In 2024, the threat of ransomware, a persistent and formidable force in the cybersecurity landscape, continues to loom large. Despite some positive strides, such as dismantling major ransomware groups, the danger remains substantial. It’s of utmost importance for businesses and individuals to stay fully informed about the latest statistics and their implications.
Let’s investigate the latest statistics and see what businesses and individuals need to know.
Alarming Ransomware statistics 2024
- Widespread threat: Despite a slight decrease in attacks, 59% of organizations were hit by ransomware in the past year.
- Skyrocketing costs: Recovery costs have jumped to a staggering average of $2.73 million per incident, up from $1.82 million in 2023.
- Massive Ransom demands: The median ransom payment has drastically increased from $400,000 to $2 million.
- Limited recovery success: Only 57% of businesses can recover their data using backups, and usage has dipped slightly.
- Shifting tactics: Ransomware groups increasingly steal data before encryption, putting pressure on victims to avoid leaks.
- Regional variations: Countries like Saudi Arabia, Turkey, and China are experiencing the highest rates of ransomware attacks.
- Questionable payoff: Only 8% of organizations could recover all their data even after ransom pay.
Ransomware in the headlines: Recent high-profile attacks
While many ransomware attacks fly under the radar, some grab headlines due to their scale and impact. Here are a few noteworthy incidents from recent years:
- Colonial Pipeline attack
In May 2021, Colonial Pipeline, a major US fuel pipeline operator, faced a devastating ransomware attack by DarkSide. The attack led to a significant fuel supply disruption along the East Coast of the United States, underscoring the vulnerability of critical infrastructure to cyber threats. Colonial Pipeline paid nearly $4.4 million in ransom to regain access to their systems. - JBS Foods attack
JBS Foods, the world’s largest meat processing company, was hit by ransomware in June 2021. The attack, attributed to the REvil ransomware gang, forced the shutdown of several plants in the US and Australia. JBS ultimately paid $11 million to the attackers to resume operations and prevent further disruptions. - Kaseya VSA attack
The Kaseya VSA attack in July 2021 was another significant incident involving the REvil gang. This supply-chain attack affected Kaseya’s remote management software, impacting hundreds of businesses that relied on their services globally. The attackers initially demanded a ransom of $70 million, though negotiations and other mitigating actions reduced the immediate impact. - Acer attack
In March 2021, Taiwanese electronics giant Acer was the victim of a ransomware attack, with the hackers demanding a record $50 million. This attack, also linked to the REvil group, was notable for the high ransom demand and the targeting of a major player in the tech industry. - CD Projekt Red Attack
Polish video game developer CD Projekt Red, known for popular titles like “The Witcher” and “Cyberpunk 2077,” experienced a ransomware attack in February 2021. The attackers accessed source code for several games and sensitive internal documents, demanding a ransom for their return. The company refused to pay, opting to rebuild its infrastructure and bolster security measures. - Ireland’s Health Service Executive (HSE) attack
In May 2021, Ireland’s Health Service Executive was targeted by a ransomware attack that severely disrupted healthcare services nationwide. The Conti ransomware group demanded a ransom to restore the systems. This attack highlighted the dire consequences of cyber threats on public health services, especially during the COVID-19 pandemic.
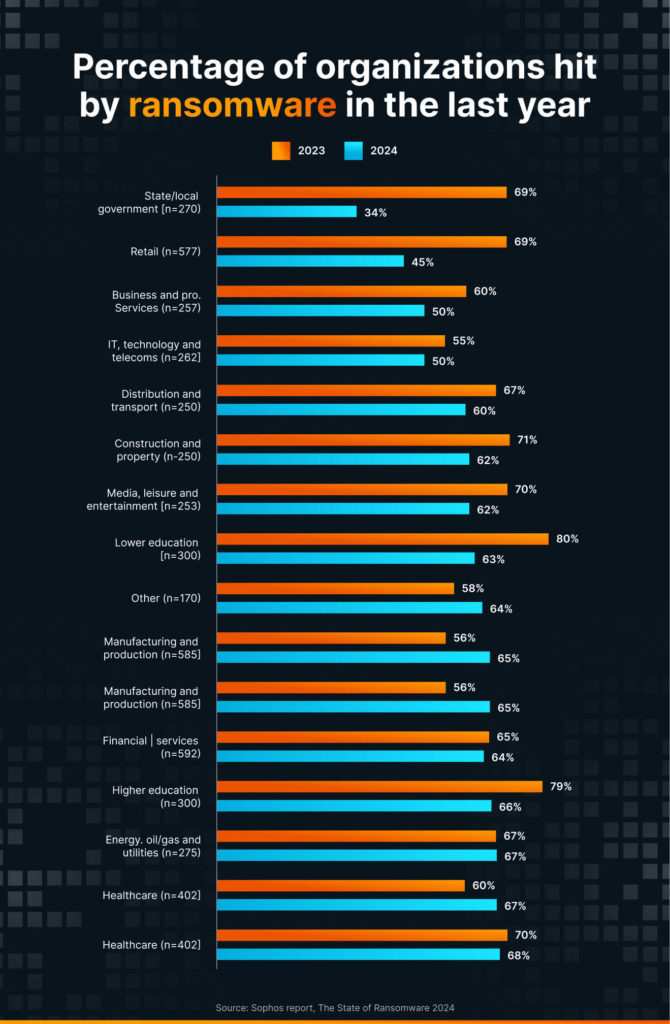
Ransomware statistics by industry
The bad news is almost no industry is immune to ransomware attacks. Recent studies found that between 60% and 68% of organizations across 11 out of 15 sectors were hit in the past year.
Here are some interesting trends:
- Central/federal governments saw the highest attack rates (68%), possibly due to politically motivated attacks. However, state/local governments experienced a significant drop (34%), potentially due to increased security measures or attackers focusing on larger targets.
- Previously a top target, the education sector showed a decrease in attacks, with higher and lower education institutions reporting 66% and 63%, respectively.
- The healthcare industry saw increased attacks, jumping from 60% to 67% in the past year.
- The IT, telecom, and technology sectors, previously with a lower attack rate, saw an increase to 55%, indicating a broader targeting by ransomware groups.
- The financial sector remains a prime target, with 28% of organizations reporting attacks in the past year. These attacks are especially costly, with average ransom demands exceeding $5 million in many cases.
- Retailers are facing a surge in attacks, with 24% experiencing at least one incident in the past year. Beyond data breaches, these attacks can disrupt sales and erode customer trust, causing long-term financial damage.
Cost of Ransomware attacks in 2024
Ransomware attacks are extremely costly in 2024, with recovery costs and ransom demands increasing. These expenses include direct ransom payments, operational downtime, recovery expenses, and long-term financial impacts on various sectors. Strong cybersecurity measures and solid recovery plans are essential for organizations to protect themselves against these expensive attacks.
Here are the key insights into the costs of ransomware attacks:
The average cost of recovery
- The global average cost of recovering from a ransomware attack in 2024 has reached approximately $1.85 million. This figure includes ransom payments, downtime, lost revenue, and recovery expenses (SOPHOS).
- In particular, the healthcare sector has seen an average recovery cost of $1.27 million per incident, reflecting the high stakes of protecting sensitive health data (SOPHOS).
Ransom payments
- The average ransom payment has increased significantly, with many organizations facing demands exceeding $5 million. Some high-profile cases have reported ransom payments in the tens of millions.
- Despite advice against paying ransoms, many organizations still opt to pay, hoping for a quick resolution to restore their operations (SOPHOS).
Downtime and operational disruptions
- Downtime costs, which include the loss of productivity and revenue during the disruption period, can be substantial. For example, the attack on the Colonial Pipeline resulted in millions of dollars in lost revenue and operational disruptions.
- Recovery efforts can extend for weeks, if not months, exacerbating the financial impact due to prolonged operational inefficiencies and additional recovery costs (SOPHOS).
Sector-specific impacts
- Government entities often face extensive recovery efforts and prolonged downtimes, with costs running into millions of dollars due to the critical nature of their services and the potential for severe public impact.
- Retailers facing a significant rise in attacks report immediate financial losses and long-term impacts such as lost sales and diminished customer trust.
- While the education sector shows some improvements in resilience, it still incurs high recovery costs and disruptions, particularly affecting data recovery and operational continuity.
Ransomware trends in 2024
As we move through 2024, ransomware attacks continue to evolve, becoming more sophisticated and targeted. Here are the key trends to watch out for this year:
- Targeted attacks: Cybercriminals increasingly focus on specific high-value targets such as healthcare providers, financial institutions, and critical infrastructure. They conduct thorough reconnaissance to maximize their extortion efforts.
- Double extortion: This tactic, in which attackers encrypt data and steal sensitive information for leverage, is becoming more common. It increases the pressure on victims to pay the ransom to prevent the release or sale of their data.
- Supply chain attacks: With the growing interconnectedness of global supply chains, attackers are exploiting vulnerabilities in third-party software and services to gain access to primary targets. This method can have widespread impacts, affecting multiple organizations within the supply chain.
- Hybrid ransomware: Expect to see more attacks that combine traditional ransomware with other types of cyber threats, such as data manipulation or destructive malware. These hybrid attacks aim to cause maximum disruption by encrypting data and damaging systems and operations.
- Ransomware-as-a-Service (RaaS): The RaaS model is evolving, offering cybercriminals more sophisticated tools and services. This includes improved encryption algorithms, techniques to evade security measures, and better support to facilitate ransom payments and decryption.
- Modernization of ransomware code: Attackers use secure programming languages like Rust to make ransomware harder to detect and analyze. They also adopt intermittent encryption to speed up the process and evade detection.
- Rise of mobile ransomware: With the increasing use of mobile devices, ransomware targeting smartphones and tablets is rising. This poses a significant threat to both individuals and businesses.
- Advanced bot usage: Cybercriminals use AI-powered bots that mimic human behavior to spread malware, conduct reconnaissance, and launch attacks like distributed denial-of-service (DDoS). These advanced bots make it more challenging to defend against attacks.
How to prevent ransomware attacks?
Preventing ransomware attacks requires a proactive and multi-layered approach to cybersecurity. Here are key strategies to help protect your organization:
1. Regular backups:
- Regularly back up your data and ensure that backups are stored securely offline. This allows you to restore your data without paying the ransom in case of an attack.
- Periodically test your backups to ensure they can be restored effectively.
2. Update and patch systems:
- Keep all software, including operating systems and applications, updated with the latest security patches. This helps close vulnerabilities that could be exploited by ransomware.
- Enable automatic updates where possible to ensure you do not miss critical patches.
3. Implement strong security measures:
- Use firewalls, antivirus software, and anti-malware tools to detect and block ransomware before it can cause harm.
- Employ endpoint protection solutions that offer advanced threat detection and response capabilities.
4. Employee training:
- Train employees regularly on cybersecurity best practices, such as recognizing phishing emails and avoiding suspicious links and attachments.
- Conduct phishing simulations to test and improve your employees’ ability to spot and report phishing attempts.
5. Access controls:
- Limit user access to only the data and systems necessary for their roles. This minimizes the potential damage if a user’s credentials are compromised.
- Implement multi-factor authentication (MFA) to add an extra layer of security for accessing sensitive systems and data.
6. Network segmentation:
- Segment your network to isolate critical systems and data. This helps contain the ransomware spread within your network.
- Implement strict access controls and monitoring to prevent unauthorized access between network segments.
7. Email and web filtering:
- Use email and web filters to block malicious attachments, links, and websites that deliver ransomware.).
- Employ sandboxing technologies to safely analyze suspicious files and links before they reach end users.
8. Incident response plan:
- Develop and regularly update an incident response plan specifically for ransomware attacks. Ensure all employees know their roles and responsibilities in case of an incident.
- Conduct regular drills to test your response plan’s effectiveness and make necessary improvements.
9. Advanced threat detection:
- In real-time, AI and machine learning-based security solutions can be utilized to detect and respond to ransomware threats.
- Implement behavioral analysis tools to identify and mitigate unusual activity that may indicate a ransomware attack.
Conclusion
Ransomware remains a significant threat in 2024 despite some initial hopes of a decline. The financial impact is more devastating than ever, with attackers targeting high-profile organizations and demanding exorbitant ransoms. The tactics are evolving, with data exfiltration becoming a growing concern.
The good news is that organizations can take action to protect themselves. Regularly updating software, implementing strong password policies, and prioritizing robust backup strategies are crucial first steps. Staying informed about the latest threats and developing a comprehensive incident response plan is also essential for minimizing damage if an attack occurs.
Ransomware isn’t going away anytime soon. However, by taking proactive measures and remaining vigilant, organizations and individuals can significantly reduce their risk of falling victim to this ever-evolving threat.