- Create a Group Policy
- Add WEC to the special user group
- Add read access to security logs for winRM services
- Restricted Group creation
- WinRM service configuration
- Summary
Introduction
As the continuation of the previous article, we are going to share information about the next step in WEC configuration. We will talk about event forwarding background, which services it uses and how to configure them in a proper way.
As we use source initiated type of subscription which was described in detail in the previous article. It allows us to define a subscription on an event collector computer without defining the event source computers, and then multiple remote event source computers can be set up (using a group policy setting) to forward events to the event collector computer.
The forwarding process is based on using winRM services as an essential part of this process. This service was explained in the other article.
So here below we are going to describe the process of configuration event forwarding through winRM service using group policies.
As a result of configuration from the previous article, we have created the subscription to receiving source initiated logs on the WEC computer.
Create a Group Policy
First of all we have to create the new group policy for example ” Forwarding” and apply it to event collector and all end computers which will send logs to WEC machine. After that we have to configure “Forwarding” group policy(GPO).
Add WEC to the special user group
However, there are strict restrictions on users’ roles in windows infrastructure. So for proper work of WEC server, there is a necessity to add it to a certain user group, the members of which have access to read logs
For this we have to perform next actions via GPO edit :
Computer Configurations -> Preferences -> Control Panel Settings -> Local Users and Groups. Click on that and choose to create a group.
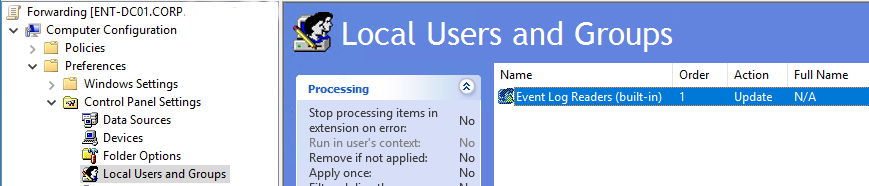
In the Group name field choose Event log readers(built-in).
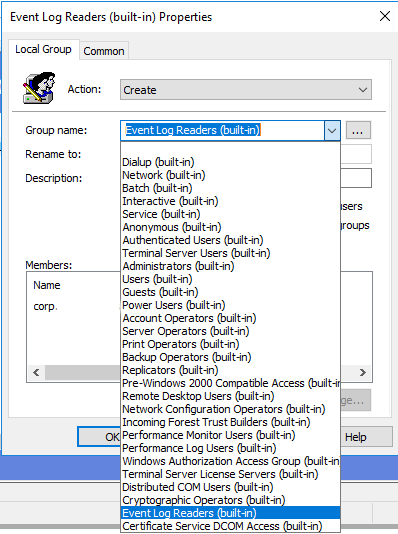
The next step is to add our WEC station to this group.
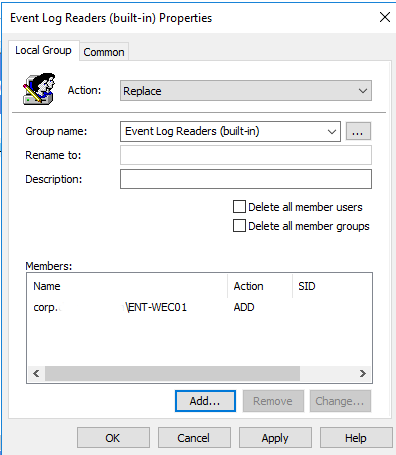
As the result, on this stage we have to see parameters the same as in the group policy configuration below.
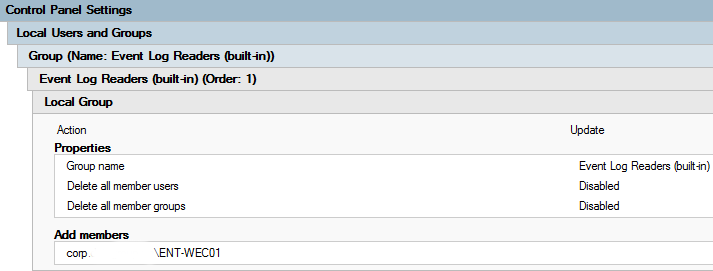
The next step is to configure System Services to automatically launch services for log collection and sending to WEC after start-up. The configured policy looks like this:
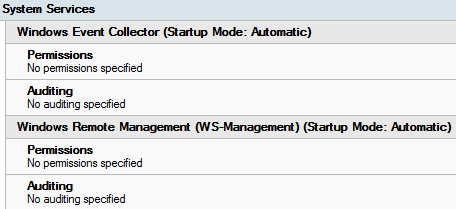
Add read access to security logs for winRM services
As we are going to collect all types of events, especially Security Events we have to provide permissions for winRM clients on all computers. By default network services as WinRM can’t access Security logs. To allow this we have to add some value to Windows registry.
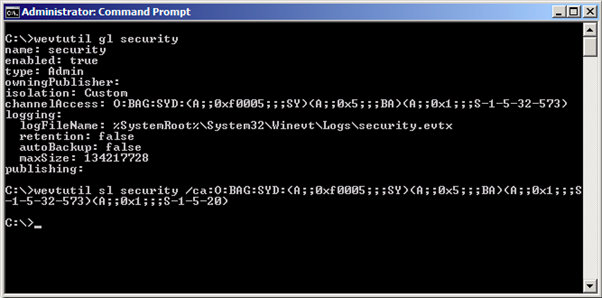
- On the end computer open command prompt with administrator privileges and run wevtutil gl security. As a result we will see the current security descriptor. It is located in channelAccess parameter and is described with SDDL (Security Descriptor Definition Language).
Global syntaksis of SDDL:
O:<owner>D:P<permissions >S:P<audit>
Value by default:
O:BAG:SYD:(A;;0xf0005;;;SY)(A;;0x5;;;BA)(A;;0x1;;;S-1-5-32-573) - If we are going to allow read access to all network services we have to add next value to the end (A;;0x1;;;S-1-5-20).
- To perform this:
wevtutil sl security
/ca:O:BAG:SYD:(A;;0xf0005;;;SY)(A;;0x5;;;BA)(A;;0x1;;;S-1-5-32-573)(A;;0x1;;;S-1-5-20)
To provide the same steps via group policies in order to apply this changes to all computers that are related to WEC we are going to perform the same actions.
In the group policy editor go to Computer Configurations -> Policies -> Administrative Templates -> Windows Component -> Event Log Service -> Security
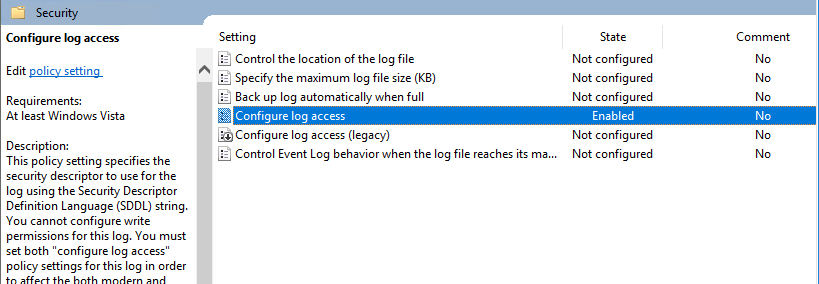
Configure log access here we have to add this value O:BAG:SYD:(A;;0xf0005;;;SY)(A;;0x5;;;BA)(A;;0x1;;;S-1-5-32-573)(A;;0x1;;;S-1-5-20) in the Log Access field.
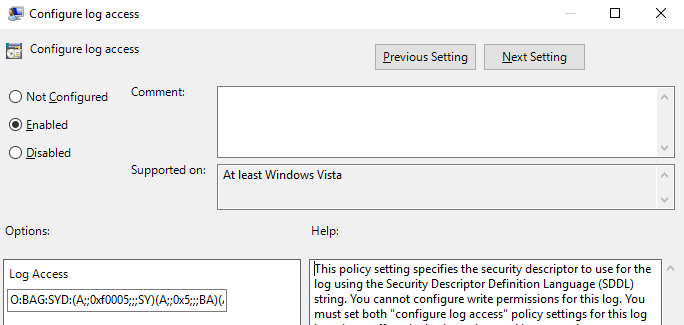
Finally policy Configure log access looks like on the picture below.
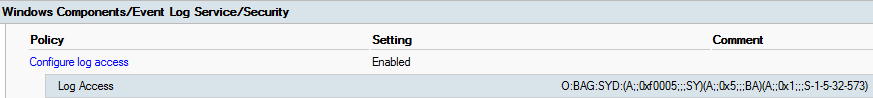
Restricted Group creation
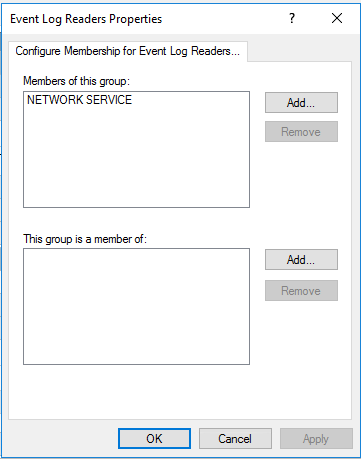
As we have previously created new user group Event Log Readers and provided Network services with permissions to read security logs. At this stage, we are going to add NETWORK SERVICE to Event Log Readers group for the possibility to read and forward all logs via winRM.
In the policy editor tab go to Policies -> Windows Settings -> Security Settings -> Restricted Groups. Here we should create a new Restricted Group – BUILTIN\\Event Log Readers.
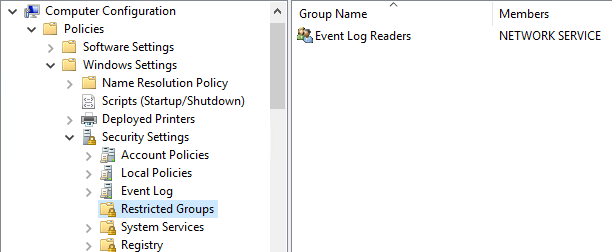
Next step is adding NT AUTHORITY\\NETWORK SERVICE user, to get a possibility for log collection via WinRM.
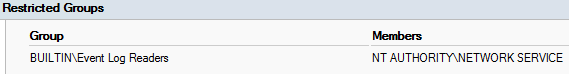
As a result we have configured policy.
WinRM service configuration
If there are no problems on previous steps we have a configured all permissions for services and all pre-requirements for log forwarding. At this stage, we are going to configure WinRM services to automatically start and provide all permission to it.
Create a policy to launch WinRM service on computers. Go to Computer Configurations -> Preferences -> Control Panel Settings -> Services here we should create a new service.
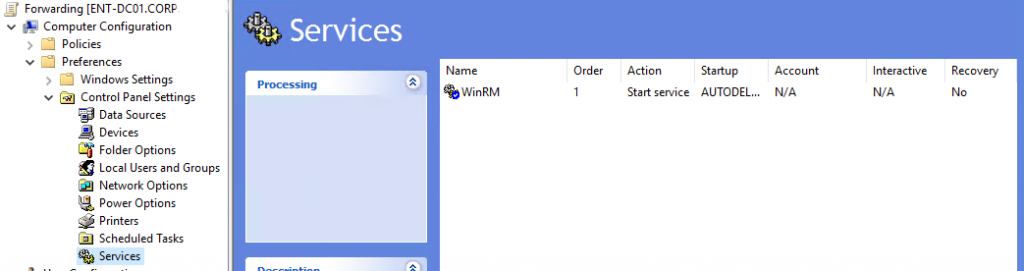
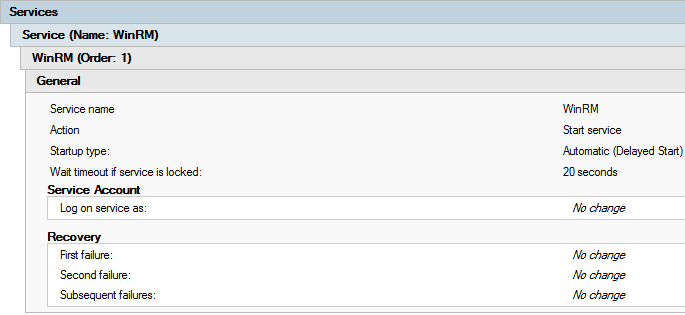
With the parameters:

As a result we have policy configuration.
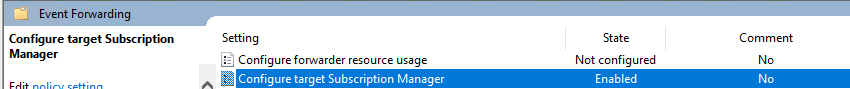
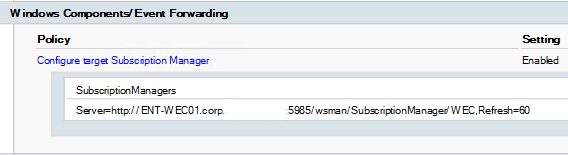
The next step is to configure log sending to event collector(WEC) on port 5985. Go to the policy Computer Configuration -> Administrative Templates -> Windows Components/Event Forwarding. Enable Configure target Subscription Manager policy and configure it.
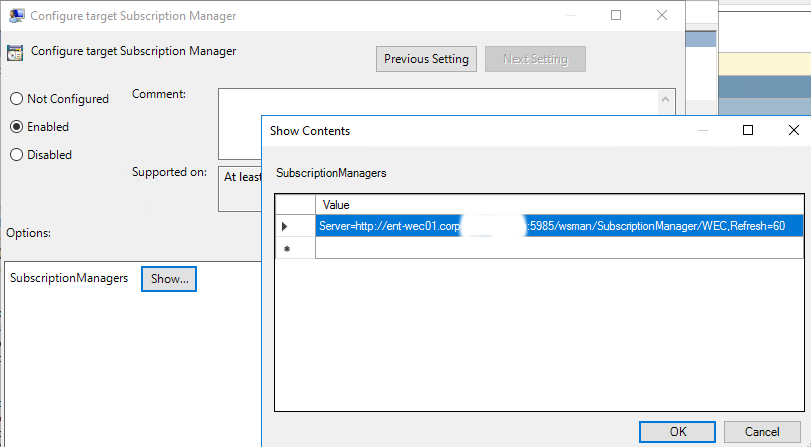
In Value field we are going to add next value:
Server= http://<Full domain name of WEC machine>:5985/wsman/SubscriptionManager/WEC,Refresh=60
Review settings:
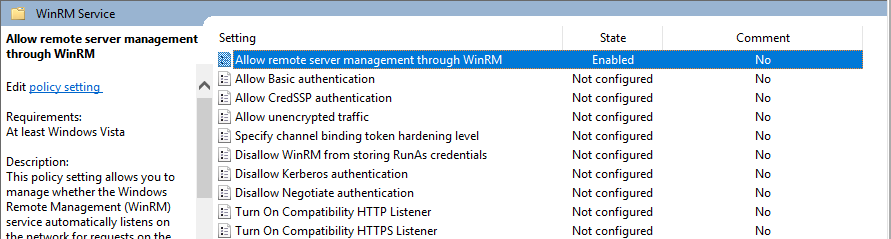
The further step is to configure permissions for all computers connected to WEC server. Go to the Computer Configuration -> Policies -> Administrative Templates -> Windows Components -> Windows Remote Management (WinRM) -> WinRM Service configure Allow remote server management through WinRM policy.
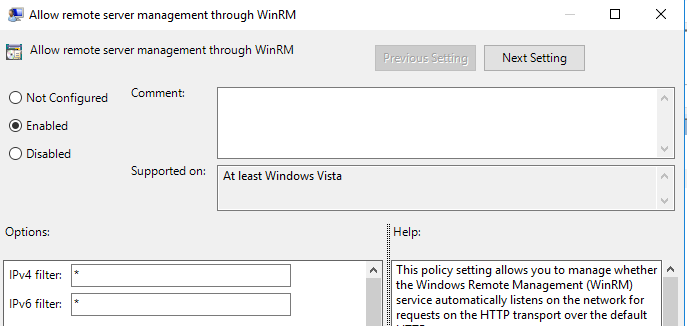
In the fields IPv4 and IPv6 write “*”. You have to do this in order to make winRM service connected to all computers in the domain.
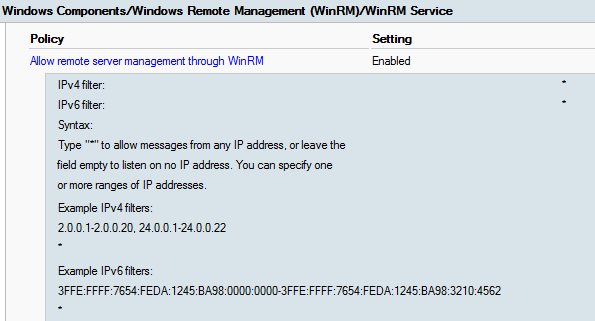
As the result we can review our policy settings:
Summary
In this article, we explain how to configure windows event forwarding through Group Policies. We have provided a step-by-step guide about Forwarding Group Policy configuration. The main points are how to run WinRM services for log collection and sending via GPO, how to manage permissions for services to provide access to logs and windows event forwarding mechanism.
















