In 2011 Benjamin Delpy released his side project that most recently became a key component of some ransomware worms that spread across Europe. Mimikatz became a ubiquitous tool in all manner of hacker penetrations, allowing intruders to quickly leapfrog from one connected machine on a network to the next as soon as they gain an initial foothold.
As we see, mimikatz is a popular and powerful tool but what it can do?
[Explore an Educational Hub with answers to the trickiest questions. Subscribe to UnderDefense YT channel and receive a resource with practical knowledge sharing]
What you need to know
Mimikatz is a console tool that has lots of modules. The full list of modules you can see here. I am going to highlight only the main three :
- Privilege – This module provides some commands to manipulate privilege on mimikatz process.
- Sekurlsa – This module extracts passwords, keys, pin codes, tickets from the memory of lsass. Also, this module can perform the well-known operation ‘Pass-The-Hash’ to run a process under other credentials with NTLM hash of the user’s password, instead of its real password.
Kerberos – This module can be used without any privilege. It permits to play with official Microsoft Kerberos API – and to create offline ‘Golden tickets’, free, long duration TGT tickets for any users.
Why do you need to be scared?
In a nutshell, with mimikatz adversary or any malware, you can get some credential and spread across domain in your network. The most famous cases are massive ransomware attacks known as BadRabbit and NotPetya that have infected thousands of networks causing millions of dollars damage. These worms get credentials by using modified mimikatz and are spread via Microsoft`s Server Message Block (SMB) protocol.
It can make an impression that mimikatz is some kind of virus or something like that but mimikatz doesn’t hack anything, it just uses Windows features, so there is no hope that with updates it is going to be fixed.
Hunter’s notes
As you can see, there are lots of reasons to detect mimikatz. The main question here is “How to do this?”. At the beginning of my way I tried to find some guides, articles, tutorials, etc. that would explain to me how to detect it. Most of them recommended only to monitor the access to lsass.exe with access mask 0x1010 and it’s very easy with Sysmon (EventID 10). But this way, we only see a usage of sekurlsa module.
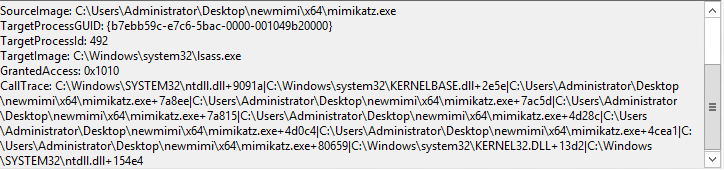
With this option, I couldn’t see the start process and usage of any other module. This made me sad, that is why I decided to try harder to detect any command of any module. I made my own target configuration of sysmon for mimikatz and started running all commands.
After all the tests I have noticed that each command has a unique call trace that allowed me to detect any single command. Following this way, I got call traces for 34 commands from 8 modules. Then I could exactly detect which command had been run. But this dream couldn’t become true: this technique has some problems.
First of all, each version of mimikatz has other call traces for commands and it means that I need to have lists of call traces for all mimikatz versions. It’s hard but it’s real. But the second problem killed last hope – nobody uses the legacy version from GitHub. More often advisories use PowerShell ( such Invoke-Mimikatz) or modified (such in BadRabbit or NotPetya) versions. So, it was interesting and funny experience, but it doesn’t work in real life.
Next step was to test PowerShell versions of mimikatz and ransomware with this one to find common signs of mimikatz usage. After all of this, I could make some conclusions.
Some technical information
For this research, I have used Sysmon+Splunk. I tested mimikatz 2.1.1. Kitten Edition, PowerShell mimikatz versions(Invoke-Mimikatz and Invoke-Mimidogz) and mimikatz in ransomware(BadRabbit and NotPetya). All tests were made on Windows 7, Windows Server 12, Windows 10 and Windows Server 16 with latest updates.
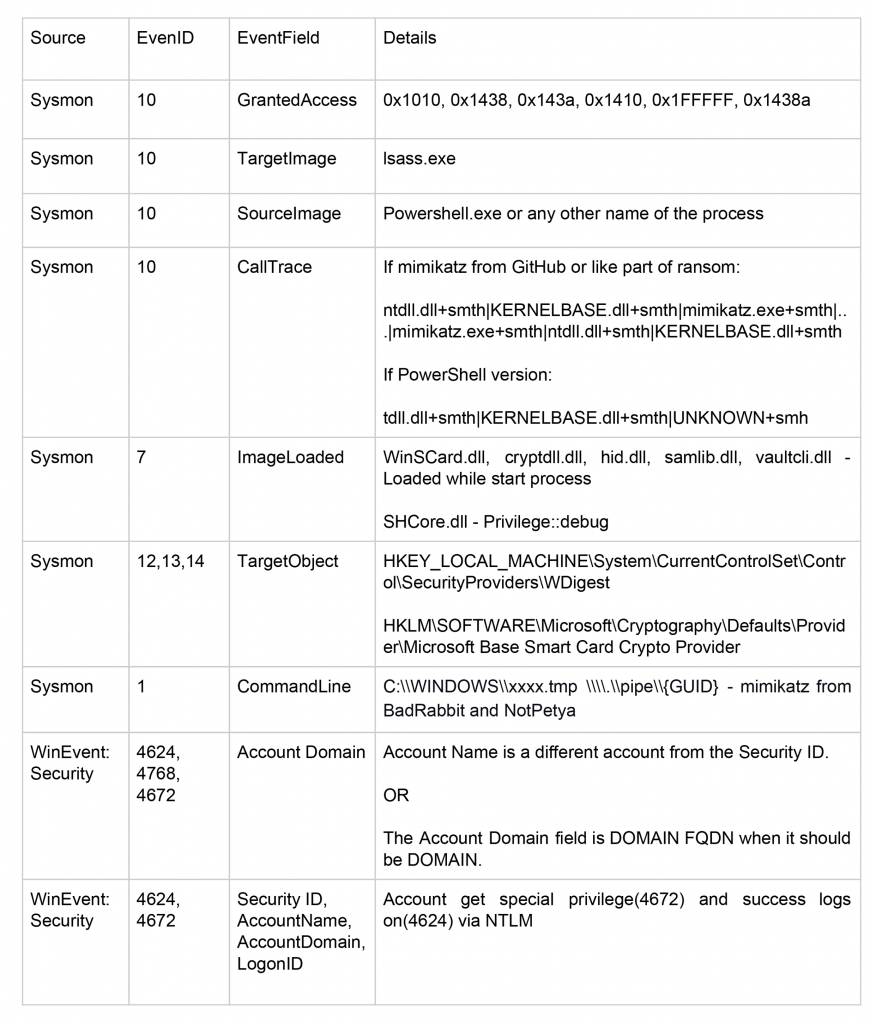
Possible sources and examples of suspicious logs:
How to feel secure
First of all stick to the principle of the least privilege. This means that Active Directory administrators have only the minimum required permissions to perform their tasks. Administrator by default can get debug privilege, but usually, he doesn’t need it. You just need to create a new group that has debug privilege and takes it away from administrators group. This way mimikatz wouldn’t get debug privilege and do something with lsass.exe during the tests. So, the administrators’ groups can do their work as they did before and mimikatz can’t get privileges it requires.
The second recommendation – if you don’t use any special password filters, smart-cards or special protocols you need to change the value RunAsPPL of HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Control\\Lsa on 1. After this Lsass.exe will work in secure mode and any process without Microsoft certificate will not have access rights to LSA process.
And the last one, to protect against attacks related to Kerberos you should use Flexible Authentication Secure Tunneling (FAST) that is part of the framework for Kerberos Pre-authentication. FAST provides a protected channel between the client and the Key Distribution Center (KDC), and it can optionally deliver key material used to strengthen the reply key within the protected channel. With FAST in place, it is relatively straightforward to chain multiple authentication mechanisms, utilize a different key management system, or support a new key agreement algorithm.
With FAST enabled and required, brute forcing the reply key is no longer possible and the highest possible cryptographic protocols and cipher strengths are guaranteed to be used by Windows clients in their pre-authentication traffic with Windows Server Domain Controllers.
[Let’s get in touch if you want to learn more about UnderDefense trainings and services, and receive updates with educational content]
Summary
In this article, we explain mimikatz as a dangerous tool hackers use to steal the credentials and get into your system. Also, it may be used as a part of the virus code that will, later on, be spread all over the environment. Recently Mimikatz has become a very popular means of penetration to hack the infrastructure and take your money and sensitive data. It allows the intruders to quickly leapfrog from one connected machine on a network to the next once they receive an opening foothold. Our security engineers have prepared some pieces of advice on how to hunt the mimikatz using Sysmon and some SIEM, especially Splunk. They will help you prevent new attacks in the future. So, now you can feel secure because you are under defense.
















