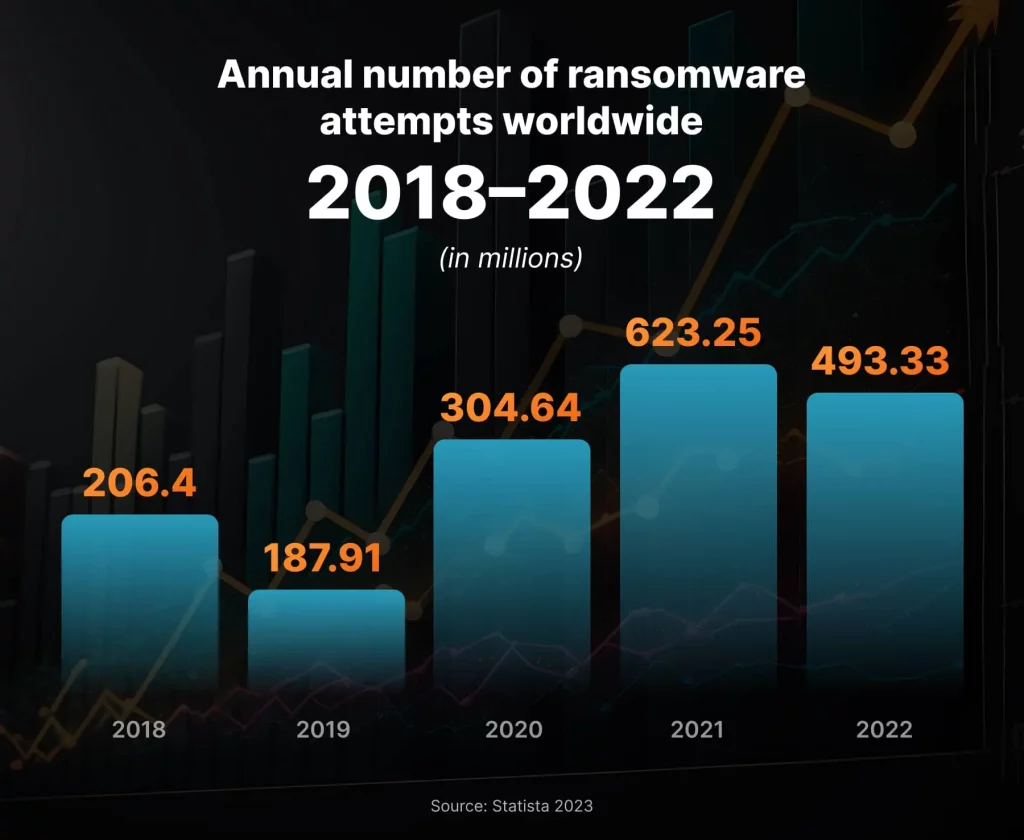
The growing number of cyberattacks makes penetration testing services a must-have for modern businesses. According to Statista, there were over 493 million ransomware attempts registered globally in 2022.
So no argument here: a reliable and secure infrastructure is an integral component of your organization’s cybersecurity. How can you ensure that? By conducting frequent network penetration tests. Such an approach empowers you to detect and proactively solve vulnerabilities that might be exploited by attackers.
With that said, we continue to introduce you to different types of pentests. In this article, we will discuss one of the trickiest topics, namely the difference between internal and external network testing. So, without further ado, let’s proceed to the definitions.
The definitions: internal vs external penetration testing
What is internal penetration testing?
Internal penetration testing is like performing an X-ray scan from within your organization. In this case, cybersecurity experts evaluate the security of your network, systems, or applications from the perspective of someone with legitimate access. The primary objective of the internal test is to simulate an insider threat, such as an employee or a compromised user, and uncover vulnerabilities that exist within your digital ecosystem.
Key characteristics of internal network penetration testing:
- Scope: Internal testing focuses on vulnerabilities that could be exploited by individuals with authorized access. It ensures the scrutiny of employees, contractors, and anyone within the organization’s trusted perimeter.
- Purpose: The primary goal of internal pentest is to identify and mitigate vulnerabilities stemming from misconfigurations, weak security policies, or imprudent actions of insiders. This approach reinforces defenses against potential insider threats.
- Methodology: Internal network penetration tests are often carried out by in-house cybersecurity teams, who employ tools and techniques that mimic the actions of insiders. They search for weak points in network architecture, access controls, and data security from within the organization.
- Advantages: Internal testing is effective in uncovering vulnerabilities that external testing might miss. It’s a critical tool for assessing the resilience of your security measures against potential insider threats.
- Limitations: It should be mentioned that internal penetration tests don’t provide a comprehensive view of your external exposure. Consequently, they don’t address vulnerabilities that could be exploited by external cybercriminals.
What is external penetration testing?
External penetration testing, on the other hand, assesses the security of your networks and systems from an outsider’s viewpoint using external threats and simulating real-world cyberattacks. Think of it as fortifying your digital castle walls against external adversaries, like hackers seeking unauthorized access from the vast expanse of the internet.
Key characteristics of external network penetration testing:
- Scope: External testing scrutinizes vulnerabilities that could be exploited by hackers and malicious actors without legitimate access to your network or system.
- Purpose: Its primary aim is to identify and rectify weaknesses susceptible to exploitation by external threats, ensuring the security of public-facing assets and preserving your organization’s integrity.
- Methodology: External penetration tests are typically conducted by third-party cybersecurity experts, ethical hackers employ a diverse array of techniques to unearth gaps in your external defenses. This includes evaluating firewalls, web applications, and remote access points.
- Advantages: External testing provides a holistic view of how effectively your defenses can withstand real-world attacks from external threats, ensuring the protection of your public-facing assets.
- Limitations: It may not uncover internal vulnerabilities, which remain hidden from external attackers, offering a unique perspective compared to internal network testing.
Penetration testing: internal vs external at a glance
As you can see, both services are essential for a robust business security strategy. Taking into account the complexity of threats and ingenuity of cybercriminals, it’s not a matter of choice anymore. So, let’s summarize the key points of external vs internal penetration testing into a brief table.
Internal penetration testing | External penetration testing | |
Scope and target environment | Focuses on the organization's internal networks, systems, and assets | Evaluates external-facing assets such as websites, servers, and applications |
Perspective | Assesses vulnerabilities from the viewpoint of a trusted insider, simulating employee actions to identify weaknesses exploitable by insiders | Emulates the actions of an external attacker, aiming to breach external defenses and uncover vulnerabilities accessible from the internet |
Access levels and authorization | Requires authorization and coordination with internal teams, as it involves testing within the organization's own network | Typically conducted without prior knowledge or access to internal systems, replicating an attacker's approach from outside the organization |
Objectives | Aims to uncover vulnerabilities associated with insider threats, assess internal security controls, evaluate employee training, and test incident response capabilities | Identifies vulnerabilities in public-facing assets, aiming to prevent data breaches, unauthorized access, and service disruptions caused by external threats |
Testing techniques | Uses methods like privilege escalation, lateral movement, and data exfiltration to simulate insider threats | Utilizes scanning tools, vulnerability scanners, and ethical hacking techniques to probe external-facing systems for weaknesses |
Security focus | Concentrates on strengthening internal security measures and addressing employee-related vulnerabilities | Focuses on bolstering perimeter security, securing public-facing systems, and guarding against external attacks |
Risk assessment | Helps organizations evaluate the risk of insider threats, including unintentional actions by employees | Identifies external vulnerabilities that could lead to data breaches, service disruptions, or unauthorized access by external attackers |
Compliance | Assists in meeting compliance requirements related to internal threats and the protection of sensitive data | Supports compliance by ensuring that external systems and data are adequately protected against external threats, aligning with regulatory standards |

Top 10 internal penetration testing examples
So, as you already know, internal penetration tests evaluate your security posture from within the organization. But what techniques and approaches do white hat hackers use? Below are ten most common examples of internal network penetration tests:
- Lateral movement testing: Testers attempt to move horizontally through the organization’s internal network to simulate how an attacker could escalate permissions and access sensitive data.
- Privilege escalation: Evaluate the effectiveness of access controls by attempting to escalate privileges, from standard user accounts to administrative or privileged access levels.
- Data exfiltration tests: Assess the ability to detect and prevent unauthorized data exfiltration by attempting to transfer sensitive information out of the organization’s network.
- Active directory assessment: Examine the security of Active Directory environments, including domain controllers, to identify weaknesses that could lead to unauthorized access or control.
- Application security testing: Analyze the security of internal applications, including in-house software, by identifying vulnerabilities like SQL injection, cross-site scripting (XSS), and insecure configurations.
- Social engineering and phishing tests: Assess employee susceptibility to social engineering attacks, such as phishing campaigns, pretexting, and baiting, from an internal perspective.
- Physical security evaluation: Evaluate physical security measures by attempting unauthorized physical access, including gaining entry to secured areas or bypassing security checkpoints.
- Endpoint security assessment: Test the security of internal endpoints, such as desktops and laptops, by identifying vulnerabilities, malware infections, and inadequate security configurations.
- Wireless network security testing: Assess the security of internal wireless networks, including Wi-Fi and Bluetooth, by identifying gaps and weaknesses in encryption and access controls.
- Insider threat simulation: Simulate insider threats by assessing the actions and behaviors of employees or contractors with access to sensitive data to identify potential security risks.
You have the right to know
Top 10 external penetration testing examples
External penetration tests highlight vulnerabilities in an organization’s external-facing systems and assets. How do ethical hackers achieve that? Below are the ten most common examples of external network penetration tests:
- Network scanning and enumeration: Testers scan the organization’s external IP addresses to identify open ports, services, and vulnerabilities that could be exploited by external attackers.
- Vulnerability assessment: Leverage solutions to conduct comprehensive vulnerability scans to identify known vulnerabilities in external-facing systems, including web servers, email servers, and firewalls.
- Web application testing: Assess the security of web applications by attempting to exploit common web vulnerabilities such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
- Phishing campaigns: Simulate phishing attacks to test how employees respond to email-based threats and to identify potential weaknesses in email security.
- Social engineering: Evaluate the organization’s susceptibility to social engineering attacks, including pretexting, baiting, and tailgating, to assess human-related security risks.
- Remote code execution: Attempt to gain unauthorized access to external systems by exploiting vulnerabilities that allow for remote code execution, such as buffer overflows.
- Password cracking: Test the strength of user passwords through password-cracking techniques, including dictionary attacks and brute-force attacks.
- Denial of service (DoS) testing: Assess the resilience of external-facing services and networks against DoS attacks by simulating high traffic loads or malicious attack patterns.
- Wireless network testing: Identify vulnerabilities in external wireless networks, such as insecure configurations, weak encryption, or unauthorized access points.
- Firewall and intrusion detection system (IDS) evasion: Evaluate the effectiveness of the organization’s perimeter security by attempting to bypass firewalls and IDS and gain unauthorized access.
Internal penetration testing vs external penetration testing: why both matter
In the ever-evolving landscape of cybersecurity, the adage “Know thy enemy” holds true, and that’s precisely why both internal and external penetration testing matter. Internal network testing is your key to understanding the subtle intricacies and potential vulnerabilities that hide within your organization’s digital fortress. By simulating insider threats and assessing your network from an inside-out perspective, you gain invaluable insights into the resilience of your security measures against those who have legitimate access.
Simply put, an internal penetration test is like performing a safety audit of your own home. You might discover a loose lock or a window that doesn’t close properly, issues that only become evident when you view your defenses from within. In a world where insider threats and accidental security lapses are real risks, internal testing is your safeguard, ensuring that your security is rock-solid from the inside, where it truly counts.
On the other hand, external penetration testing is the digital equivalent of a perimeter check, assessing how well your organization’s defenses hold up against external adversaries. Just as medieval castles had to fortify their walls against external invaders, your organization needs to protect against hackers who seek unauthorized access from the vast expanse of the internet. This type of testing reveals the chinks in your armor that might be targeted by malicious actors. It’s your opportunity to fortify those defenses, ensuring that your public-facing assets remain secure against real-world attacks.
In a world where external threats are a constant, external penetration testing is your sentinel, guarding your digital castle against the unrelenting siege of cyber adversaries. By combining both internal and external testing, you create a robust, multi-layered defense strategy, a veritable digital stronghold, equipped to repel all manner of cyber invaders.

Being prudent makes all the difference
Final thoughts
If you still doubt the necessity of external and internal penetration testing services for your organization, no problem. You can start with analyzing your exposure to external risks immediately and absolutely free. Sign up for UnderDefense MAXI platform with your business email address and get a real-time view of your security posture in minutes. Let the system automatically monitor your risks, update the dashboards every 24 hours, and notify you when a genuine threat requiring your attention is detected. Start small and try now with UnderDefense MAXI.
















