CASE STUDY
UnderDefense Team Detects and Addresses a Cyberthreat Faster Than CrowdStrike OverWatch
Key Results
UnderDefense SOC team responds to the security incident
2 days faster
than CrowdStrike Falcon OverWatch
Background
When the Russo-Ukrainian war began, Ukrainian government organizations experienced massive hacking attacks, resulting in data breaches and operational disruptions. The progressing war triggered the need to establish relevant government bodies and engage commercial units to provide additional security to government entities. The ultimate goal was to enable these organizations to continue their operations without falling victim to cyberattacks. Plus, they wanted to avoid service interruptions or any other negative consequences.
Various world-known vendors provided their security solutions for free to support Ukrainian government institutions. This way, they aimed to demonstrate shared responsibility and support in protecting critical information.
The UnderDefense team immediately joined as volunteers to contribute to cybersecurity efforts. We partnered with a well-known government cybersecurity organization by augmenting their offerings with our advanced 24/7 Security Operations Center (SOC).
Client Introduction
Headquarters:
Kyiv, Ukraine
Government, Healthcare
April 2023 – Ongoing
CrowdStrike Falcon OverWatch
No
Hybrid
Covered Endpoints:
100+
The Challenge
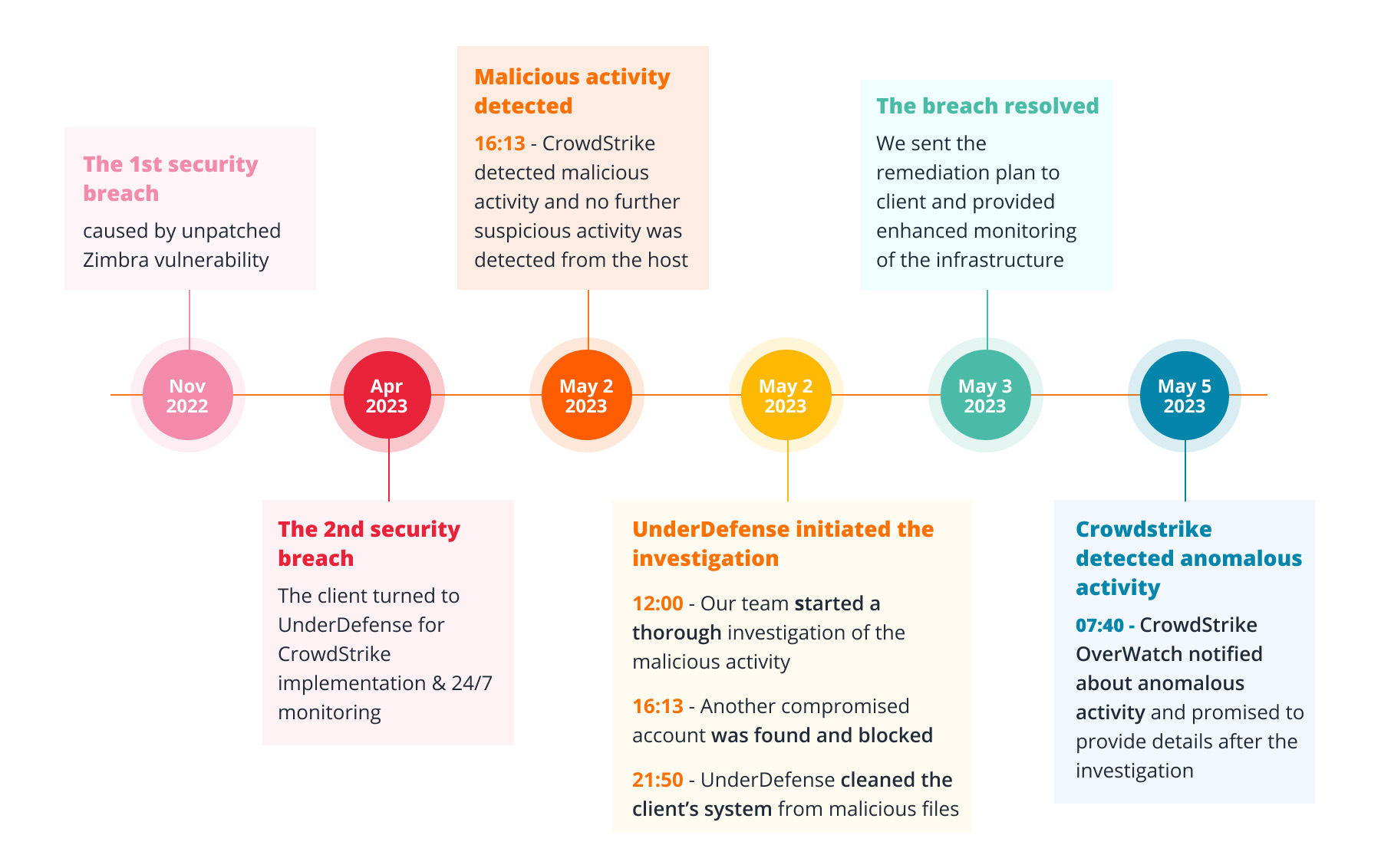
In November 2022, our client experienced a major security breach. Their accounts were hacked by Russian cyberattackers that infiltrated their network. The attackers likely stole sensitive data from the compromised database. After the incident, the post-breach investigation conducted by the client couldn’t find evidence of ongoing malicious actions.
In April 2023, the client had another breach and involved a government cybersecurity organization for Incident Response. Following that, a security hardening process was initiated to prevent future incidents.
After the second breach, the government cybersecurity organization representatives contacted UnderDefense for help. They needed a hand with integrating CrowdStrike agents into the client’s systems and implementing 24/7 monitoring to enhance the overall security posture.
Suspicious activity in the client’s network
Two weeks after UnderDefense joined forces with the client, one of our analysts discovered a suspicious command being executed on Linux servers. It was detected and blocked by a CrowdStrike agent. The command collected system data, including vulnerabilities, and sent it to an unidentified recipient.
Even though it seemed legit, we had our doubts and asked the client to confirm the activity because we couldn’t figure out why they would need that kind of information.
After thorough research, we discovered a user in the client’s Active Directory whose initials closely resembled a legitimate user but with an additional letter at the end. This indicated that the threat actors were still present within the network. As a result, the client deactivated the suspicious user account and commenced the necessary incident response measures.
Unfortunately, further analysis revealed that the data accessed by the hackers had already been leaked on the dark web. That included sensitive information like administrator emails, compromised Viber accounts, and passwords.
IT personnel as the root cause of the breach
In the cybersecurity realm, threat actors often target IT personnel to gain system control. Overconfidence of IT staff poses difficulties in handling incidents independently. Initially, they often lack insight into malicious actors’ techniques to establish their presence within the system. This challenge becomes particularly evident when dealing with Windows environments.
Adherence to predefined emergency procedures is crucial in a government organization like our client’s. From our side, checking systems and assessing the possibility of human error was paramount, as it remains the major contributing factor to cybersecurity issues. Stanford University research indicates that approximately 88% of data breaches result from employee mistakes. Our case was no exception, as we uncovered a breach caused by administrator negligence.
After the initial compromise, the client didn’t reinstall the operating system. They continued using the same compromised infected computer. As a result, the keylogger was installed there, recorded all passwords entered on the system or web browsers, and sent them to a management server. That’s why, even after replacement, all user passwords again ended up in the hands of malicious actors.
Furthermore, the IT staff didn’t follow basic cybersecurity rules. For example, all passwords were stored in a *.txt file, and all reset passwords were sent via email, disregarding essential security protocols.
The late response of CrowdStrike OverWatch
Two days after resolving the problem, we received a letter from CrowdStrike Overwatch regarding suspicious activity. Although they were uncertain about the severity, they advised us to remain vigilant. They assured us they would continue monitoring the situation and alert us if any danger emerged.
Fortunately, our SOC team was there to ensure a quick response. Such an approach allowed for mitigating drastic consequences for numerous government entities whose outcomes remain uncertain.
Incident Timeline
The Solution
This case again confirmed that the inadvertent oversight of some details could lead to dire consequences for the entire organization and the loss of confidential information. So, our next steps included the following:
- System reset. UnderDefense promptly informed the client about the issue and recommended reinstalling the operating system on most of their servers. We did that because CrowdStrike agents had been installed only on servers with detected suspicious activity
- In-depth investigation. Our team conducted a thorough investigation and engaged the client to analyze the logs available in CrowdStrike and other resources throughout the process. We had access to specific file names, allowing us to check their unique identifiers and determine when they were last modified. Plus, we took various actions within our assigned tasks while the client focused on checking network connections and monitoring user activities.
- A comprehensive response to the breach. During the investigation process, our experts discovered that multiple hackers from Russia and Vietnam had infiltrated the network and tried to gain higher privileges by brute-forcing local accounts. We isolated the compromised computer and thoroughly cleaned the system to address the threat. Finally, we leverage our extensive industry knowledge to proactively enhance the client’s cybersecurity posture and protect valuable data 24/7.

Outcomes
Preventing the spread of malicious software in government organizations
After the incident, the same malicious software was found in other government institutions. This suggested that the threat actor was following a typical pattern. The intriguing aspect was that it had a relatively low detection rate as a potentially harmful program when we looked into the backdoor on threat intelligence platforms. Although we were able to detect suspicious activity solely in this specific case, we immediately informed related official entities about the potential risks and the necessary steps to address this issue.
Leveraging lessons learned
In the face of the ever-evolving cyber threat landscape, attacks on government institutions are rising, particularly in light of the ongoing war in Ukraine. Despite the diligent efforts of IT professionals to secure and recover from these attacks, there remains a disconcerting reality that attackers can easily regain access in approximately 20% of cases. Often, IT professionals try to restore operations first rather than conduct comprehensive investigations into the root causes or identify potential entry points.
Currently, the client is delighted with our services. We have successfully integrated top-tier tools, cleaned their data and systems, and established 24/7 monitoring to ensure end-to-end visibility and continuous protection.
Using tools and human intelligence to strengthen security posture
This case highlights the critical role of human involvement in cybersecurity. Even with powerful tools, timely detection of suspicious activity proved insufficient.
At least our team reacted to the threat two days faster than CrowdStrike Overwatch, which allowed us to prevent any negative consequences. Admittedly, tools play an essential role in cybersecurity. But it is crucial to acknowledge that people matter just as much, if not more.
UnderDefense clients frequently inquire about the human effort invested in our product and services. This emphasis on human expertise highlights the recognition that technology alone is insufficient to address cyber threats’ dynamic and sophisticated nature. It underscores the significance of skilled professionals who possess the knowledge, experience, and adaptability to navigate evolving security landscapes and provide effective defense strategies. By combining cutting-edge tools with human intelligence, we ensure a comprehensive approach that maximizes the protection of our client’s valuable assets and safeguards against emerging threats.





