Resource Hub
Dive deep into the realm of cybersecurity with our expert insights on Managed Detection and Response, Incident Response, Endpoint and Cloud Security, and more. Stay updated with the latest enhancements of the UnderDefense MAXI platform. Discover our trailblazing achievements and let our satisfied customers inspire you with their stories.
How to protect from COVID-19 Cyber Attacks
It is not new that COVID-19 pandemic influenced the lives of humanity in the XXI century. However,...
Forwarding MySQL log file in AWS to Splunk: monitoring connections
Intro Working for our client with a database hosted on Amazon, we have faced the case of...
Effortless Splunk Universal Forwarders update with Ansible
Are you familiar with a pain of trying to install or update a large number of Splunk universal...
Eset Remote Administrator App for Splunk
About data visualization and Splunk apps Shortly about app App Description Summary Links About...
How to Configure Log Sending from Cisco Firepower to Splunk [2024]
In this article, we are going to describe the process of connecting Cisco FirePower Threat Defense...
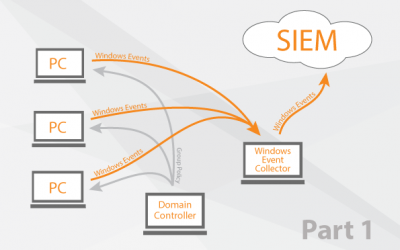
Windows Event Collector orchestration 2
Create a Group Policy Add WEC to the special user group Add read access to security logs for winRM...
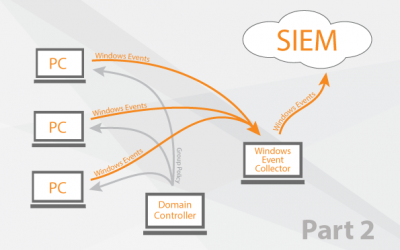
Windows Event Collector orchestration
Different Methods of log collection Splunk Universal Forwarder VS WEC How it works (Solution...
Splunk Add-on for Eset Remote Administrator
Development How to use it Summary Development First of all we need to install Splunk Add-on...
How to deploy MSI packages remotely in Windows infrastructure using remote shell
How to use msiexec on remote hosts? Description of the situation in the environment How do...









![How to Configure Log Sending from Cisco Firepower to Splunk [2024]](https://underdefense.com/wp-content/uploads/2018/05/How-to-configure-log-collection-from-Cisco-FirePower-to-Splunk-1-400x250.png)