How to Protect Business Against Cyberattacks Amid Israel-Hamas and Russo-Ukrainian Wars

by Andrew Hural
Max 10min read
Back in 2022, the digital landscape has turned into a mirror of geopolitical tensions. The Russian invasion of Ukraine has shown what a modern war looks like, as it is now happening not only on the physical battlefields. The war has evolved and proliferated online to social media, news, and most parts of our daily lives.
Table of Contents
Wars and cyberattacks: what’s the connection?
While the actual damage caused by these attacks is comparatively contained, don’t let this fact deceive you. You may say that each attack is a response to specific political events, and each carries a message. However, the so-called “offensive flash mob” affected even those countries and organizations that hadn’t directly expressed their solidarity with Israel or Ukraine. It is now obvious that the cyber groups’ previous activities and availability also influenced the selection of targeted entities.
We must admit that direct damage or profit is not the only motivation of hacktivists. They want to emphasize their presence and authority in the international dialog by creating discomfort and fear. The general goal is to disturb the normalcy of everyday life. But considering that any business is a part of the daily routine, in one way or another, it is crucial to start taking proactive security measures ASAP.
You may also be interested in reading about must-have cybersecurity tools for small businesses
Cyber perspectives from Russo-Ukrainian and Israel-Hamas wars
The wars continue, and the last two years have proved that anyone can be a victim. Our experience has shown that the number of incidents doubled. And it is no longer a problem of the healthcare or banking sectors only. The numbers of targets in different industries during the 500 days of the Russo-Ukrainian War speak for themselves.
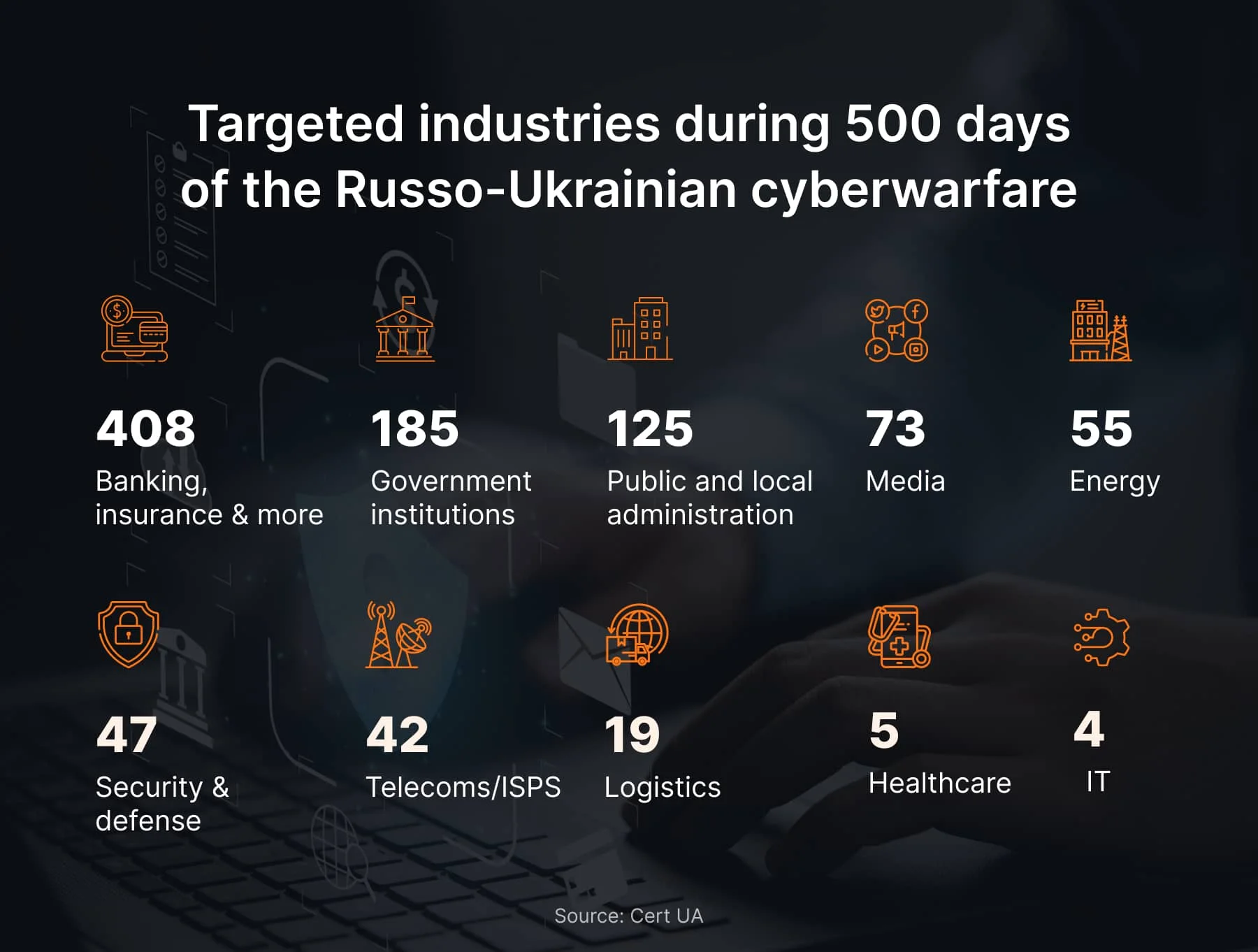
With that said, it is no longer a question of if but when you will be attacked. And sooner or later, all businesses will admit the need for better cyber defense.
Your 4 must-haves to build better business cybersecurity
We are witnessing the rise of more sophisticated cyberattacks and mature malicious actors. As the conflicts unfold, the number of risks and the range of targeted entities will continue growing.
So, apart from regular penetration testing services, what should organizations do to strengthen their defenses? Below, we list a bare minimum that each business should implement to tough it out.
1. Multifactor authentication
MFA is one of the easiest ways to add another security layer to an organization. But still, not all companies leverage it, which may cost them millions of dollars.
The 2023 Data Breach Investigations Report by Verizon found that 74% of breaches were caused by people, namely via the use of stolen credentials, social engineering, privilege misuse, or error. How is that possible? The sad truth is that 62% of people are reusing passwords even though most have cybersecurity education and awareness training. And the only thing worse is that those passwords are so common that AI tools can easily crack them in a few seconds.

So, what can you do about that? Enable prebuilt rules offered by the largest vendors, like Google Workspace security best practices and others. Another relevant example that you can follow is Amazon Web Services, which will mandate MFA for all privileged accounts starting in mid-2024. Doing so, can enhance your basic security and lessen the risk of account hijacking.
2. Security automation
You will hardly find here some bold statements saying that AI will become the main driving force in cybersecurity in the next few years. In our opinion, this is not the case because human intelligence is still crucial. Yet, AI can become a perfect assistant to your in-house employees as there are too many alerts to sift through manually.

Security automation is a broad term that may mean different functions. And what we know for sure is that the more you automate, the better. But, like with any other technology, do it wisely to safeguard your sensitive data. One of the easiest and safest ways to introduce security automation to your business is to try UnderDefense MAXI security-as-a-service platform. The automation inside the platform has already proved its efficiency to users in the following areas:
- External attack surface monitoring
- Threat and context enrichment
- Reporting
- Security assessment of AWS, Azure, and GCP platforms
If you still doubt, we should mention that cybercriminals also actively use automation. That’s one of the many reasons why the sophistication and number of attacks continue to grow daily. Meanwhile, your security teams won’t be able to keep up, executing defenses manually. Consequently, to effectively resist the offensive onslaught, you should do as the famous idiom states: “Fight fire with fire”.
3. Consolidation of the security stack
No one will be surprised if we say cybersecurity is complicated, right? Multiple consoles, constant switches between contexts, manual correlations, and other operational inefficiencies increasingly demotivate security teams. Meanwhile, business leaders get even more dissatisfied with the security outcomes amid the evolving threatscape.
It’s also no surprise that according to Gartner, 75% of organizations are looking to consolidate their security tools and vendors. That, in turn, has recently provoked a wave of mergers and acquisitions as cybersecurity companies thrive to offer comprehensive platforms.
The latter is the preferred CISOs’ option for obvious reasons. Instead of trying to connect myriad tools that may/may not communicate with each other, they merely delegate that to a platform provider who has handled all the hard work with integrations.
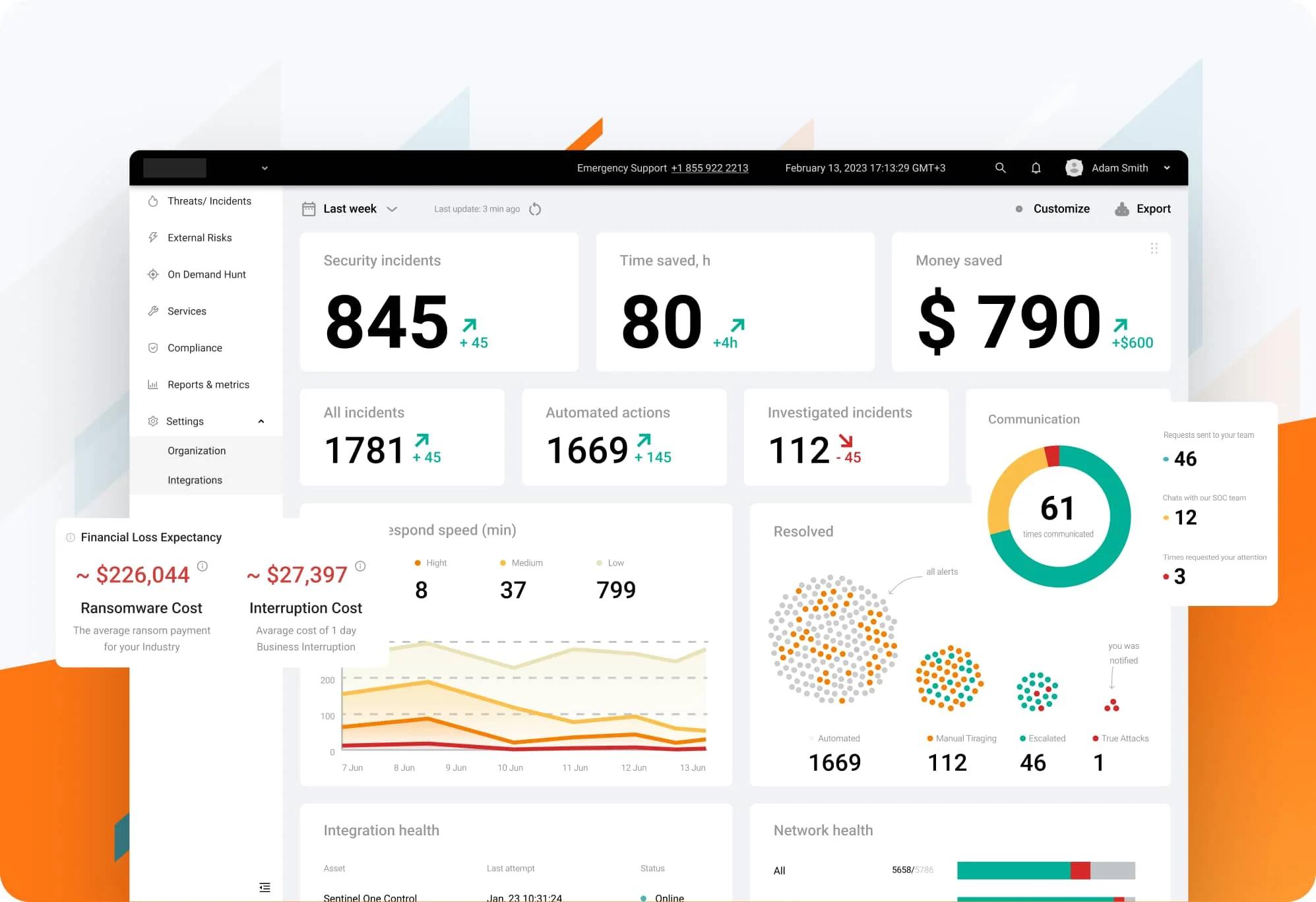
Source: UnderDefense MAXI platform
Sounds like a perfect option, doesn’t it? Unfortunately, there’s a catch. While UnderDefense MAXI leverages your current stack, most providers have lists of required software vendors. So, to start using their platforms, you will need to adjust your security stack, leading to additional expenses, complexities, and delays.
Not all security executives and organizations can afford that, especially considering the ongoing wars, risks, and dynamics. We feel your pain. That was one of the main reasons we’ve created a turnkey MDR solution that integrates into existing stacks, improving security visibility, reporting, and in-house team productivity. In this case, UnderDefense, as a provider, adjusts to your toolset and enhances its efficacy, not vice versa.
However, if you still tend towards other consolidation variants, pay attention to supported tools and environments to not open Pandora’s box with a wrong decision.
4. 24/7 monitoring, backed by people
Finally, it’s time to tell hard truths. Protecting your organization against modern ransomware, social engineering, and other sophisticated attacks requires a multi-layered defense strategy, and 24/7 security monitoring should be at its core. In-house or external managed SOC is what makes all of this possible.
Round-the-clock monitoring works well only if it relies on both technology and people. Tech solutions are essential now but not enough on their own. Our case with one of the clients, when we detected and responded to the incident two days faster than CrowdStrike OverWatch, is the best proof here.
But is it better to build SOC in-house or hire a third party? The latest findings in IBM’s Cost Of a Data Breach Report 2023 show that most companies can’t handle their cybersecurity alone. According to the research, only one-third of organizations identified a data breach through their in-house security teams or tools. In cases when attackers disclosed a breach, it cost businesses about $1 million more compared to initial detection.

So, considering the breach cost, it would be fair to say that hiring a third party for 24/7 threat detection and response is more efficient and cost-effective. Moreover, many providers don’t stop on attack surface monitoring and offer other security services. For example, at UnderDefense, we also provide our clients with proactive threat hunting, remediation on their behalf, and notifications with contexts via Slack or MS Teams. As you can see, the right third-party provider can significantly strengthen your security posture.
You may also be interested in reading about managed detection and response benefits for modern organizations
Final thoughts
The theater of modern cyberwarfare serves as not just a reminder but a wake-up call for most businesses to stay vigilant and agile. We also call for all individuals to take precautionary measures and avoid clicking unfamiliar links, downloading software from unknown sources, and ignoring system updates, especially critical ones. All those basic recommendations are now more crucial than ever.
As we see the careful execution of offensive cyber operations and new details of malicious events that emerge over time, it becomes clear that the online front is as crucial as the physical one. So, to safely exist in today’s interconnected world, security executives should embrace a proactive approach.
The aforementioned cybersecurity must-haves require time and effort. Security teams and managers should be ready to streamline cybersecurity operations, expand response capabilities, and adapt their defense strategies as quickly as the threat actors. With that said, there is only one rule–don’t leave it until it is too late. If you have questions or need help with some aspects of your business security, you can contact our experts and have a free consultation.
More from UnderDefense:
Questions about cyber security?
Read more
Read more about Managed Detection and Response Service (MDR)

Download MDR Datasheet

Read more about our Incident Response Service

Discover all features of our UnderDefense Security-as-a-service MAXI platform







