In today’s rapidly evolving digital landscape, cyber threats loom large and data breaches make headlines almost daily, and there is no end to cyber risk. Most businesses are facing a critical need to protect their sensitive information and digital assets. Traditional security measures often prove inadequate in the face of sophisticated attacks, prompting organizations to seek more robust solutions.
Security-as-a-Service has emerged as a game changer that empowers businesses to fortify their defenses by outsourcing their security needs to specialized vendors. SECaaS vendors have revolutionized the way organizations safeguard their invaluable data, intellectual property, and customer information, offering an array of scalable and cost-effective security solutions.
In this article, we will introduce the top four Security-as-a-Service providers who have established an outstanding reputation through their extensive range of services, innovative technologies, and unmatched knowledge and skills.
We have the answers
Who are Security-as-a-Service Providers?
Security-as-a-Service (SECaaS) providers are companies that offer various security services and cost-effective, scalable, and customized solutions to organizations on a subscription basis adapting to their evolving needs.
SECaaS providers deliver security-related functions and technologies through the cloud. By leveraging the expertise and infrastructure of SECaaS providers, organizations can access advanced security technologies, and offload the responsibility of managing security systems and operations. It allows businesses to focus on their core activities while ensuring the security and protection of their digital assets.
To meet different needs and requirements, SECaaS vendors offer a range of security services:
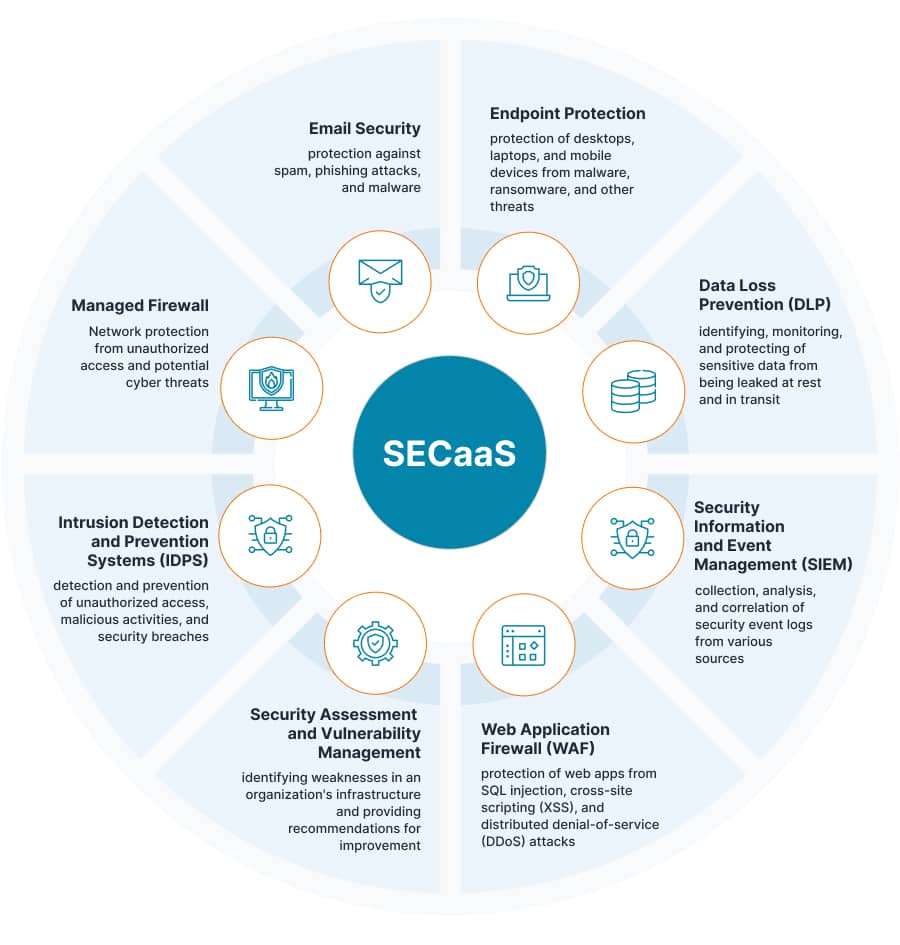
Why Security-as-a-Service is Important
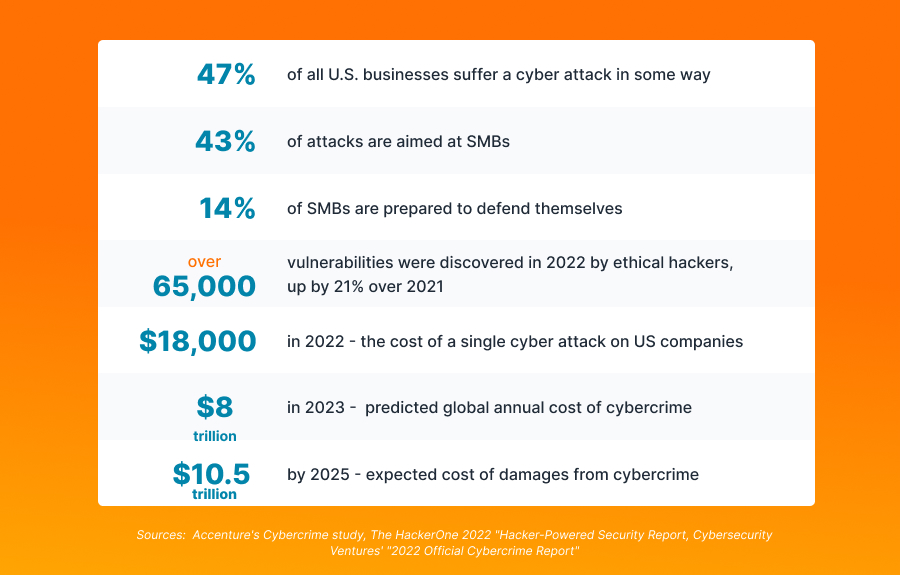
As the infographic shows, the statistics are not very encouraging, and there is a tendency for an increase in the number of cyber attacks. That is why Security-as-a-Service (SECaaS) plays a vital role in today’s digital landscape. And here are the key reasons:
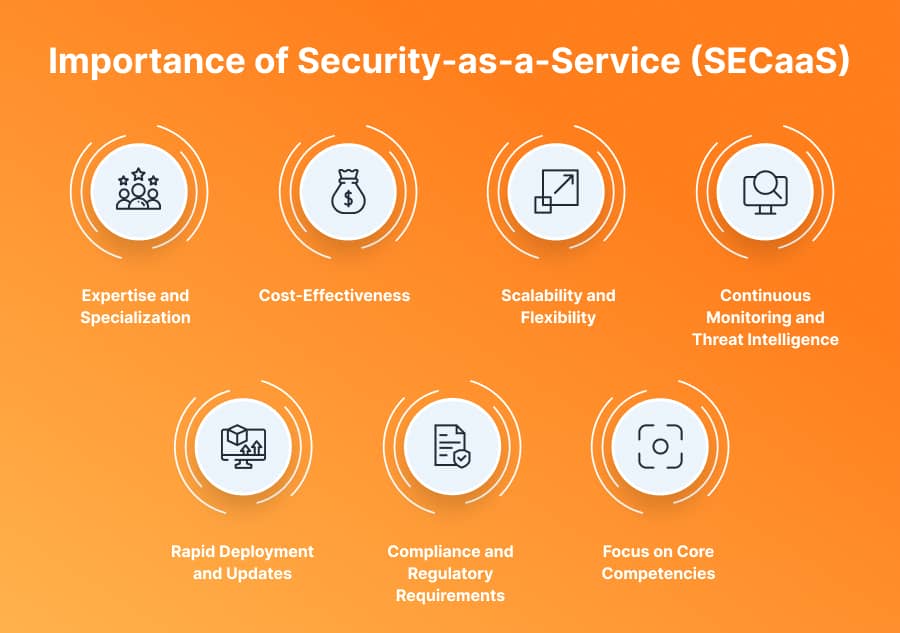
- Expertise and Specialization: SECaaS providers have specialized expertise in the field and are dedicated to providing security services and solutions. They stay updated with the latest security threats, trends, and technologies. It allows them to offer robust and effective security measures. Organizations can benefit from their advanced security capabilities without building and maintaining an in-house security team.
- Cost-Effectiveness: Implementing and managing comprehensive security measures in-house can be expensive. It requires investments in hardware, software, infrastructure, and skilled personnel. SECaaS eliminates the need for upfront capital expenditures and allows organizations to pay for security services on a subscription basis. This cost-effective model reduces the financial burden and provides access to enterprise-grade security technologies.
- Scalability and Flexibility: As organizations grow and their security requirements evolve, SECaaS vendors can easily adjust the level of security services based on the organization’s needs. SECaaS providers can accommodate these changes quickly and efficiently, whether it’s adding new users, or expanding security controls to different locations.
- Continuous Monitoring and Threat Intelligence: Security threats constantly evolve, and organizations need continuous monitoring and real-time threat intelligence to stay protected. SECaaS vendors offer 24/7 monitoring and analysis of security events, promptly identifying and responding to potential threats. They leverage threat intelligence sources, vulnerability databases, and security analytics to provide proactive security measures and timely incident response.
- Rapid Deployment and Updates: With SECaaS, security solutions can be deployed rapidly, as they are delivered through the cloud. It eliminates the need for lengthy implementation processes and allows organizations to improve their security posture quickly. Furthermore, the service provider handles updates and patches, ensuring the security infrastructure remains up-to-date and protected against emerging threats.
- Compliance and Regulatory Requirements: SECaaS vendors have experience meeting specific compliance and regulatory requirements related to data security and privacy. They offer data encryption, access controls, audit trails, and logging to meet regulatory standards and facilitate compliance audits.
- Focus on Core Competencies: By relying on the expertise of SECaaS providers, organizations can concentrate on their core competencies and strategic objectives that directly contribute to their business growth.
The Major Cybersecurity Risks SECaaS Providers Can Help You Avoid
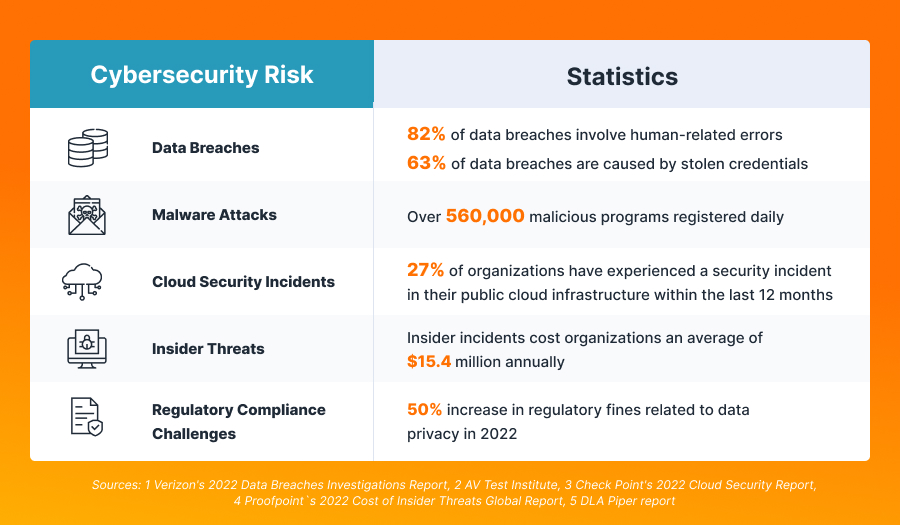
By partnering with SECaaS providers, the companies can benefit from their expertise, specialized security solutions, and proactive approach to mitigating cybersecurity risks. SECaaS vendors can help organizations stay ahead of emerging threats, enhance their security posture, and effectively protect their digital assets and sensitive information.
SECaaS providers can assist organizations in mitigating various cybersecurity risks:
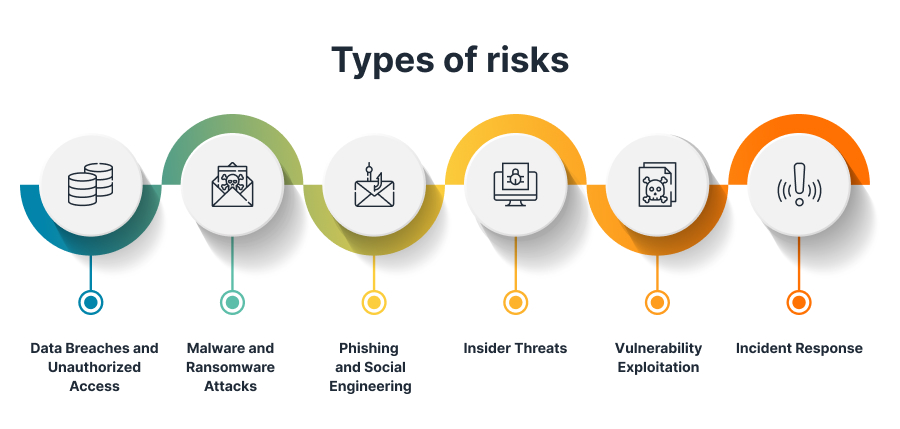
- Data Breaches and Unauthorized Access: SECaaS providers implement robust security measures such as firewalls, intrusion detection/prevention systems, and access controls to protect against unauthorized access to sensitive data.
- Malware and Ransomware Attacks: SECaaS providers offer advanced threat detection and prevention solutions, including secure email gateways, web application firewalls, and endpoint protection. These solutions help identify and block malicious software, viruses, ransomware, and other malware-based attacks that could compromise organizational systems and data.
- Phishing and Social Engineering: SECaaS vendors deploy email security solutions with anti-phishing measures, spam filters, and email authentication protocols. They reduce the risk of phishing attacks and other social engineering tactics that trick users into sharing sensitive information or performing unauthorized actions.
- Insider Threats: SECaaS providers often implement security controls and monitoring mechanisms to detect and prevent insider threats. It includes user behavior analytics, data loss prevention (DLP) systems, and access controls to minimize the risk of unauthorized data access or malicious activities by insiders.
- Vulnerability Exploitation: SECaaS providers conduct regular vulnerability assessments and penetration testing to identify weaknesses of an organization’s infrastructure. By proactively identifying vulnerabilities, organizations can remediate them before malicious actors exploit them. SECaaS providers may also offer vulnerability management services to assist in prioritizing and managing remediation efforts effectively.
- Incident Response: In the event of a security incident or breach, SECaaS vendors can provide timely incident response services. It includes incident detection, containment, analysis, and recovery, minimizing the impact of security breaches and facilitating the organization’s return to normal operations.
How to Choose Security-as-a-Service Provider
When selecting a Security-as-a-Service (SECaaS) provider, it’s essential to consider several factors and conduct a thorough investigation to ensure they meet your organization’s specific needs, requirements, budget, and long-term goals.
Here are main considerations for choosing a SECaaS provider:
- Expertise and Reputation: Evaluate the provider’s expertise and reputation in cybersecurity. Look for an established vendor with a proven track record of delivering high-quality security services. Research their certifications, partnerships, and customer reviews.
- Range of Services: Assess the security services the provider offers. Consider the specific security needs of your organization and ensure that the provider offers comprehensive solutions to address those requirements. Look for services such as firewall management, intrusion detection/prevention, secure email gateway, web application firewall, SIEM, DLP, and endpoint protection.
- Scalability and Flexibility: Consider the provider’s ability to scale their services as your organization grows or undergoes changes. Ensure they can accommodate increases in bandwidth, users, and geographical locations. Flexibility is crucial, as it allows you to adapt the level of security services based on your evolving needs.
- Technology and Infrastructure: Evaluate the provider’s technology stack and infrastructure. Ensure they leverage advanced security technologies, such as threat intelligence feeds, machine learning, and behavioral analytics, to effectively detect and mitigate emerging threats. Additionally, consider their data centers, network architecture, redundancy measures, and disaster recovery capabilities to ensure the security and availability of your data.
- Compliance and Regulations: If your organization operates within a specific industry or geographical region with regulatory requirements, verify that the SECaaS provider has experience in meeting those compliance standards. Inquire about their adherence to frameworks such as GDPR, HIPAA, PCI DSS, or other relevant regulations and assess their ability to provide necessary compliance features.
- Service Level Agreements (SLAs): Review the provider’s SLAs to understand the level of service they guarantee, including response times, uptime, and incident management. Ensure the SLAs align with your organization’s requirements and expectations.
- Incident Response: Evaluate the provider’s incident response capabilities. Inquire about their incident detection and response processes, including their incident response team’s expertise and availability. Assess their communication protocols, escalation procedures, and post-incident reporting.
- Customer Support and Service: Consider the level of customer support and service provided by the SECaaS provider. Determine their responsiveness, availability, and support channels. Ensure they offer ongoing support, including assistance with configuration, troubleshooting, and security advisory services.
- Cost and Contract Terms: Evaluate the provider’s pricing model, compare pricing with other vendors, and ensure it aligns with your budget. Review contract terms, including termination clauses, data ownership, and data handling policies.
- References and Recommendations: Seek references and recommendations from trusted sources, such as industry peers or security consultants. Get insights into their experience working with the SECaaS provider and the quality of their services.
Four prominent Security-as-a-Service (SECaaS) providers
The following providers offer specialized security services and solutions to address different aspects of cybersecurity. However, it is advisable to conduct your own research, evaluate their offerings, and consider your organization’s specific needs before making a decision.
UnderDefense
UnderDefense specializes in cybersecurity for businesses of all sizes, offering a full stack of cybersecurity services tailored to the specific needs of each organization. We provide 24/7 monitoring and advanced analytics to detect and respond to security threats effectively.
UnderDefense offers a comprehensive UnderDefense MAXI SECaaS platform that includes managed security services, threat intelligence, incident response, and vulnerability management. The platform guides organizations of any expertise level in addressing their security challenges. We provide a comprehensive view of the organization’s security posture and offer solutions to improve and enhance it. Our focus is on problem-solving rather than selling technologies.
The key advantages:
- Free assessment of risks, vulnerabilities, and data leakage for the organization, including how other organizations, partners, clients, and hackers in the Darknet environment see them
- Calculation of financial losses per incident, with valuable insights for businesses to improve ROI
- Free templates aligned with CIS, ISO 27001, and SOC2 requirements, enabling organizations to understand how to achieve compliance
- Providing an agent for deploying infrastructure protection solutions such as asset management and endpoint detection and response (EDR)
- Free integration with Attack Surface Management, which monitors data leakage and helps organizations understand the necessary controls for mitigating future incidents
- A holistic platform that seamlessly integrates with CX’s SOC/MDR solutions and services
- Managed Detection and Response (MDR) and SOC as part of Security-as-a-Service (SECaaS) offerings
- Flexible pricing models, allowing organizations to align the solution with their specific requirements and budget.
By combining these features and services, our platform stands out among the top SECaaS providers, offering organizations a holistic approach to security, irrespective of their expertise level.
Astra
Astra is a SECaaS provider offering lots of advantages that set them apart in the market. These advantages make Astra a compelling choice for organizations seeking specialized web application security and comprehensive SECaaS solutions. They offer a cloud-based web application firewall (WAF) that helps protect websites and applications from common vulnerabilities, such as SQL injection, cross-site scripting (XSS), and OWASP Top 10 threats. Astra’s solution also includes automated malware scanning, vulnerability assessment, and distributed denial-of-service (DDoS) protection.
The key advantages:
- Security features beyond the traditional WAF (automated malware scanning, vulnerability assessment, and Distributed Denial-of-Service (DDoS) protection)
- The SECaaS platform which is easy to deploy, configure, and manage, even for organizations with limited technical expertise
- Use of automation and machine learning to enhance security capabilities to reduce manual effort and increase the speed and accuracy of security incident identification and mitigation
- 24/7 monitoring and support to ensure ongoing protection
- Ability to accommodate changes in web traffic, application complexity, and business growth without compromising on security effectiveness
- Support of various compliance frameworks, reporting, and auditing capabilities to help organizations demonstrate compliance with industry regulations and standards
Expel
Expel provides a managed detection and response (MDR) platform that combines security expertise with advanced technology. Their SECaaS offering includes real-time threat detection, proactive hunting for malicious activities, incident response, and 24/7 monitoring. Expel’s platform integrates with existing security tools and provides transparent visibility into an organization’s security posture. These advantages position Expel as a strong SECaaS provider, offering organizations the expertise, tools, and support needed.
The key advantages:
- Managed Detection and Response (MDR) and 24/7 monitoring and support services
- Proactive threat hunting that identifies and addresses potential security issues before they escalate
- Security platform that integrates with existing security tools and technologies within an organization’s infrastructure
- Clear and accessible communication channels, ensuring organizations understand their security posture, ongoing incidents, and recommended actions
- Incident Response Capabilities that minimize the impact of security incidents and reduce the detection and response time
- Actionable insights and comprehensive reporting on security incidents with clear metrics and visualizations
Vanta
Vanta focuses on providing SECaaS solutions for startups and small to medium-sized businesses (SMBs). Overall, Vanta’s main advantages lie in their expertise in compliance management, comprehensive security assessments, automated risk mitigation, attack surface management, integration capabilities, and scalability.
The key benefits:
- Streamlined compliance management enables organizations to demonstrate their adherence to industry standards more efficiently
- Comprehensive security assessments that identify risks, vulnerabilities, and data leakage within an organization
- Agent-based deployment of infrastructure protection solutions, such as asset management and endpoint detection and response (EDR)
- Free integration with Attack Surface Management, which continuously monitors data leakage for organizations
- Integration with CX’s SOC (Security Operations Center) and MDR (Managed Detection and Response) solutions and services
Being prudent makes all the difference
Conclusion
The emergence of Security-as-a-Service (SECaaS) providers has revolutionized the way organizations protect themselves against potential breaches, vulnerabilities, and data loss. Choosing the right Security-as-a-Service (SECaaS) provider is essential for safeguarding your business against ever-evolving cyber threats.
We have explored the top 4 SECaaS providers and their best-in-class solutions. Each provider brings unique strengths, advanced technologies, and comprehensive services to protect businesses of all sizes. By outsourcing security needs to these industry leaders, organizations can focus on their core competencies while leveraging specialized tools and expertise.
Make an informed decision to fortify your business with the best SECaaS solution and ensure a secure future. If you want to safeguard your business from cybersecurity risks, the UnderDefense MAXI Platform is here to help. With its comprehensive range of SECaaS solutions tailored to your specific needs, the MAXI Platform offers a holistic approach to enhancing your organization’s security posture.
Additionally, for advanced threat detection and response capabilities, consider exploring our Managed Detection and Response (MDR) services. They are designed to proactively identify and mitigate threats, providing an extra layer of security for your digital assets.
Reach out now to get a quote and take the first step toward enhancing your organization’s security posture and explore our comprehensive range of SECaaS solutions tailored to your specific needs.
Your digital assets deserve the best protection, and we are committed to providing it.
Don’t wait, contact us today.

















