Have you experienced a cybersecurity breach or data security challenges? If so, you understand the importance of safeguarding your digital assets. To be fully armed against threats, you should know your vulnerabilities. And that is when you should consider a penetration test. The next move is selecting the most suitable type that aligns with your needs.
This article explores the types of penetration tests, approaches, and real-world applications. You will gain the insights to select the ideal approach and pinpoint your existing weaknesses. Knowing them will help you make better strategic decisions to fortify your digital defenses, all geared toward enhancing your business security.

What is penetration testing?
Penetration testing is a simulation of a real cyberattack. It involves a systematic evaluation process that uncovers vulnerabilities in your people, systems, or processes.
Your ultimate guide to different types of penetration testing
Before you decide on the perfect provider, it’s essential to understand the various types of pentesting. Each of them focuses on specific aspects of security evaluation. They can vary in what they concentrate on, how deep they go, and how long they take. Let’s explore this topic to help you make the best choice for your needs.
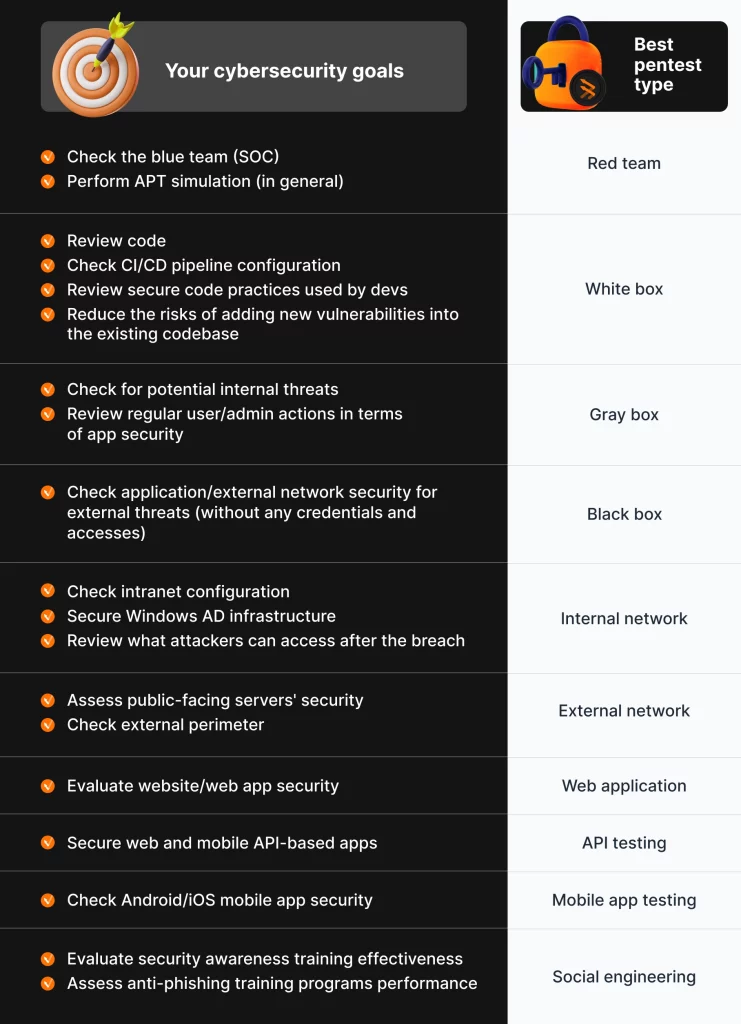
1.Network penetration testing (internal and external)
This type of pentesting involves internal and external assessment of an organization’s network infrastructure for vulnerabilities and security weaknesses. Experts simulate real-life attacks to identify probable entry points that cybercriminals could exploit. They analyze network architecture, configurations, and devices to help you discover misconfigurations, open ports, weak authentication mechanisms, and other access points.
The process involves:
- Passive and active scanning
- Vulnerability assessment
- Attempts to exploit identified vulnerabilities
- Lateral movement to access all parts of the network
- Post-exploitation to show the impact of found vulnerabilities
The goal is to provide insights into potential risks, prioritize remediation efforts, and enhance the network’s security posture.
Who needs network penetration testing?
Any entity relying on computer networks can benefit from this type of pentest: government agencies, financial institutions, healthcare providers, tech companies, critical infrastructure, and service providers.
2. Wireless penetration testing
This service aims to uncover vulnerabilities of wireless networks that malicious actors could use to access your digital ecosystem. It may involve attempts to bypass authentication mechanisms, gain unauthorized access to a network system, or intercept sensitive data. By emulating potential threat vectors, testers can pinpoint areas where defenses are weak.
Who needs wireless penetration testing?
Any organization using wireless networks should perform such tests to protect data and prevent unauthorized access.
3. Mobile penetration testing
This type of pen testing allows companies to discover and analyze existing security gaps in their mobile apps that could result in data leaks, unauthorized access, and reputation damage. The process combines manual and automated techniques. Creating scenarios replicating attacks helps identify codebase weaknesses and misconfigurations in mobile architecture.
Who needs mobile penetration testing?
It is essential for organizations that develop and use mobile applications (e.g., iOS, Android) and their associated APIs. This type of pentest is crucial before launching a new application or implementing substantial updates.
4. Web application penetration testing
As the name suggests, experts perform this type of pen testing to discover vulnerabilities in web solutions that could result in unauthorized access, breach, data compromise, and service interruptions. Ethical hackers investigate app design, code, and configuration using manual and automated techniques. The ultimate goal is to find vulnerabilities and provide insights to organizations about their app’s security posture.
To achieve the primary goal of web app pentests, security experts follow industry-standard methodologies, including OWASP Web Security Testing Guide, Open Source Security Testing Methodology Manual, and Penetration Testing Execution Standard. This process encompasses reconnaissance, threat modeling, vulnerability scanning, and manual testing.
Who needs web application penetration testing?
This type of service is critical for e-commerce companies, online service providers, and other firms with web applications. Additionally, it is recommended for public APIs before the initial launch or major update.

5. Social engineering campaign
Even with the latest firewalls, antivirus, and other security measures, businesses still remain vulnerable. Why? Because in most cases the weakest link in the entire security chain is not technology but the employees.
Social engineering involves manipulating or deceiving individuals to gain unauthorized access to sensitive information or systems. Attackers exploit human psychology and various tactics, such as phishing emails, text messages, and even AI technologies for Deepfake and Voice Synthesis.
Ethical hackers conduct social engineering campaigns where they collect valuable information to create customized scenarios. They maintain a flexible approach that adjusts to emerging social engineering tactics like spear-phishing, pretexting, and vishing. The aim is to help clients identify vulnerabilities, bolster employee resilience, and reduce susceptibility to social engineering attacks.
Who needs social engineering penetration testing?
It is crucial for all businesses, no matter how much an organization invests in hardware and software security. A social engineering campaign will help assess human risk as an attack vector in your company.
6. Cloud penetration testing
During this type of penetration testing, experts perform cyberattacks on your cloud infrastructure and assess configurations to discover weaknesses and possible entry points.
As cloud providers implement a shared responsibility model, testers focus on the vulnerabilities that are part of the client’s obligation. While the cloud service provider accounts for the security of hardware, network, and cross-tenant access, clients are responsible for the code and data security they deploy. Depending on the chosen cloud platform, security engineers will examine the setup for particular misconfigurations associated with that provider’s environment.
Who needs cloud penetration testing?
It is crucial for businesses utilizing cloud services: AWS S3 buckets for storage, GCP Compute engine for virtual machines, AWS Lambda for serverless applications, Microsoft Entra ID (prior Azure AD) for identity management, and more.
to help you respond to known threats and whatever new tomorrow will bring
7. IoT penetration testing
This type of pentesting evaluates Internet of Things (IoT) devices for security vulnerabilities and existing misconfigurations. Its goal is to detect weaknesses and suggest realistic safeguards that will not disrupt business processes or require device reengineering.
This service involves simulating attacks on IoT devices and communication protocols to check each chip/component for known vulnerabilities, such as side-channel attacks, memory leaks, power glitching, etc. It helps to ensure the hardware design is security-focused. In terms of software, penetration testers will examine communication protocol gaps, including but not limited to Wi-Fi, Bluetooth, RFID, ZigBee, Modbus, or other custom-made protocols.
Who needs IoT penetration testing?
IoT penetration testing is critical for businesses and industries relying on IoT (e.g., smart devices, industrial automation, ICS/SCADA systems) to ensure data protection and prevent unauthorized access.
8. Red team attack simulation
Red teaming is a comprehensive and structured cybersecurity assessment approach designed to uncover vulnerabilities and weaknesses within an organization’s overall security posture. It goes beyond traditional penetration testing by simulating sophisticated and persistent cyberattacks that mimic the tactics, techniques, and procedures (TTPs) employed by real adversaries. Red teaming can also help organizations comply with regulatory requirements and strengthen their overall security posture.
Who needs a red team attack simulation?
It is valuable for organizations that require a thorough evaluation of security measures, especially those in high-stakes industries like finance, healthcare, government, and critical infrastructure.
The most popular approaches to penetration testing
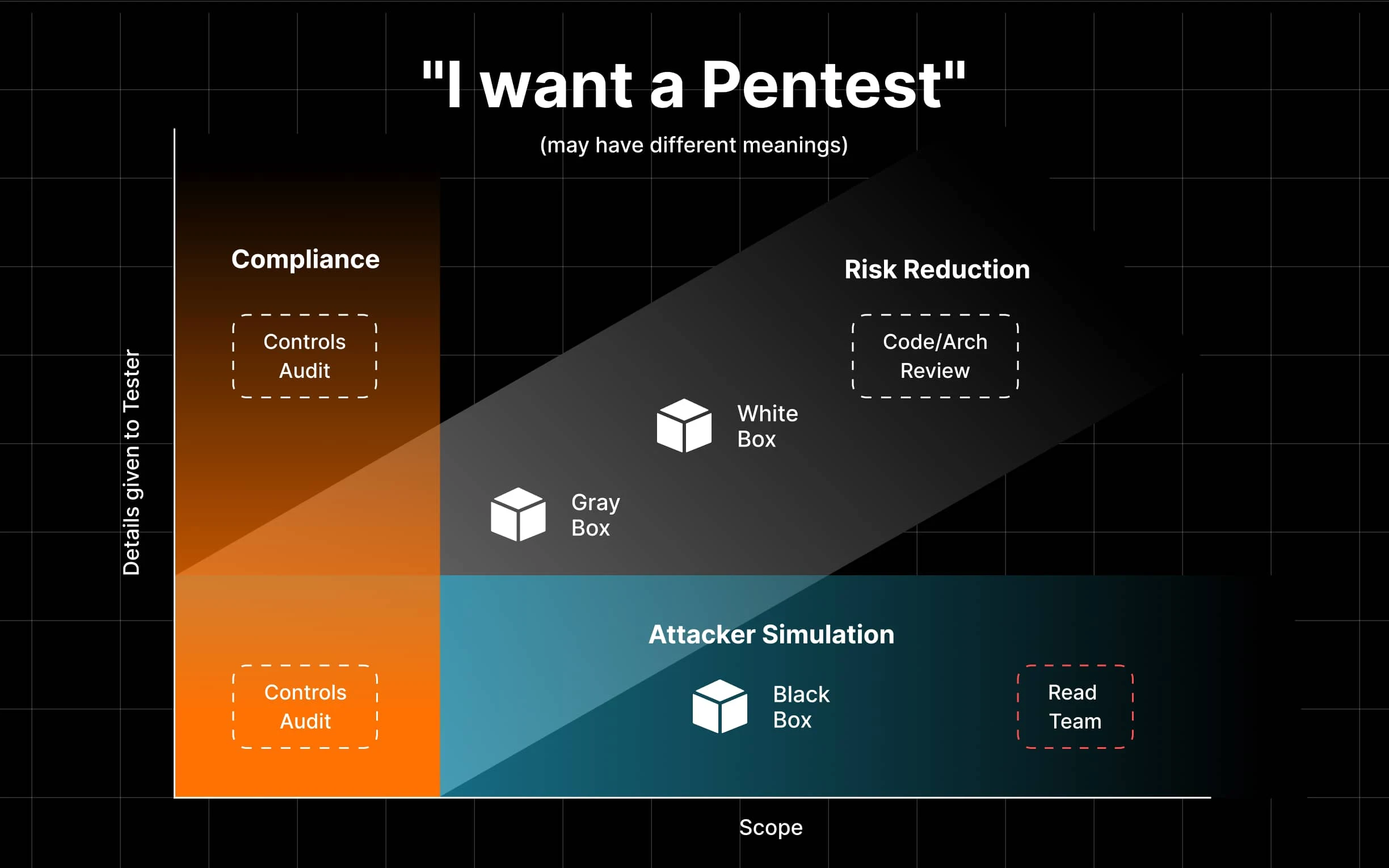
Apart from penetration test types, there are three fundamental approaches to penetration testing, including:
Black box (zero knowledge)
It is a simulation of an external cyberattack on a company’s domain or application environment. Ethical hackers have limited information, typically just the link to the target system. The objective of black box penetration testing is to identify vulnerabilities and potential entry points solely based on external-facing components.
Pentesters utilize various tools, techniques, and methodologies the attacker could use. They perform reconnaissance, scanning, vulnerability assessment, and exploitation attempts.
The advantage of black box testing is that it provides an unbiased assessment from an outsider’s perspective, mimicking real-world attack scenarios.
Gray box (basic knowledge)
This approach involves starting the assessment with a certain level of access already granted. This information is typically provided by the client or obtained through limited access to the system. The level of shared information may vary, but testers usually have access to some documentation, login credentials, or network schemes.
The goal of this testing methodology is to emulate the actions of a motivated attacker who has obtained a minimum level of access. By adopting this perspective, the pentest team can uncover vulnerabilities that may have been overlooked during regular security assessments.
White box (full knowledge)
During such assessments, penetration testers have complete internal visibility, including access to the system’s functionality, architecture, configuration, and implementation details. They also have access to the application’s source code, database schemas, system documentation, and other relevant information.
Ethical hackers can perform activities such as code review, static and dynamic analysis, configuration review, and architecture assessment. By having complete visibility into the system, they can identify weaknesses that may not be apparent from an external perspective.
As you can see, various types of penetration tests serve specific purposes. Choosing the most suitable one for your needs can be challenging. To provide clarity and assist you in making an informed decision, we’ve created a comparison table based on our clients’ most common requests.
Why penetration testing is important
Penetration testing is a fundamental component of a robust cybersecurity strategy. By proactively identifying vulnerabilities and addressing them, companies can protect their sensitive information, maintain customer trust, and avoid significant financial and reputational damage caused by cyber incidents.

So, let’s dive deeper into the benefits of penetration testing and see why it is a must-have for all business sizes and maturity levels.
1.Identify vulnerabilities and enhance incident response
All pentest types help uncover vulnerabilities in systems, applications, and network infrastructure. Addressing these issues before cybercriminals exploit them is essential for proactive defense. Additionally, pentesting allows organizations to fine-tune their incident response plans, thus minimizing damage, reducing downtime, and facilitating recovery in case of a breach.
2. Comply with regulations and ensure business continuity
Most industries have strict regulatory requirements for data integrity and confidentiality. Penetration testing services empower businesses to strengthen their overall cybersecurity and resilience. All that leads to better compliance with industry and local requirements and prevents them from legal consequences and heavy fines. Not to mention lower risks of operational disruptions, downtime, loss of productivity, and service unavailability.
3. Prevent financial loss and ensure better resource allocation
By conducting pentests and strengthening their business defenses, executives avoid financial losses caused by data breaches or cyberattacks. Such expenses may include recovery costs, regulatory fines, legal fees, and potential compensation to affected parties. Moreover, all pen testing types provide actionable insights allowing management teams to allocate their resources more effectively. It ensures that investments are directed toward addressing the most critical security gaps and minimizing financial risks.
4. Safeguard reputation and customer trust
A data breach or successful cyberattack can ruin a company’s reputation. News of it spread quickly, eroding customer trust and loyalty. Penetration testing helps prevent it all. Clients are more likely to engage with businesses that invest in their data integrity.
Penetration testing is not a one-time effort, but an ongoing process that adapts to evolving threats and technologies. Regular testing promotes continuous improvement and helps organizations stay ahead of potential attackers and boost their reputation.
UnderDefense can help with all types of pen testing

UnderDefense is a global cybersecurity provider, widely recognized by industry experts as one of the most powerful in the field. We meet the cybersecurity needs of international companies across various sectors including technology, online gaming, finance, healthcare, insurance, e-commerce, manufacturing, government, legal, etc.
UnderDefense pentest team offers comprehensive expertise in various types of penetration testing services, making us your go-to cybersecurity partner. Our ethical hackers unravel service weaknesses, skillfully exploit them, retrieve confidential data, and uncover network security gaps alongside code flaws in a multitude of projects.
When it comes to protecting your business, choosing UnderDefense means choosing a partner who is as invested in your security as you are. Our penetration testing services can benefit you directly, and here’s why:
- Expert team: We bring a team of experienced and skilled professionals who truly understand the ever-changing world of cybersecurity. We’re here to protect your unique business.
- Cutting-edge tools: We stay ahead of the game by using the latest tools and technology, ensuring that we catch vulnerabilities that others might miss.
- Real-life scenarios: Our tests replicate real-world attack situations, so you can be confident that we’re assessing your security posture in a way that matters.
- Proactive protection: We don’t just find problems, but we actively work to stop them before they become threats.
- Clear guidance: We provide you with easy-to-understand reports that empower you to take action and improve your security.
- Regulatory support: If compliance is a concern for you, we’ve got the expertise to help you meet those requirements.
- Your needs first: Your satisfaction and security objectives are our top priorities. We’re here to ensure that our services align perfectly with your goals.
Penetration testing types we provide:
You can explore our case studies to witness the tangible impact of our efforts and the variety of penetration testing types we provide. With UnderDefense, you’re not just getting a service – you’re partnering with experts dedicated to bolstering your cybersecurity defenses.
Let us help you ensure the safety and resilience of your digital environment. Discover our services today and set out on a path toward a more secure future.
FAQ
1.How do different types of penetration testing work?
Penetration testers emulate attacker techniques to exploit vulnerabilities and gain unauthorized access. Later they include all the findings into detailed reports and recommend actionable countermeasures to solve them.
2. Who needs penetration testing?
Any organization that uses computer systems, networks, or applications can benefit from penetration testing. It’s especially crucial for businesses that collect and store sensitive data, and those obliged to comply with regulations and standards.
3. How often should penetration testing be conducted?
Penetration testing should be conducted at least annually, with additional tests performed after significant changes to your systems, security incidents, or as required by compliance regulations.
4. Is penetration testing legal?
Yes, all pentesting types are legal when performed with proper authorization from the system owner. Unauthorized testing is illegal and can lead to legal consequences.
5. How long does a penetration test take?
The duration depends on the scope and complexity of the test. It can range from several days to weeks, including planning, testing, analysis, and reporting.