Everything you need to know about MDR services, benefits, specifics, pricing, and vendors. Whether you’re beginning to enhance your defenses or already seeking a solution, this overview is for you.
Table of Contents
- How does MDR work?
- Challenges that MDR can help you resolve
- Why invest in MDR? Top benefits for your business
- The most important things to pay attention to when choosing an MDR provider
- MDR cost – how is it calculated?
- UnderDefense MDR pricing models
- Top MDR vendors
- UnderDefense Turnkey MDR: your trusted partner for 24/7 business protection
How does MDR work?
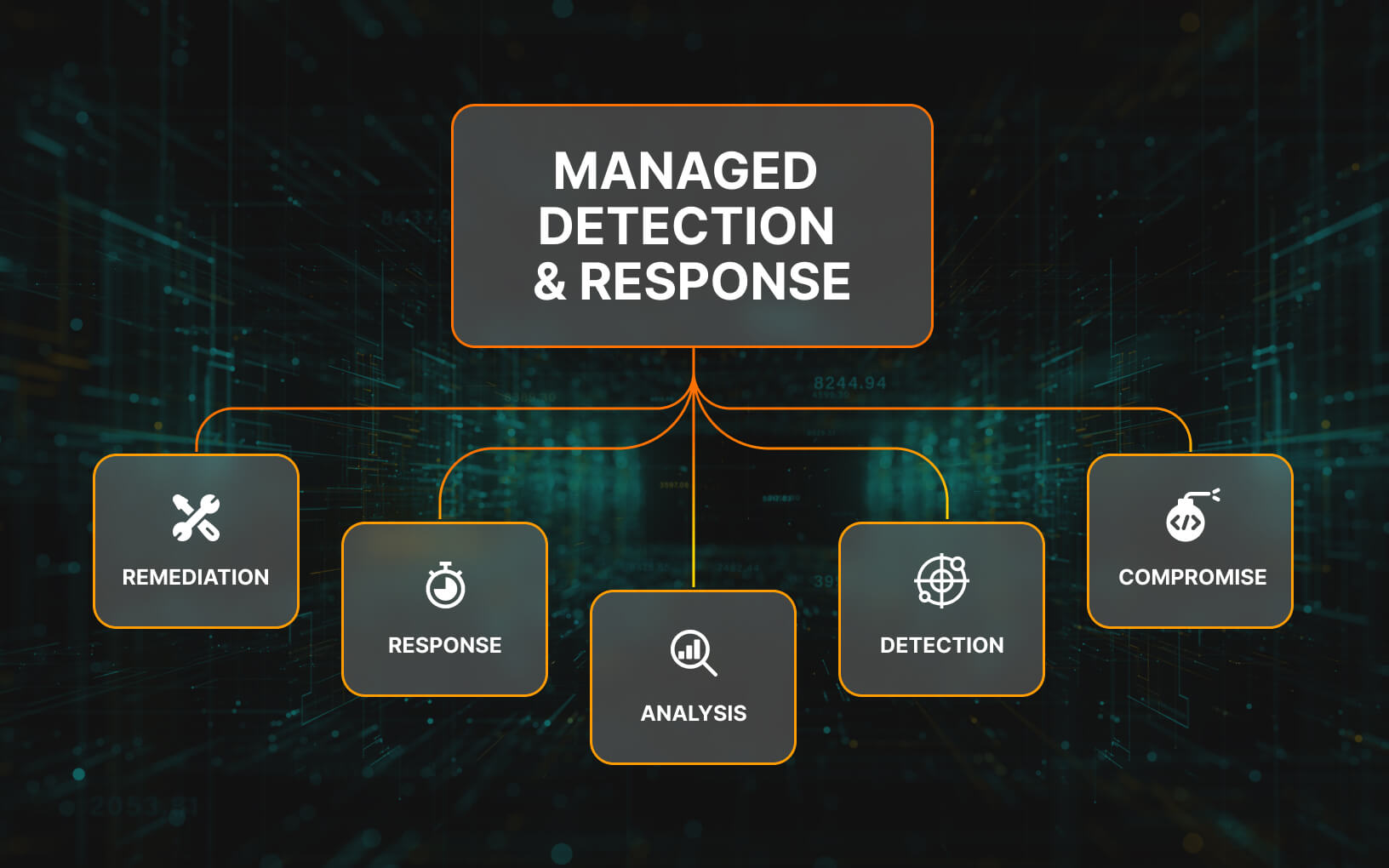
Managed Detection and Response (MDR) combines advanced technology, expert human analysis, and proactive threat hunting to detect, respond to, and mitigate cyber threats effectively. Here’s how it typically operates:
- Continuous Monitoring: MDR solutions monitor your organization’s networks, endpoints, servers, cloud environments, and other IT assets for any signs of suspicious activity or potential security breaches.
- Threat Detection: MDR solutions use security tools, including endpoint detection and response (EDR), network traffic analysis, log monitoring, and behavioral analytics, to identify indicators of compromise (IOCs) and potential security incidents.
- Alert Triage and Validation: When potential threats are detected, MDR analysts triage and validate each alert to determine its severity and legitimacy. This involves investigating the root cause of the alert, analyzing relevant data and logs, and assessing the potential impact on the organization.
- Incident Response: In a confirmed security incident, MDR analysts orchestrate an incident response plan to contain, eradicate, and recover from the threat. This may involve isolating compromised systems, mitigating further damage, and restoring affected services to normal operation.
- Proactive Threat Hunting: MDR providers proactively hunt for hidden threats and vulnerabilities that automated tools may miss. This involves analyzing historical data, conducting threat intelligence research, and identifying potential risks before they escalate into full-blown security incidents.
- Continuous Improvement: MDR solutions continuously refine and improve their threat detection capabilities based on real-world data and emerging threats. This iterative process ensures the organization’s security posture remains resilient against evolving cyber threats.
- Integration of MDR with Managed SIEM: This integration combines MDR’s continuous monitoring and advanced threat detection capabilities with the managed SIEM’s centralized log management and real-time event correlation.
Challenges that MDR can help you resolve
Addressing cybersecurity challenges requires innovative solutions that leverage the capabilities of Managed Detection and Response (MDR) services. Here’s how MDR can help organizations overcome common obstacles:
- Lack of human resources: Building and maintaining a skilled cybersecurity team can be expensive and time-consuming. MDR services bridge this gap by extending your security force with expert analysts who continuously monitor your systems, investigate threats, and orchestrate responses. This augmentation of human resources enhances your organization’s ability to effectively detect and respond to security incidents.
- Limited budgets and unclear pricing: Uncertain costs and budget constraints often hinder organizations from investing in robust cybersecurity measures. MDR services offer transparent pricing models and flexible cooperation options, making comprehensive security solutions accessible regardless of budget limitations. Whether you require a complete MDR solution or prefer to co-manage your Security Information and Event Management (SIEM) system, a tailored plan is available to meet your needs and budget requirements.
- Misconfigured tools: Misconfigured security tools can leave organizations vulnerable to cyber threats and compromise their overall security posture. MDR services leverage the intelligent use of existing tools and technologies, seamlessly integrating and optimizing them to enhance the effectiveness of your security infrastructure. Whether you rely on in-house security solutions or third-party platforms, MDR experts ensure these tools are utilized to their full potential, maximizing protection against evolving threats.
- Overload with false positives: Traditional security solutions often generate false alarms, inundating organizations with irrelevant alerts and wasting valuable time and resources. MDR addresses this challenge by leveraging advanced threat detection techniques and automation to minimize false positives and prioritize real threats. By filtering out noise and focusing on genuine security incidents, MDR helps organizations streamline their response efforts and allocate resources more efficiently.
Why invest in MDR? Top benefits for your business
Managed Detection and Response offers a range of benefits that contribute to a robust cybersecurity posture:
- Ability to enhance threat detection accuracy. MDR solutions can identify and prioritize genuine threats through intelligent automation and advanced analytics while minimizing false positives. This ensures that security teams can focus on addressing real risks rather than wasting time chasing irrelevant alerts.
- MDR enables organizations to streamline and accelerate security operations. By automating routine tasks such as threat detection, incident response, and remediation, MDR solutions help reduce manual workload and improve response times. This increases efficiency and allows security teams to allocate resources more effectively, enhancing overall threat detection and mitigation efficiency.
- MDR provides organizations access to expert security analysts who can investigate and validate security alerts, conduct in-depth analyses of complex threats, and orchestrate incident response procedures. This human-led approach ensures that security incidents are addressed promptly and accurately, minimizing the impact on the organization’s operations and reputation.
- MDR offers comprehensive reporting and alerting capabilities, providing organizations valuable insights into detected threats, incident responses, security trends, and vulnerabilities. This enables informed decision-making and prompt responses to security threats, helping organizations stay ahead of evolving threats and mitigate risks effectively.
- MDR helps organizations strengthen their security posture by providing continuous monitoring, rapid response capabilities, expert analysis, and actionable insights. By leveraging MDR’s benefits, organizations can enhance their ability to detect, respond to, and mitigate security threats, ensuring the safety and security of their data and systems.
- Reduced security costs. Building and maintaining a skilled in-house security team is expensive. MDR offers a cost-effective alternative, providing access to a team of security specialists without additional recruitment, training, and infrastructure investment.
The most important things to pay attention to when choosing an MDR provider
Downloading the complete MDR Buyer’s Guide offers a deeper dive into each aspect. It’s your comprehensive roadmap to making informed decisions about MDR providers. You’ll get detailed explanations, expert insights, and practical tips to help you confidently navigate decision-making.
The overview below provides only a glimpse into the key points to consider:
- Experience and expertise: When evaluating managed detection and response (MDR) services, consider the vendor’s experience in the industry, the qualifications of its team members, and its track record in successfully mitigating security threats. Look for a provider with a proven history of delivering effective MDR solutions and a team of certified security experts.
- Integrations: A critical aspect of MDR services is seamlessly integrating with your existing IT infrastructure and security tools. Ensure the MDR solution is compatible with your network architecture, endpoint security solutions, cloud platforms, and other third-party applications. Look for a flexible MDR platform that can adapt to your organization’s unique environment and technology stack.
- Automation: MDR services leverage technology to streamline and accelerate security operations, including threat detection, incident response, and remediation. Seek an MDR vendor with robust automation capabilities that can reduce manual workload, improve response times, and enhance overall threat detection and mitigation efficiency. Automation is essential for keeping pace with today’s rapidly evolving threat landscape.
- Human-led responses: While automation is crucial in MDR solutions, human expertise is equally important. Look for an MDR vendor that combines advanced technology with skilled security analysts who can investigate and validate security alerts, conduct deep dives into complex threats, orchestrate incident response procedures, and communicate effectively with your team. The human element ensures that critical security issues are addressed promptly and accurately.
- Reporting and alerts: MDR services should provide customizable reports covering detected threats, incident responses, security trends, and vulnerabilities. These reports enable informed decision-making and prompt responses to security threats. Look for an MDR platform that offers comprehensive reporting capabilities and real-time alerts to keep you informed of potential security issues as they arise.
- Speed of detection and response: Evaluate the provider’s advanced threat detection capabilities and rapid response protocols. Look for an MDR vendor that can minimize damage and downtime by quickly detecting and containing threats before they escalate. The speed of detection and response is critical for effectively mitigating security incidents and minimizing their impact on your organization.
- Service timeline: Understand the timeline for onboarding, deployment, and ongoing service with the MDR vendor. Consider factors such as the implementation process, availability of support, and escalation procedures for critical incidents. Ensure that the MDR provider offers timely assistance and support when needed, with clear service level commitments and response time SLAs.
- Pricing model: Transparency in pricing is essential when selecting an MDR vendor. Consider subscription fees, implementation costs, and any additional charges for incident response or additional services. Look for a pricing model that aligns with your budget and clarifies the total cost of ownership. Ensure there are no hidden costs and that the pricing structure is flexible enough to accommodate your organization’s evolving needs.
- Scalability: Choose an MDR vendor that can adapt and grow its services alongside your organization. Scalability is crucial for accommodating increases in data volume, network complexity, and user activity without compromising performance or security. Look for a scalable MDR platform that can grow with your business and provide continuous protection as your security needs evolve.
- Compliance: Ensure that the MDR vendor meets your industry’s requirements. Verify that their security practices and solutions meet regulatory standards and guidelines relevant to your organization’s sector. Look for an MDR provider with expertise in compliance management and a track record of helping organizations maintain regulatory compliance
MDR cost – how is it calculated?
MDR costs are influenced by various factors tailored to each organization’s requirements, reflecting the comprehensive nature of managed detection and response services. Here’s an insightful overview of how MDR costs are typically determined:
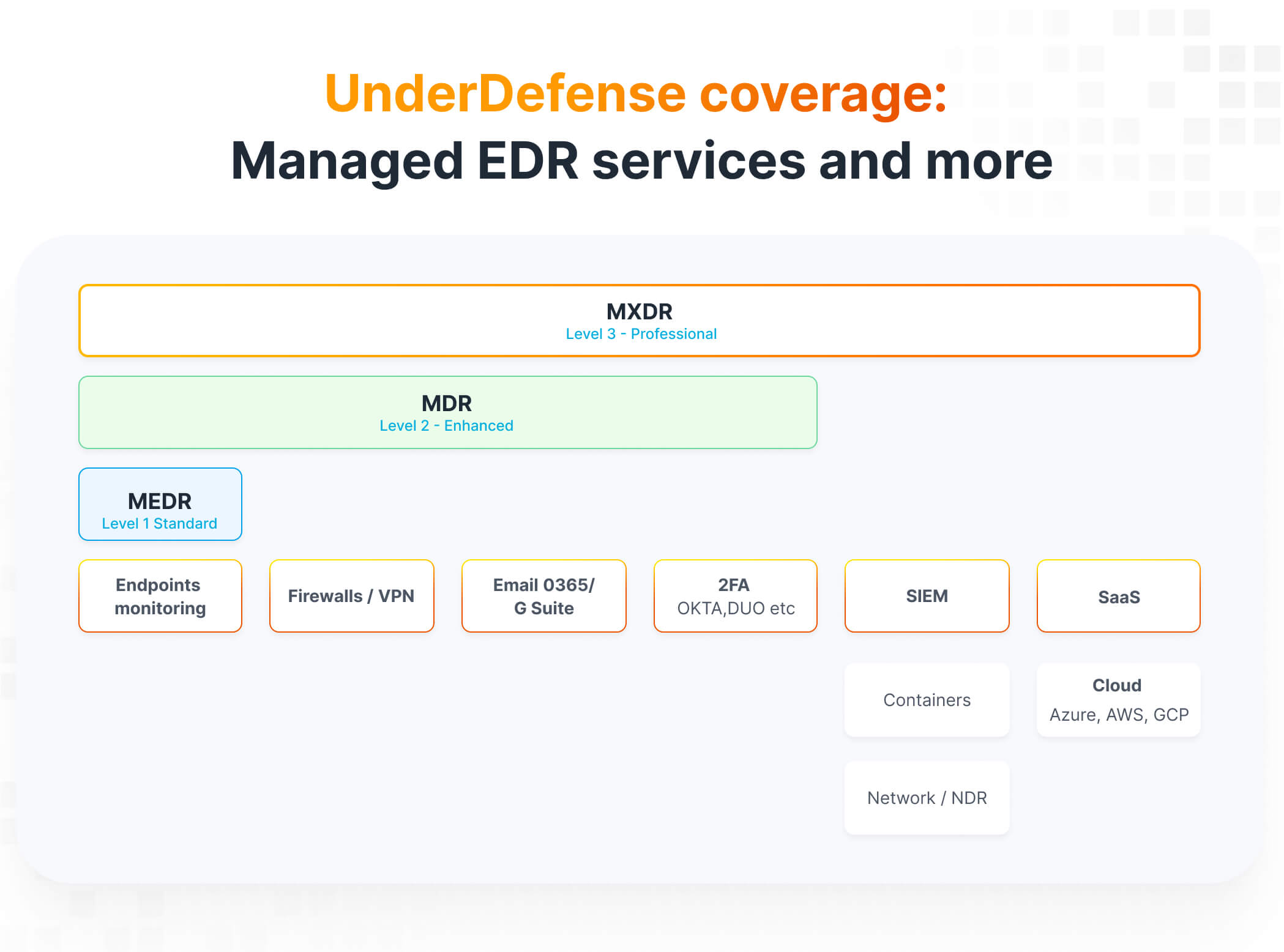
- Service tier: MDR vendors offer different service tiers with varying features, support, and capabilities. Organizations can select a tier that aligns with their needs and budget, with higher tiers often providing more comprehensive protection and additional services.
- Scope of coverage: The cost of MDR services is influenced by the scope of coverage required by the organization. This encompasses the number of endpoints, servers, cloud environments, and other IT assets that necessitate monitoring and protection.
- Number of users: Some MDR providers determine their pricing based on the number of organization users requiring security monitoring and protection. Consequently, larger organizations with more users may face higher costs due to the increased scope of coverage needed.
- Additional services: MDR vendors may offer supplementary services such as incident response, threat hunting, vulnerability assessments, and compliance support. These services can be priced separately or bundled into comprehensive packages tailored to the organization’s needs.
- Customization and integration: Organizations seeking custom integrations, tailored configurations, or specialized support may incur additional costs for these services. MDR solutions are often designed to seamlessly integrate with existing IT infrastructure and security tools, enhancing overall efficacy.
- Contract duration: The contract or subscription period can impact MDR costs. Longer-term contracts may offer discounts or incentives, while shorter-term contracts may have higher monthly fees.
- Add-ons and upgrades: MDR providers may offer add-on services or upgrades, such as enhanced threat intelligence feeds, advanced analytics, or access to premium support. These enhancements contribute to the overall cost of MDR services and can be tailored to meet specific security requirements.
- Negotiation: Pricing for MDR services is often negotiable, particularly for larger organizations or long-term contracts. Organizations are encouraged to negotiate based on their unique needs and budget constraints, ensuring cost-effectiveness and value.
UnderDefense MDR pricing models
Our pricing models include:
- UnderDefense MAXI Platform backed by 24×7 concierge team
- Unlimited security investigations during an incident
- No data restrictions
- Out-of-the-box security automation without setup delays
- Smart use of your current security tools
MDR STANDARD | MDR ENHANCED | MDR PREMIUM |
Confident protection 24/7 | With cloud & office protection | 360° security and visibility |
|
|
|
Top MDR vendors
Selecting the right MDR partner is crucial for your organization’s security. Don’t rely solely on brand recognition. While established MDR providers offer robust solutions, smaller vendors can be just as effective, often providing greater flexibility and potentially lower costs. Here is the table of the top MDR vendors, comparing their strengths, capabilities, and unique offerings to help you make an informed decision.
The Best Managed Detection and Response Vendors: Feature Comparison Table | ||||||
Features | UnderDefense | Arctic Wolf | Alert Logic | Expel | Red Canary | Proficio |
Technology | Top notch SIEM, MDR,EDR, SOARs | Own technology, proprietary | Own technology, proprietary | General toolset | General toolset | General toolset |
Customer Portal |  |  |  |  |  |  |
24/7 availability |  |  |  |  |  |  |
Concierge service (SOC analysts directly available) |  |  |  |  |  |  |
Custom IR plan and playbook built with the client's IT |  |  |  |  |  |  |
Threat intelligence |  |  |  |  |  |  |
Support of your existing security investments |  |  |  |  |  |  |
Compliance visibility and implementation capabilities (SOC2, ISO, HIPAA) |  |  |  |  |  |  |
Vulnerability scanning |  |  |  |  |  |  |
Fine-tuning of your security tools to get maximum value for money |  |  |  |  |  |  |
Incident response, threat mitigation and containment on your behalf |  |  |  |  |  |  |
SOARs of your choice (Phantom, Siemplify, Demisto) |  |  |  |  |  |  |
Malware analysts |  |  |  |  |  |  |
Alerting via Slack or Email |  |  |  |  |  |  |
Dark Web monitoring/Leaked accounts monitoring |  |  |  |  |  |  |
Learn more about the top MDR providers by exploring our comprehensive article.
UnderDefense Turnkey MDR: your trusted partner for 24/7 business protection
24/7 continuous protection: | Faster Incident Response with UnderDefense MAXI | Intelligent integration |
Unwavering vigilance across all your environments, from cloud infrastructure to network endpoints and applications. UnderDefense MDR provides a safety net that operates around the clock. | UnderDefense MAXI platform is a powerful suite of tools that streamlines incident response through automation and facilitates direct communication with our Security Operations Center (SOC) for expedited action. | UnderDefense MDR seamlessly integrates with your existing security infrastructure, maximizing the value of your current security investments—no need to rip and replace – UnderDefense works with what you already have. |
Flexible cooperation models | Cutting-edge innovation | Expert threat hunting and mitigation |
UnderDefense MDR offers a range of flexible cooperation models to fit your specific security needs. Whether you require an extension to your existing SOC, a fully managed turnkey service, co-managed SIEM support, or assistance building a SOC from scratch, UnderDefense has a solution for you. | We leverage in-house expertise to create proprietary tools and best practices that enhance protection, affordability, and effectiveness. This includes a custom app for Splunk Audit logs, unique SIEM correlation rules, and best practices for strengthening popular platforms like GSuite and AD/AzureAD. | Our team of experienced security analysts goes beyond simply reacting to threats. UnderDefense MDR proactively hunts for hidden threats that automated tools might miss. We identify and neutralize these threats and offer personalized guidance on preventing future occurrences. |