Cloud Penetration Testing Service
We conduct Cloud Penetration Testing to identify weaknesses in your cloud security and suggest improvements. Our experts simulate real attacks to find vulnerabilities before hackers do.

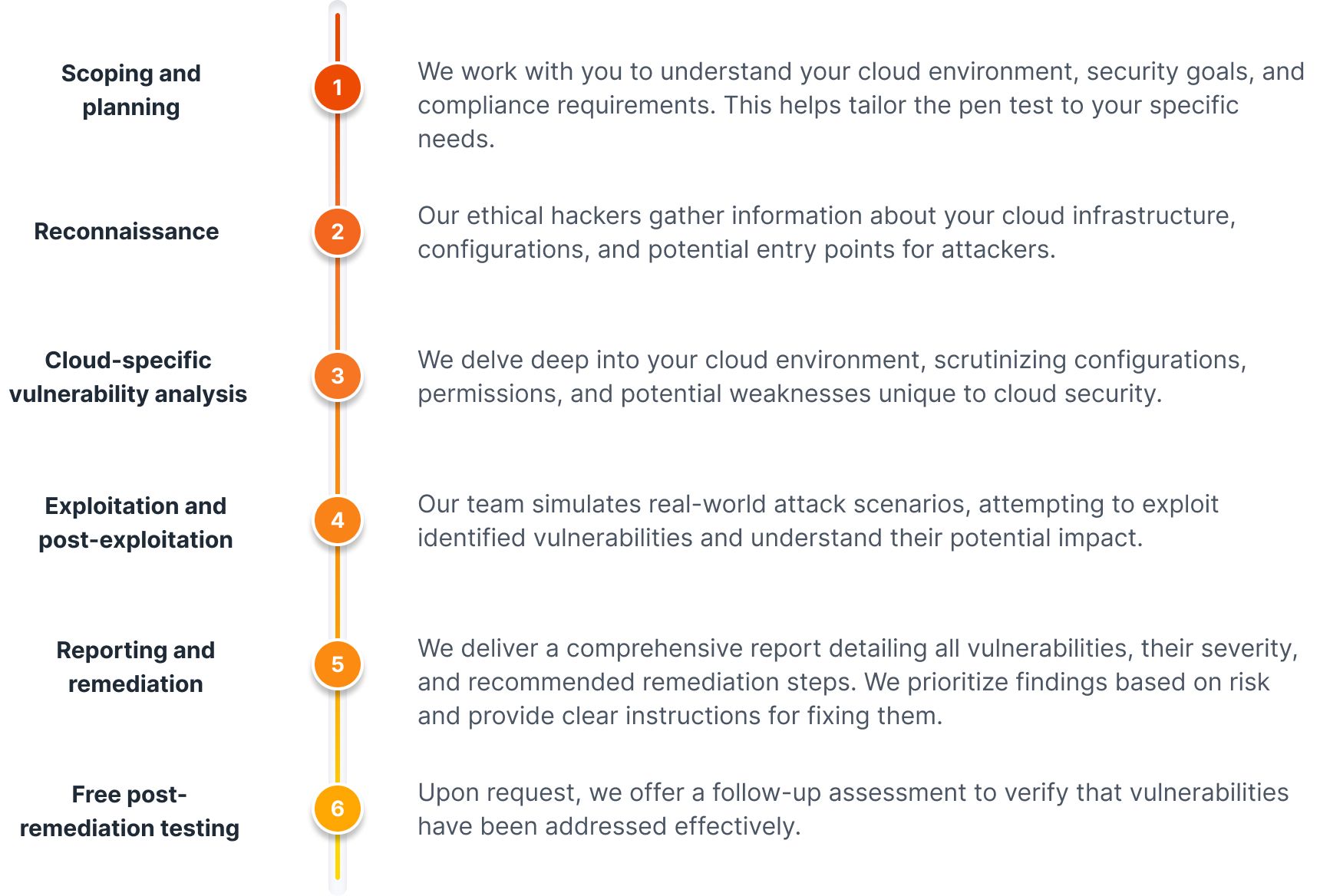
Our cloud pen testing process: uncovering and defending
Most common cloud vulnerabilities
Types of cloud pentests we provide
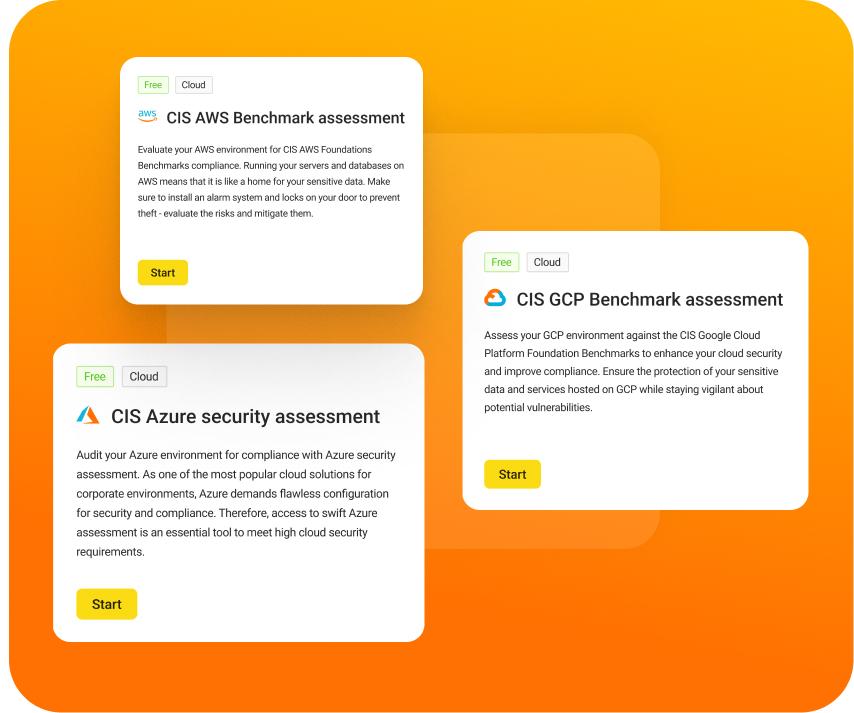
UnderDefense MAXI cloud assessment
Our expert team tailors assessments to each platform's security benchmarks.
UnderDefense MAXI Assessment doesn't limit itself to a single platform. It offers a holistic view of your cloud security posture across all cloud providers.
UnderDefense MAXI Assessment covers various security aspects, including configuration review, vulnerability scanning, threat detection, and compliance checks. It also includes more advanced threat intelligence and analytics.
You get a consolidated report on the security posture of all your cloud environments, highlighting areas for improvement across different platforms.
By consolidating your cloud security assessments into a single platform, you can save time and resources and potentially reduce overall costs compared to separate assessments for each provider.
Frequently asked questions
What are the steps involved in planning and executing a cloud penetration test?
- Scope Definition: Define the objectives, scope, and rules of engagement for the test.
- Reconnaissance: Gather information about the target cloud environment.
- Vulnerability Analysis: Identify potential vulnerabilities and misconfigurations.
- Exploitation: Attempt to exploit identified vulnerabilities to gain unauthorized access.
- Post-Exploitation: Assess the impact of successful attacks and escalate privileges.
- Reporting: Document findings, including vulnerabilities, exploitation techniques, and recommendations for remediation.
- Remediation Verification: Verify that identified vulnerabilities have been adequately addressed.
What are the main differences between penetration testing in traditional IT and cloud environments?
- Infrastructure Complexity: Cloud environments often involve more complex and dynamic infrastructure than traditional IT environments.
- Shared Responsibility Model: Cloud providers and customers share responsibility for security in cloud environments, requiring a clear understanding of roles and responsibilities.
- Virtualization and Containerization: Cloud environments heavily utilize virtualization and containerization technologies, introducing unique attack vectors.
- API Security: Cloud environments rely heavily on APIs for resource management, requiring thorough testing of API security.
- Data Protection: Data in transit and at rest in cloud environments require robust encryption and access controls to ensure security.
What role does cloud penetration testing play in compliance standards (like PCI DSS, HIPAA, or GDPR)?
- Pen testing helps uncover weaknesses in your cloud environment's configuration, access controls, and data security. These vulnerabilities could potentially be exploited to violate compliance regulations regarding data protection and privacy
- Fulfilling control requirements: Many compliance standards mandate specific security controls. Penetration testing verifies the effectiveness of these controls in withstanding simulated cyberattacks.
- Proactive risk mitigation: By proactively identifying and addressing vulnerabilities, you can prevent security incidents that could lead to non-compliance fines and reputational damage
- Regular penetration testing is often required to comply with PCI DSS, HIPAA, and GDPR.
How does cloud penetration testing support continuous improvement in security posture?
- Cloud penetration testing helps organizations identify vulnerabilities and weaknesses in their cloud environments on an ongoing basis
- Organizations can proactively detect and remediate security issues by conducting regular penetration tests before malicious actors exploit them.
- Penetration test reports provide valuable insights into emerging threats and attack trends, enabling organizations to adapt their security strategies accordingly.
- Continuous testing and improvement help organizations stay ahead of evolving threats and maintain a robust security posture in their cloud environments.
Things to check out
Ransomware: Still a Threat in 2024?
In 2024, the threat of ransomware, a persistent and formidable force in the cybersecurity...
Building a Strong SOC Team: Best Practices and Strategies
Introduction About SOC team functions Key SOC team roles and responsibilities Best practices of...