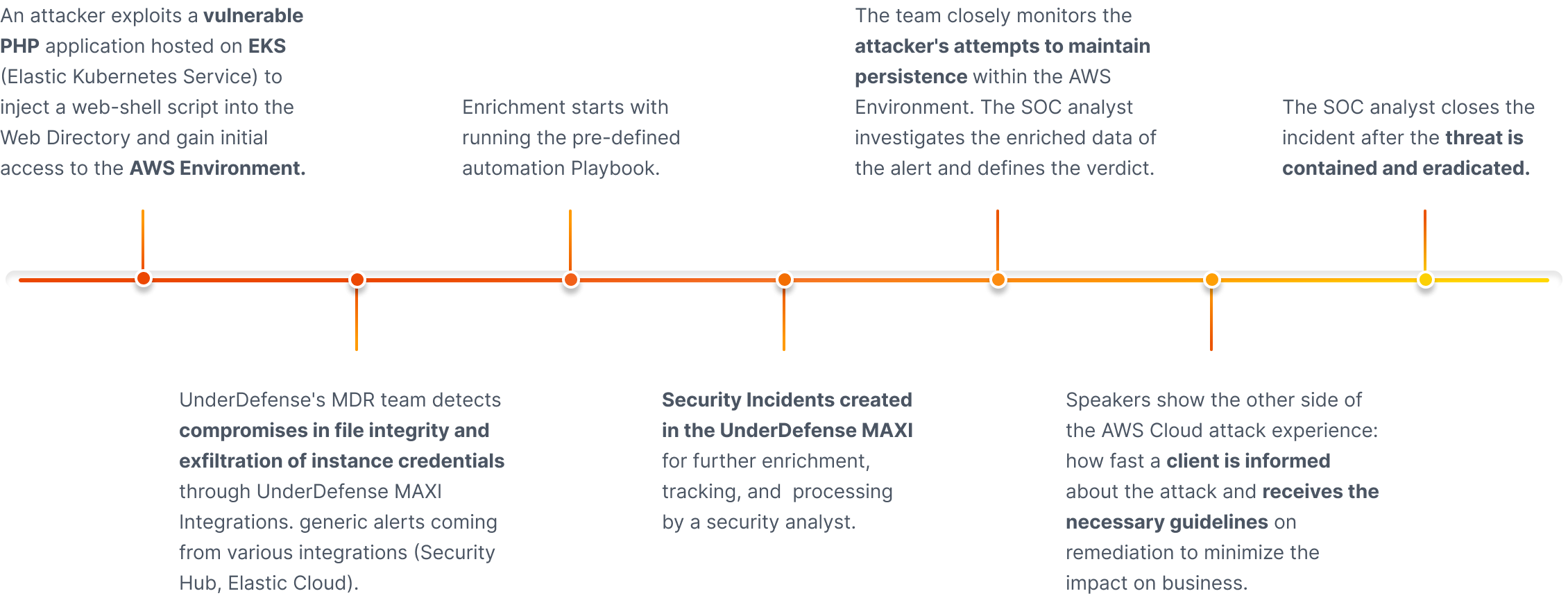
Watch live AWS Cloud attack response demo
The award-winning MDR team uses the UnderDefend MAXI platform as to detect, investigate, and respond quickly and effectively to an attack on the cloud in real time.
- 10 min UnderDefense MAXI product introduction
- 25 min real-life attack response
- 10 min Q&A session