Cloud adoption, hybrid work, and interconnected IT ecosystems create a spreading external attack surface. This includes everything from web applications to public cloud resources, which are becoming a growing challenge for security teams. External Attack Surface Management (EASM) is vital in the ongoing fight against cyber threats. It offers comprehensive visibility, proactive vulnerability management, and continuous threat monitoring, empowering organizations to secure their external assets and stay ahead of sophisticated cyberattacks.
In our previous article about the top 5 attack surface management vendors, we’ve already explored the most powerful solutions you can choose from. It’s no longer a luxury but an essential tool for building enduring cybersecurity defenses and safeguarding digital assets.
Let’s explore how EASM can deal with security challenges, how to choose the right tool, and what tendencies are waiting for your business in the future.
What is external attack surface management?
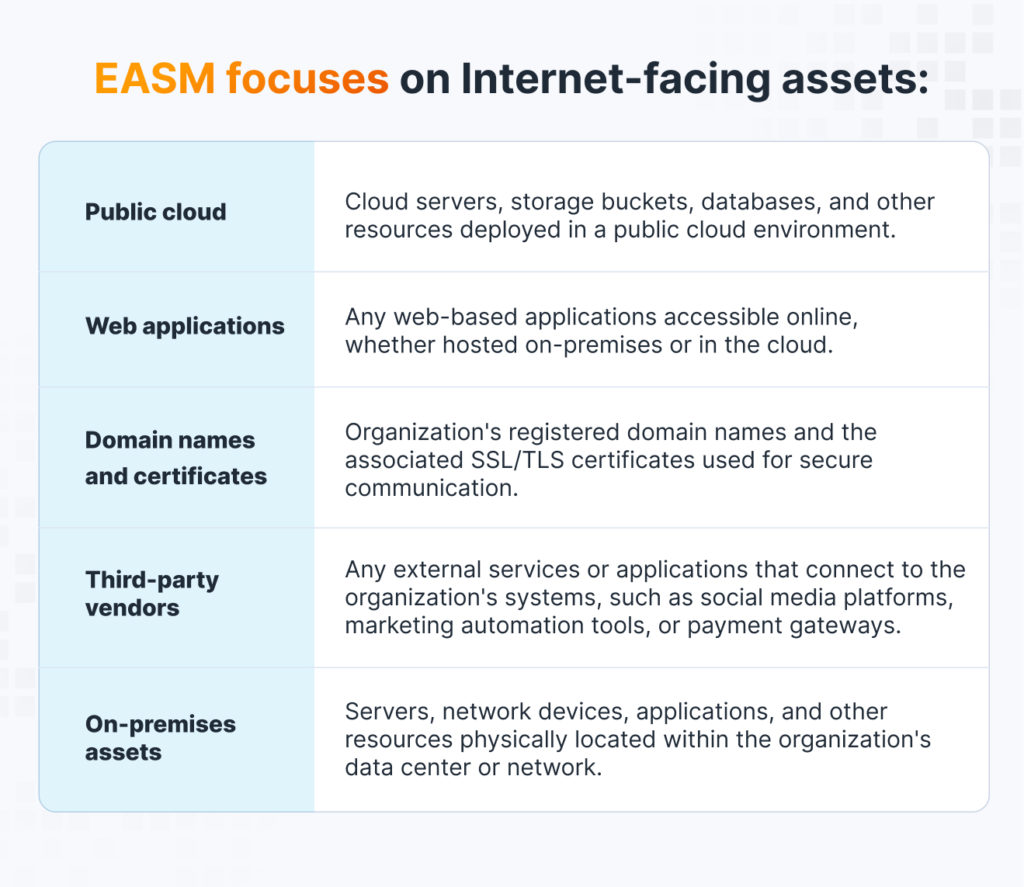
Let’s start by defining an External Attack Surface. Also known as a Digital Attack Surface, it is the sum of an organization’s internet-facing assets and the associated attack vectors that can be exploited during an attack. So, External Attack Surface Management is a continuous practice of discovering and assessing Internet-facing assets and looking for their vulnerabilities and anomalies.
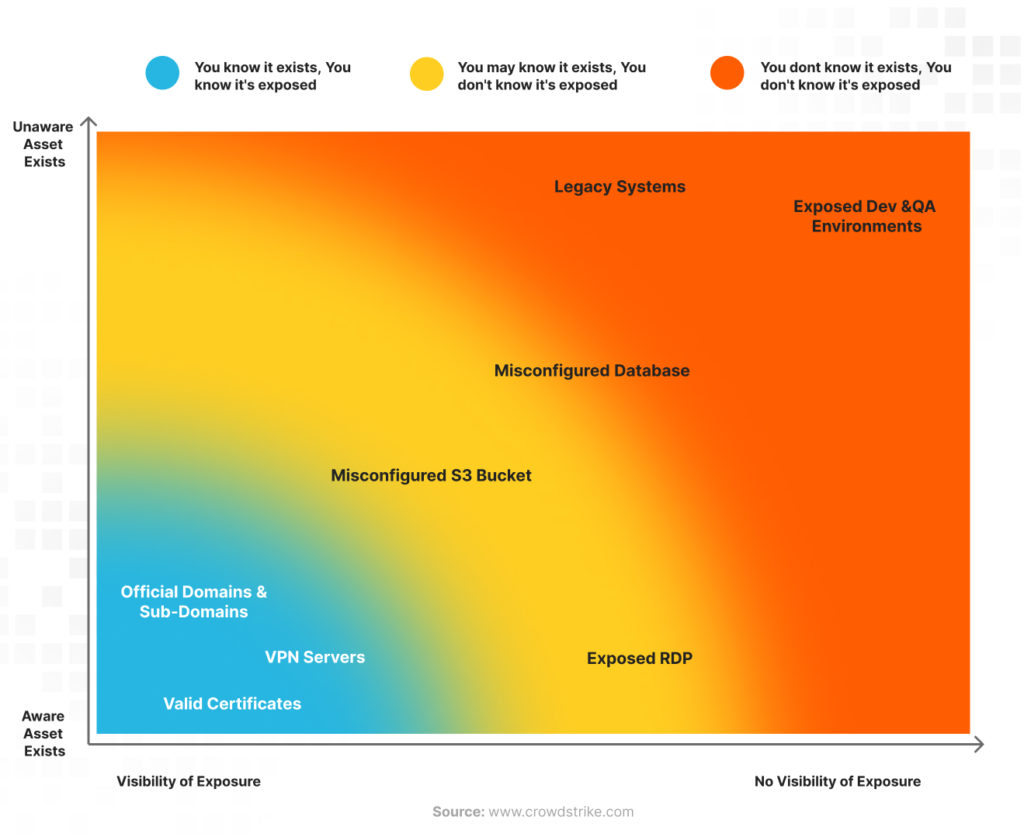
This diagram exposes the dangers of a hidden attack surface. The “visible & exposed” assets are manageable on the first level. However, the second and third levels, “potentially exposed” and “completely unseen,” pose significant risks. These unknown assets could be exploited by attackers. EASM solutions can help you identify and manage your external attack surface, minimizing vulnerabilities and keeping your organization secure. As shown in the graphic below, a significant portion of your attack surface may be hidden, posing a major security risk:
EASM aims to provide a holistic view of all these assets that attackers could potentially exploit. Organizations can better understand their security posture and proactively mitigate potential risks by identifying and monitoring these assets.
Tools and techniques for securing your digital assets
By empowering your organizations to comprehensively identify, classify, and manage external assets, EASM tools become a powerful weapon in the fight against cyber threats. Here are the main approaches that EASM tools leverage to achieve their goals:
- Discovery and Inventory: Identifying and inventorying all internet-facing assets.
- Monitoring and Vulnerability Management: Proactively identifying vulnerabilities in external assets.
• Vulnerability scanning: EASM tools scan identified assets for known vulnerabilities using various vulnerability databases and scanning engines.• Configuration management: These tools monitor asset configurations for changes that might bring security risks.• Security Information and Event Management (SIEM): EASM tools often integrate with SIEM/SEM solutions to collect and analyze security events from various sources, including the discovered assets, for potential threats.
- Risk Management and Prioritization: Assessing the potential impact of identified vulnerabilities and prioritizing which ones to address first.
Overall, Monitoring and Vulnerability Management is a crucial component of any comprehensive cybersecurity strategy, especially when it comes to protecting your organization’s internet-facing assets. Regular scans help to identify newly discovered vulnerabilities or changes in existing ones. Proactively identifying, assessing, and addressing vulnerabilities helps significantly reduce the risk of cyberattacks and safeguard your valuable data and systems.

We have looked into the main approaches of EASM tools and the benefits that come with them. It shows that proactively managing your external attack surface can significantly strengthen your overall security posture, enhance compliance, and build a more resilient defense. Next, we will dive into the reasons why you need to take a closer look at the external perimeter of your organization.
Why EASM is critical for security now
It’s no secret that cyber threats are constantly evolving, becoming more sophisticated, and targeting every kind of business regardless of industry and size. Bad actors continuously search for new vulnerabilities, including zero-day exploits (previously unknown vulnerabilities), to access sensitive information by disrupting critical systems and gaining profit.
There is a dangerous tendency that surged in 2023 connected directly to the EAS, which CybelAngel 2024 State of the External Attack Surface Report compiled in the following numbers:
- Exposed databases surged 100% in 2023, doubling from 740,000 to 1.5 million.
- Cloud-based data exposure skyrocketed 11% in 2023.
- Nearly 8 out of 10 alerts (about 79%) clients received in 2023 originated outside their IT network, highlighting the external threat landscape.
It’s a signal to CISOs and security teams to put regular scans and monitor the external perimeter of their organization on a to-do list. Returning to the graphic of visible and no-visible exposure, the risks of Internet-facing assets can become serious security threats requiring assessment and timely remediation. Here come in handy powerful MDR solutions capable of orchestrating running tools and adopting a proactive security approach.
The data from 2023 gives profound insights into how companies face increasingly numerous and sophisticated attacks. CybelAngel’s 2024 State of the External Attack Surface Report shows that ransom demands have increased by 40% due to the development of RaaS (Ransomware-as-a-Service) services. Another important point we can make is the necessity of awareness training.
Organizations can significantly bolster their defenses and mitigate the growing risk of cyberattacks by prioritizing proactive external security measures and adopting a vigilant approach.
How to choose the right EASM solution
With many EASM solutions available, selecting the right one becomes crucial. Here we will equip you with practical steps to navigate the selection process. By understanding your unique needs, evaluating key features, and carefully considering vendors, you can find the ideal EASM solution to fortify your external defenses and enhance your overall cybersecurity posture.
Additionally, you can check our article about Top 5 Attack Surface Management Vendors, where you can find the list of the best solutions in the market. Weight their key features to make the choice. While the 3-step process provides a solid foundation, choosing the ideal EASM solution requires a deeper dive into specific features and considerations.
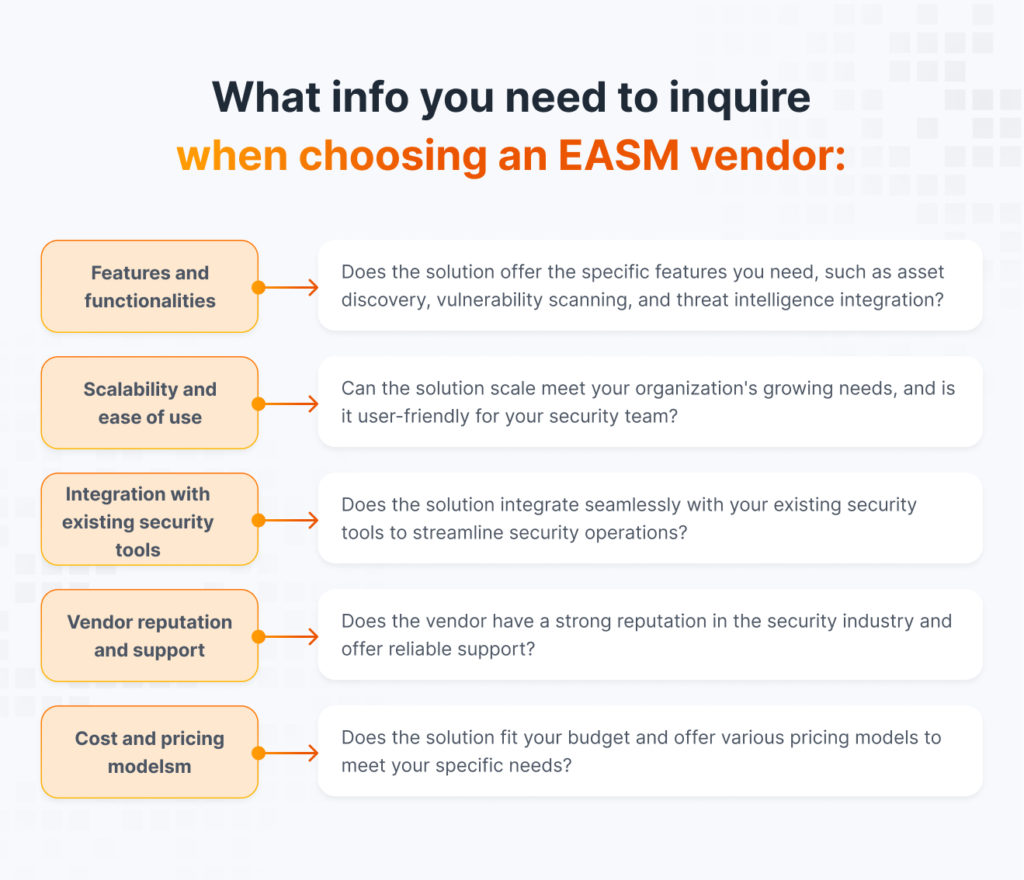
By carefully considering these factors alongside the outlined 3-step process, you can make an informed decision and select the EASM solution that best fits your organization’s needs and security goals. Remember, the chosen solution should empower your security team to proactively manage your external attack surface and ensure a more resilient defense against ever-evolving cyber threats.
MAXImizing the defense of your external perimeter
One of the biggest challenges companies face is that the public-facing perimeter constantly expands and changes. But how can you be sure you have identified and prioritized all security gaps? Here are the key steps for tracking your EASM effectively:

Overall, the UnderDefense MAXI platform can streamline security for your digital ecosystem. It simplifies every action in attack surface management with a few clicks. Also, it will empower your organizations to effectively monitor, detect, and manage vulnerabilities across your entire digital ecosystem, eliminating the need for using multiple disjointed security tools.

One of the key features of the UnderDefense MAXI is the Dashboard, which provides easy navigation and is updated in real-time. There, you will find all vital information on your domain: risk summary, estimates of 1-day business interruption, ransomware payment, and post-breach recovery cost. The additional advantage is the Concierge Service, which is available 24/7 and ready to help with remediation guidelines or explain the dashboard indicators.
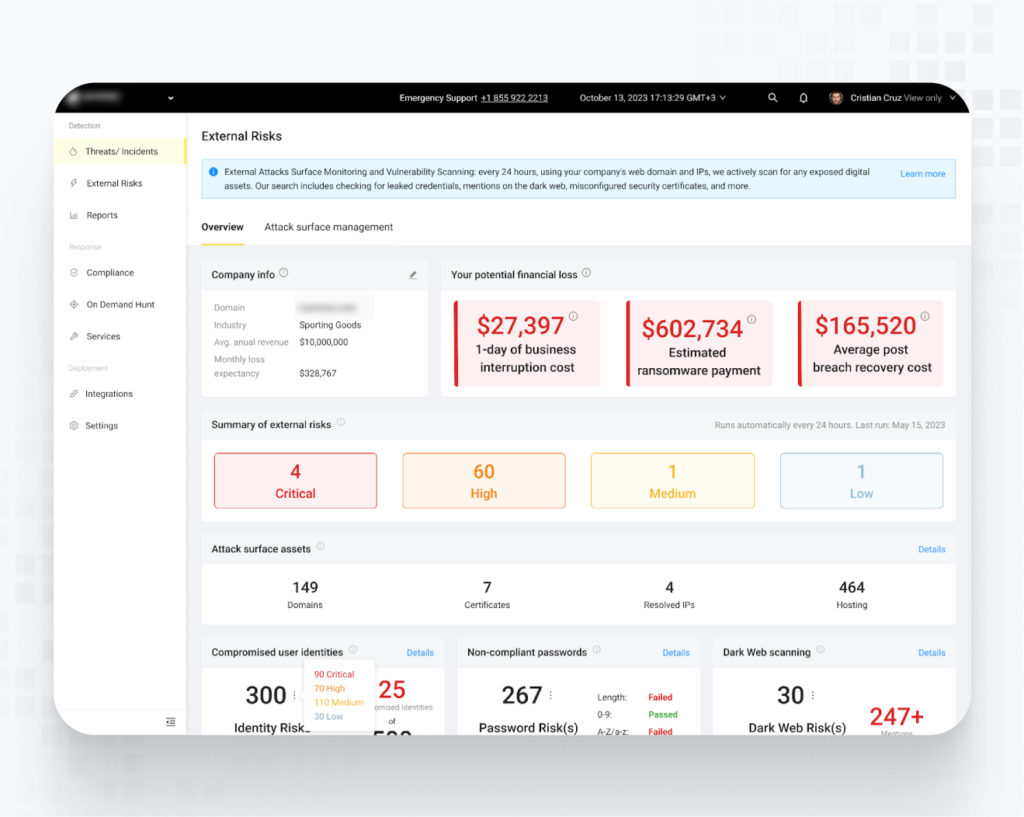
Key features of External Vulnerability Scan:
- Leaked Corporate Credentials. The scan analyzes if any corporate credentials were leaked and can be used by attackers to access your data and internal network. It can reveal issues with password governance within an organization.
- Mentions in the Dark Web. The search includes various mentions in the dark web, like leaked credentials or exposed corporate data that attackers might exploit. It can also indicate an ongoing or already executed attack.
- Certificate Misconfiguration. The scan can identify expired, self-signed, or improperly configured certificates, highlighting potential vulnerabilities for man-in-the-middle attacks or data interception.
- Domain Reputation. The main goal is to check whether malicious activities like phishing emails, spam, malware, or scams have been running using your domain, which could have damaged or lowered its reputation.
- Email Authentication Misconfiguration. The scan shows errors or oversights in setting up and implementing email authentication protocols like DKIM/DMARC authentication. It can lead to vulnerabilities that attackers can exploit, potentially enabling email spoofing.
One way to accomplish effective defense is to know your organization and adversaries. It’s vital to regularly monitor your Internet-facing assets and prioritize your efforts and resources in mitigating vulnerabilities. Knowing bad actors’ moves, motives, and techniques is also vital. Experts at UnderDefense are ready to guide you through every step of enhancing your EASM. Starting from a complimentary scanning of your external perimeter and moving to the vulnerability assessment or other services, you can receive a security roadmap.

We have created a solution, the UnderDefense MAXI platform, that doesn’t just get the job done but also helps you save time, money, and human resources. This is the way to bring together everything you might need for cloud security under one roof—24×7 threat detection, full visibility of your network health and security posture, and real-time detection of attacks against your infrastructure. Even the lack of security resources isn’t an issue anymore.
The future of EASM
EASM is rapidly becoming the cornerstone of an organization’s security strategy in the face of ever-evolving threats. Advancements in automation, machine learning (ML), and artificial intelligence (AI) will further enhance its capabilities, making EASM indispensable for securing today’s digital footprint. The future of EASM lies in seamless integration with existing business processes. Sophisticated AI and predictive analytics will enable proactive security measures, allowing organizations to anticipate and mitigate threats before they occur.
Organizations will strategically leverage EASM as a foundation, incorporating Digital Risk Protection Services (DRPS) and Cyber Threat Intelligence (CTI) to enrich its effectiveness. Gartner predicts a surge in converged solutions, with 70% of organizations utilizing a combined ASM and DRPS offering by 2026.
These additions provide valuable layers of intelligence and protection, empowering EASM to deliver positive security outcomes. As digital ecosystems expand and regulations evolve, so adaptable EASM, DRPS, and CTI solutions will become increasingly critical. EASM, when combined with those solutions, forms a comprehensive exposure management framework. This unified approach fosters proactive cybersecurity, enhances decision-making, optimizes resources, and strengthens trust within the digital ecosystem.
The journey of EASM, evolving from a tool for cyberwarfare to a mainstream business necessity enriched by DRPS and CTI, exemplifies the ever-changing dynamics of the digital world. As threats evolve, so must our methods of managing and mitigating them. EASM can offer a powerful defense against threats.
Conclusion
Rapid cloud adoption has transformed how businesses operate. While offering agility and scalability, it also paves the way for highly dynamic assets. As a result, the more you move to the cloud, the more adversaries move to the cloud with you. These hidden threats are often difficult to track and monitor.
Reaching 100% visibility is elusive in these conditions, but effectively organized defense amplified with UnderDefense MAXI can significantly strengthen your security posture. Consulting with UnderDefense security experts can help you navigate the threats of the external perimeter. Contact us today to choose the best approach for your organization.