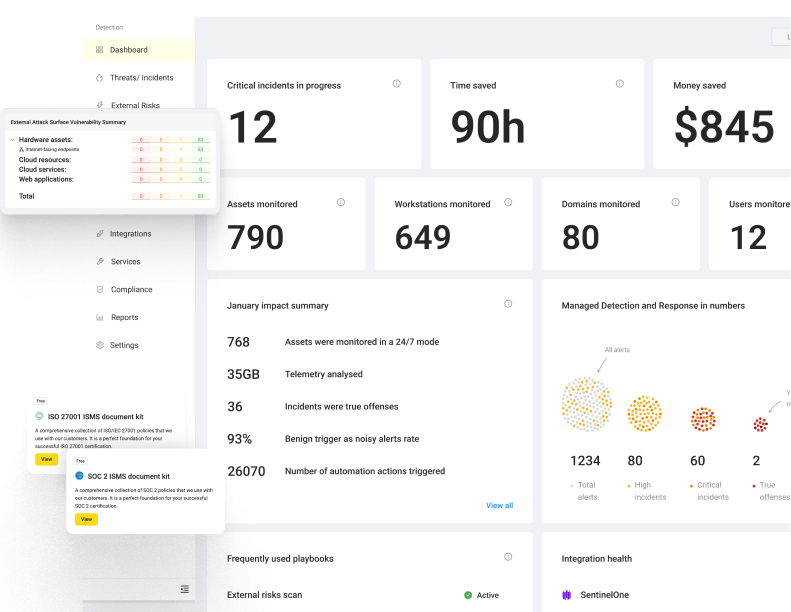
Let’s be frank—no one wakes up thinking, “Today’s the day I get phished.” But that’s exactly what...
How to Choose a SIEM: 8 Key Criteria for the Right Fit
Imagine signing up for a gym that promises world-class equipment, 24/7 access, and personal...
Why NOC Fails Your Security. NOC is NOT Your SOC
Regarding protecting a business, there’s a common myth that a Support team or Network Operations...
CISOs’ Compliance Roadmap: 2025 Regulations & Standards Made Clear
Welcome to the CISOs' guidebook for navigating the 2025 compliance updates. If you've ever felt...
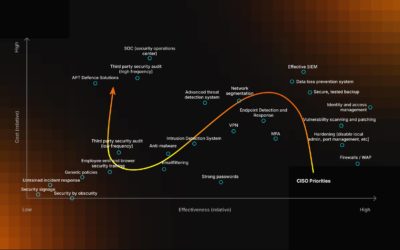
Building a 2025 Security Stack: A Veteran CISO’s Guide to Cost-Effective Priorities
“Security is like an onion: the more layers you add, the harder it is to peel through.” Matthew...
Guide to 2025 Compliance: Why 24/7 Log Monitoring is a Must
Let’s face it—getting audit approval is tougher than ever, especially when we consider log...
11 Kubernetes Security Best Practices: Ultimate Guide to Your Cluster Safety
Securing Kubernetes can feel like an uphill battle—it’s dynamic, complex, and a prime target for...
MDR Price: How It’s Determined and What It Depends On (A Practical Guide)
Managing cybersecurity can be a never-ending juggling act—keeping threats at bay without breaking...
Top 18 Sophos Competitors & Alternatives in 2025
If you're familiar with Sophos, you know it's a big name in the cybersecurity world, offering...
We make cybersecurity simple, affordable,and consistent...
...by unifying currently disjointed security tools from multiple vendors. UnderDefense MAXI is on the mission to automatically detect, investigate, and respond to all possible attacks.