Introduction
The escalating frequency and sophistication of cyberattacks have made it critical for organizations to build robust SOC teams. A well-structured SOC team acts as the first line of defense, continuously monitoring and responding to potential security incidents to minimize the impact of cyber attacks.
As we reflect on our years of experience building and managing our own Lv. 5 SOC at UnderDefense, we will delve into the crucial role SOC teams play in your organization’s cybersecurity. A successful SOC team requires a strategic and systematic approach, where each team member understands their specific duties and how they contribute to the overall security objectives.
In this article, we will explore the essential elements of building and managing a strong SOC team, including hiring the right talent, providing continuous training, fostering effective communication and collaboration, and equipping your team with state-of-the-art security tools. By sharing our expertise and lessons learned, we aim to empower organizations to build a SOC team that protects against digital threats and ensures the security and resilience of their digital infrastructure.
About SOC team functions
What does a SOC team do? One of the most prominent scientific papers, “Security Operations Center: A Systematic Study and Open Challenges,” dives into architecture, main roles and responsibilities, and the main processes the SOC team is involved in. It also presents a clear definition of core roles, including tiers differentiation and their specialization.
The Security Operations Center (SOC) team is the heart of an organization’s cyber defense system. They are the ones who continuously monitor and safeguard an organization’s IT infrastructure against cyberattacks.
If you’re considering whether to build or hire a vendor for SOC services, we suggest you read the article “Outsourced SOC vs. In-House SOC: Making the Right Choice“, in which we examine both options in detail.
Proactive Security Measures | Threat Intelligence Gathering and Analysis: The SOC team actively gathers and analyzes threat intelligence to stay ahead of potential attacks. This involves collecting data on emerging threats, attacker behaviors, and vulnerabilities. |
Vulnerability Management and Patching: They identify and prioritize vulnerabilities in systems and applications. They then ensure timely patching or mitigation steps to address these weaknesses before attackers can exploit them. | |
Security Awareness Training: The SOC team (or a dedicated security awareness team) may also be responsible for educating employees on cybersecurity best practices. This can help minimize risks associated with human error, such as phishing attacks. | |
Real-Time Monitoring and Detection | Continuous Monitoring of Security Tools: SOC analysts constantly monitor many security tools, including firewalls, intrusion detection/prevention systems (IDS/IPS), and endpoint detection and response (EDR) systems. These tools generate alerts when suspicious activity is detected. |
Security Information and Event Management (SIEM): An SIEM system is a powerful tool that collects logs and events from various security tools across the network. The SOC team uses SIEM to aggregate, analyze, and correlate this data to identify potential security incidents. | |
Incident Response and Resolution | Identifying and Investigating Security Incidents: When a security incident is suspected (e.g., a triggered IDS alert), the SOC team investigates to determine its scope and impact. |
Containing and Eradicating Threats: The team takes steps to contain the threat, prevent further damage, and eradicate the attackers from the system. This may involve isolating infected systems, shutting down compromised accounts, or deploying antivirus/anti-malware tools. | |
Recovering Systems and Data: After containing the threat, the SOC team focuses on recovering affected systems and data. This may involve restoring backups or rebuilding compromised systems. | |
Developing and Maintaining a Well-Defined Incident Response Plan: The SOC team plays a key role in developing and maintaining a well-defined incident response plan (IRP) that outlines handling security incidents effectively. |
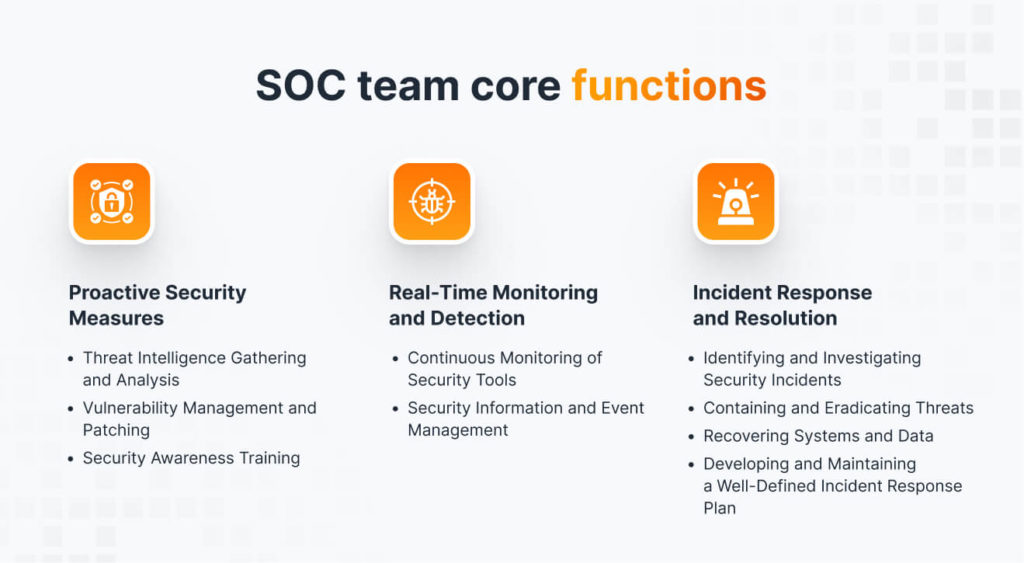
These core functions ensure that SOC teams play a vital role in safeguarding an organization’s data and maintaining business continuity in the face of ever-evolving cyber threats.
What does a SOC team do? A well-functioning SOC team acts as the organization’s cybersecurity backbone. By effectively executing their monitoring, analysis, detection, response, and remediation core functions, they protect critical systems and data from cyber threats around the clock. A strong SOC team is an investment in the organization’s overall resilience, ensuring business continuity and minimizing the impact of security incidents.
In the next chapter, we’ll examine the essential roles and responsibilities within a SOC team, providing a clearer picture of the expertise needed to keep your organization safe.
Key SOC team roles and responsibilities
Although the roles at any company may have different names, all organizations have similar responsibilities when it comes to cybersecurity. Here are the more common roles within a SOC team and the individual responsibilities that are associated with each role.
SOC Principal | |
| |
Security Engineer | SOC Manager |
|
|
Tier 3 analyst: Threat Hunter | Tier 2: Incident Responder |
|
|
Tier 1: Security Analyst | |
| |
The SOC team structure outlined here is based on the extensive experience of UnderDefense in managing successful SOC operations. While various resources may offer different team structures with a wider range of roles, we’ve found this core group to be essential for effective security operations. Ultimately, the optimal structure for your SOC team will depend on your organization’s specific needs and resources.

Building a strong SOC team goes beyond simply identifying roles inside the team. Each team member plays an important role in the overall cyber defense strategy built for a specific organization. Truly, a wise manager can ensure he has the right person in the right position to maximize output and ‘tune’ the team’s work correctly. That’s why processes established inside the team should make it work as one united machine.
Years of experience and much effort put into the SOC team have allowed UnderDefense to grow to a level 5 security center. The impressive maturity level of “Predictive Analytics” offers many advantages if you decide to look into our Managed SOC service. If you even already have your own team or decide to build one, we could take a second seat, augment your SOC, filtering through the noise and presenting only true, confirmed offenses
Our trained and award-winning team of experienced security professionals can provide the expertise and resources needed to keep your organization safe around the clock. Choosing UnderDefense for your SOC-as-a-Service means opting for a reliable, innovative, and client-focused SecOps partner dedicated to fortifying your digital defenses fast and effectively.

The next chapter will explore best practices for organizing your SOC team to maximize efficiency, collaboration, and overall effectiveness. We’ll also examine challenges like incident response procedures, certification requirements, and training drills to ensure your SOC team operates at its full potential.
Best practices of SOC team organization
A Cyber Security SOC team is a group of skilled cybersecurity professionals dedicated to actively monitoring an organization’s IT infrastructure and digital ecosystem. Their primary mission is to detect, analyze, and respond to security incidents in real-time, thereby minimizing the potential damage caused by cyberattacks.
1. Define Clear Roles and Responsibilities
This is the foundation of an effective SOC team. Each team member must understand their specific duties and how they contribute to the overall security objectives. This clarity enhances communication and streamlines incident response efforts.
- Tiered Analyst Approach: Implement a tiered analyst structure (Tier 1: Watchtowers, Tier 2: Deep Dives, Tier 3: Hunters) to optimize efficiency. Each tier focuses on specific tasks, allowing analysts to develop specialized skills.
- Clearly Defined Roles and Responsibilities: Clearly define theSOC team responsibilities and roles and for each member, including security analysts, engineers, threat intelligence analysts, security incident and operations managers, and (potentially) security awareness trainers. This avoids confusion and ensures everyone knows their part.
- Cross-training and Collaboration: Encourage cross-training among analysts to broaden their skill set and enable them to support each other during high-pressure situations. Foster a collaborative environment where information is shared openly.
2. Recruit and Retain Top Cybersecurity Talent
Hiring the right individuals with the appropriate skill sets is paramount for the SOC team’s success. Look for candidates possessing relevant certifications such as CISSP (Certified Information Systems Security Professional), CEH (Certified Ethical Hacker), and CompTIA Security+. Additionally, emphasizes the importance of fostering a supportive work environment to retain top talent and encourage continuous skill development.
- Standardized Incident Response Plan: Develop a well-defined and documented incident response plan (IRP) that outlines the steps for identifying, containing, eradicating, and recovering from security incidents. Regularly test and update the IRP to ensure its effectiveness.
- Clear Communication Protocols: Establish clear communication protocols for both internal and external communication. This includes communication within the SOC team, with other departments (IT, legal), and external stakeholders during an incident.
- Documentation and Knowledge Sharing: Maintain comprehensive documentation of SOC processes, procedures, and best practices. Encourage knowledge sharing within the team through regular meetings, training sessions, and internal knowledge bases.
3. Implement Advanced Security Tools
Equipping your SOC team with state-of-the-art security tools enhances their efficiency and efficacy. Sophisticated tools, such as SIEM (Security Information and Event Management), threat intelligence platforms, and automation tools (SOAR), play pivotal roles in monitoring, analyzing, and responding to security incidents.
Furthermore, consolidated platforms are the way forward for the SOC. With Logpoint Converged SIEM, SIEM fits seamlessly with SOAR, User and entity behavior analytics (UEBA), and more in one platform. Converged SIEM helps SOC teams combine data sets from multiple sources. Instead of using multiple standalone products, they now have one single source of truth. It’s the only unified platform that delivers SIEM+SOAR, UEBA, EDR capabilities and security monitoring of SAP systems for both enterprises and MSSPs.
The benefits of a converged platform include full data integration for automated TDIR, no integration or maintenance, out-of-the-box compliance support, and flexible deployment based on your needs.
- Security Information and Event Management (SIEM): Implement an SIEM system to centralize log collection and analysis from various security tools, enabling efficient monitoring and threat detection.
- Threat Intelligence Integration: Integrate threat intelligence feeds into your SOC workflows to provide analysts with real-time information about emerging threats and vulnerabilities.
- Automation and Orchestration: Leverage automation and orchestration tools to automate routine tasks and streamline incident response processes, freeing analyst time for more complex investigations.
4. Provide Continuous Training and Professional Development
Cyber threats evolve rapidly, and it’s essential to provide continuous training and professional development opportunities for your SOC team. Encourage team SOC Team members to attend workshops, conferences, and online courses to stay updated on the latest cybersecurity trends, threat vectors, and defensive strategies.
- Define and Track Key Performance Indicators (KPIs): Identify and track relevant KPIs like mean time to detect (MTTD) and mean time to respond (MTTR) to measure SOC team effectiveness.
- Regular Reporting and Analysis: Generate regular reports on security incidents, threats detected, and overall SOC performance. Analyze these reports to identify areas for improvement and adjust strategies as needed.
- Continuous Learning and Improvement: Foster a culture of continuous learning within the SOC team. Encourage ongoing training for all members to stay updated on the latest threats and defensive techniques.
5. Foster Collaboration and Communication
Effective communication and collaboration are pivotal for a well-functioning SOC team. Establish channels that facilitate seamless information sharing among team members and other departments. Regular meetings and cross-training initiatives enhance the team’s overall cohesiveness and ability to respond quickly to security incidents.
6. Practice Regular Drills and Simulations
Some companies feel these are invaluable for testing the SOC team’s capabilities, refining incident response procedures, and identifying areas for improvement. These exercises provide hands-on experience and help the team stay well-prepared for real-world cybersecurity challenges.

By implementing the best practices outlined in this chapter, organizations can establish a strong foundation for effective security operations. From clearly defined roles and skilled personnel to advanced security tools and a culture of continuous learning, each element is crucial in optimizing your SOC’s effective operability.
Conclusion
The significance of a robust SOC team cannot be overstated. By defining clear roles and responsibilities, recruiting top cybersecurity talents, and providing continuous training, you can shield your data against cyber threats. Also, to avoid challenges associated with building in-house SOC, you can always find a reliable vendor to augment your team most quickly and cost-effectively.
Managed SOC services by UnderDefense will give you the real benefits of a well-established SOC team level 5, whose expertise extends beyond incident response. It can reinforce your organization’s overall cybersecurity resilience and reputation. As cyber threats continue to evolve, investing in a skilled and proficient SOC team becomes irreplaceable to a cybersecurity strategy, protecting your digital assets.
Consulting with UnderDefense security experts can help you navigate the best way to benefit from SOC service. Contact us today to choose the best approach for your organization.