The use of Google Workspace cloud applications like Google Drive and Gmail can help companies significantly boost workforce productivity and collaboration. On the other hand, G Suite comprises vital business information like emails, documents, and calendars, making it an attractive target for cybercriminals. So, protecting this ecosystem is paramount, given the sensitive data and communication it manages.
Entrust your Google Workspace protection to experts.
Without proper mechanisms and procedures to monitor and protect the G Suite environment, organizations can become vulnerable to the exposure of critical data. Currently, the best way to minimize these potential risks and ensure the utmost security is by enhancing threat visibility and enabling instant prevention and response to attacks using Google Workspace security best practices. So, check out important lessons described below and find out how to apply them in practice.
Disclaimer: These lessons are based on top Google recommendations and our advice to help you achieve ultimate security and proactively and reactively respond to threats.
Table of Contents
- Lesson #1: Lock the doors: the peril of weak passwords – swift entry for attackers
- Lesson #2: Guard the vault: monitor data sharing to safeguard your digital treasures
- Lesson #3: Shield the gateway: avoid using Google accounts for external sign-inss
- Lesson #4: Fortify defense: guarding against phishing emails targeting employees
- Lesson #5: Calendar lockdown: ensuring privacy and security for your Google calendar
- Lesson #6: Meet with confidence: strengthen security in Google Meet
- Lesson #7: Locking in privacy: ensuring secure chats with Google
- Lesson #8: Guard your Chrome: enhancing Google Workspace security through the browser
- Lesson #9: Aware minds & safe corporate environment: the imperative of user training in Google Workspace security
- Lesson #10: Advanced Google Workspace protection: activate security monitoring through prebuilt and custom rules
- Unlocking enhanced Google Workspace security with UnderDefense
Lesson #1: Lock the doors: the peril of weak passwords – swift entry for attackers

Why is it important?
Passwords are the first line of defense against unauthorized access to your G Suite environment. Setting high requirements for password length and strength is reasonable because it helps you protect your sensitive data.
Steps you should take
1.Implement and monitor robust passwords. Introduce strong password policies and create a separate policy that enforces regular password changes.
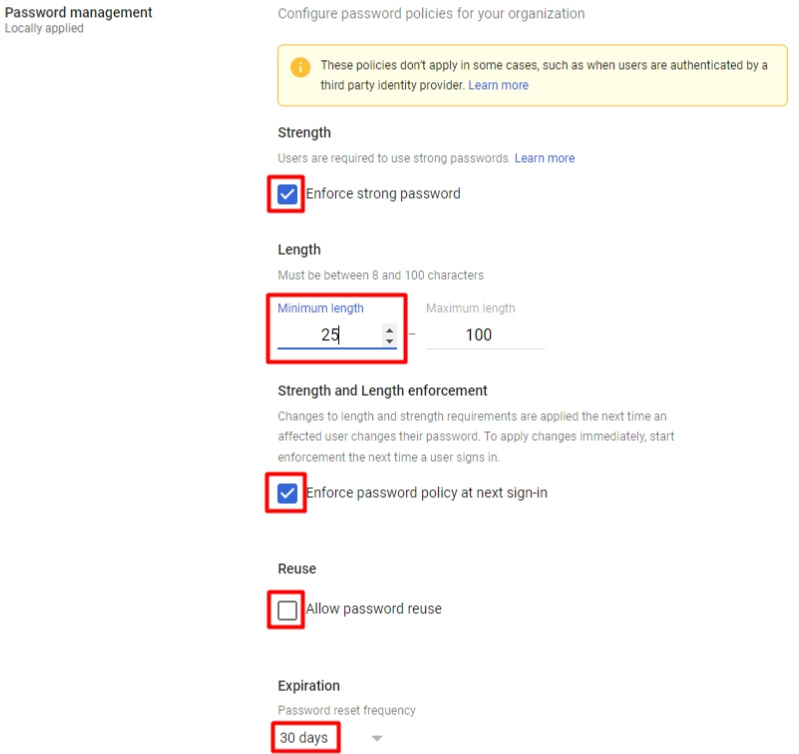
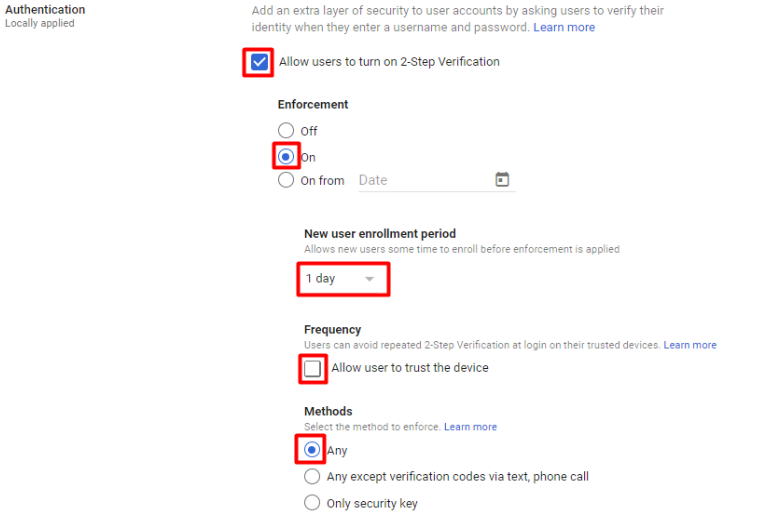
2. Configure 2-Step Verification (2SV) for all accounts. Give priority to accounts dealing with sensitive data.
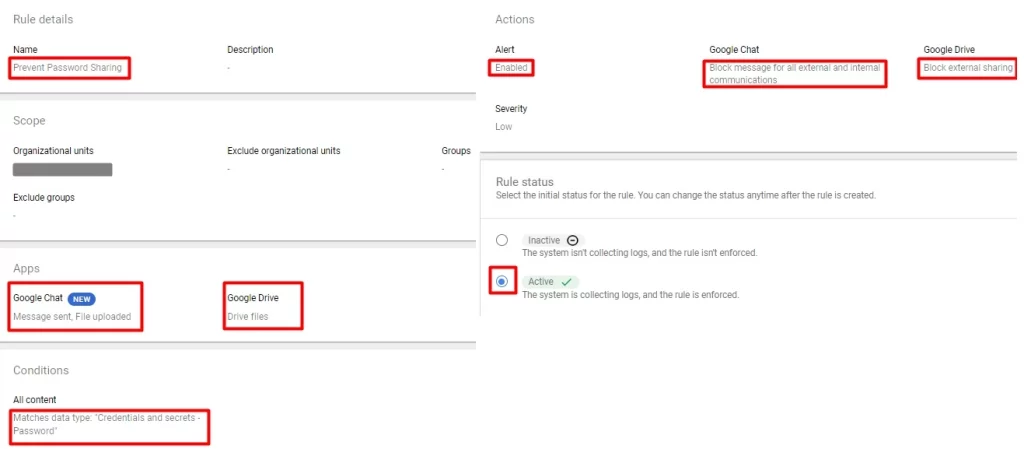
3. Enable data loss prevention (DLP) rules for password sharing. Creating complex rules will help you prevent data leaking.
Lesson #2: Guard the vault: monitor data sharing to safeguard your digital treasures

Why is it important?
It’s worth noting that Google Workspace’s default settings allow users to share sensitive corporate information with anyone. One careless action by an employee—such as sending an email via Gmail, shooting a message via Google Chat, or granting access to a document on Google Drive—can result in immediate and irreversible critical data leakage.
Steps you should take
1.Regulate the entire employee life cycle. Create a workbook with clearly defined internal procedures for granting access to new employees and revoking it when an individual leaves. Communicate that to the staff and ensure strict adherence to the rules. Documented procedures are among the most important elements of your G Suite security checklist.
2. Implement role-based access control. Such an approach guarantees that users get only the permissions necessary for their specific roles. It minimizes the risk of unauthorized access to sensitive data and its sharing.
3. Structure the data on Google Drive. By doing that, you will facilitate and enhance the management of access rights and permissions. Sensitive information can be restricted to specific individuals or groups, reducing the risk of data breaches. Additionally, this step also helps improve navigation, collaboration, and scalability.
4. Define appropriate external sharing options for Google Drive and Gmail within your domain. Pay particular attention to the restriction of sharing to specific domains. Also, consider establishing distinct sharing configurations for both folders and documents.
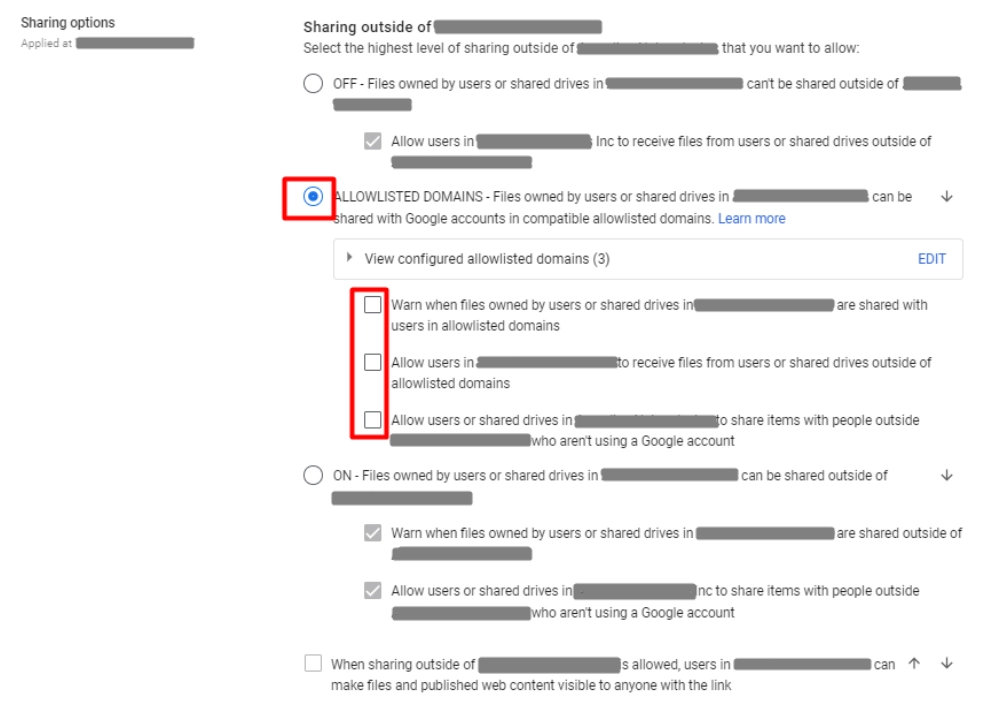
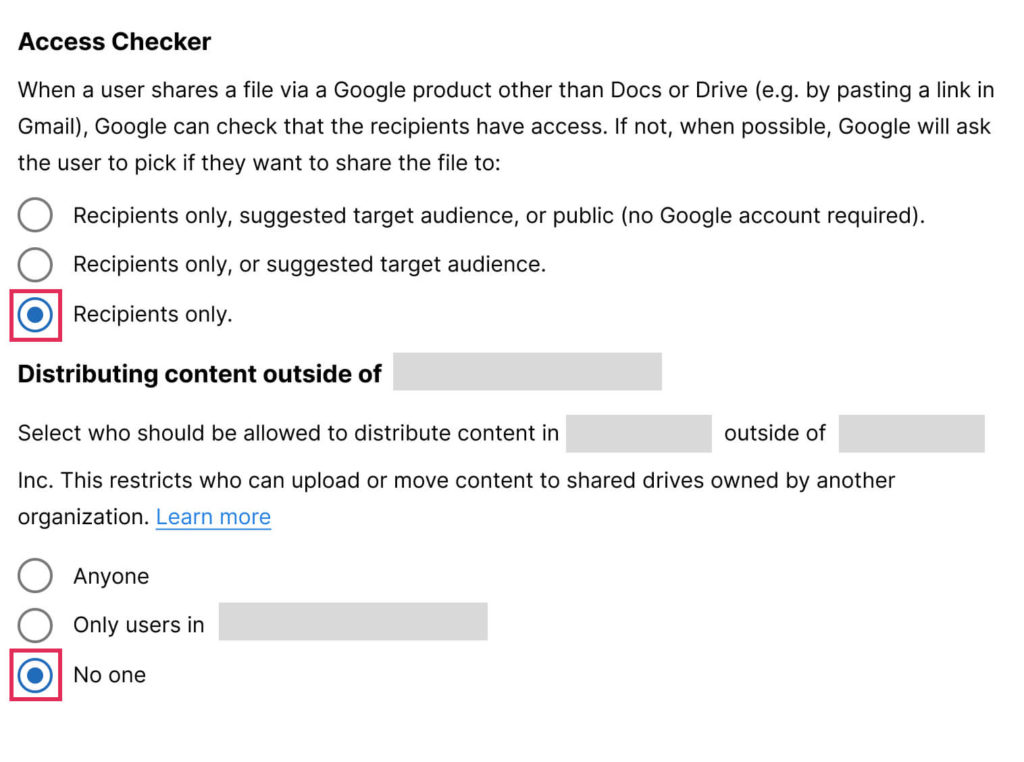
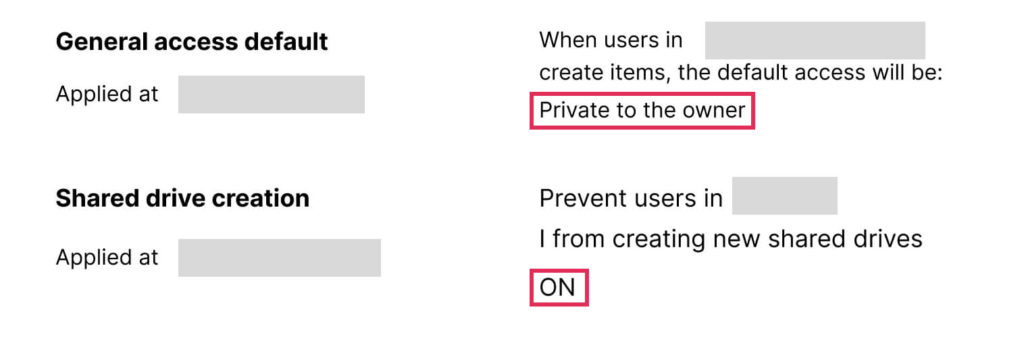
5. Configure data loss prevention (DLP) rules: Use this feature to detect and prevent sensitive data sharing, such as credit card numbers or Social Security numbers via Google Drive, Google Chat, and Gmail to enhance G Suite cyber security inside your organization.
Lesson #3: Shield the gateway: avoid using Google accounts for external sign-ins
Why is it important?
Numerous online services and applications offer the convenience of signing in with Google accounts. Many people opt for this approach because it eliminates the need to create a new profile. By default, Google Workspace allows individuals to use their accounts for that.
However, when employees utilize their corporate Google accounts to log into external services, they grant the app the same level of access as they have, often without even knowing that. For instance, an application might request write access to the user’s Google Drive, which from a business perspective, poses a significant risk.
Steps you should take
1.Control data access for all internal and external services. Determine the scope of work-related Google account usage for employees and ensure that only safe apps can use Google accounts for sign-ins (such as Slack). Alternatively, consider disabling access to external services.
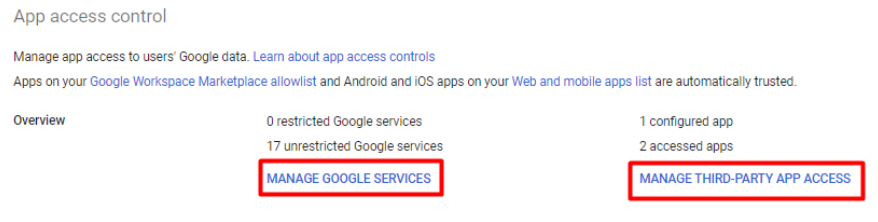
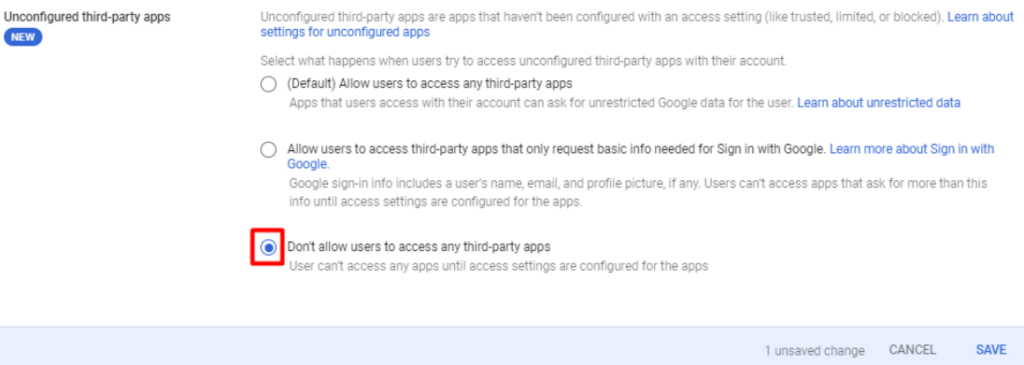
Lesson #4: Fortify defense: guarding against phishing emails targeting employees

Why is it important?
Phishing emails often serve as a gateway for cybercriminals to gain unauthorized access to sensitive information, personal data, and confidential business details. These incidents can have a detrimental impact on the company’s clients, partners, and overall reputation. Another significant risk is financial losses resulting from fraudulent transactions, unauthorized fund transfers, or fake invoice payments. Additionally, these emails frequently contain malicious attachments or links that can admit malware or ransomware into corporate systems.
Steps you should take
1.Activate Google’s pre-delivery scanning option. This feature scans all messages before delivery, making it one of the crucial G Suite email security options to enable. If it detects suspicious content, it conducts further checks. If suspicions persist, the message is sent to the spam folder. If no issues are found, the message is directed to the inbox.
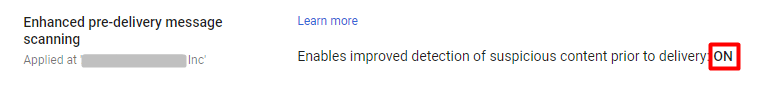
2. Set Gmail filters to allow messages only from approved senders. G Suite email security best practices also offer the option to create whitelists and blacklists specific to your environment for additional protection.
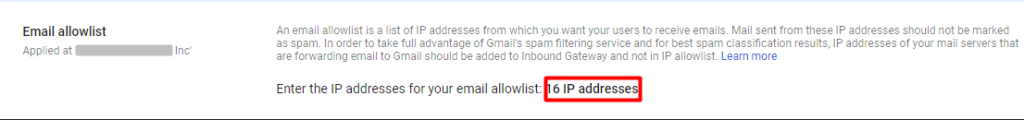
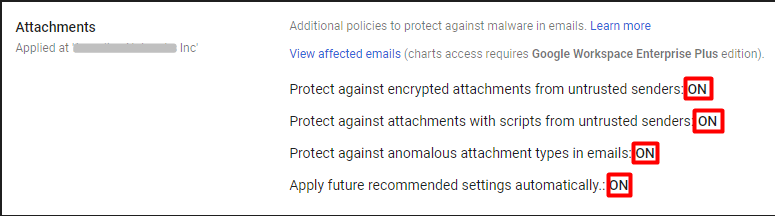
3. Configure protection for attachments. Google’s Attachment Protection is also one of the most valuable G Suite security features that can effectively handle encrypted attachments, untrusted sender scripts, and unusual attachment types.
4. Introduce a Sender Policy Framework (SPF). This feature designates authorized mail servers for your domain to minimize spoofing and phishing risks. Additionally, SPF helps the receiving servers confirm legitimate messages from your domain.
5. Implement DKIM and DMARK. DKIM adds encrypted digital signatures to thwart spoofing, while DMARC provides attack reports, enhancing vulnerability detection.
6. Disable external email auto-forwarding. Compromised accounts often activate auto-forwarding to external addresses, facilitating phishing, data leaks, and payment redirection. It can also signal internal data leakage.
Lesson #5: Calendar lockdown: ensuring privacy and security for your Google calendar
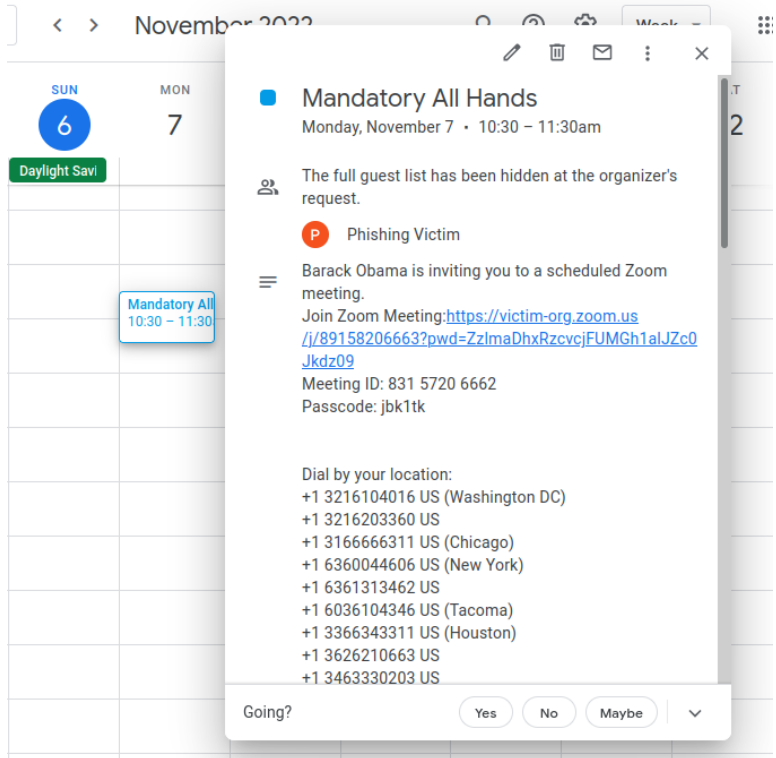
Why is it important?
Google Calendar often contains sensitive information such as appointments, meetings, and events. It can unveil personal and professional schedules, contacts, and locations. Insecure calendars can be exploited for phishing attacks and scams. Tampering with calendar events can cause confusion, missed appointments, and miscommunication, impacting personal and business operations. Unauthorized access can lead to the exposure of private data.
Steps you should take
1.Review and adjust calendar privacy settings. Start with limiting event visibility to only necessary participants to control who can see your events.
2. Share calendars only with trusted users. Regularly review who has access to your shared calendars and remove any unauthorized users.
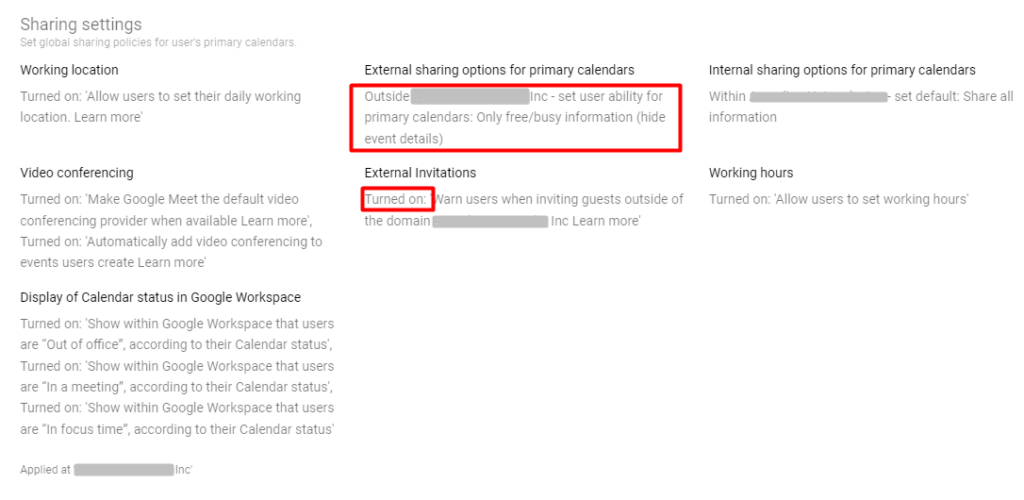
3. Avoid sharing sensitive details in event descriptions and titles.
4. Check and revoke access permissions for apps linked to your Google Calendar. Ensure any applications or extensions you no longer use do not have any access to the calendar.
5. Turn off the Google Calendar feature that automatically adds invitations to Calendars.
Lesson #6: Meet with confidence: strengthen security in Google Meet
Why is it important?
Google Meet is used for sensitive discussions, and unauthorized access can result in leaks of confidential information. So, take necessary actions to protect this data against unauthorized access and recording.
Steps you should take
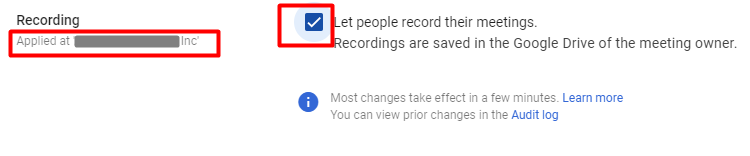
1. Configure recording options correctly. Ensure the recording option is enabled selectively for specific organizational units. Monitor all the recorded meetings carefully.
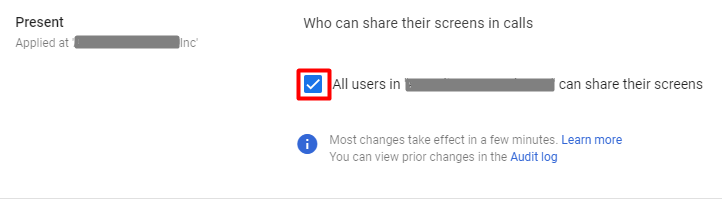
2. Manage screen sharing. Restrict the screen sharing option to authorized participants (based on organizational units) to prevent inadvertent demonstration of confidential data.
3. Secure with separate meeting rooms. Enhance security by assigning unique rooms for various sessions and ensuring only intended participants can enter.
Lesson #7: Locking in privacy: ensuring secure chats with Google
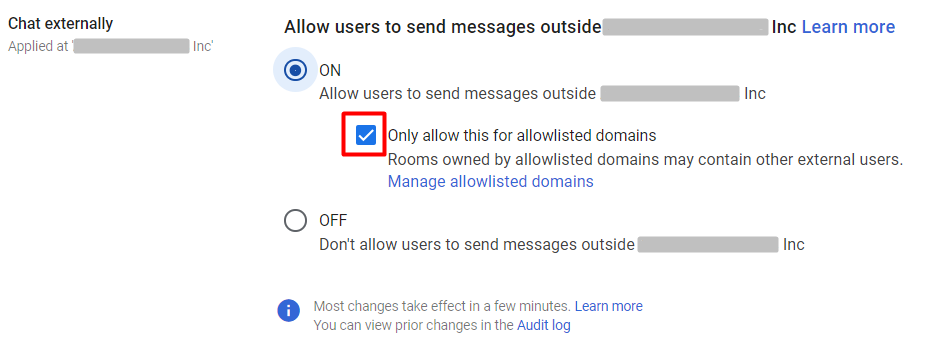
Why is it important?
Protecting the content of chats prevents unauthorized access to personal and confidential information shared within the conversations. Meanwhile, effective security measures prevent unauthorized users from gaining access to conversations, ensuring participants are legitimate and authorized.
Steps you should take
1.Enable External Chat for allowed domains only.
2. Enable DLP rules for sensitive information sharing in private conversations.
Lesson #8: Guard your Chrome: enhancing Google Workspace security through the browser
Why is it important?
Google Chrome is a primary gateway to online resources, making it a prime target for cyberattacks. Breached Chrome can expose stored passwords, resulting in unauthorized access to various online accounts. Vulnerable Chrome extensions can introduce malware, leading to data theft, system compromise, and identity fraud.
Protecting Chrome helps block phishing attempts and malicious websites, safeguarding users from scams and threats. By doing so, you also ensure sensitive corporate data remains secure during browsing activities.
Steps you should take
1.Manage extensions. This is one of the most useful G Suite security best practices for Chrome. Introduce the policy that helps specify all allowed and denied extensions to ensure users work only with safe and work-related extensions.
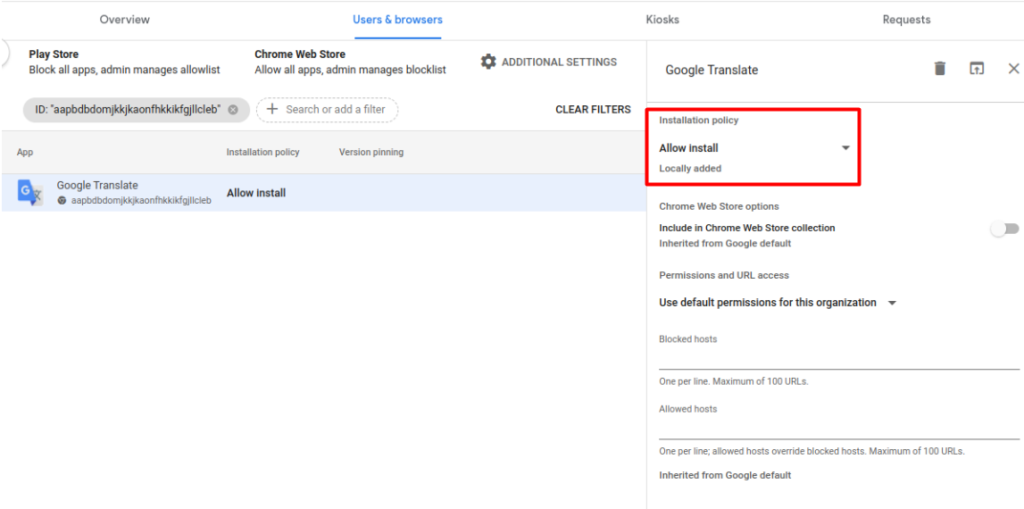
2. Enable built-in protections against phishing and malware. Chrome deploys Google’s Safe Browsing tech, alerting users about risky sites and downloads. Safe Browsing is on by default and can be enforced by admins to prevent user disabling.
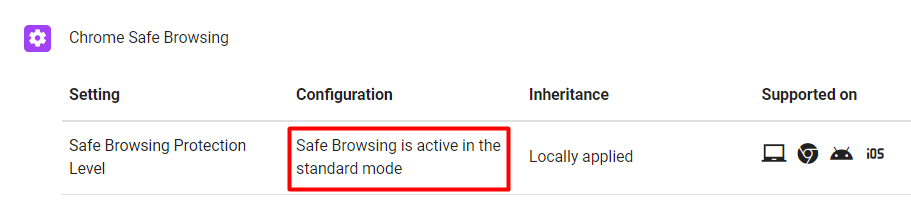
3. Ensure your browsers are regularly updated with the latest security patches. Such an approach will protect users from known and “zero-day” vulnerabilities.
4. Ensure that Google Workspace resources are only accessible from managed and updated Chrome Browsers using Context-Aware Access options.
Lesson #9: Aware minds & safe corporate environment: the imperative of user training in Google Workspace security

Why is it important?
Even if Google Workspace is secured with the great hardening of the environment, the main threat remains active. Any user, due to a lack of awareness about threats related to G-Suite security and daily work activity, quickly and easily becomes the weakest link, leading to breaches and data leaks. That is why it is important to train people and deepen their understanding of risks.
Steps you should take
- Assess the organization’s specific Google Workspace security needs, roles, and potential vulnerabilities. Tailor the training program accordingly.
- Customize the training program. Ensure it is relevant, engaging, and relatable to users’ daily tasks and responsibilities within Google Workspace.
- Make it clear. Use interactive elements (make GIFs, videos, quizzes, simulations, and real-life scenarios) to make it easier for users to understand the importance of security.
- Repeat. Offer regular training sessions to reinforce knowledge and keep users up-to-date with the evolving threat landscape.
Lesson #10: Advanced Google Workspace protection: activate security monitoring through prebuilt and custom rules

Why is it important?
Learning the previous 9 lessons from the Google Workspace security checklist and following the provided recommendations will help you protect the G Suite environment against various threats proactively. However, if you want to take security to the highest level and shift to a reactive mode, you’ll benefit from learning another advanced-level lesson.
Google Workspace offers numerous prebuilt security rules that cover a wide range of security scenarios and can be used to enhance monitoring processes in your environment. They are easy to implement and customize. By using them, you’ll be able to activate another level of protection – G Suite security monitoring. It helps to control the overall activity in your Google Workspace, quickly detect potential threats, and mitigate them as fast as possible. Sounds great, right?
But that’s not all. Additional G Suite data security benefits can be gained by creating and implementing custom rules based on audit logs. This approach can help you monitor more advanced cases and respond quickly to more complicated threats.
Steps you should take
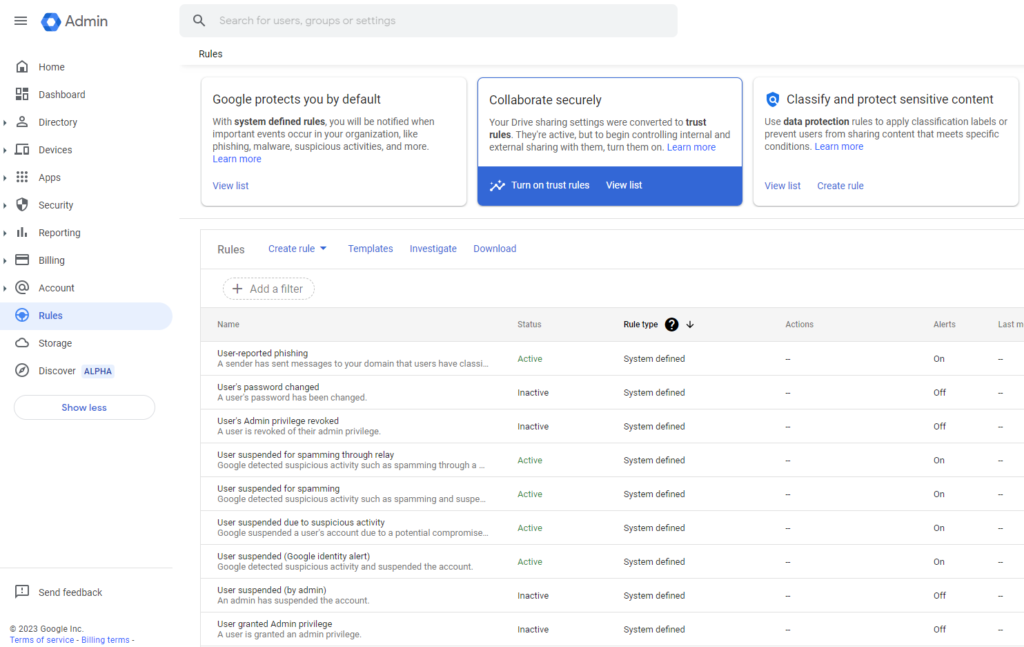
1.Enable prebuilt security rules. Below we list the top 10 recommended rules to try:
- User-reported phishing to detect potential phishing attacks targeting your employees. It empowers quick responses to prevent data breaches and unauthorized access.
- User-reported spam to identify patterns of spam emails and lets administrators take necessary action to prevent further spam-related issues and improve email security for Google Workspace.
- Malware message detected post-delivery to ensure that malicious content is recognized even after the initial scanning, preventing potential malware propagation within the organization.
- Suspicious login to unleash unauthorized access attempts, potentially indicating compromised accounts or security breaches, giving the opportunity to secure accounts.
- Gmail potential employee spoofing to prevent attackers from impersonating employees via email. This rule helps reduce the risk of social engineering attacks and sensitive data exposure, improving the overall G Suite email security.
- Domain data export initiation to stop unauthorized or accidental data exfiltration, ensuring that sensitive information remains under your control.
- Leaked password to proactively identify potential breaches of user credentials and mitigate the risk of compromised accounts and unauthorized access.
- Primary admin changed to maintain control over the organization’s administrative privileges, preventing unauthorized access and potential account hijacking.
- Super admin password reset to ensure that only authorized personnel are making such changes, reducing the risk of unauthorized account access.
- A suspended user is made active to prevent unauthorized reinstatement of accounts and ensure compliance with access control policies.
2. Create custom rules. Must-have custom use cases that you should focus on are the following:
- Set up DLP rules to eliminate the possibility of sensitive data sharing and protect confidential information from accidental or unauthorized exposure, maintaining confidentiality and compliance with data protection regulations.
- Detect spikes in sensitive data downloads/uploads to identify potential data exfiltration attempts and respond quickly, preventing data breaches and unauthorized data transfers.
- Check MFA policy modification to exclude unauthorized changes to security settings, ensuring that strong authentication remains in place to protect user accounts from compromise.
- Control password policy modification activity to stop unauthorized changes to password requirements, maintaining strong security practices and unauthorized access.
- Track all new members being added to a privileged group to prevent unauthorized elevation of access privileges, reducing the risk of insider threats and ensuring that only authorized individuals have advanced access rights.
We also recommend you to:
- Ensure that the rules generate alerts in the Alert Center for a fast and easy investigation process.
- Use the G Suite Security Center and Alert Center to monitor all security issues.
- Set up email notifications for quick responses to potential threats.
- Utilize a SIEM solution or UnderDefense managed SIEM service to track alerts and logs consistently and constantly.
Of course, this is not the full list of useful use cases and Google Workspace security features that could help you improve G Suite visibility and control its security. Using different rules, either prebuilt or custom ones, to observe the environment makes sense only if alerts are monitored 24/7. However, this additional layer of security provides an opportunity to initiate an additional investigation right away and mitigate/prevent all the possible impacts as fast as possible.
Unlocking enhanced Google Workspace security with UnderDefense
The introduction of these security best practices can strengthen your defenses, minimizing common risks related to user activities, potential breaches, and unauthorized access. UnderDefense takes your security further by introducing continuous monitoring. We provide you with all the necessary capabilities to activate reactive security mode and detect and address suspicious behavior right away. This proactive approach bolsters protection against data breaches, phishing attacks, and unauthorized account access in real-time, ensuring rapid response.
With UnderDefense MAXI MDR + SOAR security-as-a-service platform backed by 24/7 concierge team, your Google Workspace enterprise security can become record high. Together, we safeguard sensitive information and uphold the integrity of your business operations.
Here is what we offer:
MDR expertise: Our turnkey Managed Detection and Response (MDR) solutions ensure 24/7 monitoring of your Google Workspace. The UnderDefense team diligently watches your environment, precisely identifies suspicious activity, and neutralizes threats immediately.
SIEM integration: Security Information and Event Management (SIEM) is pivotal to modern security. UnderDefense helps you seamlessly integrate SIEM with Google Workspace to ensure real-time visibility into your security landscape. The synergy between MDR and SIEM ensures rapid incident response, keeping you ahead of potential threats.
Compliance services: Navigating the intricate world of compliance, whether it’s SOC2, ISO 27001, or industry-specific regulations, can be daunting. Compliance services and consulting offered by UnderDefense simplify this process, helping you meet all obligations while maintaining robust security practices.
By partnering with UnderDefense, you not only secure your Google Workspace but also elevate your business protection to a professional standard. Your G data security suite is up and running, so all information remains protected, your operations keep their integrity, and you can focus on your organization’s growth and success. Contact us today for a free quote.
Author: Anna Bondar
SOC Analyst at UnderDefense
















