CASE STUDY
Underdefense Pentesters Saved the Client over $2M per Day by Detecting Critical & Medium Vulnerabilities on Time
Key Results
Vulnerabilities discovered
Expected daily losses in case of business interruption
Background
Our client is a global enterprise and a leader in the art supply industry, offering a diverse range of related products. They have expanded their market presence through strategic acquisitions of iconic brands.
The Challenge
- Vulnerability:The manufacturing industry was in the top 5 victim industries, according to Verizon’s 2023 Data Breach Investigations Report. The industry experienced 1814 incidents and 259 confirmed data breaches globally. Moreover, hackers were driven by financial motives in 96% of cases. All of that raised significant concerns for our client.
- Decentralized network:The size of this distributed network, which encompassed around 600,000 hosts and servers, evolved into an issue that had to be addressed. Obviously, this could translate to 600,000 entry points for hackers.
- Legacy: The client had acquired numerous multinational manufacturing companies, each with its own tech stack and often outdated technologies. Despite efforts to consolidate these networks into one comprehensive system, there was a severe lack of visibility and documentation. This led to situations where administrators had little to no knowledge about specific subnets.
- Impact on employee performance: While the network challenges didn’t directly affect core business processes, they did reduce employee productivity. Slow or disrupted connections within the internal network frustrated employees and prevented them from working efficiently. Fear of potential attacks by ransomware groups and advanced persistent threats (APTs) loomed due to the lack of network visibility and monitoring.
About the client
Headquarters:
Art materials
7000+ employees
170,000+ IP addresses
The Solution
Objectives | Revealed problems |
Detecting potential risks, particularly the risk of a ransomware attack |
|
Identifying network-based threats and vulnerabilities in the Active Directory |
|
Checking for cyber hygiene |
|
Comparing the customer's security measures to industry best practices |
|

Scope and timeframe
Scope | Description |
Internal/external network scope | Active Directory, Internal Network Servers including SAP systems |
Network devices scope | L2/L3 Network Devices |
Wi-Fi testing scope | Wi-Fi networks (6 SSIDs) |
SAP testing | SAP NetWeaver application, SAP J2EE engine, SAP SOAP API, SAP Main database |
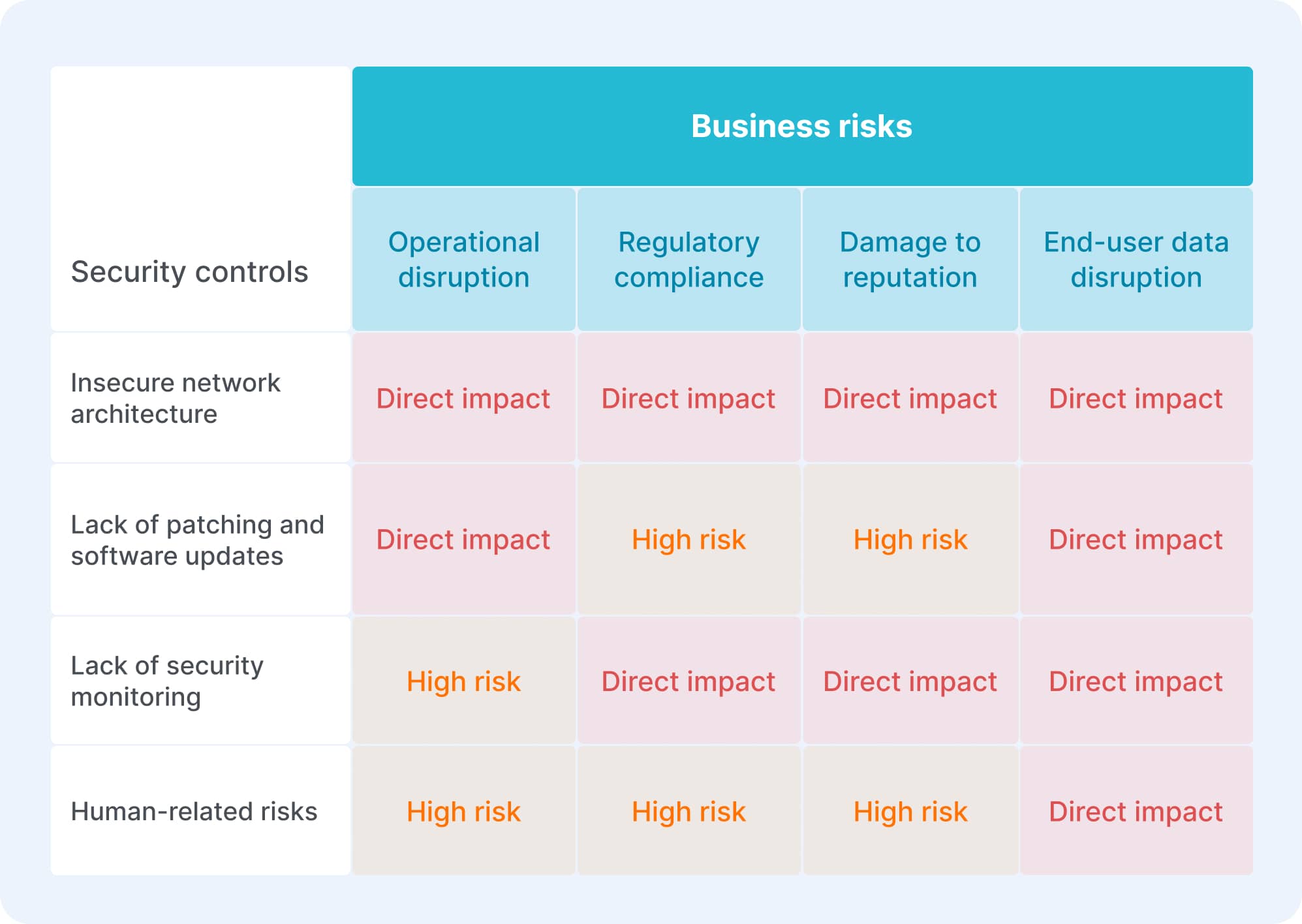
Findings overview
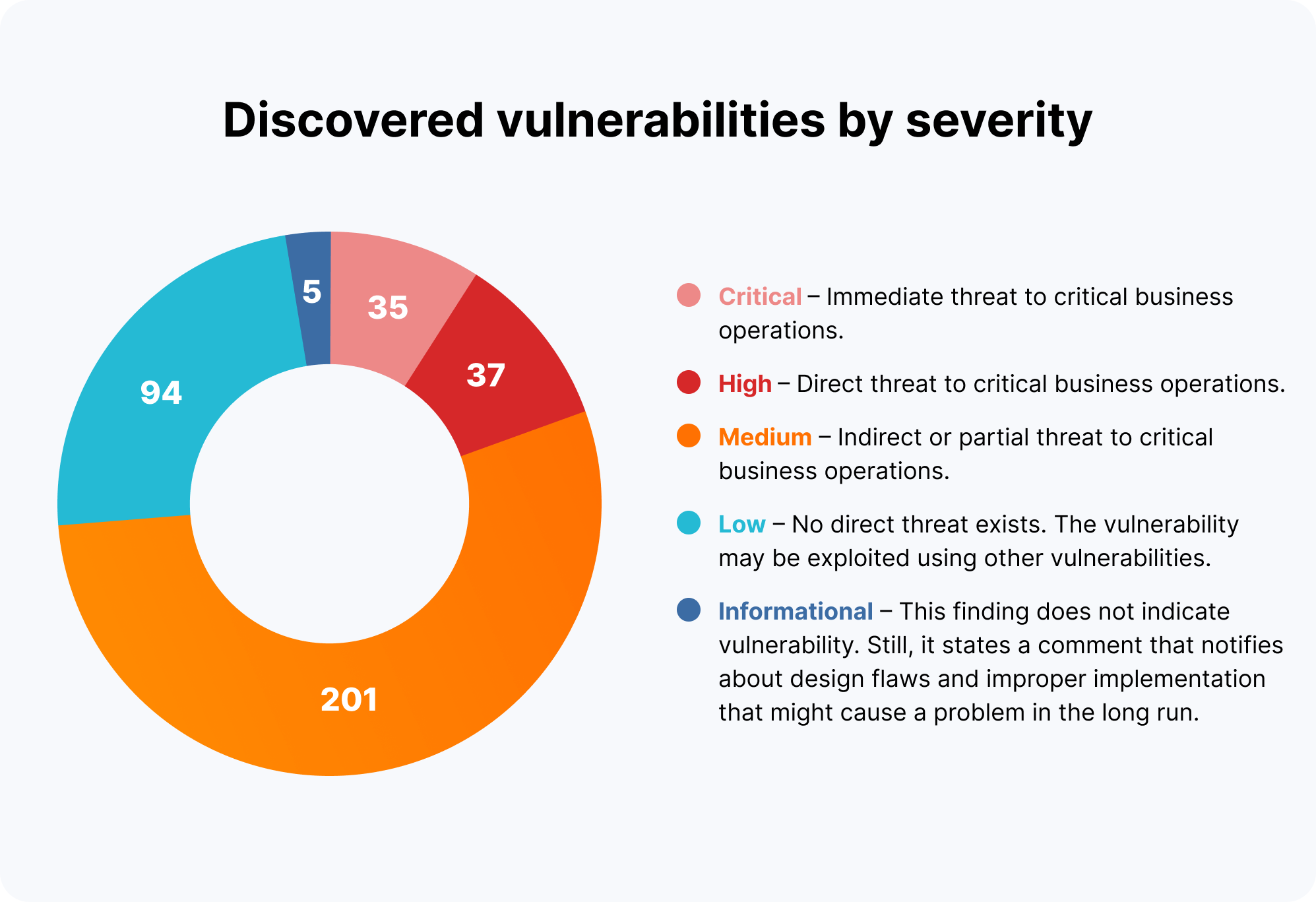
Business risks
Outcomes
Network visibility and control
Effective Incident Response plan
Cost-efficiency
Enhanced cybersecurity measures
- Deployed EDR tools for immediate threat protection on critical endpoints and servers.
- Introduced multi-factor authentication and robust password policies, including complexity requirements, length, expiration, and history.
- Prioritized system patching based on vulnerability findings, with compensating controls for cases where patching is not feasible.
- Subscribed to threat intelligence feeds for early detection of compromised emails/accounts and dark web exposure of critical data.
- Conducted remediation testing of the internal network.
- Initiated biannual penetration tests, including social engineering, to ensure proper security thresholds.
- Established a security awareness program to educate employees and foster a security-conscious culture within the organization.






