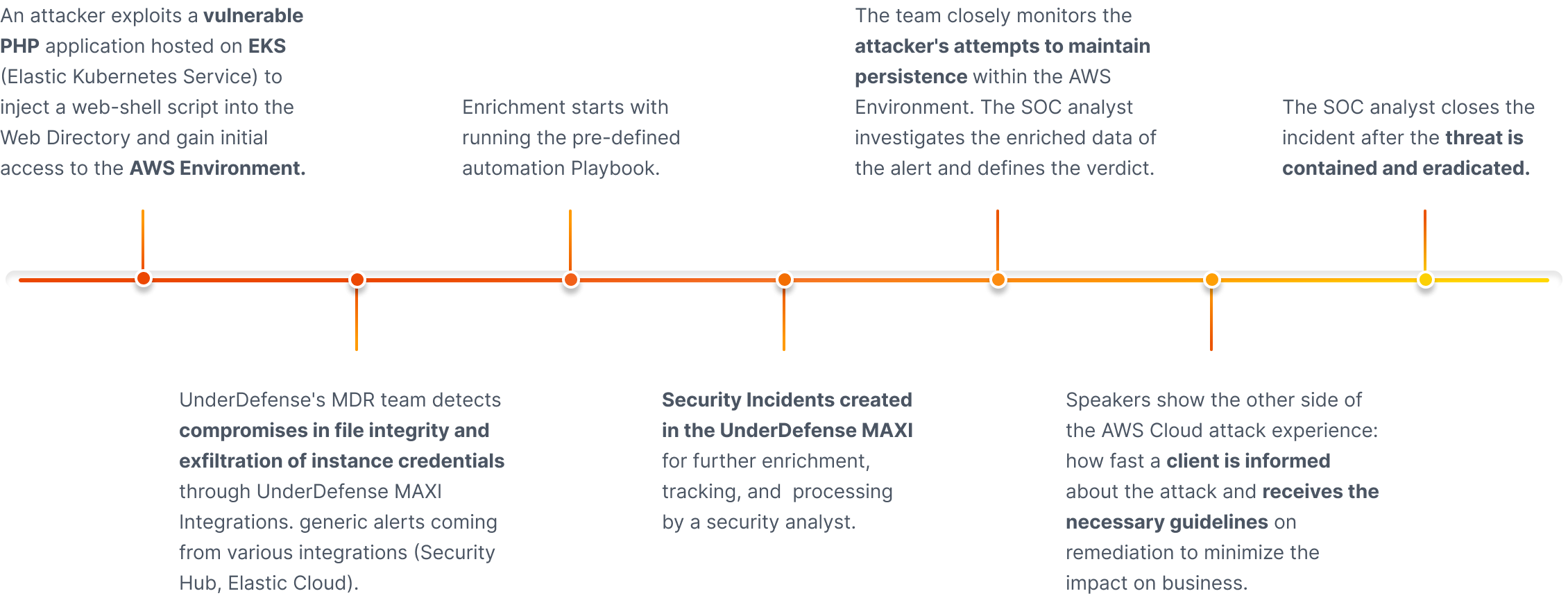
UnderDefense MAXI MDR Demo: Protecting Kubernetes on AWS from Exploits
The award-winning MDR team uses the UnderDefend MAXI platform as to detect, investigate, and respond quickly and effectively to an attack on the cloud in real time.
Watch Attack- 24x7 security monitoring is critical to spot a breach in time and contain it promptly with MDR.
- AWS breaches are possible. It is harder to execute than on endpoints, but all infrastructure is vulnerable.
- AWS credentials are valuable. Additional monitoring of identities and escalation of privileges is needed.
- AWS is not responsible for your security.
- Most companies experience detection and recovery challenges with cloud security.
- Temporary credentials may seem harmless, but they can be used to create persistent credentials, causing a potential threat.
- Regularly monitor and audit your AWS environment to detect any suspicious activity that could indicate a privilege escalation.
- Keep a close eye on the following key identities:
- Temporary credentials
- IAM users
- Roles
- Roles Anywhere
- Identity providers
- AWS credentials are powerful and can be costly. Hackers can create resources for malicious activity and extract valuable data.
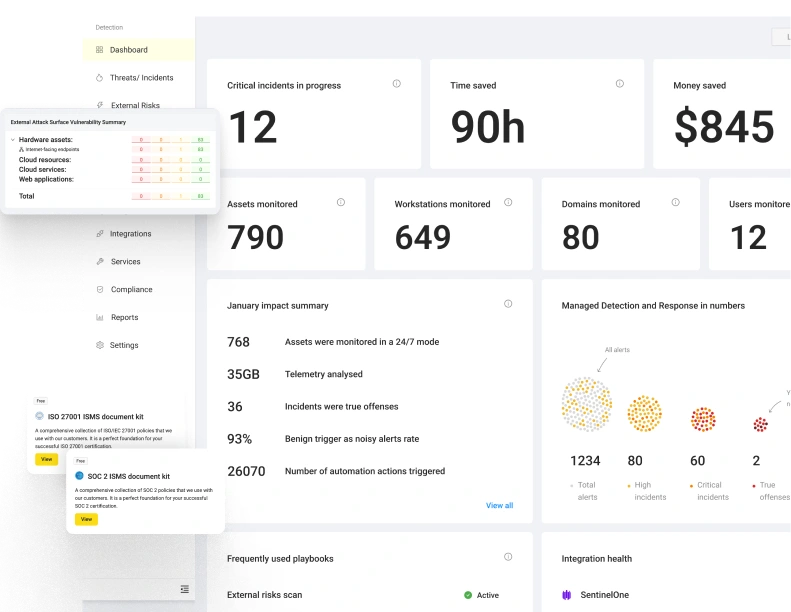
Get instant visibility and control over your multi-cloud environment
Effective DevSecOps work requires a combination of centralized management, automation, and prioritization to separate noise from true positives. Our platfrom is designed to move fast.

Mary Roak
CISSP, Product Marketing Director
Experienced leader and strategist in the cybersecurity industry with over 15 years of international technology marketing experience.