Today, artificial intelligence (AI) has turned into a driver for cybersecurity innovation. It helps detect, analyze, and respond to threats faster and more effectively. AI-driven solutions are deployed to protect organizations against increasingly sophisticated cyberattacks, also weaponized by malicious actors.
Gartner has found that about 68% of business executives think the advantages of using AI technologies outweigh the potential risks. And only 5% of responders pointed to the opposite. But as investments grow, the potential impact of data breaches may shift the perspective, especially after some unsuccessful cases that we will cover later.
This article will tell you how to prevent data leakage when employees use AI apps. We will give you a list of tools that will help achieve that. Additionally, we will discuss how to keep technological initiatives and innovations in the CIO or CISO position.
But let’s start with the actual numbers and cases to ensure we are on the same page.
The state of AI technologies in cybersecurity
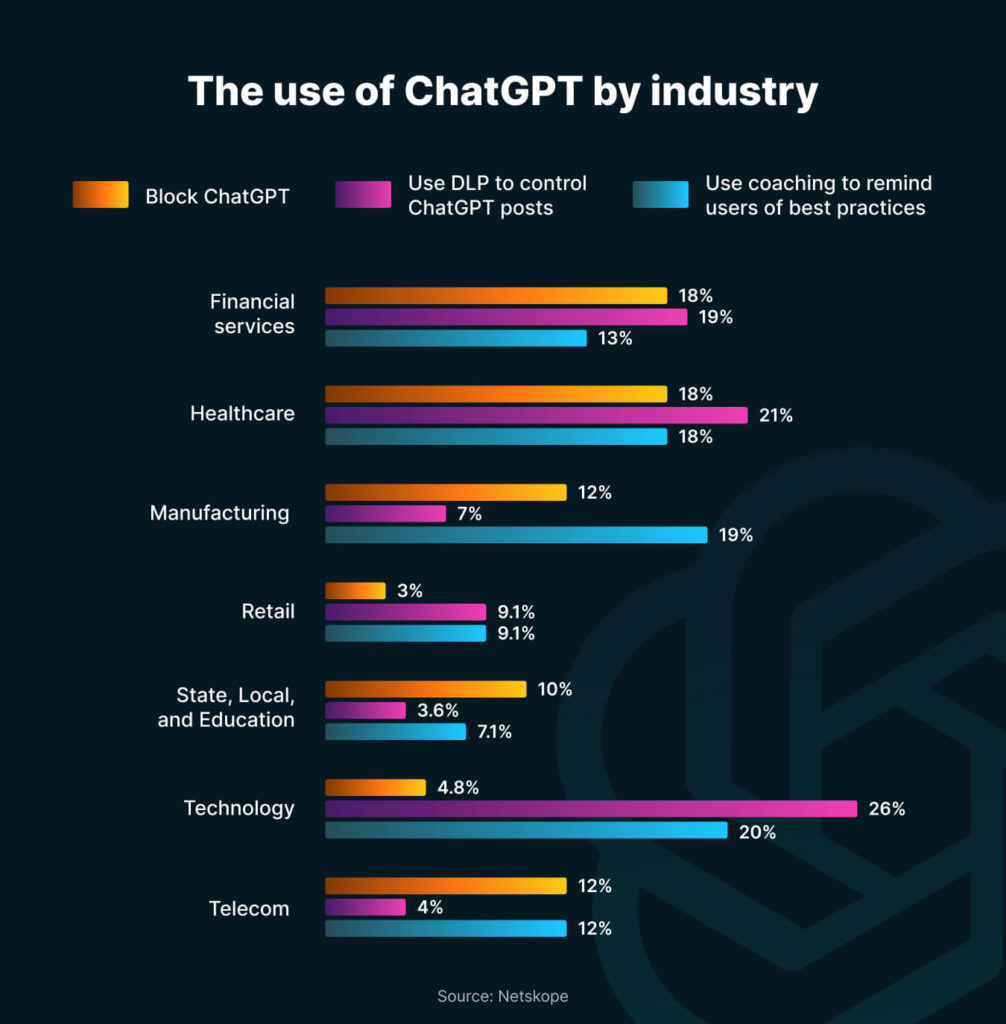
The number of AI users in the enterprise sector keeps growing. The cybersecurity company Netskope discovered that during Q2 2023, the percentage of enterprise users accessing AI apps increased by 22.5%. To what we want to point your attention is the following:
- Organizations with over 1,000 users accessed 3 AI apps daily.
- Organizations with over 10,000 users interacted with 5 AI apps daily.
- 1 out of 100 enterprise users access an AI app every day.
These numbers indicate that the adoption of AI apps among enterprises will continue to increase exponentially. Even if we consider ChatGPT only, the results are impressive, as every 10,000 users post 660 prompts daily to the chat. With that said, the question is: How can you protect your company against data exposure or regulatory risks?
Analyzing global experience, we can actually divide organizations into three categories. The first group restricts or fully blocks access to ChatGPT and similar solutions. The second introduces policies and educates employees about best practices. Meanwhile, the third implements data loss prevention (DLP) control.
One of the most shocking and exemplary cases of uncontrolled AI use happened to Microsoft in September 2023. Wiz researchers found that 38TB of data in Azure Storage at Microsoft was accidentally exposed. Employees’ passwords, internal Teams messages, workstation backups, private keys, and source codes were stored in a GitHub repository. It belonged to Microsoft’s AI research division and was shared via Azure Storage account to provide open-source code and AI models for image recognition. The discovery was made during a routine internet scan for misconfigured storage containers.
Next, we will see what steps you can take to prevent similar situations in your organizations.
How to prevent data leakage while using generative AI technologies
Adopting chatbot technologies at work may give many positive results, but at the same time, it presents significant security challenges. Your security team should know and weigh all factors before letting employees use generative AI applications. We’ve prepared top 5 recommendations that can empower your staff to effectively use AI-based apps, while mitigating data leakage risks for the whole organization:
1. Educate staff and establish data-handling policies
It’s necessary to conduct regular data security awareness training for all employees to educate them about data protection principles, business risks, and their responsibilities in handling sensitive data. Additionally, it’s a general practice to establish clear and comprehensive data handling policies in your company that outline acceptable practices, data protection procedures, and incident reporting guidelines.
Every new employee must also receive instructions about security measures and disciplinary procedures during onboarding. The complexity of all measures makes it possible to reinforce data protection practices in the corporate workflow.
2. Employ DLP solutions and anonymize sensitive data
A crucial part of preventing data leakage is implementing DLP solutions to identify, monitor, and protect data movement within the organization, checking for unauthorized access, disclosure, or alteration. Three main types of DLP are designed to monitor data at rest, in use, and in motion:
- Endpoint DLP
- Network DLP
- Cloud DLP
Email, cloud and web apps, storage, servers, databases, and other channels should be regularly checked to detect and prevent data breaches.
3. Conduct regular data sensitivity reviews
You need to regularly assess and classify the level of sensitivity of data assets to identify critical sections that require additional security measures. Before that, you must establish a clear data classification framework that defines levels and aligns with regulatory requirements in your industry. It’s easier to do with data classification tools that can automate and speed up this process, ensuring consistent and accurate categorization.
4. Monitor LLM use and restrict access to sensitive data
Next, you should monitor and control lightweight machine learning (LLM) apps usage in your organization. Ensure that such applications are utilized only for specific purposes and do not access sensitive data without permission. Another necessary measure is to restrict access to confidential information of employees and systems, limiting potential exposure. By implementing access control mechanisms, such as role-based access control (RBAC), you can enforce granular access permissions, prevent unauthorized access, and implement a verification process.
5. Use secure environments and continuous monitoring
You can protect digital assets from external and internal threats by enforcing appropriate security measures for your organization, such as firewalls, IDS, and access control lists. Among additional recommendations are:
- Encrypting sensitive data at rest and in transit to safeguard it from unauthorized access or breaches.
- Conducting continuous monitoring of data systems and network traffic to promptly identify and respond to suspicious activities and potential data leakage.
- Utilizing SIEM solutions to aggregate and analyze data, enabling proactive detection and response to security incidents.

Armed with these data security principles, you should be confident that employees are not exposing sensitive data or corporate IP while using generative AI apps.
Best SASE tools to control employees’ requests for AI applications
Organizations need to not only control how employees use generative AI tools. They should also implement appropriate policies and technologies to create an additional security layer. Chatbots can be used for many tasks, for example content creation. However, in such cases you should be ready for certain risks including sharing confidential information, violating privacy, failing quality control, unauthorized use of intellectual property, misrepresentation of data, etc.
Is there a way to prevent and deal with that? A framework that merges network solutions of on-prem protection with security services and enables a comprehensive cloud-based security approach is called secure access service edge (SASE). It provides secure access to applications and data within the company’s network based on specific access policies.
Depending on various features and configurations, you can choose one of the following SASE tools:
- Zscaler uses generative AI and can predict possible breaches. Also, it offers an option to create policies for better threat detection, prevention, and response. Zscaler’s expertise lies in zero-trust connectivity and securing all cloud data channels.
The DLP platform controls data through all channels, devices, and users, allowing organizations to retain content as prompts from publicly available AI and LLM applications, queries, and outputs. Such content gets recorded and monitored in its environment to prevent potential data leakage. - Cloudflare Access provides secured access for employees to all on-premise, SaaS, and non-web apps. The main feature of this product is to prevent lateral movement, which means providing the least privileged access to resources and reducing the attack surface. Firstly, Cloudflare should protect the most critical apps and high-risk users and enforce security measures for all available data.
It replaces VPN as a faster and safer solution, especially in taking the load off critical apps. Also, there is a function to integrate robust authentication methods, like security keys and limited-level access options for different user types. - Cato SASE Cloud offers a comprehensive cloud-based management solution that lets users control the service. It provides granular network and security policy configurations and detailed analytics for network traffic and security events. Additionally, Cato allows decrypting and inspecting all traffic in the enterprise, along with managing security policies.
It provides users zero-trust network access (ZTNA) to the cloud and on-prem apps through all devices. Users should install the app and enable multi-factor authentication (like FIDO2). Only authorized users will have access based on their identity, access policy, and context. At the same time, all traffic is being inspected by the security stack to eliminate possible malware from compromised endpoints. - Cisco Duo is made to protect data at your organization from access by any device or location, enforcing multi-factor authentication (MFA). It offers MFA, which helps to prevent phishing, malware, and ransomware attacks. The authentication process is streamlined for employees using a mobile app to verify their identity. Duo operates as a VPN replacement for remote access and provides ZTNA principles.
The next feature of this access management tool is the ability to customize the permissions. You can control what kind of data, when, and what users can access based on employees’ roles, devices, and locations. Also, every device connecting through Duo can be verified for trustworthiness and checked for health status. - Quantum SASE combines on-device and cloud-based capabilities to ensure employee hybrid and remote access protection. Its key features include zero-trust access, software-defined wide area network (SD-WAN), connectivity with ThreatCloud AI, and cloud-native infrastructure. Among its benefits are fast deployment, simplified management, scalability, and reduced costs.
- Google IAP provides secure access to Google Cloud applications and virtual machines (VM) based on identity and context. It implements ZTA, enforces granular access-control policies, excludes VPN for remote employees, and protects VMs hosted on Google Cloud. The main advantages of this solution are reduced attack surface, enhanced security, scalable architecture, cost-effectiveness, and centralized access control.
- Forcepoint ONE delivers the critical enforcement point to stop the theft of data in motion through email or web channels. The solution provides real-time visibility and control over network traffic so you can detect, respond to, and remediate threats faster. Another essential feature is accelerated compliance: a pre-packaged coverage of global regulations with central control across your IT environment.
- Jamf Connect offers simplified device management and security for Apple products. Among its features are:
- Fortinet Universal ZTNA is a complex of tools, techniques, and policies that ensures ZTNA principles regardless of the employee’s location or network. You can apply these principles without affecting connection for users, so they can keep working from anywhere. Fortinet solution reduces the attack surface, provides consistent and simple onboarding about data security policies for new employees, allows integration with an SD-WAN, improves compliance, and reduces costs.
- Microsoft Purview Data Loss Prevention (Microsoft 365 E5 Compliance Suite) allows you to detect and control sensitive information across Microsoft products and on the endpoints. Also, it enables optimized data protection automatically through context-aware detection, dynamic controls, and automated mitigation. Comprehensive insider risk management (IRM) can detect risky users and assign levels. PDLP can also trigger DLP solutions that can dynamically apply preventative controls.Among its benefits are no configuration required for cloud workloads, an activated system of receiving and tracking unified alerts through DLP, integration with information protection classification (IPC) and labeling feature, and the option to create and enforce security policies.
- Prisma SASE by Palo Alto Networks protects various cloud environments. It is also positioned as a complete solution because it covers network security, SD-WAN, autonomous digital experience management (ADEM), Enterprise DLP, and SaaS security. Prisma is suitable for organizations of all sizes with a remote workforce and uses cloud-based applications.One of the primal add-ons to the platform is the security posture policy engine (SPPE). It resolves critical misconfigurations and detects compromised accounts and malicious activity.

Implementing one of these powerful tools to control employees’ interaction with LLMs will help your organization mitigate the risks associated with AI apps. You can ensure these technologies are used responsibly with clear guidelines, training, monitoring, and access control.
How CIOs and CISOs can lead AI initiatives and innovate securely
About 90% of CISOs dealt with at least one disruptive attack on their company in 2022. The CIO and CISO’s decisions concerning security policies may have devastating effects on business. As a result of such pressure, the question of whether to use generative AI apps or not is distressing. Having effective SASE tools and ensuring that AI tools are being used responsibly and according to existing security policies can outweigh the doubts.

Here are the main steps you, as CIO or CISO, should consider to secure your organization and chatbot apps:
1. Understand AI exposure and data governance
The most important task is to conduct thorough security assessments and identify and quantify AI exposure across the organization’s systems, applications, and data sources. Then, you can implement data governance practices to establish clear policies and procedures for data collection, storage, usage, and access. Another thing is to ensure data privacy compliance with relevant regulations and standards in your industry.
2. Secure the entire AI pipeline
It’s necessary to employ security measures throughout the AI pipeline, from data input and output to machine learning models, data flows, and continuous monitoring. Without data access control, it’s impossible to restrict unauthorized access to sensitive information in AI applications. Also, you can encrypt data to protect it from unauthorized disclosure and access by employees. Machine learning tools can identify and prevent potential security risks in your organization’s various AI applications or tools.
3. Invest in tools to secure AI
You need to assess and evaluate SASE solutions available in the market, considering their capabilities, features, and integrations with your existing security infrastructure. It’s better to prioritize tools to monitor and detect AI vulnerabilities, ensure data integrity, and prevent unauthorized access. Also, you need to consider tools that can automate routine security tasks, such as vulnerability scans, compliance checks, and alert systems.
4. Safe operations and maintenance with 24/7 monitoring
Continuous monitoring of AI applications and systems that can detect and respond to potential security threats in real-time is essential. The essential element of security architecture is a security operations center. Your company can build a 24/7 security operations center in-house or buy a SOC-as-a-service from a reputed vendor to monitor AI infrastructure and respond to incidents.
5. Secure design and development
You need to embed security measures into the entire development process, starting from design and development to deployment and management, to establish a robust security foundation for applications made by your organization.

Following these five steps, you can bring innovation into your company’s workflow and boost business value while effectively mitigating security risks related to generative AI apps.
Being prudent makes all the difference
Final thoughts
The fast-paced adoption of AI tools comes with valid concerns about loss, leakage, or misuse of sensitive data. Building a security strategy and choosing suitable SASE tools to control employees’ use of LLM apps to mitigate the risks is a must. Exploring technological innovations amid cybersecurity risks may look challenging, but embracing main recommendations can prevent the negative consequences and strengthen your organization’s defense.
If you are seeking an experienced partner in cybersecurity with whom you can consult about SASE tools, UnderDefense is the right candidate. Our experts will guide you through each solution’s pros and cons to find the most suitable solution for your company. Contact us today to protect your business tomorrow.
Disclaimer: The text of the article is based on the security webinar presented by Nazar Tymoshyk, CEO at UnderDefense, and Marijn Markus, Data Scientist at Capgemini.
















