Case Study: Incident Response
Targeted C-level attack.
What consequences it may have on business?
About the client:
A global healthcare company that is focused on innovating the healthcare system. A pioneer that effectively introduced the use of blockchain in healthcare.
Location: Global
Industry: Healthcare, Blockchain
“Compromise assessment performed by UnderDefense gave us literally our lives back. We were highly impressed by the quality and speed of their work.”
the CEO
Services used:
Prerequisites
Clients’ company management was notified by the US Security Service about a planned targeted attack. Due to the USSS, the probable attackers goal was to steal digital tokens from the company or investors’ tokens. Few days later the CEO of the company became a victim of a SIM theft attack with identity theft, account takeover and attempt to compromise external services.
UnderDefense was involved to assess the current situation and help to make sure that the company assets are not at risk of being compromised.

Our Findings
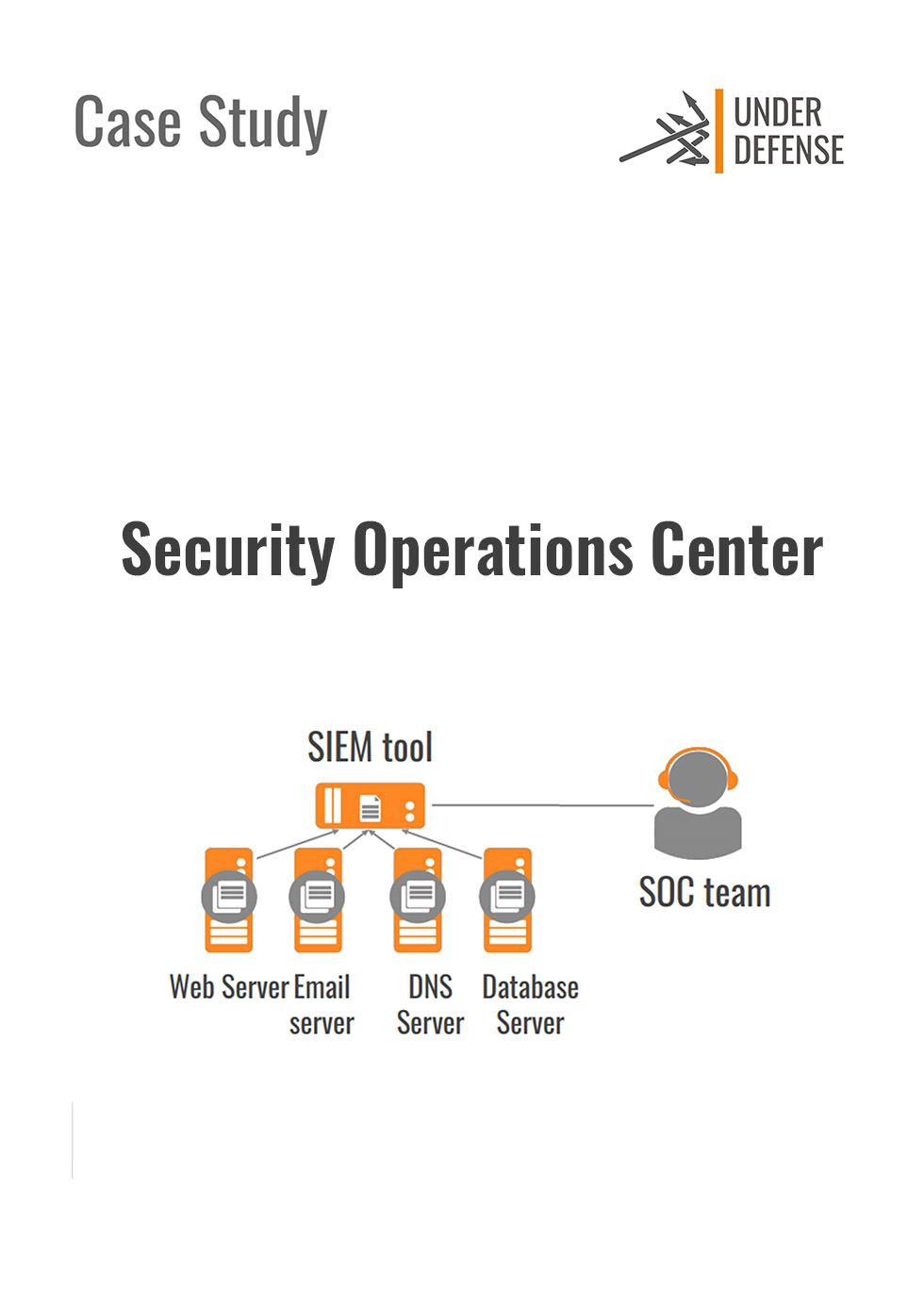
Besides Covid-19 world-wide restrictions, part of the UD Incident Response team arrived on-site and along with our remote team, we performed a full-scope compromise assessment of the client’s infrastructure.
The assessment included real-time infrastructure monitoring with deep forensics back in time looking for signs of Advanced Persistent Threats.
During our investigation, we found both threat actor’s footprints and multiple Security Misconfigurations that may lead to probable compromisation. As a result of work, we prepared a detailed report with provided recommendations to improve clients’ cyber resilience state.
Our Findings
Besides Covid-19 world-wide restrictions, part of the UD Incident Response team arrived on-site and along with our remote team, we performed a full-scope compromise assessment of the client’s infrastructure.
The assessment included real-time infrastructure monitoring with deep forensics back in time looking for signs of Advanced Persistent Threats.
During our investigation, we found both threat actor’s footprints and multiple Security Misconfigurations that may lead to probable compromisation. As a result of work, we prepared a detailed report with provided recommendations to improve clients’ cyber resilience state.

Attack Timeline
Notification from the US Security Service about a planned targeted attack
Personal phone number of CEO was stolen using SIM swap attack
An unsuccessful attempt to login and reset the password of primary Office 365
Personal email account of CEO stolen using stolen SIM card
Fake G-suite domain created
Usage of CTO’s leaked account credentials
Attacker hijacked company website
CEO starts receiving extortion emails
0 hours Company requests a Compromise Assessment Service
8 hours UD Team starts with technology deployment and interview witness onsite
UD Team performed deep forensics of both client infrastructure and critical clients assets
10 days UD team presented the final report with findings

The Result
During this investigation, we discovered multiple, critical misconfigurations that could have been used as entry points for malicious actors. All the findings were documented with suggested actions to mitigate them according to cyber security best practices.
We have spotted multiple ongoing attacks, though none of them was successful and there were no signs of the active presence of malefactor actors and no active threats in the Client’s corporate environment.