Over the past few years, the whole business world has been actively acclimating to the global situation and activities. The pandemic and shift to remote/hybrid work, the succeeding Great Resignation, geopolitical instability, global talent shortage, and constantly emerging and quickly maturing technologies represent only a small part of all the factors and challenges that business and cyber leaders have to consider and address. Meanwhile, the cybersecurity landscape has been changing too. Check Point Research found that in 2022 the number of cyberattacks on businesses increased by 38% compared to 2021.
Today more organizations opt for managed detection and response services to effectively protect complex security ecosystems and deal with emerging advanced cyber threats. In 2022, the global MDR market reached $2.6 billion, and it’s projected to hit $5.6 billion by 2027. So, let’s dive deeper into solution offerings and see which managed detection and response vendors deliver the best value for money.
The Role of MDR Solutions in Tomorrow’s Business Protection
We’ve recently discussed what MDR is and how it differs from EDR and XDR products. Meanwhile, the long list of advantages makes the current popularity of MDR security solutions easily explainable. In the Market Guide for Managed Detection and Response Services, Gartner states that by 2025, 60% of companies will actively employ remote threat disruption and containment capabilities offered by MDR providers, compared to 30% today. So, what problems do companies solve with this type of service?
Top 3 challenges managed detection and response solutions solve
1. Lack of human resources
It’s no secret that cybersecurity is facing a tremendous talent gap. Moreover, only a few industries experience the same skill shortages. Deepwatch SecOps Pulse Survey found that in July 2022, there were over 700,000 cybersecurity vacancies in the United States alone. If no corrective measures are taken, the gap will surpass one million by 2025.
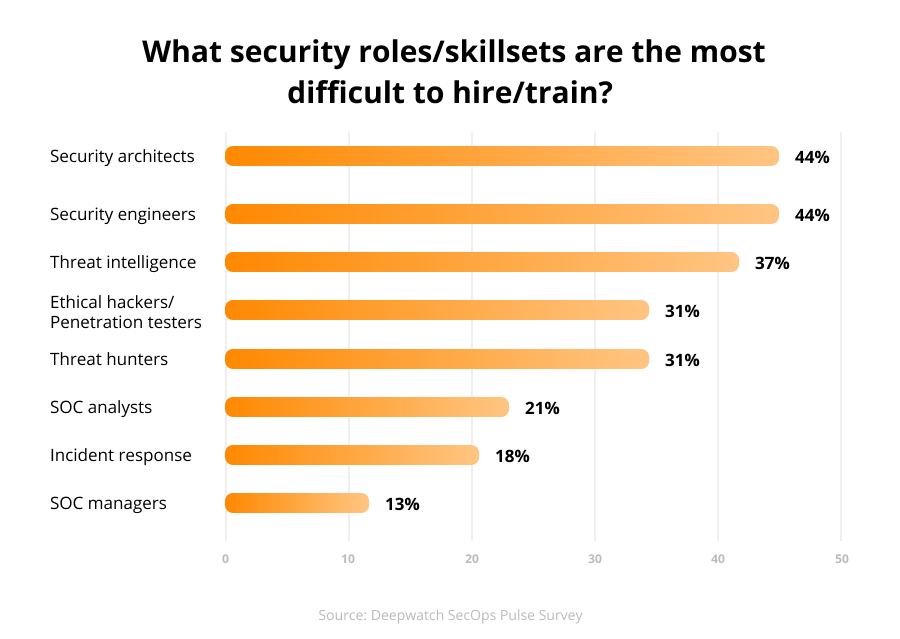
Many organizations have adopted modern security tech to help their understaffed departments address the glooming threat landscape. For instance, the number of security products planned to be implemented in the upcoming 12 months will increase by over 80%. However, such an approach only aggravates the situation since companies lack the resources and expertise to properly deploy, fine-tune, and smoothly orchestrate new tools with other software in place.
2. Alert fatigue
Overwhelmed security teams are the second biggest problem of modern organizations. Reviewing, sorting, and managing a great many alerts coming from all those security technologies require more expertise and resources than companies typically own. Meanwhile, the number of alerts keeps growing along with digital estates and the number of endpoints.
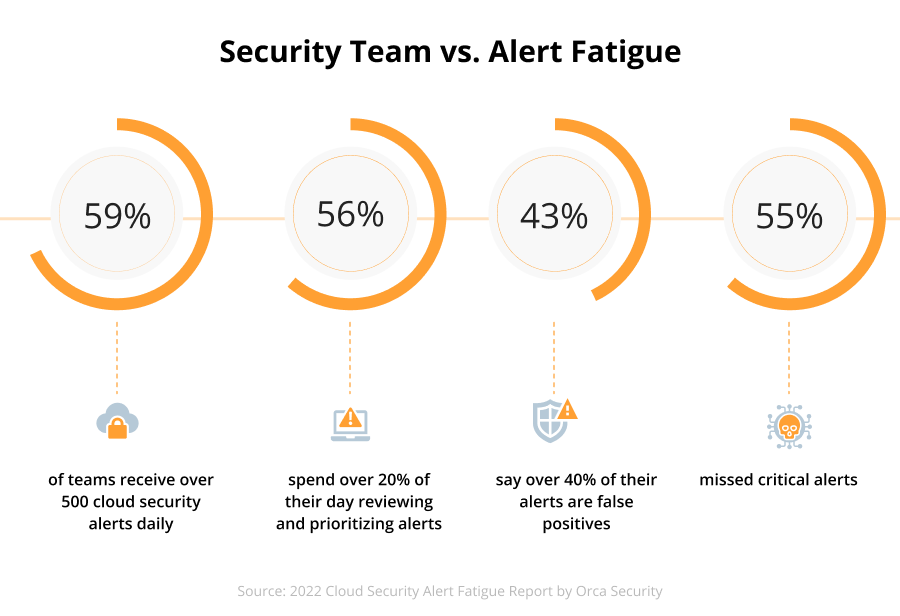
Security teams are forced to deal with the same situation daily, which results in demoralization, burnout, and high attrition rates.

3. Limited budget
Considering today’s cybersecurity landscape, every organization should monitor its environment around the clock. But let’s admit that building an internal security operations center (SOC) is time-consuming and costly. In its 2022 State of Cybersecurity Report, CompTIA revealed that 40% of companies lack a cybersecurity budget. Though it’s a common problem in most IT areas, in the cybersecurity field, the situation is worse. Calculating the return on investment is challenging, and positive outcomes are not well-defined.
Finally, even if a company decides to build an in-house SOC, it should be ready to spend months or even years building a comprehensive and effective detection and response strategy. And during all this time, the organization will remain vulnerable.
Managed detection and response tools and services are designed to solve these and other challenges related to compliance regulations, emerging technologies, and more. So, when you decide to join the ranks of forward-thinking leaders and benefit from MDR security systems, you will easily find dozens of vendors online. However, this is a double-edged sword since selecting and hiring the best one may be anything but easy.
How to Choose the Best MDR Provider
Managed detection and response solutions come with a wide range of services, and you may not need them all. So, start with analyzing your existing capabilities and identifying the gaps that should be filled. By doing so, you will augment your current security investments and optimize further operating expenses.
Done? Then we’re good to go. Below are five questions that will help you select a reputed MDR service provider.
- What experience and expertise does the managed detection and response provider possess?
- What service delivery models does the vendor offer? Do any of these options work for you?
- How will the company work with and orchestrate your current security software for effective threat detection and response?
- What are the vendor’s incident response experience and typical workflow? How do they communicate with clients, manage alerts, and provide reports?
- Does the vendor provide a portfolio with actual client reviews?
Narrowing down your search to a few companies, take time to conduct due diligence on the top MDR providers before making a choice and signing a contract.
If you have data privacy, residency, or other compliance requirements, ensure that managed detection and response providers are familiar with and can comply with them. Work closely with the potential partner and your legal department to prevent any compliance violations and heavy fines.
For instance, UnderDefense has a tried and tested working approach to such cases. Our team can use metadata and telemetry, meaning that all information coming from the client’s side is related to network or system performance only. By doing so, we don’t process or store personally identifiable information (PII) and have read-only data access.
Over the years in the cybersecurity industry, we’ve often heard from our clients that it is hard for them to make a choice. The market is flooded with different vendors, products, and offerings. So, we’ve created a short list of top MDR providers worth your attention.
The List of 6 Best MDR Providers
1. UnderDefense MDR
UnderDefense is the award-winning cybersecurity team and top-rated company on Gartner and Clutch. Its holistic MDR solutions combine managed threat hunting and incident response experts with state-of-the-art technologies to predict, prevent, detect, and respond to the most advanced cyberattacks.
The company offers different service delivery models that meet you where you are and scale easily as your business needs grow. You can choose a suitable package and pay only for those services you need today. Such an approach makes the UnderDefense MDR platform the most cost-effective solution for full visibility and complete breach protection.
The main features:
- Quick deployment and seamless integration into your existing IT security stack allowing you to get the most out of current tools without overpaying
- Automation of day-to-day security operations from immediate detection to seamless remediation. Prebuilt and custom correlation rules for companies to boost response capabilities, optimize security costs, and deal with alert fatigue
- 24/7 monitoring, threat intelligence, and user behavior analytics to guarantee unprecedented environment visibility, detect suspicious activity across endpoints, networks, cloud, on-premises, and hybrid environments
- Comprehensive forensics to provide insight into the root cause of a security incident, detailed view of the affected assets within the network, and clear guidance on how to remediate and minimize the consequences for business
2. Arctic Wolf
Arctic Wolf’s managed detection and response tools offer 24/7 threat monitoring of endpoints, networks, and cloud environments. They empower companies to detect and contain advanced cyberattacks and prevent future attacks with workflow customization and exhaustive threat analysis.
The main features:
- White-glove deployment engagement to minimize confusion, complexity, and time
- Around-the-clock security coverage of major cloud platforms by a dedicated team
- Combination of security industry experience and unique understanding of cloud strategies to guide clients’ ongoing cloud security posture improvement
3. Alert Logic / Fortra
Alert Logic offers white-glove managed detection and response solutions for SaaS, public cloud, on-premises, and hybrid environments. It was named the leader by IDC and G2 (MDR for enterprises). In March 2022, Fortra acquired Alert Logic to augment the existing cybersecurity resources and enrich its industry portfolio.
The main features:
- Threat intelligence that combines human smarts with industry data, continuous threat research, and machine learning
- Real-time reporting on compliance status, vulnerabilities, risks, remediation activities, and configuration exposures
- Platform scalability to protect the entire attack surface and ensure visibility and security analytics for networks, applications, and endpoints in cloud, hybrid, and on-premises environments
4. Expel
Expel’s MDR security solutions cover SaaS, Kubernetes, cloud, and on-premises environments with around-the-clock detection and response. The company leverages a software-driven approach to eliminate the noise, allowing clients to dedicate time to what matters most.
The main features:
- Integration with existing tech without agents, SIEM, or new hardware
- Automation of alerts and logs, as well as auto-remediation or full resilience recommendations
- Investigation of suspicious activities by the SOC and further provision of answers to the alerts
- Real-time alerts and comprehensive reports to prevent risks and gain full visibility into the investigation process
5. Red Canary
Red Canary offers 24/7 MDR security systems for identities, endpoints, network, cloud, and SaaS. They integrate with many modern security products to make it easier for companies to gain the best value and ROI from their current security investments.
The main features:
- Threat monitoring, detection, and investigation 24/7 applying advanced analytics to telemetry
- Automation and orchestration of playbooks to respond to threats, start remediation, and inform the right people
- Executive reporting to ensure complete transparency and let leaders track ROI and MTTR
6. Proficio
Proficio’s MDR services leverage AI-based threat hunting, threat intelligence, and cutting-edge technologies to detect attacks effectively and promptly. The company was the first to offer response automation products, and today they propose a holistic set of Security Orchestration Automation and Response (SOAR) solutions
The main features:
- 24/7 security monitoring and alerting
- Integrated threat intelligence and AI-based threat hunting
- Managed endpoint detection and response
- Risk-based vulnerability management
- Automated and semi-automated containment
Proficio’s MDR services leverage AI-based threat hunting, threat intelligence, and cutting-edge technologies to detect attacks effectively and promptly. The company was the first to offer response automation products, and today they propose a holistic set of Security Orchestration Automation and Response (SOAR) solutions
The Best Managed Detection and Response Vendors: Feature Comparison Table | ||||||
Features | UnderDefense | Arctic Wolf | Alert Logic | Expel | Red Canary | Proficio |
Technology | Top notch SIEM, MDR,EDR, SOARs | Own technology, proprietary | Own technology, proprietary | General toolset | General toolset | General toolset |
Customer Portal |  |  |  |  |  |  |
24/7 availability |  |  |  |  |  |  |
Concierge service (SOC analysts directly available) |  |  |  |  |  |  |
Custom IR plan and playbook built with the client’s IT |  |  |  |  |  |  |
Threat intelligence |  |  |  |  |  |  |
Support of your existing security investments |  |  |  |  |  |  |
Compliance visibility and implementation capabilities (SOC2, ISO, HIPAA) |  |  |  |  |  |  |
Vulnerability scanning |  |  |  |  |  |  |
Fine-tuning of your security tools to get maximum value for money |  |  |  |  |  |  |
Incident response, threat mitigation and containment on your behalf |  |  |  |  |  |  |
SOARs of your choice (Phantom, Siemplify, Demisto) |  |  |  |  |  |  |
Malware analysts |  |  |  |  |  |  |
Alerting via Slack or Email |  |  |  |  |  |  |
Dark Web monitoring/Leaked accounts monitoring |  |  |  |  |  |  |
Conclusion
Many business leaders used to believe that cybersecurity is the undoubted prerogative of large enterprises. However, the lesson of recent years shows that more small and mid-sized companies fall victim to cyberattacks due to their weak security posture.
Considering the growing aggressivity of modern malware and the stratagem of hackers, being cybersecurity conscious is not just a trend but a must for businesses of all sizes. And that’s where time becomes the biggest problem because organizations need time to become truly cyber resilient. Building or expanding a security team, selecting, deploying, and synchronizing all security tools, and establishing a security culture among staff and C-level—all that is no small and quick task. It may take months and years for a company to ensure cyber resilience.
In this context, choosing a managed detection and response solution and a reliable cybersecurity partner is half the battle. Such an approach will prevent common pitfalls and save you months of unnecessary work. But most importantly, MDR will save you hundreds of thousands of dollars budgeted for cybersecurity measures. So, we hope that our list of top MDR providers will help you make the right choice.
On our part, we want to emphasize that MDR is as much about technologies and features as it’s about people who stand behind all that. UnderDefense is home to the brightest cybersecurity minds, and numerous positive reviews from our clients prove that. If you want to protect your business with effective managed detection and response tools and make the most of them, reach out to us today and get a quote.


















