In today’s interconnected digital landscape, securing your organization’s external perimeter goes beyond mere compliance. In fact, it’s your first defense line against ever-evolving threats and growing cyberattacks. And since your organization is complex and dynamic, checking all assets once doesn’t guarantee security tomorrow.
Ensuring that your public-facing perimeter is reliable and consistent requires regular checks, which sooner or later will turn into a tedious and time-consuming routine requiring additional human resources. That’s why having the right partner makes this complex journey more manageable. Whether you’re a small startup struggling to grow and deal with shadow IT or a global enterprise managing a vast digital footprint, this guide will provide practical insights on choosing the ideal attack surface management vendor. So, let’s dive in and explore the leading contenders in this crucial pursuit of digital security.
The introduction to external attack surface management (EASM)
What is it?
EASM is a cybersecurity practice that continuously monitors, analyzes, and manages all organization’s internet-facing assets, identifies potential vulnerabilities and attack vectors, and prioritizes remediation efforts. This approach enables organizations to avoid external threats, demonstrating a commitment to security and fostering a resilient digital environment. It is crucial in today’s dynamic threat landscape as businesses expand their online presence.
Why do you need it?
The need for EASM arises from the growing complexity of digital landscapes, including myriad web/mobile applications, networks, and multi-cloud infrastructures. As organizations adopt new technologies, the attack surface expands, providing more opportunities for potential cyber threats. This type of service helps businesses proactively assess and mitigate current and future risks, improve incident response, and maintain compliance.

Benefits of external attack surface management for business
Attack surface management is a crucial tool for organizations seeking to protect themselves against growing cyberthreats. Below some of the key advantages it has to offer:
- Risk reduction as security teams can proactively identify and address vulnerabilities before they can be exploited. ASM translates into more efficient incident response, enabling faster reaction to potential threats.
- Better compliance with cybersecurity regulations, ensuring that organizations align with industry standards. By doing so, they prevent legal repercussions and improve their brand reputation. They may consider partnering with cybersecurity compliance services providers for assistance.
- Prevention of financial fallout caused by cyberattacks, including the substantial costs of data breaches and downtime.
- Improved view of security investment outcomes and more effective allocation of resources.
- Better understanding of the attack surface allowing IT decision-makers to prioritize the next steps and remediation efforts based on actual risks.
The most common risks in your external attack surface
Businesses today are often judged by their ability to secure external-facing assets, making EASM an integral part of maintaining a good reputation. The threat landscape constantly evolves, with new attack techniques and technologies emerging regularly. Meanwhile, your organization expands its online presence and corporate infrastructure, adding more partners, business units, subsidiaries, and more.
All these factors force you to proactively mitigate and prioritize external attack surface risks to protect your valuable assets from harm because only a secure organization is successful. To help you achieve that, we list the most common external attack surface vulnerabilities that you should be aware of:
- Unpatched software and open ports. Outdated software often contains known vulnerabilities that attackers can exploit. Unnecessarily open ports on firewalls and servers can provide direct access to internal systems. Organizations can engage in regular penetration testing services to proactively identify and address these weaknesses before they’re exploited.
- Insecure APIs. Application programming interfaces (APIs) are essential for enabling communication between applications. However, insecurely designed or implemented APIs can expose sensitive data and functionality to unauthorized users.
- Cloud misconfigurations. Cloud services offer a range of benefits, but misconfigured cloud resources create significant security risks. Exposed storage buckets, overly permissive access controls, and insecure configurations can all leave data vulnerable to attacks.
Explore our article on Google Workspace security best practices for insights on ensuring ultimate G Suite security. - Third-party vulnerabilities. Organizations rely on a vast ecosystem of third-party vendors and partners. However, third-party product and service vulnerabilities create indirect risks for your organization.
- Shadow IT. Unapproved and unmanaged use of technology, such as personal devices, new software, or cloud applications, creates significant security risks.
- Zero-day attacks. In such cases, hackers exploit previously unknown vulnerabilities, making them particularly difficult to defend against. Staying up-to-date on security patches and implementing defense-in-depth strategies can help mitigate zero-day attack risks.
For a more in-depth understanding of solutions that can fortify your defenses, check out our article on the top 10 must-have cybersecurity solutions for SMBs.
5 best attack surface management vendors
Staying ahead of vulnerabilities and misconfigurations in your organization and vendor networks is crucial for effective security. Fortunately, automated Attack Surface Management (ASM) software can centralize this process, providing a single platform for monitoring and managing potential threats.
With numerous solutions available, choosing the right one for your organization can be overwhelming. This guide will help you navigate the critical considerations of effective ASM software and highlight some of the best available options.
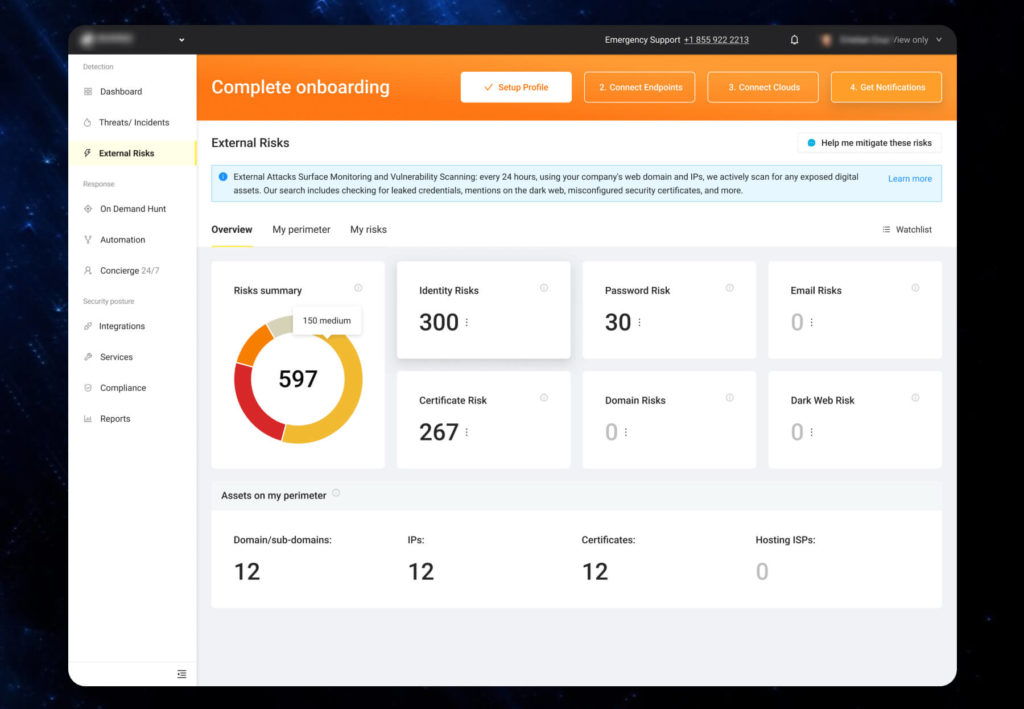
UnderDefense MAXI is a powerful attack surface management platform that empowers organizations to effectively monitor, detect, and manage vulnerabilities within their digital ecosystems. The platform offers a centralized solution for securing business attack surfaces, eliminating the need for multiple disjointed tools.
Key features:
- 360° security visibility: Gain real-time insights into your entire attack surface, including unmanaged assets, unused servers, and legacy systems. You will discover vulnerabilities and risks early before they can be exploited.
If you want to know how to turn this vast amount of data into actionable intelligence, read our article on how correlation rules can supercharge your security operations. - Automated security processes: Accelerate and streamline such checks as leaked business credentials, dark web monitoring, and misconfigured security certificates with AI-powered automation available right out of the box. Free up your in-house security team to focus on more strategic initiatives.
- 24×7 concierge service: Get professional advice or assistance whenever you need it with a 24×7 expert team backed by MDR capabilities. They are available via live chat or phone to answer your questions and help resolve any issues.
- Clear remediation steps: Hear actionable recommendations and guidance for remediating vulnerabilities quickly and effectively. It ensures you take the proper steps to address risks before they evolve into real security incidents.
- User-friendly dashboard: Valuable insights, reports, and comprehensive analytics are available via the client portal anytime.

2. ManageEngine
ManageEngine Vulnerability Manager Plus is a comprehensive attack surface management solution that helps organizations identify, assess, and prioritize vulnerabilities across their entire digital ecosystem.
Key features:
- Vulnerability scanning: Identify misconfigurations, outdated software, and known vulnerabilities across various endpoints, including servers, workstations, applications, cloud resources, and network devices.
- Automated patch management: Streamline the process of downloading and applying patches, ensuring systems are up-to-date.
- Attack surface analysis: Uncover unmanaged assets, unused servers, and other potential vulnerabilities exposed to the internet to shrink your attack surface.
- High-risk software audit: Detect and flag unauthorized or unsupported software on the network, mitigating potential vulnerabilities associated with outdated programs.
- Zero-day vulnerability mitigation: Guidance and recommendations to help mitigate zero-day vulnerabilities before patches become available.

3. Tenable
Tenable Attack Surface Management is a comprehensive solution for organizations that want to gain complete visibility into their external attack surface, identify potential threats, and take proactive steps to mitigate risks.
Key features:
- Complete visibility: Continuous mapping of the entire internet and real-time discovery of connections to internet-facing assets.
- Asset discovery and mapping: Attack surface map with over 5 billion assets and continuous monitoring with change notifications.
- Business context integration: 200+ metadata fields for insights and streamlined asset management with filters and tags.
- Seamless risk assessment: Integration with Tenable solutions and comprehensive scanning for unknown assets.
- Legal compliance: Identifying non-compliant technology and legal issues.

4. Group-IB
Group-IB Attack Surface Management is a comprehensive and user-friendly solution for organizations seeking to proactively manage their attack surface and improve their overall security posture.
Key features:
- Attack surface analysis: Visualize external attack surface, identify vulnerabilities, and prioritize remediation efforts.
- Continuous discovery: Benefit from automatic mapping of the attack surface, ensuring you always have an up-to-date inventory.
- Risk assessment: Prioritize remediation efforts by assigning risk scores to vulnerabilities based on their severity and exploitability.
- Advanced threat intelligence insights: Access industry-leading data on malware, botnets, phishing, dark web mentions, and more.
- Customizable notifications and reporting: Get alerts and reports to stay informed and demonstrate security improvements to stakeholders.

5. CyCognito
CyCognito Attack Surface Management is a powerful and user-friendly solution to help organizations navigate the ever-changing digital landscape and proactively secure their digital assets.
Key features:
- Deep and continuous discovery: Explore the hidden areas of the internet to find overlooked assets, misconfigurations, and exposed data, leaving no blind spots.
- Real-time risk assessment: Use advanced algorithms to prioritize vulnerabilities based on exploitability, severity, and potential impact, guiding the remediation efforts efficiently.
- Threat intelligence integration: Access vast threat intelligence feeds that help identify emerging threats and vulnerabilities before they exploit your weaknesses.
- Automated remediation playbooks: Customizable playbooks that automate vulnerability reporting, remediation workflows, and vendor communication.
- Actionable insights and reporting: A clear picture of the attack surface with intuitive dashboards and customizable reports.
Being prudent makes all the difference
Conclusion
Selecting the right attack surface management solution is crucial for safeguarding your organization against evolving cyberthreats. Each of the five solutions we’ve discussed excels in specific areas, offering diverse functionalities and strengths.
However, if you’re seeking a comprehensive, innovative, and cost-effective solution that prioritizes automation, real-time threat intelligence, and proactive vulnerability management, then UnderDefense MAXI stands out as a champion. Its powerful features, seamless integration, and customizable approach give you full control over your attack surface. Security is not a destination, it’s a journey. UnderDefense MAXI isn’t just a tool, it’s a reliable partner to make this journey smooth and safe.
Contact UnderDefense today and unlock your MAXImum security potential.
















