Do you need a pentest but are worried about deciphering the report? Are you seeking a pentest report template that saves time and empowers informed decisions?
Here’s how UnderDefense can help!
We offer an industry-leading pentest report template and expert guide to create clear, actionable reports that empower decision-making.
Unveil valuable insights with our structured format, clear explanations, and actionable recommendations. Get your free template now and transform your findings into a security roadmap that strengthens your defenses.
Ready to go beyond a template? Order a professional pentest from UnderDefense and receive a custom report built on our industry-leading template, along with expert analysis and remediation guidance.
Free Remediation Guidance Included!
Pentesting reports: Communicating your findings effectively
Penetration testing reports are the cornerstone of conveying the value of security assessment. The written report transforms the intangible process into a tangible product, offering clients a clear understanding of their security posture. Effective communication is key, as the report must resonate with various audiences, technical and non-technical.
UnderDefense’s reports go beyond the surface, providing
- Clarity: We communicate findings in a structured and understandable format, ensuring everyone grasps the vulnerabilities and their potential impact.
- Actionability: Our reports don’t just highlight issues; they offer concrete recommendations to strengthen your defenses against evolving threats.
- Transparency: Detailed information and evidence-based findings allow for informed decision-making.
- Strategic Guidance: We provide a snapshot of vulnerabilities and strategic recommendations to build a robust long-term security posture.
By combining clear communication with actionable insights, UnderDefense’s pentesting reports empower you to take decisive action and fortify your organization’s security.
Why accurate pentest report is important for business?
An accurate penetration testing report is crucial for businesses for several reasons:
Identifying vulnerabilities | Assessing risks | Compliance requirements |
Penetration testing reports provide a detailed analysis of potential vulnerabilities in your organization's systems, networks, and applications. Identifying these vulnerabilities allows you to address security weaknesses before malicious actors exploit them. | By accurately documenting findings and assessing their potential impact on the business, penetration testing reports help you prioritize remediation efforts based on the severity of the identified risks. This enables you to allocate resources effectively to mitigate the most critical threats first. | Many industries have regulatory requirements mandating regular security assessments, including penetration testing. Accurate penetration testing reports demonstrate compliance with these regulations and help you avoid potential fines and penalties for non-compliance. |
Building trust | Preventing data breaches | Informing security investments |
Demonstrating a commitment to security through accurate and thorough penetration testing reports helps build trust with customers, partners, and stakeholders. It reassures them that the organization takes security seriously and is actively working to protect sensitive data and assets. | Penetration testing reports uncover vulnerabilities and provide recommendations for remediation. They help prevent data breaches that could result in costly downtime, financial losses, reputational damage, and legal liabilities. | Accurate penetration testing reports provide valuable insights into the effectiveness of existing security measures and help businesses make informed decisions about future security investments. This ensures that resources are allocated to the most needed areas to strengthen the overall security posture. |
Guide: How to write a penetration testing report?
What has to be included?
Executive summary
- Project objectives
Clearly defined goals and objectives for the penetration testing engagement aligned with the client’s concerns. - Scope, timeframe, and limitations
Detailed explanation of the testing scope, duration, and any constraints or limitations encountered during the assessment. - Summary of findings
A concise overview of the key findings discovered during the testing, highlighting critical vulnerabilities and areas of concern.
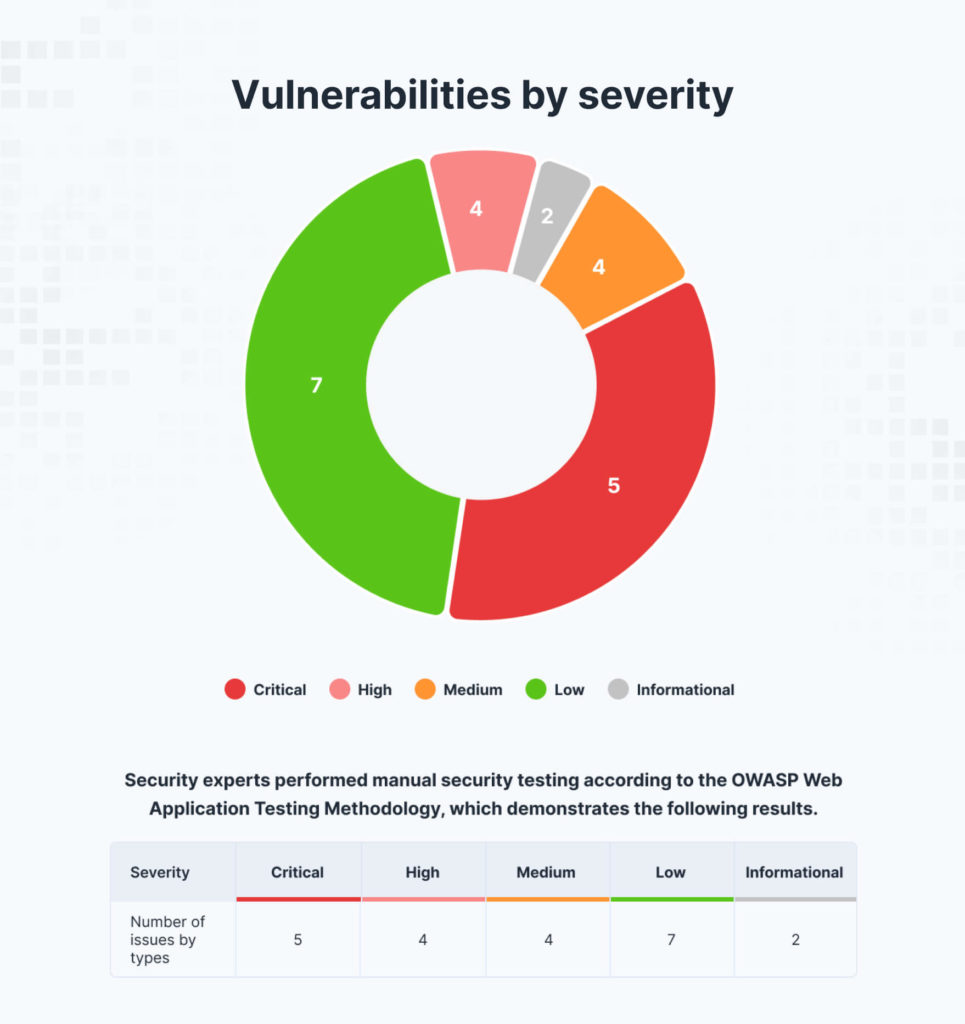
- Summary of business risks
Assessment of the potential impact of identified vulnerabilities on your organization’s business operations and reputation.- → Data breach: What sensitive data could be compromised?
- → Financial loss: What financial losses could occur due to the exploitation?
- → Reputational harm: How could the organization’s reputation be damaged?
- → Operational disruption: How could the attack disrupt business operations?
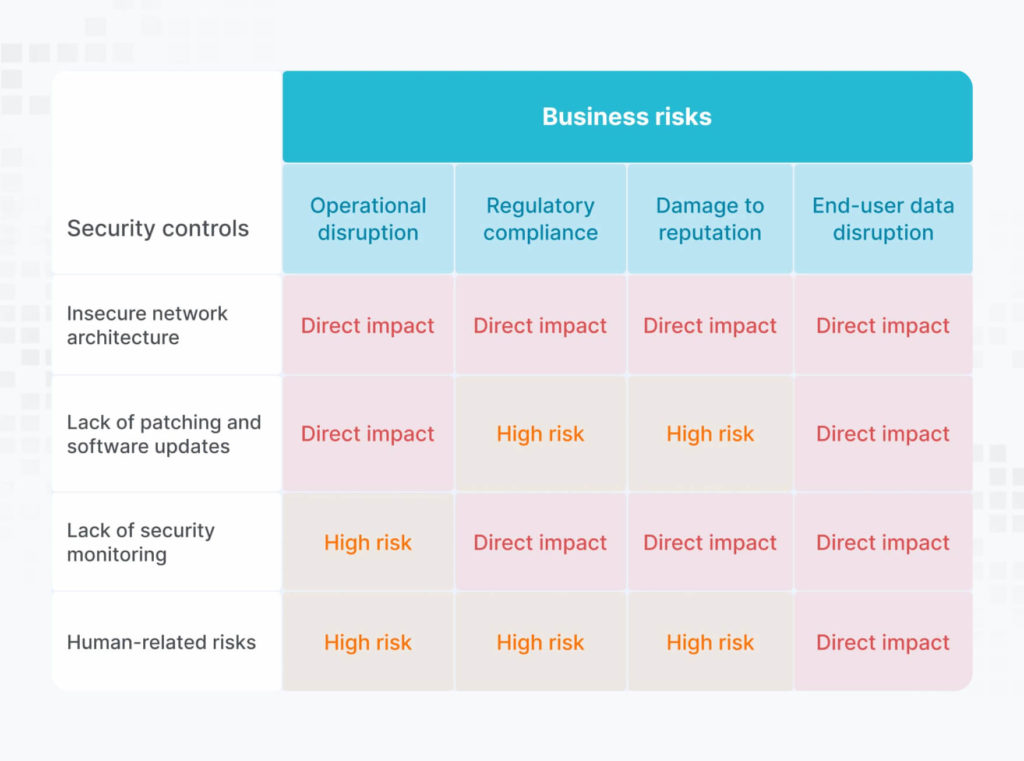
- High-level recommendations
Actionable recommendations for remediating the vulnerabilities, categorized by severity and risk:- → Critical: Immediate mitigation actions like patching or disabling vulnerable systems.
- → High: High-priority actions like patching or implementing additional security controls.
- → Medium/Low: Suggestions for longer-term remediation efforts.
Project disclaimer
- Methodology
Insight into the methodology employed during the testing (e.g., white box, black box, grey box), providing transparency into the approach used to identify vulnerabilities. - Security tools used
Overview of the tools and techniques utilized during testing, including automated scanning tools and manual testing methodologies. - Project limitations
Any limitations or constraints encountered during the testing process and their potential impact on the overall assessment.
Findings details
- Description
A clear explanation of the vulnerability. - Severity
The vulnerability’s potential impact, using a common system like CVSS. - Exploit details
How the vulnerability could be exploited by a malicious actor (technical details may be redacted). - Proof-of-Concept (POC)
Evidence that the vulnerability exists, potentially including screenshots or logs. - Remediation
Specific recommendations for addressing the vulnerability.
Appendices
- Additional technical details
Screenshots, network diagrams, or raw scan results that provide further context and support for the findings and recommendations (e.g., Mapping of identified vulnerabilities to the MITRE ATT&CK framework, providing additional context and insight into potential attack vectors and techniques)
Details to pay attention to
- Accuracy: Ensure findings are accurately documented with evidence.
- Clarity: Use clear and concise language to communicate findings and recommendations.
- Relevance: Focus on vulnerabilities that pose the greatest risk to the organization.
- Actionability: Provide actionable recommendations with step-by-step instructions for remediation.
- Context: Include relevant contexts, such as system configurations and network diagrams, to support findings.
How to make it effective and actionable?
- Prioritize critical issues: First, address critical vulnerabilities to mitigate the most significant risks.
- Provide context: Explain the potential impact of vulnerabilities on business operations to help stakeholders understand the importance of remediation.
- Include remediation steps: Offer clear and practical steps for addressing each vulnerability to facilitate timely and effective remediation.
- Engage stakeholders: Ensure the report is accessible and understandable to technical and non-technical stakeholders to encourage collaboration and buy-in for security improvements.
- Follow-up: Schedule follow-up discussions to review the report findings, address any questions or concerns, and track progress on remediation efforts.
- Offer timelines and resources: Estimate implementation timelines and resource requirements for recommended actions.
Frequently asked questions (FAQ)
1. What is a penetration testing report?
A penetration testing report is a document that summarizes the findings of a simulated cyberattack against an IT system. It details discovered vulnerabilities, their severity, potential impact, and recommendations for remediation. It is a crucial communication tool for security professionals and management, guiding informed decision-making to improve an organization’s security posture.
2. What are the types of penetration testing reports?
There isn’t a standardized format for pentesting reports, but they typically share essential elements like methodology, findings, risk analysis, and recommendations. However, the detail and technical information level might vary depending on the:
- Audience: Reports for technical audiences may include detailed technical explanations. At the same time, those for non-technical stakeholders may use simpler language and focus on business impact.
- Engagement type: Different pentesting approaches (e.g., black box, white box) may yield reports with varying levels of detail about the testing process and exploited vulnerabilities.
- Client requirements: Clients can specify their preferred format and level of detail within the report.
3. How much do penetration testing reports cost?
Several factors influence the cost of a penetration testing report:
- Scope and complexity of the test: Larger and more complex engagements involving multiple systems or deeper testing levels generally cost more.
- Location and experience of the testing team: The expertise and experience of the pentesters can affect the cost.
- Client requirements and report format: Highly customized reports with detailed technical information may be more expensive.
4. Who should read a penetration testing report?
Penetration testing reports are designed to be read by various organizational stakeholders, including executives, IT professionals, security analysts, and compliance officers. Non-technical stakeholders can benefit from executive summaries, while technical personnel may delve into the detailed findings and recommendations.
5. What are the benefits of conducting penetration testing and producing a report?
Penetration testing helps organizations identify and address security vulnerabilities before malicious actors can exploit them. Producing a comprehensive report allows organizations to prioritize remediation efforts, comply with regulatory requirements, and demonstrate a commitment to cybersecurity to customers, partners, and stakeholders.
















