The past pandemic has taught us all that staff mobility and immediate data availability are vital. In fact, COVID-19 acted as a natural selection for businesses globally, weeding out all those not ready for digital transformation and the future of work. Meanwhile, cyberattacks and data leakages continued testing the survivors’ strength, turning business security into a looming challenge.
Being prudent makes all the difference
The need for better protection and all-proliferating use of cloud technologies nurtured the popularity of security as a service (SECaaS) business model. The trend is not new, but it has gotten its second wind recently, and not because it’s the only solution to the issues that have arisen. IT security as a service has emerged as the best solution for the world, where business leaders prioritize operating expenses (OpEx) over capital expenditures (CapEx), seeking financial rationality and faster ROI. Moreover, the approach fits perfectly with limited security budgets and the need for seamless IT scalability.
Does that sound interesting? Then keep reading to discover what functionality stands behind the SECaaS concept and how it can help your business stay in the game despite future crises.
The introduction to security as a service: definition and working principles
So, what is SECaaS? Inspired by the software as a service model, security as a service follows a similar principle. It implies the delivery of cybersecurity solutions on a subscription basis. In other words, an organization delegates its cybersecurity management to a reliable SECaaS provider, like UnderDefense, eliminating the need to install hardware and software locally.
How security-as-a-service works
Organizations used to install multiple security tools like firewalls, anti-spyware, antivirus, and similar software on every on-premise asset. In this case, business owners had to pay for hardware, licenses, and additional staff to regularly check and ensure all the packages were up-to-date. Such an approach was inefficient and labor-consuming.
Today organizations can avoid that by opting for security as a service and benefit from all that cyber security technologies but in a cloud-based manner. By doing so, they access security expertise, innovation, and the ultimate set of tools and services necessary for effective and efficient 24/7 threat detection and response. Meanwhile, the external provider takes on all the tasks related to licenses, software configuration, coverage, and updates, threat landscape monitoring, plus staff onboarding, retention, and upskilling.
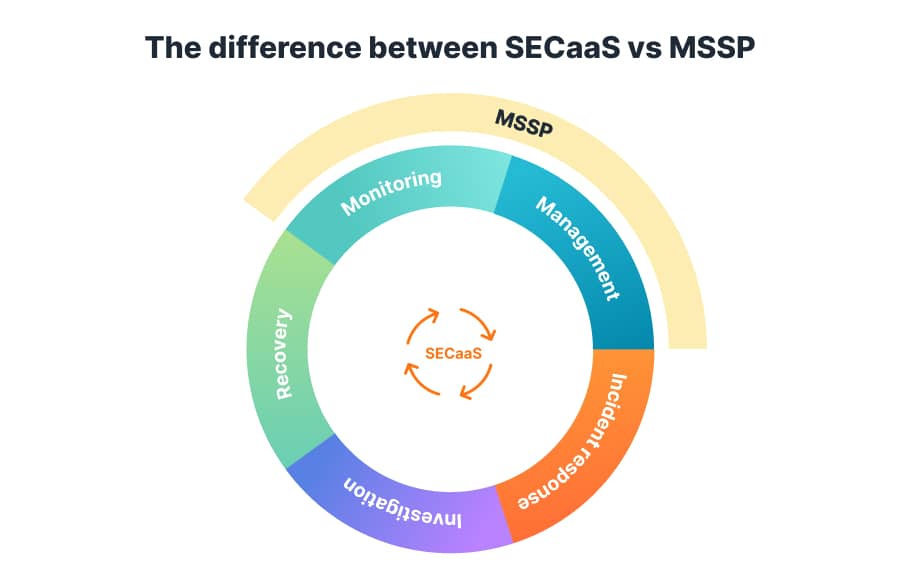
SECaaS vs. MSSP: what’s the difference
Admittedly, security as a service and managed security service providers may sound similar, and it’s easy for you to get confused. Both approaches aim to help organizations deal with security challenges without additional hires. However, SECaaS is more comprehensive compared to MSSP. Why? Let’s dig deeper to see the differences.
Managed security service providers offer security monitoring and management to help business leaders protect their organizations from threats. They can also assist with system upgrades and various modifications.
Security-as-a-service vendors provide security monitoring and management too. But they also support businesses with incident response, investigation, and recovery. So, it’s the best option for organizations that need to get and maintain compliance.
Examples of security-as-a-service solutions
Meanwhile, the answer to the question “What is security as a service” seems relatively straightforward, the situation with its delivery models may be complicated. Security vendors wrap their offerings in different names, causing confusion and overcomplicating the selection process. That’s why a not-for-profit organization, Cloud Security Alliance, has divided SECaaS solutions into 12 categories, namely:
- Identity and access management includes tools for identity assurance, authentication, user management, and access intelligence.
- Encryption software uses numerical and cryptographic ciphers to turn your text into an unreadable cryptogram.
- Email security protects your organization against malware, spam, phishing, and other offensive campaigns.
- Security assessment solutions check your current security measures and practices against industry standards.
- Security, information, and event management tools collect event and log data to help you detect any abnormal activities in your network or infrastructure.
- Continuous monitoring products constantly check internal security processes and perform risk management.
- Intrusion management leverages pattern recognition technology to detect suspicious behaviors and events, prevent and unleash intrusion attempts, and manage contingencies.
- Web security helps you protect public-facing applications accessed by users in real time.
- Vulnerability scanning offers tools to inspect your system or IT infrastructure and discover existing security vulnerabilities.
- Network security empowers you to control network access, as well as monitor, defend, and allocate network services.
- Data loss prevention includes solutions that verify, monitor, and ensure data safety at rest, in transit, and in use.
- Business continuity and disaster recovery introduce specific measures to guarantee your operational resiliency in case of a system outage or emergency.
Even with such a categorization of offerings, the overcrowdedness of the market is beyond dispute. And in case you’re wondering if we already witness a peak activity in the SECaaS supply and demand, our answer is a clear no. Moreover, the upcoming security challenges will keep the security-as-a-service market skyrocketing.
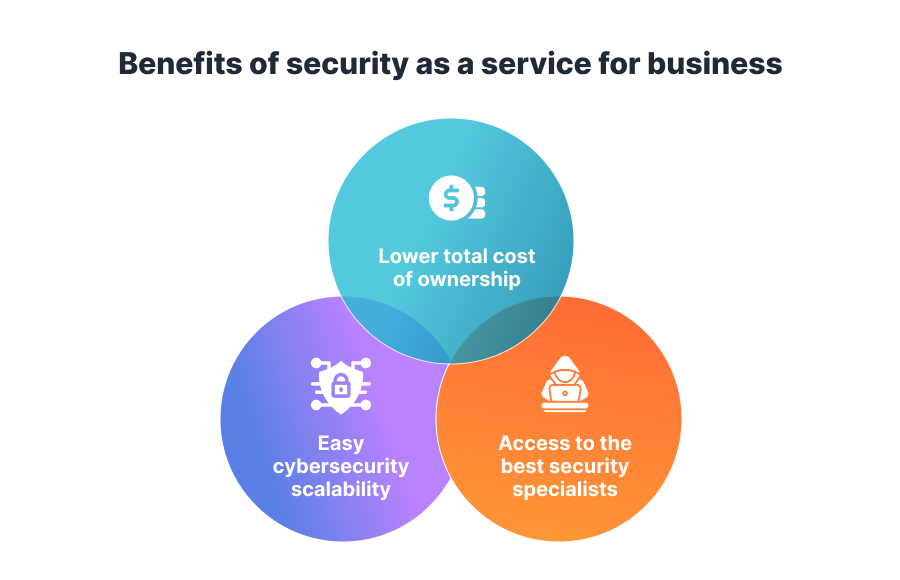
Top 3 benefits of security as a service for business
Today many factors nurture and drive the high popularity of the security-as-a-service approach. Any company of any size and budget can use it to address their specific challenges or needs. Let’s discuss the main advantages of SECaaS over the traditional in-house business model and how it can benefit your organization.
#1 Lower total cost of ownership
Cost saving rightly tops the list of security as a service benefits for businesses. The “as-a-service” model is mainly available on a subscription basis, with several plans or solution packages to choose from. Consequently, you pay only for the tools and services you actually use. Additionally, such an approach eliminates the need to purchase hardware, buy and regularly renew software licenses, or hire and train additional staff.
#2 Easy scalability
Your business grows, as do the number of assets and potential vulnerabilities. Instant access to necessary technologies is another advantage that makes this business model thrive. You can add or remove services on demand according to your current needs and risks and rely on the provider to check and update the configurations. Besides that, you can quickly grant access to new users, ensuring the required agility and speed.
#3 Access to the best security specialists
Building domain expertise in-house is time-consuming and costly, especially considering the global IT talent shortage. Moreover, the lengthy recruiting process leaves your organization vulnerable. SECaaS providers have motivated and well-organized teams who bring in the missing experience, best practices, and insights. Moreover, they are available 24/7 via the agreed communication channels like email, phone, and others.
But most importantly, these SECaaS advantages allow you to free up expensive in-house resources and refocus them on more important, revenue-driving tasks. At the end of the day, you gain confidence and comprehensive visibility to continue growing and outmaneuvering the competitors.
How to choose a SECaaS provider
to help you respond to known threats and whatever new tomorrow will bring
If you think that IT security as a service is a good fit for your business needs and goals, selecting a reliable provider is critical to make it work. Like with any other alliance, you can achieve the best results only by doing proper research, making a well-informed choice, and engaging the right partner. So, what should you look for when you choose a security-as-a-service provider?
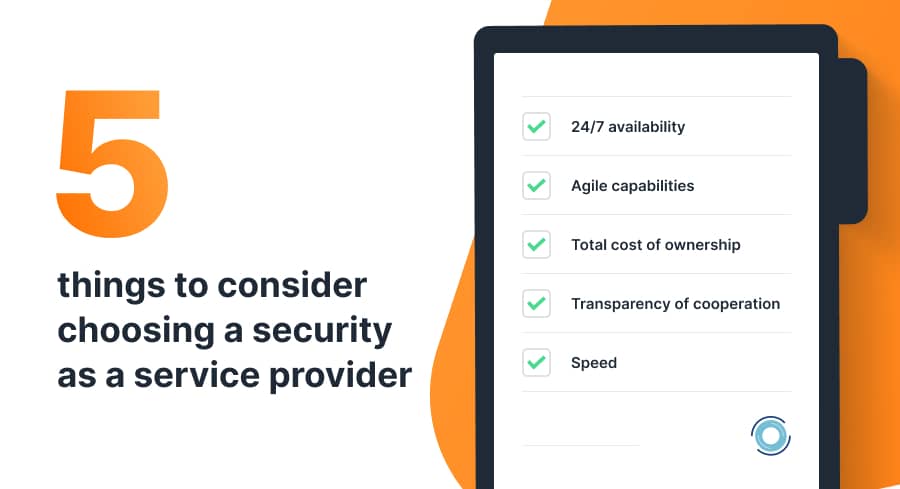
- 24/7 availability. Business protection functions must run round-the-clock to be effective. And though most cloud-based services bring in nearly constant accessibility, you need to be sure that the people behind these solutions are also available to respond to any issues or threats immediately. Otherwise, your organization will be vulnerable, and you may want to see more options.
- Agile capabilities. Most companies offer a wide range of services, allowing you to pick the necessary ones to keep your costs down. However, consider your current needs and think ahead to secure your future business growth. If you face a new problem, will the SECaaS provider be able to scale and propose a quick and relevant solution? In this context, companies like UnderDefense, with various capabilities and offerings, may be more effective in the long run. They can support you with additional services in case of emergency or as your number of assets increases, saving you months of researching, negotiating, and onboarding a new security ally.
- Total cost of ownership. We’ve already mentioned cost savings as one of the key SECaaS benefits. However, be sure to double-check the suggested business plans and their pricing models. Read the fine print and discuss all your questions and concerns with the provider to ensure you’re on the same page. Otherwise, you may end up overpaying for the provider’s ads but get less value and quality that are vital for your business.
- Transparency of cooperation. Though security as a service company takes on all the tasks and actions related to your business cyber security, you still want to know the score. So, comprehensive and readable reports provided regularly are crucial for effective and transparent engagement. You should be able to see all security measures and events, attack logs, incidents solved, and other important information. Check the vendor’s service level agreement, find out what indicators they collect, and how often they report them. Finally, ask for client testimonials, report examples, and other references that can help you make a good choice.
- Speed. In cybersecurity, every second matters, so timing is critical. This factor refers to both onboarding and the actual collaboration process. If you consider a SECaaS platform, ask for a guided demo and see how user-friendly and straightforward the product is. Choosing a SECaaS provider, specify what uptime and response time the company guarantees. Their team must be on guard and react instantly whenever an issue arises.
Risks of security as a service and how UnderDefense solves them
SECaaS risk 1: Dependence on the actions of the provider
Have you heard the saying, “The cobbler always wears the worst shoes”? Well, that’s what we should pay attention to here. Some IT security-as-a-service providers may access, collect, and process a large bulk of data, becoming a worthwhile target for cybercriminals. So, if they are hacked, your company may be at risk too. That’s why the security consciousness of your entire supply chain and your security partner is crucial. Ensure that the selected vendor has certificates and all the necessary security measures and practices in place. You can also conduct a security audit if necessary.
Our solution. UnderDefense is ISO 27001 certified, meaning that we take information security seriously. The company has important security processes at work, including physical security controls and 24/7 monitoring, detection, and response. Moreover, our team doesn’t store or process any client’s data and has read-only access to the resources. Working with organizations, we use telemetry and metadata, which means that all information that we receive is strictly related to network and system performance.
SECaaS risk 2: Security knowledge outflow
Outsourcing any business function or engaging an external partner is considered risky because the key knowledge holder is actually outside your organization. Meanwhile, as a business stakeholder, you must have end-to-end visibility and keep abreast of all the latest threats, attacks, updates, and implemented measures. Finally, you should be able to answer simple questions like what, when, and why something has happened in terms of business security.
Our solution. Apart from security awareness training sessions that we prepare and conduct for the client’s staff, we also provide and present comprehensive security reports on the work done. By doing so, we help business executives stay up-to-date on all the completed activities and prevented threats. Additionally, we keep management and employees informed of the current threat landscape, security best practices, and innovations in the field.
Being prudent makes all the difference
Ready to get started?
Security outsourcing is not new. However, the pandemic and shift to remote work have given it a tremendous impetus and turned SECaaS into one of the top security trends of 2023 and beyond. Whether you aim at saving costs, protecting your IT infrastructure, or quickly plugging security skill gaps on your team, security as a service can provide much value to your organization.
For your SECaaS initiatives, try UnderDefense MAXI security-as-a-service platform. It’s a one-stop shop for your compliance, security automation, advanced MDR, and reporting needs. No matter if you’re a team of one or hundreds, it is one unified and powerful solution that eliminates complexity, additional hires, and overhead. Start for free today and see how easily you can solve your security challenges with UnderDefense.
















