The ISO 27001 standard is a globally recognized set of principles emphasizing information security and offering a framework for the Information Security Management System (ISMS).
Get certified quickly and continue growing together with UnderDefense
Business executives utilize our ISO 27001 checklist to evaluate their organization’s preparedness for ISO 27001 certification. With it, you can identify process gaps, assess the existing ISMS, and implement the necessary measures. It also serves as a reference to evaluate various categories aligned with the ISO 27001:2013 standard.
We’ve already covered an ISO 27001 internal audit checklist and shared free ISO 27001 templates for you to get audit-ready faster. So, in this article, we’re going to answer the main questions you might have about the ISO 27001 checklist and go through the steps involved.
Table of Contents
- How long does ISO 27001 certification take?
- ISO 27001 Checklist
- Drawbacks of independent preparation for certification
- Advantages of preparing for certification with an information security consultant
- Download UnderDefense ISO 27001 templates for free
- Become ISO 27001 certified with UnderDefense’s reliable guidance
How long does ISO 27001 certification take?
The entire process of obtaining ISO 27001 certification can range from six months to over a year. The duration depends on several factors, including the size of the organization, its current information security posture, the complexity of its operations, and the level of preparedness for the certification process. Smaller organizations often achieve certification faster than larger ones. However, it’s important to note that the timeline also relies on the organization’s commitment, available resources, and the speed of addressing any identified gaps or non-conformities.
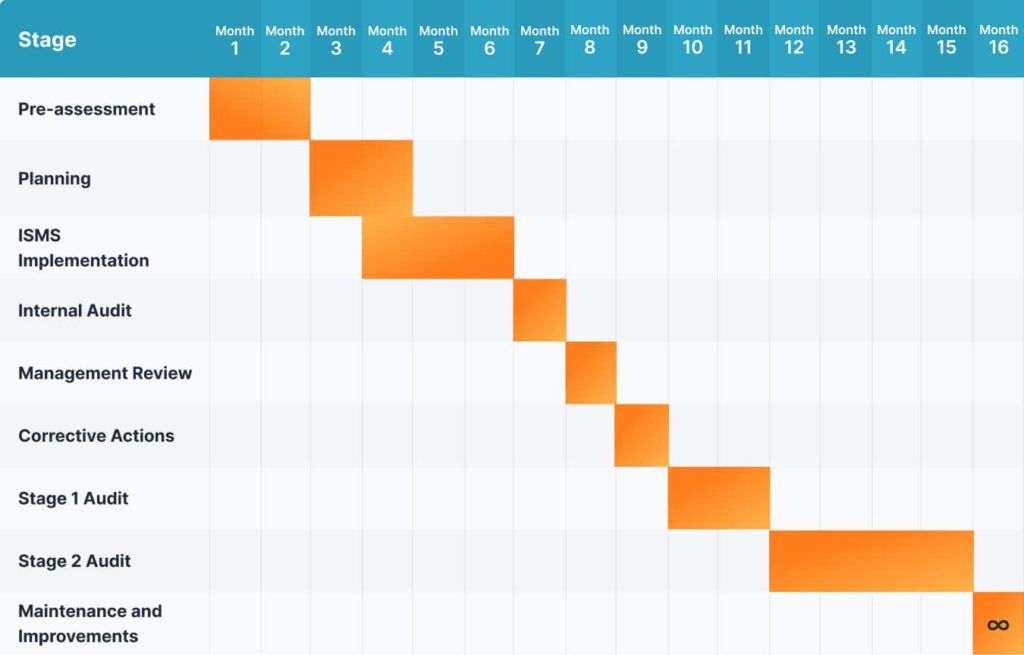
Below you can see a simple breakdown of the ISO 27001 certification process and the average time required for each stage:
Pre-assessment | 1-2 months |
Planning | 1-2 months |
ISMS Implementation | 2–3 months |
Internal Audit | 1 month |
Management Review | 1 month |
Corrective Actions | 1 month |
External Audit (Stage 1 audit) | 1-2 months |
External Audit (Stage 2 audit) | 2–4 months |
Maintenance and Improvements | ∞ |
The diagram displays a visual timeline of the certification process, considering the longest potential duration.
If you prepare for compliance on your own, be ready for a complicated and lengthy process. There are over 35 policies that should be created and implemented within your organization. But they are not about technologies or procedures only. They are also about employees and their security awareness. Meanwhile, failing to conform to some of the requirements may cost you an audit and time. So, consider engaging an experienced external cybersecurity expert to guide you through the process and guarantee your compliance success.
To effectively prepare for ISO 27001 compliance you should know what to start with and what to anticipate. It’s important to understand the requirements and steps, so let us walk you through the process.

Pre-assessment
1.Establish a dedicated pre-assessment team
Create a dedicated team for ISO 27001 compliance with clear objectives, timelines, and resource requirements. Define roles and responsibilities for information security management, ensuring accountability, and decision-making processes. Involve a C-level representative for a comprehensive understanding of company procedures. Consider the impact on compensation and revenue due to diverted employee duties. Engage specialists like software engineers, data scientists, legal experts, and technical writers if needed, but be mindful of reduced productivity. Utilize a third-party service provider to minimize costs.
Planning
2. Create a comprehensive ISMS roadmap
An Information Security Management System is the framework a company uses to manage information and risk. It comprises policies and procedures that provide precise guidelines for data storage and management. Developing an Information Security Management System involves a structured approach to protect sensitive information, so start by gaining leadership support and defining the scope. To establish the ISMS scope, do the following:
- Define the information to protect all storage locations (physical and digital).
- Document all access points (e.g., employee computers, file cabinets).
- Identify business areas that don’t store valuable information and exclude them from the scope.
- Develop comprehensive policies and procedures.
- Create an ISMS team, and provide training to employees.
- Implement security controls.
- Continuously monitor and measure the ISMS’s effectiveness.
It’s important to note that as your company evolves, new processes and departments may be created. So, it’s necessary to regularly review the ISMS and make adjustments as needed.
3. Conduct a risk assessment
Risk assessment is a crucial component of Information Security Management.
Here’s a concise overview of the steps involved:
- Identify critical information assets that include data, systems, hardware, software, personnel, and facilities.
- Identify potential threats that could compromise the security of these assets. Threats can be external (e.g., cyberattacks, natural disasters) or internal (e.g., employee errors, unauthorized access).
- Evaluate the weaknesses or vulnerabilities in your information assets that could be exploited by the identified threats.
- Determine the potential impact on the organization if a threat exploits a vulnerability. Assess the consequences in terms of financial losses, reputation damage, legal implications, and operational disruptions.
- Calculate the risk by multiplying the likelihood of a threat occurrence with the potential impact.
- Prioritize the identified risks based on their risk level to efficiently allocate resources and address the most critical risks first.
4. Complete a Statement of Applicability (SoA)
After choosing the controls that effectively address identified risks, the next step on the checklist is to develop a Statement of Applicability (SoA). It is a crucial document in the ISO 27001 Information Security Management System (ISMS) implementation that should cover all the relevant controls from Annex A of the ISO 27001 standard applicable to your organization. The SoA should outline the security measures you’ve selected to mitigate identified risks effectively. Additionally, it should explain the inclusion or exclusion of specific controls based on your business risk assessment and context. Finally, the SoA should serve as a reference for understanding the security controls implemented and point to the relevant documentation that explains how each control is applied within your organization.
ISMS implementation
5. Create and publish ISMS policies, documents, and records
To prepare ISMS documents, policies, and records you should do the following:
- Develop clear ISMS policies that align with business objectives and regulations.
- Create detailed supporting documents like procedures and guidelines.
- Maintain comprehensive records of ISMS activities and incidents.
- Review, approve, and communicate the documents.
- Update the ISMS materials to address evolving risks regularly.
- Ensure compliance with standards and prepare for audits.
- Foster a culture of continuous improvement for information security.
You can also check our list of ISO 27001 policies to get a better understanding of their role in information security and the establishment of ISMS.
6. Implement ISMS policies and controls
Once risks have been identified and risk management processes developed, you can proceed with the Information Security Management System (ISMS) policy. This policy provides a high-level overview of your approach to information security.
Many organizations adopt the Plan-Do-Check-Act (PDCA) method to effectively implement their ISMS plan. The PDCA cycle is a four-step management method widely used for continuous improvement in various processes, including the implementation and maintenance of an Information Security Management System (ISMS) following the ISO 27001 standard.
If you also want to follow the PDCA method, here’s the explanation for each step:
- Plan: In this stage, you’ll need to plan and establish the ISMS. It involves identifying security objectives, conducting a risk assessment, defining security controls, and developing a policies and procedures checklist. The goal is to create a robust plan that aligns with your organization’s needs and objectives.
- Do: This step involves implementing the ISMS according to the plan developed in the previous stage. You’ll have to put the policies and procedures into action, deploy security controls, and conduct training for employees to ensure they understand their roles in maintaining information security.
- Check: In the Check phase, you should monitor and assess the effectiveness of the implemented ISMS. This includes conducting internal audits, reviewing security incidents, and evaluating performance against established security objectives. The aim is to identify any deviations or areas for improvement.
- Act: Based on the findings from the Check phase, you’ll take corrective actions to address any identified weaknesses or non-conformities. Additionally, this phase involves making necessary adjustments and enhancements to the ISMS to continually improve its effectiveness and efficiency.
7. Conduct employee awareness & training programs
ISO 27001 emphasizes the importance of awareness programs to educate employees about information security practices, policies, and responsibilities. Creating a conscious culture is a fundamental aspect of a comprehensive security program. Regular cybersecurity training for employees is considered a best practice within the ISO 27001 standard. While such an approach may involve costs, it is essential to ensure that all employees participate and that the sessions effectively promote a security-conscious environment. Whether conducted internally or with a third-party provider, the training reinforces the organization’s commitment to safeguarding sensitive information and complying with ISO 27001 requirements.
Internal audit
8. Gather documentation and evidence
Having well-documented and reliable evidence assures successful ISO 27001 certification and demonstrates your commitment to information security to stakeholders, customers, and regulatory bodies.
Here’s how to approach it:
- Document Control: Ensure all relevant ISMS policies, procedures, guidelines, and records are properly documented, organized, and version-controlled. This documentation forms the foundation of your ISMS implementation.
- Evidence Collection: Collect evidence to demonstrate that ISMS policies and controls are effectively implemented and followed. This evidence could include meeting minutes, audit reports, training records, incident reports, and other supporting documents.
- Compliance Verification: Verify that the implemented controls align with ISO 27001 requirements. Cross-reference your documentation with the specific controls and requirements outlined in the standard.
- Evidence Retention: Retain documentation and evidence as part of your records management process. This documentation will be valuable during external certification audits and ongoing monitoring of your ISMS’s effectiveness.
9. Undergo internal audit
The internal audit helps identify areas that may need improvement and ensures that the ISMS is functioning effectively and aligns with ISO 27001 requirements. It also serves as valuable preparation for the external certification audit, providing an opportunity to address any issues beforehand. Regular internal audits play a vital role in maintaining the security and compliance of your corporate information assets.
Here are the general steps for conducting an ISO 27001 internal audit:
- Establish the scope based on your objectives and risks.
- Plan the audit and assign the team and resources.
- Review the ISMS documentation for compliance.
- Conduct interviews with key employees, gather evidence, and assess effectiveness.
- Identify non-conformities and gaps.
- Analyze findings and report to the management.
- Develop corrective action plans.
- Verify the implementation and follow-up.
- Continuously improve the audit process.
Read our comprehensive guide on the ISO 27001 internal audit checklist for a secure and resilient information security management system.
Management review
10. Ensure the ISMS remains effective and aligned with business goals
The management review stage should demonstrate that top management is actively involved in the ISMS operations, ensuring its ongoing effectiveness. In this stage, you make decisions, assess performance, and drive ongoing improvements to your organization’s information security management system.
Corrective actions
11. Identify, evaluate, and resolve non-conformities and incidents
During this stage in the ISO 27001 checklist, you should follow a structured process for addressing and rectifying non-conformities, security incidents, and deficiencies identified within your Information Security Management System (ISMS).
You have the right to know
External audit
12. Undergo a Stage 1 audit
As soon as you complete the internal audit with no issues, you are ready for the external audit, which is the final step leading to ISO 27001 certification. The external audit is similar to the internal one but aims to certify your ISMS.
The Stage 1 audit is actually a preparation stage for the final certification audit (Stage 2). Addressing any identified non-conformities and implementing necessary improvements based on the Stage 1 findings will significantly improve your chances for a successful Stage 2 certification audit.
During the Stage 1 audit, the auditor assesses the organization’s ISMS, scope, and certification readiness, and identifies areas for improvement. The audit report generated at the end of Stage 1 highlights these findings and provides valuable insights for the organization’s readiness to proceed to Stage 2.
To ensure a smooth certification process, it is advisable to conduct both Stage 1 and Stage 2 ISO 27001 audits within six months. If the Stage 1 audit is not completed within this timeframe, it may need to be repeated to address any shortcomings before moving to Stage 2.
13. Undergo a Stage 2 audit
The Stage 2 audit is the final validation of your organization’s efforts to implement and maintain a robust Information Security Management System. It provides the official certification demonstrating your commitment to safeguarding sensitive information and maintaining a strong security posture.
Here’s what you can expect during this critical audit stage:
- The auditor will verify the scope of your Information Security Management System (ISMS) to ensure it aligns with the objectives and requirements of ISO 27001.
- The auditor will conduct a comprehensive evaluation of your ISMS’s implementation. They will assess how well your organization has incorporated the ISMS policies, controls, and procedures into everyday practices.
- The auditor will gather evidence to validate the effectiveness and compliance of your ISMS. It may include interviews with personnel, observation of processes, and review of records and documentation.
- If any non-conformities are identified during the audit, the auditor will record them and provide feedback to help your organization address and correct these issues.
- Based on the audit findings, the certification body will decide on the certification of your organization’s ISMS. If the audit is successful and all requirements are met, your organization will receive the ISO 27001 certification.
Maintenance and improvements
14. Post-certification and periodic surveillance audits
After obtaining ISO 27001 certification, your organization should undergo periodic surveillance audits to maintain and demonstrate continued compliance with the requirements. The certification body conducts the surveillance audits at regular intervals, typically annually or as determined in the certification agreement.
Surveillance audits ensure ongoing compliance with the standard, validate the effectiveness of the Information Security Management System (ISMS), and verify the implementation of corrective actions if any non-conformities are identified. These audits offer an opportunity for continuous improvement.
15. Perform ongoing improvements
Performing continual improvement is a fundamental principle of ISO 27001 and an integral part of maintaining an effective Information Security Management System (ISMS). Continual improvement involves an ongoing process of identifying areas for enhancement, implementing changes, and monitoring the results to ensure that the ISMS evolves and remains effective over time.
Drawbacks of independent preparation for certification
Preparing for certification without engaging an external consulting company can save money. But it can also drag out and complicate your preparation due to a lack of resources and experience. All that may lead to a slowdown in corporate operations, and audit fees are non-refundable.
Hiring a reputed consultant may help you get audit-ready faster and improve your chances of becoming compliant on the first try. Let’s see what other benefits this approach has to offer.
Advantages of preparing for certification with an information security consultant
Navigating this process often requires a comprehensive checklist approach. If a company is uncertain about its financial capability and needs more knowledge, time, or resources to prepare for ISO 27001 compliance, it’s advisable to engage an external consultant.
Finding a reliable contractor to oversee certification preparation can be challenging but worthwhile. Hiring a virtual chief information security officer (vCISO) or other qualified experts can save time, cut costs, and ensure successful certification. They can provide checklist-driven expert assistance at all stages and better planning for the challenging duties involved in the process.
The consultant can assume responsibilities for pre-assessment and implementation, reducing up to 80% of the workload.
Pros:
- Improved understanding and preparation for ISO 27001 audits.
- Professional guidance available at all stages, including implementation.
- Full guarantee of successful certification.
Things to consider:
- Finding a trustworthy contractor that pays attention to every stage is challenging, so perform thorough research before making a choice.
- Additional expenses are typically reasonable because they allow other staff members to focus on their primary tasks instead of being drained by ISO 27001 compliance preparations.
Download UnderDefense ISO 27001 templates for free
ISO 27001 policy templates are valuable resources that can significantly streamline the checklist-driven approach to the ISO 27001 certification process. They provide standardized frameworks for creating essential information security policies and procedures required for compliance with the ISO 27001 standard. The use of pre-built policy templates can save time and effort, ensuring that your verified policies align with the specific requirements of ISO 27001.
ISO 27001 certification policy templates are available on our website if you want to begin this process independently.
Request free ISO 27001 certification policy templates now to get started.
Being prudent makes all the difference
Become ISO 27001 certified with UnderDefense’s reliable guidance
We are ready to assist you if you have deadlines and don’t want to fail a certification. We will do our share to ensure you pass the certification on the first attempt by giving you a “reserve” of knowledge.
We will help you handle all that is needed to get ISO 27001 compliant, including the following:
- Conduct a risk assessment.
- Adapt and prepare ISO 27001 policies checklist.
- Conduct security awareness training.
- Decide on the auditing company.
- Get a qualified virtual chief information security officer (vCISO) who will help at every stage of certification preparation.
- Conduct a penetration test if you have not done it yet.
- Address ISO 27001 security monitoring requirements by providing SOC (Security Operations Center) service.
- Gain and maintain compliance effortlessly with our SECaaS platform and compliance services.
Get advice on passing the certification by contacting our sales department. We’ll be happy to share your joy after achieving ISO 27001 certification!


















