If you have decided that penetration test (an authorized simulated attack on a computer system, performed to evaluate the security of the system) is what your business needs, next step will be to choose its type.
We will guide you through this process to find out which pen test works best for you.
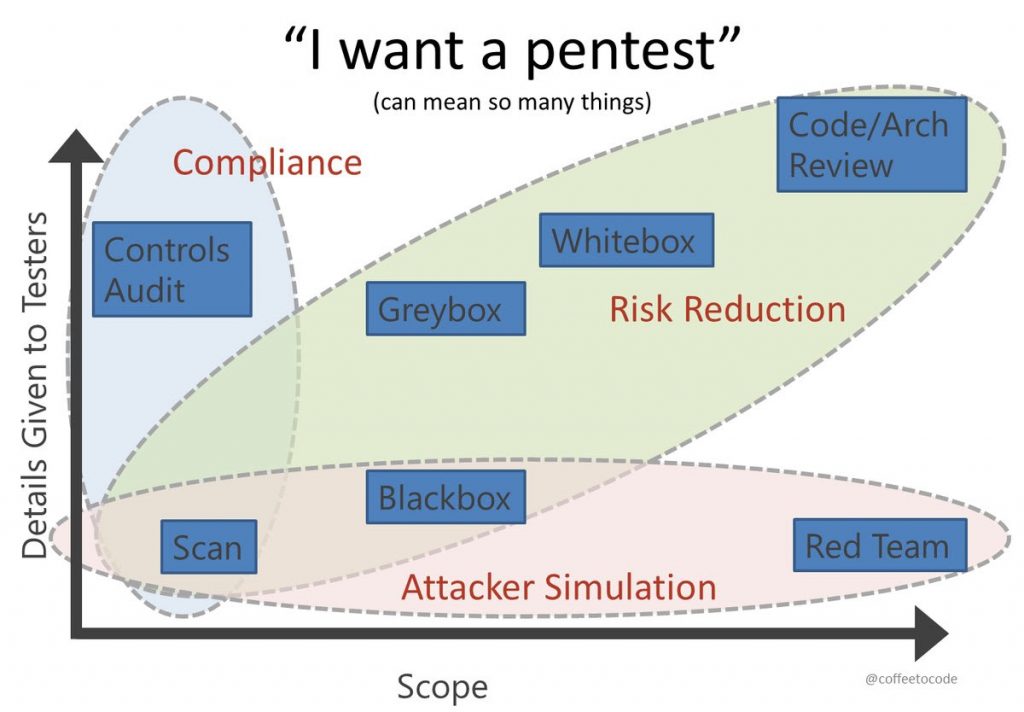
At first, you should understand the scope of work, namely how deeply our engineers should look for holes or test your environment for perversion. They can simulate the attacker behavior or scan your code for vulnerabilities. Depending on the size there can be a red team of 1-2 or up to 5 individuals examining your business.
Another factor that you should pay attention to is the details given to pentesters.
- White box testing – is pen testing, when you give the full assess to your product/architecture with all passwords and our engineers try to hack your company from the inside.
- Grey box testing – is when you partially have the assess to the system, with a few admin privileges.
- Black box testing – is when you break the system without inside information given. You start going deeper with small steps getting more and more access gradually. This kind of test is the most difficult to conduct technically that is why the longest period of time is needed to do it.
All of our clients receive a special report with recommendations to implement from UnderDefense pentesting company. We advise the best solutions in our opinion and give tips on what you can do more to protect your business in a better way. This all is for free and whether to follow or not our security directions is completely your choice.
If you are still confused what pentest you need, we are always ready to help you get more information and advice the service that will suit you best!
















