CASE STUDY
German Healthcare Leader scales its IT security team with UnderDefense MDR
Key Results
€5,400,000+
saved daily by partnering with UnderDefense
25,000+
covered endpoints and servers
15
Background
The client is Germany’s biggest and oldest healthcare organization, with 100+ different centers, institutes, and departments. They offer a wide range of healthcare services with state-of-the-art equipment and highly-qualified personnel. The institution is regularly listed among the best hospitals locally and globally.
The Challenge
Cyberattacks on healthcare organizations increase at an alarming rate. Hospitals and other health institutions globally experienced on average 1,400+ cyberattacks PER WEEK in 2022. The statistics demonstrated a 74% growth compared with 2021, according to Check Point Research. But most importantly, cyberattacks led to not only financial or reputational losses but patient deaths (attacks on University Hospital Düsseldorf in Germany and Springhill Medical Center in Alabama, USA).
Our client knew that and had an in-house security team with over 100 IT engineers. Unfortunately, it wasn’t enough as they were fighting a losing battle against:
- The resistless barrage of continuous infections, viruses, and malware that employees and patients brought by sending emails, installing apps, and taking reckless actions
- Cybersecurity staff frustration and burnout. The internal IT team was overwhelmed by alerts, attacks, incidents, and essential security events. Plus, the hospital fell victim to several hacks including the Emotet Attack and the burden of containment, remediation, and post-incident activities lied heavy on the in-house team
- Global cybersecurity talent shortage and limited budget that made additional hiring impossible
- The deployed Endpoint Detection and Response solution didn’t operate at full throttle. Since the tool wasn’t fine-tuned properly, it didn’t reduce alert fatigue and didn’t perform functions the client paid for.
Consequently, various types of malware could easily sneak into the client’s infrastructure and block all business functions. As it actually happened now and before.
Malware Types Threatening the Security of the Client’s Healthcare Business | |
Ransomware | Fileless malware |
Virus | Emotet and other trojans |
Stealers | Unwanted programs |
All that only aggravated the situation for the in-house specialists.
Meanwhile, the client had too much at stake. Business security directly impacted the timeliness and quality of provided healthcare services. Additionally, the private information of many Europeans, including their medical recorders, was at risk of becoming public. All that could lead to violating medical confidentiality and heavy penalties under GDPR, the Convention on Human Rights and Biomedicine, and others. Not to mention the potential serious harm to the client’s reputation.
Client Introduction
Industry
Covered Endpoints
“The UnderDefense team is doing great! The type of engagement that we are getting is the type of conversation that we’ve been hoping for since we first envisioned SOCaaS. Friendly conversations mixed with in-depth details, clarifications, and recommendations have been truly great for me to witness. Please tell the team to continue…but my current “net promoter” score is an 11 on a 10 scale!”
Hans, IT Director
Challenges
- Limited visibility on 25,000 endpoints and weak cybersecurity posture
Results
- Complete visibility on 25,000 endpoints and across the entire network
- Ability to identify and act quickly on important alerts
- Prevalent alert fatigue demoralizing the entire security system and burning out expensive internal IT security employees
- Over 30,000 alerts reviewed and resolved to reduce alert fatigue and optimize the workload
- Heavy reliance on out-of-the-box configurations of security tools
- Professional fine-tuning of endpoint detection and response solution to maximize its value for the business
- IT security team working 8-5 overwhelmed by alerts, viruses, malware, and ransomware attacks. Employees requested many changes, permissions, and whitelisting
- 24/7 coverage delivered by talented cybersecurity engineers with constant access to unique domain expertise. All automated or with delightful customer experience
- Increasing cyberattacks targeted at healthcare institutions
- Comprehensive protection and response to all malicious security threats, including malware, ransomware, and viruses
Challenges & Results
Challenge
- Limited visibility on 25,000 endpoints and weak cybersecurity posture
Result
- Complete visibility on 25,000 endpoints and across the entire network
- Ability to identify and act quickly on important alerts
Challenge
- Prevalent alert fatigue demoralizing the entire security system and burning out expensive internal IT security employees
Result
- Over 30,000 alerts reviewed and resolved to reduce alert fatigue and optimize the workload
Challenge
- Heavy reliance on out-of-the-box configurations of security tools
Result
- Professional fine-tuning of endpoint detection and response solution to maximize its value for the business
Challenge
- IT security team working 8-5 overwhelmed by alerts, viruses, malware, and ransomware attacks. Employees requested many changes, permissions, and whitelisting
Result
- 24/7 coverage delivered by talented cybersecurity engineers with constant access to unique domain expertise. All automated or with delightful customer experience
Challenge
- Increasing cyberattacks targeted at healthcare institutions
Result
- Comprehensive protection and response to all malicious security threats, including malware, ransomware, and viruses
It can take one email for your company to come from “Woohoo!” to “D’oh!”
Don’t postpone your business security, request a quote today
The Solution
The company realized they couldn’t hire more employees in-house. So, they started looking for a reliable and professional cybersecurity partner to lessen the burden on the in-house employees and guarantee that no incident would go unnoticed. They needed solid cybersecurity experience and hands-on best practices to get maximum of their current and future security investments.
The client discovered UnderDefense, which provided not only relevant expertise but also a 24/7 security operation center (SOC) and a full team of elite cybersecurity engineers.
Since UnderDefense had a mature expert team and a well-established MDR service, we got to work nearly immediately, saving the client months of recruiting, interviewing, and onboarding. But most importantly, a quick collaboration kickoff prevented 15 severe incidents in the client’s infrastructure.
To ensure comprehensive endpoint protection and deal with alert fatigue, we fine-tuned EnSilo (now Fortinet) across all Windows and MacOS systems within the hospital. Finally, the platform introduced automated incident detection, response, and prevention against modern malware and cyberattacks. Meanwhile, we also started monitoring and fighting malware on over 20,000 endpoints.
Maintaining compliance with strict European regulations and standards was another pressing issue for the company’s IT Director and a high-priority task for the UnderDefense team. So, to improve data safety, we provided 8/5 or 24/7 security monitoring team Tier 1-3 with 20 minutes SLA for critical alerts with notification, reporting, and IR guidance.
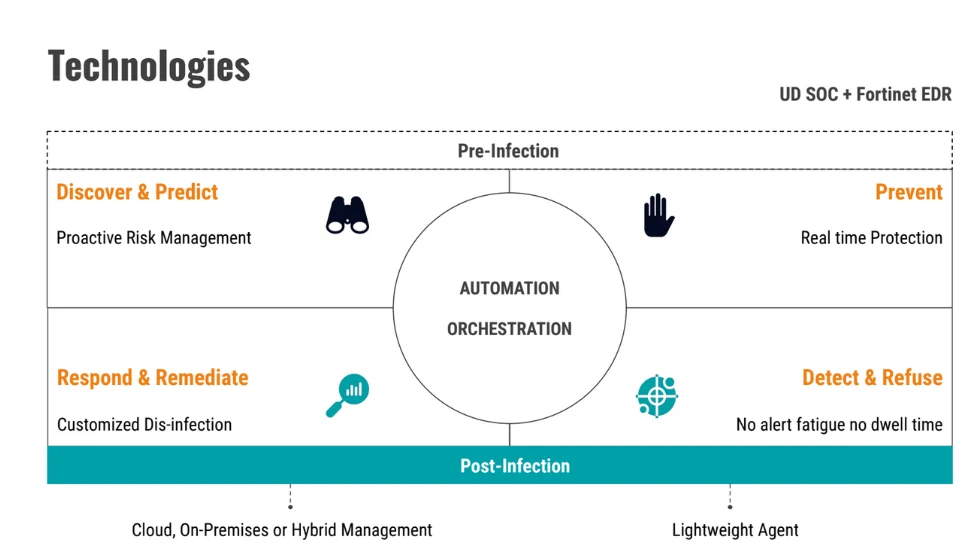
During the first year of cooperation, the UnderDefense team analyzed 31.07 TB of data logs and 7.05 billion processes executed on 19,842 endpoints. We also did the following:
- Reviewed 55,160 potentially threatening events
- Eliminated 37,508 false positive alerts
- Provided feedback on 7,722 events that were marked as allowed
- Notified the client about 73 confirmed attacks
- Confirmed 27 attacks (APT) that were remediated by our team
- Used the IR plan to respond to 3 threats
- Held 54 active communication sessions between the client’s in-house and our SOC teams
- Conducted 89 calls with the client’s IT specialists
- Fielded 19 direct calls to the 24/7 SOC hotline
- Helped to increase CIS maturity level by 10 points
UnderDefense MDR service also included:
Incident management and reporting | Development and adaptation | Operations | Regulatory compliance |
 Security logs monitoring methodology  Real-time incident handling  Trend analysis |  Changes in log sources and formats  Changes in search criteria  Creation of reports and dashboards  Creation and change of alarm structures |  NOC/SOC delivery  Service monitoring  SLA  SIEM management |  Compliance reports  Deviation reports |
Incident management and reporting
Security logs monitoring
Real-time incident handling
Trend analysis
Development and adaptation
Changes in log sources and formats
Changes in search criteria
Creation and change of alarm structures
Operations
NOC/SOC delivery
Service monitoring
SLA
SIEM management
Regulatory compliance
Compliance reports
Deviation reports

Outcomes
The collaboration with UnderDefense allowed the client to free up an expensive in-house security team and focus them on more strategic cybersecurity tasks unique to their industry and business. Internal engineers no longer need to spend time on the front-line monitoring alerts. Moreover, they don’t get thousands of alerts with no context anymore. UnderDefense sends in-depth reports with instructions instead.
Plus, we helped the IT Director to successfully address security gaps and blind spots within the large hospital infrastructure, resulting in the following:
“We feel much more secure knowing that there is someone 24/7 watching our backs.”
Hans, IT Director
Better protection of sensitive assets and data
Fine-tuning of the endpoint detection and response solution, along with SOC provided by UnderDefense, added the missing security layer to the hospital’s perimeter protection. Now the data of European patients are safe, and the client has eliminated the risk of becoming non-compliant.
Professional configuration and orchestration of the entire security flow allowed the client to lower the number of false positives, reduce alert fatigue, and lessen the burden on the internal staff. The UnderDefense team not only notifies about important security incidents but also provides detailed remediation guidance.
Seeing and understanding what’s actually happening in the environment is crucial for any business. Visibility is the key that gives c-level peace of mind and confidence to make important decisions. Working with UnderDefense, the client certainly has that. Additionally, our team provides threat investigation, advanced analytics, and custom monthly reports.
The Story of One Incident: Emotet Attack
Emotet is one of the most expensive and destructive malware. The price tag may exceed $1 million per incident to clean up. Meanwhile, it targets individuals, companies, and government entities using malicious spam to infect an end-user and get a foothold on the network. Once there, it moves from system to system using a list of common passwords.
Emotet was initially designed as a banking Trojan to sneak into a computer and steal sensitive and private information. Later, its functionality was extended with spamming and malware delivery services.
That’s what happened to the client’s organization. Fortunately, UnderDefense was there to augment the internal IT security team and strike back.
UnderDefense vs Emotet Attack: The Timeline
- Devices moved to the “suspicious” group
- Files remediated
- Activity reports created and shared
- Events handled
- The OS on the hosts reinstalled by the client and moved to the “default’” group
- Post-incident activities





