If you are here – most likely, you are going to perform penetration testing (also called “pen test”, “pentesing”. Customers ask you about pentest, or it is a compliance requirement. Or you are the one who just takes care of the company’s state of security.
If it is your first penetration testing, you have more questions than answers. Is pentest what you really need right now? What might happen if you decide to avoid it? How much money do you need for a high-quality service? This article combines answers to the most common questions and average penetration test prices to help you make the right decision.
Table of content
- Do I Really Need Penetration Testing?
- Why, When and How Often to Perform a Penetration Test?
- What is Penetration Testing?
- Which Type of Penetration Test Should I Choose?
- How Much Does Penetration Testing Cost?
- What is The Real Value of Penetration Testing?
- Conclusion
Do I Really Need Penetration Testing?
Only you can decide if you need a penetration test. The same as only you can decide if you need to go to the dentist regularly for check-ups or once per 10 years to pull teeth.
But before making a final decision about pen test service, take a look at this FBI report statistic. There is an Internet Crime Complaint Center (IC3) accountable to the FBI. This service exists to fight cybercrime and as an addition to composing statistics on cybercrime. Every year the FBI publishes the Internet Crime Report based on this statistic. The results of 2020 are terrifying. The frequency of some types of cybercrime increased up to 300%, and the cost of some crimes has increased by more than 2,400%. For example, only in California victims lost $621,452,320 in cybercrime. Unfortunately, fighting cybercrimes has become a routine, and the only way to deal with it is to be ready and protected.
Manual penetration testing is the perfect way to see if you’re safe from attacks or data leaks. With the penetration testing service (in other words ethical hacking services), you will learn about your business’s vulnerabilities before they become the targets of malefactors.
Why, When and How Often to Perform a Penetration Test?
The primary purpose of pentesting is to identify how the company might be hacked and highlight weaknesses in its current security policies. Overall, you need a pentest if you need:
- Penetration testing for regulatory compliance and audit;
- To prove to your clients that you are secure and trustworthy;
- Pentest as a stage of your SDLC;
- To be sure that your application updates are secure;
- To know what problems are in your security posture;
- To see if/how your business can be hacked;
- To be sure that you don’t have the same security problems as you hacked competitors had;
- to get strategic and tactic recommendations from security experts;
- To minimize everyday risk for your employees, business, and clients.
Regulation of performing penetration testing depends on updates in your network infrastructure or applications, on certificates your business maintains, on the size of your company, and other custom factors. We recommend consulting with a trusted cybersecurity vendor to plan to perform ethical hacking.
There are various software applications for vulnerability searching or attack simulation. But none of them can show how vulnerable the tested system is. You can only see if your system can resist a real attack by applying for ethical hacking. No software can imitate the unpatterned behavior of real hackers using manual techniques.
What is Penetration Testing?
Penetration testing, “pentest,” or ethical hacking, is almost the same as a simulation of real-world attacks, the difference is that certified penetration testers provide it with client’s permission and field limits of services defined by the customer. To understand it better, imagine the crash test for the car before it goes to the market.
The main aim of the pen test service is to show the real state of a business’s cybersecurity for the customer. Pentesters not only search for vulnerabilities but also try to exploit them. Pentesters mimic real hackers’ specific tactics, techniques, and procedures (TTPs) to illustrate how the breach might happen to the customer.
Which Type of Penetration Test Should I Choose?
During the testing, an ethical hackers team simulates the attacker’s behavior, testing the security of your application/organization from various attack vectors, simulating inside attacks (when malefactor has already got inside the system) or external threats (when malefactor tries to get inside). To define your sensitive vectors that need to be tested take a look below at the types of pentest, what they are used for, and what these tests include.
Types of Penetration Testing
In penetration testing vendors offerings, you can find the following penetration testing types that our ethical hackers specialize on:
- External penetration test – the assessment of the internet-facing systems to determine if there are exploitable vulnerabilities or misconfigurations that expose data or allow unauthorized access.
- Internal penetration test/network penetration testing – the assessment of internal systems and applications, conducted to determine how deep the malicious insider can reach.
- Mobile application assessment – the testing for platform-specific vulnerabilities; an application security audit inside Android/iOS environment.
- Social engineering – the testing of how vulnerable client’s employees are to social attacks (such as phishing).
- Web application penetration testing – testing for vulnerabilities according to OWASP top 10.
- Internet of things (IoT) security assessment – security assessment of the IoT solutions to ensure end-to-end security.
- Red team attack simulation – a comprehensive assessment of how quickly and efficiently a client can respond to the attack – checking the company’s detection, defense, and response capabilities.
Read here in more detail about what’s included in each type.
Penetration Testing Levels of Access Permission
Before signing a penetration testing contract, the vendor offers clients three main penetration testing methods divided by the level of access permission.
- White box pen testing – A penetration testing method illustrates how much damage an attacker with an authorized user could cause. The main feature of white box testing is that you give penetration testing services providers full access to your product/architecture (network infrastructure schematics). Also, the scope may include security code review if requested. This permission level allows pentesters to study the clients’ services more deeply in short testing time frames and brings more value from a security perspective.
- Gray box pen testing – A penetration testing method where pentesters have limited knowledge and only partial access to a user’s system. This penetration testing method directs attention towards access to critical data and observing how well the security processes are configured in client systems. Ethical hackers might simulate attackers’ actions with longer-term access to the network using the client test account.
- Black box pen testing (blind testing) – A penetration testing method that simulates an external threat where the pen testers have no information on the security policies, network structure, software, or network protection used. During the first stage, their main task is to test the external line of defense and estimate how strong the possibility is to come inside. If they get inside the targeted system, ethical hackers will move forward into the system with small steps, gradually trying to gain more access.
Difference Between Vulnerability Scanning and Penetration Testing
You already know what penetration testing is, but you might also find information about vulnerability scans. Let me explain what this service is.
Vulnerability Scanning is an automated tool’s actions that identifies known software vulnerabilities that can be exploited. And on the first sight, it may seem to be a cheap analog of penetration testing. But this is not the case.
There are two main differences between a vulnerability scan and penetration testing. A vulnerability scan is a tool, while penetration testing is conducted by highly-experienced security analysts – ethical hackers.
A vulnerability scan identifies only vulnerabilities that the tool was programmed to define, and it can be exploited, while penetration testers dig deeper and try to simulate real-world attackers’ actions to define firstly invisible vulnerabilities and find a possibility of compromising.
Vulnerability scanning is considered to be cheaper than penetration testing, so if the vendor offers you a suspiciously cheap pentest, most likely, it is just vulnerability scanning without further manual work of security experts.
Vulnerability scanning vs Penetration Testing
/ | Vulnerability scanning | Penetration Testing |
Type of Service | Understanding weakness sides using automated tools | Complex analytics service with the investigation of how to exploit vulnerabilities, which were found by vulnerability scanning |
Research Method | Automated | Manual |
Cost | Cheap | Expensive |
Result | Identifies known software vulnerabilities that can be exploited | Dig deeper and act like real world attackers to find the way to use these and unknown vulnerabilities and find a possibility of compromise |
When to Perform | As a part of penetration testing | As a stage in SDLC |
Keep in mind that no vulnerability scans can mimic the behavior of a real attacker. Don’t waste time and money on automated assessment.
How Much Does Penetration Testing Cost?
As with every service, the pentest may vary depending on several factors. The key components that determine the scope of work and the price are the number of testing IPs, web applications, and the number of roles and pages per application.
List of Factors that Influence Pen Test Pricing
Objective
The objective is exhibited during the consultation with the person who guides you during the work with the vendor. The object of testing is what actually needs to be tested in the customer’s business. Is it only application, IoT devices, network, or all of it? How many devices are in the network?
The size and complexity of the testing environment is the main factor that influences security test cost. Do you have a small local business? Or is it a worldwide international company?
Approach
Penetration testing pricing also depends on the approach, methodology, and tools set used to conduct penetration testing. If it is a comprehensive professional approach to ethical hacking, pentest vendors provide customers with the risk extent, give tactical recommendations for immediate improvement and longer-term recommendations for maturing the cybersecurity posture. Your pentest vendor’s team explains vulnerabilities’ influence and potential consequences for the business. The vendor should give a general security assessment that might vary from A (Excellent) to F (Inadequate) and give high-level recommendations to implement – that’s how we do this in UnderDefense. Also, ask your vendor to provide you with evidence and artifacts (videos and screenshots). Such materials allow IT and Development teams to recreate penetration testers’ findings.
Skills
As well as in all services, people’s professionalism is the key in penetration testing. Applying for penetration testing, pay attention to the specialist who works with you. Buying pentest in a well-experienced company, you get a service provided by highly educated ethical hackers who understand malefactors’ actions and industry trends and use various attack vectors.
Re-Testing
The next step after conducting penetration testing is to cover founded cybersecurity gaps. But you need to know if you did it well enough. Here comes remediation testing. Some vendors provide 1-2 days of 100% free remediation assessment to attain a clean final report, confirm that all flaws are fixed, and be sure of your cyber reliability.
Advice of Choosing the Right Penetration Testing
Since we know what factors influence the price, let’s take a look at the price range that the market offers.
Penetration test service price limits
/ | Average Price, USD | Included | Deliverables | UnderDefense Tips |
min | 13 000 | Up to 3 weeks of testing; is provided by a few pentesters. | Standard network/ application testing. Good as a one time testing; might be not enough for black-box testing to find all critical gaps. | If a vendor offers you a lower price, but you know that your network is wide, be vigilant. It could be only vulnerability scan, shirt-terms pentest or service, provided by not-experienced pentesters. |
max | 60 000 | The team of high-experienced ethical hackers; duration – 3-6 weeks. | Penetration testing for wide-network companies. | This is a reasonable price for the service of the TOP pentest vendors. |
supermax | 100 000 | The team of high-experienced ethical hackers tests the system during >6 weeks. | Most likely, for this money, you will receive full organization penetration testing. | Pay this amount of money only if you have a super huge business and TOP vendor. |
Comparison of Penetration Testing Cost by Type
Different pentest types cost differently and might greatly vary not only because of complexity and scope but also due to special customer requirements.
Comparison of Penetration Testing Cost by Type on the US market
Penetration Testing Type | Average Cost, USD |
Mobile Application assessment | 17 000 – 21 000 |
External penetration test | 16 000 – 19 000 |
Internal penetration test/network penetration testing | 17 000 – 22 000 |
Social Engineering | 15 000 – 20 000 |
Web Application penetration testing | 20 000 – 22 000 |
What is The Real Value of Penetration Testing?
Cost Loses from Cyber Attacks
Every year the world becomes more and more digitized. And unfortunately, cybercrime has become a new normal – as offline crime is. Some companies lose millions of dollars, reputations, and customers in cyberattacks. Some lose whole businesses. And some don’t lose anything. The key here is cyber resilience and a proactive approach to cybersecurity. Take a look at 5 biggest cyber attacks in 2021.
Examples of Cost Loses from Cyber Attacks*
Company | What Happened? | Ransom |
Colonial Pipeline | The attack on Colonial Pipeline was the most shocking in 2021. This situation has shown how vulnerable each of us is to cyberattacks. The attack on the largest fuel pipeline in the USA caused disruption of fuel supplies in 12 states of the USA and caused long queues for fuel | Paid $4.4 million |
Acer | Taiwanese multinational hardware and electronics corporation Acer had been attacked by a Russia-based REvil (Ransomware Evil) hacker group | Demanded $50 million |
JBS Foods | JBS Foods, one of the largest American-based food processing companies, was attacked by REvil, the same Russia-based hacking group that hacked Acer. Due to this attack, meat processing operations stopped in Canada, Australia, and the USA | Paid $11 million |
KIA Motors | Kia Motors suffered a ransomware attack. Though сompany representatives did not confirm they were hacked, their IT failured | Demanded $20 million |
CNA Insurance | CNA, one of the largest commercial property and casualty insurance companies in the USA, was hacked. Ransomware hackers gang hit 15,000 devices and compromised the data of 75,000 CNA employees. The Russian hacker group Evil Corp is supposed to be guilty of this cybercrime | Paid $40 million |
*Source: PrivacyAffairs
All of them entailed multi-million dollar expenses and a lot of inconveniences for people who use the services of hacked companies.
According to the IBM Report, the average cost of a data breach in 2021 is USD 4.24 million. During one year, data breach costs rose from USD 3.86 million and became the highest average total cost in the 17-year history of IBM reporting. The average penetration testing price is USD 20.000, which is 212 times less than the average cost of a data breach.
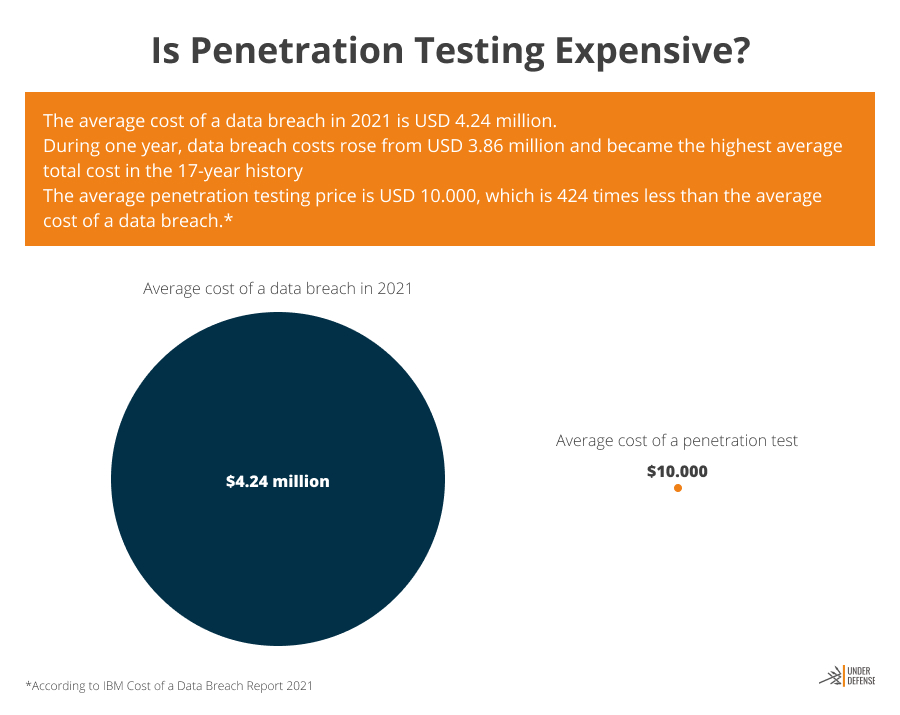
Think about a pentest not like spending but like business investment, which will help you keep your business protected continuously. If you still think that penetration testing is too expensive for you, don’t forget that the cost of an average data breach is much higher.
But don’t forget that penetration testing is a spot check of the state of security. Only with constant 24×7 security monitoring – MDR security services – you can see what is going on inside your system at the exact moment.
Cyber Risks for Small and Medium Businesses
If you are a small- or medium-sized business representative, you might have thought: “Ok, I don’t have that much money, my business is small, and I’m not interesting for hackers.” We are sorry to say that, but you are.
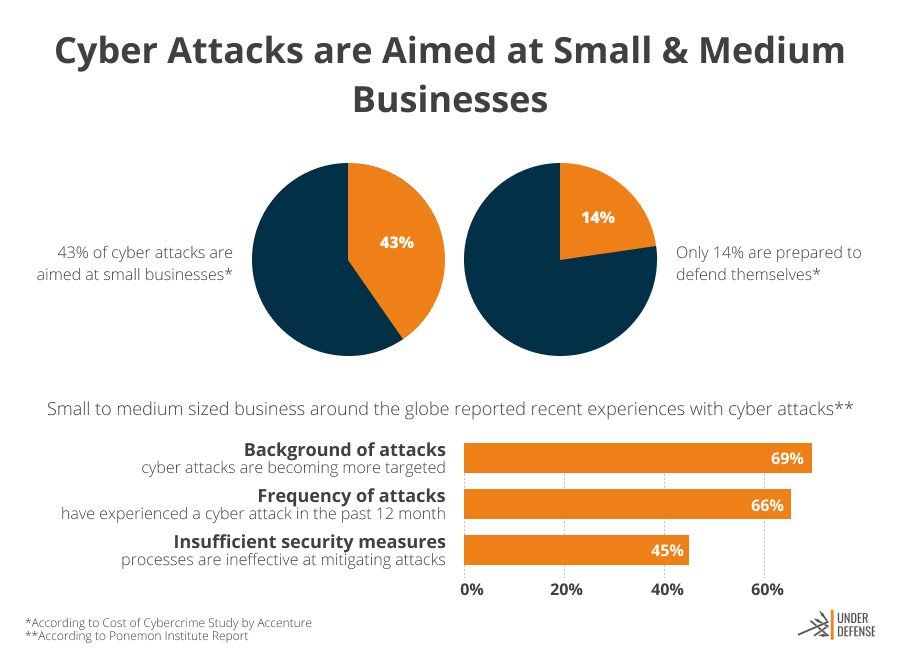
According to Accenture’s Cost of Cybercrime Study, 43% of cyber attacks happen with small-sized businesses. Unfortunately, only 14% of them are ready to defend. If cyberattacks damage important IT assets and infrastructure, it might be impossible for a small business to recover due to the high recovery costs and limited security budgets. Often cyberattacks become fatal for small businesses. If the attack blocks the business systems, it interrupts business processes and makes interaction with the clients impossible. And even if small companies have some budgets to recover, it most likely takes so long that they can easily be ousted from the market by competitors.
Ponemon Institute conducted a small and medium businesses survey about cyber attack experience and published the State of Cybersecurity Report. Here are the results of the survey:
- 45% of responders said that their actions are ineffective for attacks mitigation.
- 66% of responders had cyberattack experience during the past year.
- 69% of responders think that attacks became more targeted.
The bad news is that with a high probability, you will be attacked. The only question is, “Are you sure that you belong to a minority that will survive?”
Conclusion
Investing money on penetration testing is a wise and proactive investment, which helps to detect critical gaps in the cybersecurity business and save your business from irreparable damage. A trusted and thorough penetration testing vendor protects your money and reputation. But be vigilant while choosing the vendor. By buying a pentest that costs less than 13 000 USD, you risk getting a pig in a poke. Trust only professionals – certified ethical hackers teams who can prove to you their expertise by telling success project references and sharing anonymized reports of other clients. Professionals will easily and transparently explain to you what steps they will need to take and what results you will get.
Each business gets its particular penetration testing price, depending on the scope of work, assessment approach, and other factors. To understand how much money your company needs for penetration testing, consult with a potential vendor. Pay attention to whether the vendor is trying to understand your case, how much attention pays to your goals and details, available financial resources, and limitations.
Only regular penetration testing as a part of your cybersecurity program makes your business cyber resilient and saves you from a false sense of security.
For a comprehensive and reliable penetration testing service, consider reaching out to UnderDefense Penetration Testing Service. Our experienced team of certified ethical hackers is committed to enhancing your cybersecurity posture. Learn more about our services and how we can tailor them to your specific needs by visiting our website.
















