defending against external cyber threats, enhancing the security of public-facing assets, and protecting customer data.
Internal pentest | External pentest | |
Goal | Discover existing security gaps from a malicious insider’s viewpoint | Detect current security gaps from an external hacker’s viewpoint |
Target | Internal networks, apps, systems, and other endpoints | Public-facing assets like servers, sites, external apps, and networks |
Performer | In-house team or third-party provider | External security provider |
Result | The findings are used to strengthen the network baseline | The findings are used to detect and prevent attacks on business |
Duration | Up to 5 days, depending on network scale and complexity | Up to 3 weeks, depending on network scale and complexity |
Being prudent makes all the difference
Conclusion
Internal network penetration testing is an effective but complex way to proactively strengthen your cybersecurity defenses. It requires extensive knowledge and expertise to discover and properly mitigate vulnerabilities. But when it’s done right, this type of testing can help organizations significantly reduce the risk of data breaches in the long run.
If you are looking for a reputed and experienced penetration testing company, UnderDefense is the best choice for you. We are among the leaders in the field of cybersecurity solutions. Moreover, our team reaffirms the status annually by participating in Splunk’s highly competitive Boss of the SOC challenge. In 2023, the UnderDefense experts bagged 4th place out of over 185 participating teams.
Our ethical hackers have the perfect combination of business and technical competencies and in-depth practical skills. All of that allowed us to develop a creative approach to penetration testing and a distinctly individualized methodology. We offer a one-step-ahead service to track your organization’s vulnerabilities and effectively prevent breaches. Contact us today for a free pentest quote.
















