- Different Methods of log collection Splunk Universal Forwarder VS WEC
- How it works (Solution overview)
- Installation description
- Subscription creation process
- Summary
Introduction
This blog is one of many in a series that will discuss log collection variants. Today we are going to talk about log collection in Windows Infrastructure. If you’d like to monitor your infrastructure or provide SOC services, you will need to collect a lot of logs from infrastructure to a Log Management Tool or a SIEM system. It’s a really difficult choice about how to run this process. That’s why we are going to share with you some thoughts on this topic, especially what are the known methods of logs collection in Windows Infrastructure, and the pros and cons of them.
Different Methods of log collection Splunk Universal Forwarder VS WEC
As we use Splunk as SIEM solution we will describe the method of log collection provided by Splunk. Its grounding on using Splunk universal forwarders, which are installed on every computer which have to be monitored. The main advantages of using this method are:
- Simplicity in configuration – you only need to install it and set the deployment server. Once installed you can manage it remotely from the Splunk deployment server.
- It’s the fastest way to receive logs from your endpoints. It provides a reliable and secure data collection process.
- It is a tool where the data can be consolidated from different types of inputs. So one doesn’t need to worry about the data coming up from different sources and how the data needs to be processed.
- Scalability of Universal Forwarder is very flexible, it can handle tens of thousands of remote systems collecting terabytes of information or data without any problem.
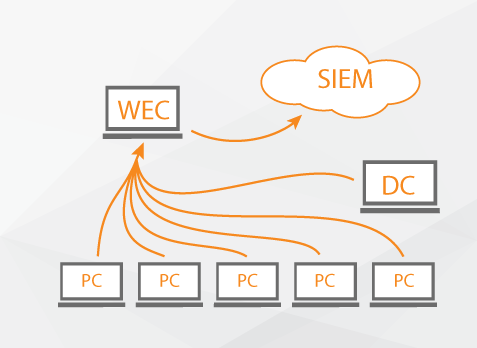
But there is one big drawback – It’s a third-party software, and sometimes you could come across the situation where using of third-party components is unacceptable in accordance with some compliances. If you have the same situation, when you can’t install third-party software on your critical endpoints, and your infrastructure is windows oriented, continue reading for more options and resources on how you can still accomplish this. Microsoft infrastructure has its own method of log collection, it’s called Windows Event Collector. Here we will describe what it is and how to configure it. WEC server is a centralized log collection server in Windows infrastructure which uses Windows Event Forwarding concept. Let’s look at the objectives which could be achieved with WEC. WEC service allows users to determine one or several servers as the event collector. These servers will act as subscription managers and allow to choose which types of logs will collect from endpoints and will save on them. Centralised log processes allow us to save time and increase the reliability of the logs. It’s a more secure way to save all log files in one place with limited access and it’s like the backup copy of log files. There is no necessity to check every computer for logs availability, and if someone erases them on the endpoint the backup copy on WEC will be safe. WEC data sending occurs with WinRM services as it’s native windows service. Pros of using WEC:
- all events encrypted with Kerberos by default
- subscriptions could be created as XML files and supported with versioning control software such as git
- new endpoints register automatically after connection to the domain
- WEF can be configured with pull or push modes
- sending intervals can be changed.
How it works (Solution overview)
Event collector service works with subscriptions which are created for events on remote machines. One subscription could be connected to several remote machines, which are sources for events. There is a filter connected to the subscription which determines what types of events will be sent. Event collector service uses WS-Management protocol for its connection with sources and sending logs. Windows Event Forwarder reads all administrative system logs on the endpoints and redirects suitable events to Windows Event Collector. There are two different subscriptions for this case which are published on endpoints.
- baseline WEF subscription – events collected from all hosts, this includes some role-specific events, which can only be produced by those machines
- Targeted WEF subscription – events collected from a limited set of hosts due to unusual activity.
There are two types of subscriptions by type of log sending:
- source-initiated subscriptions determine subscription in WEC without event source assignment. After those several remote computers could be configured with Group policy parameter for events transmitting to WEC. It is useful when there is no necessity to manually configure all computers in your infrastructure.
- collector initiated subscription allows to create subscriptions on events when all computers – events sources are well known. In this case, WEC will take logs from the assigned computer by itself.
We use a source-initiated subscription type because it is simpler in terms of configuration and troubleshooting. So let’s describe the configuration process:
Installation description
The first step is the creation of a Windows Event Collector. After choosing the machine which will be run as WEC, go to it and open the command line with administrative privileges. Type “wecutil qc”, click on enter and type “y” to approve.
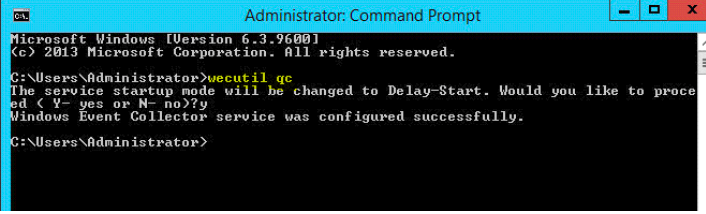
As result, you will see the message about successful configuration.
Subscription creation process
The next step is subscription creation. Before that, we have to sort a list of event codes by log types such as Security, System, Setup, Application, etc. All actions should be performed under Administrator account. In addition to this, the Windows Firewall services have to run. So, let’s describe the creation process:
- Open the Event Viewer and go to Subscriptions
- In the right-hand corner choose Create Subscription
3. In Subscription Name field it is recommended to write an informative name such as Critical_Security (we understand that this subscription contain Event Codes which belong to Security logs). 4. In Destination log field chose the Forwarded Events. It determines where the logs will be sent.
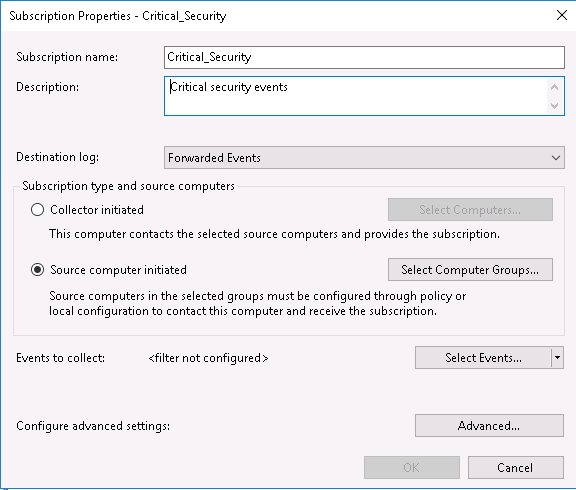
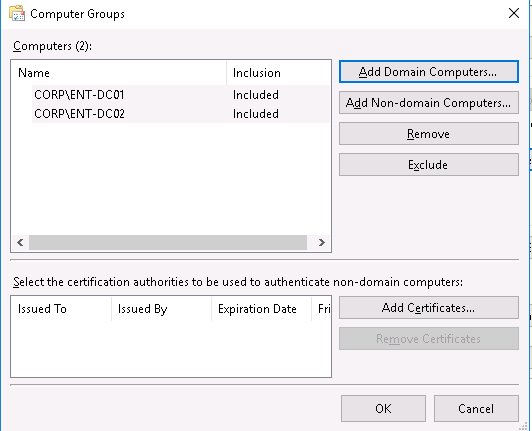
5. In Subscription type and source computers choose Source computer initiated, that is if we want to config source initiated type of subscription, as we explain above. After that go to Select Computer Groups tab. 6. With Add Domain Computers and Non-Domain Computers tab add computers which will applied to subscription. Click OK and move back.
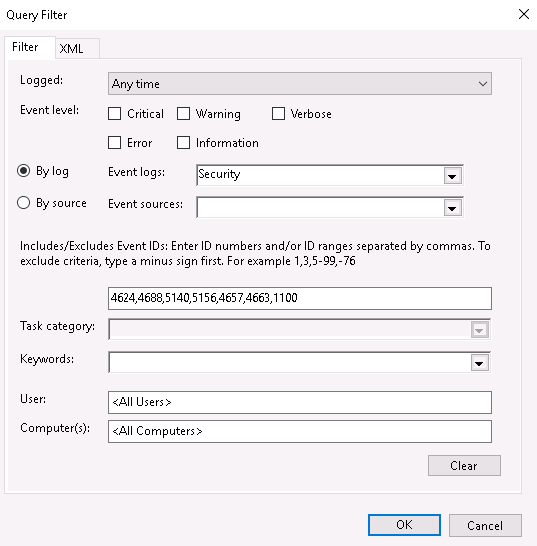
7. Open Select Events tab. Here we can configure the filter for Event Codes, specify what Events code we are going to monitor. In By log tab choose the log’s source (in our case its Security). And below specify the necessary Event Codes. Other parameters are additional and you can configure those on your own. Click OK twice.
8. Finally we have a created subscription which can be applied to all specified computers.

Summary
Upon completion of the configuration, we will have the possibility to track and receive events from remote computers. In the next part of this article, we are going to describe the configuration process of Windows Remote Management service which is used for log sending.