Ransomware Attacks Double: Prepare Your Organization for 2024’s Threats in 6 Steps

by UnderDefense
Max 10min read
Recovering from a ransomware attack is a complex and time-consuming process that goes far beyond simply decrypting and restoring data. It requires rebuilding entire systems, addressing operational downtime, and has a significant impact on customers.
Table of Contents
- The state of ransomware: attacks double
- Why current security measures don’t work: The urgent need for better detection capabilities
- 6 things to do now to guard your business against ransomware attacks
- Security awareness training for all employees
- Multi-factor authentication
- Tested and validated IR and recovery plan
- Better use of threat intelligence platforms
- 24/7 monitoring and security tool consolidation
- Automated, continuous external risk assessment
- Make your business ransomware-proof in 2024 and beyond
The state of ransomware: attacks double
The situation with ransomware attacks is becoming increasingly concerning. The CyberEdge’s annual Cyberthreat Defense Report has found that in 2023, ransomware attacks affected more than 72% of businesses worldwide, continuing a five-year upward trend. This figure represents the highest reported percentage to date.

As stated in Zscaler ThreatLabz 2023 Ransomware Report, ransomware attacks surged by more than 37%. With the significant progress in AI, there is no sign of these attacks slowing down in 2024. So, it’s crucial for businesses to stay vigilant.
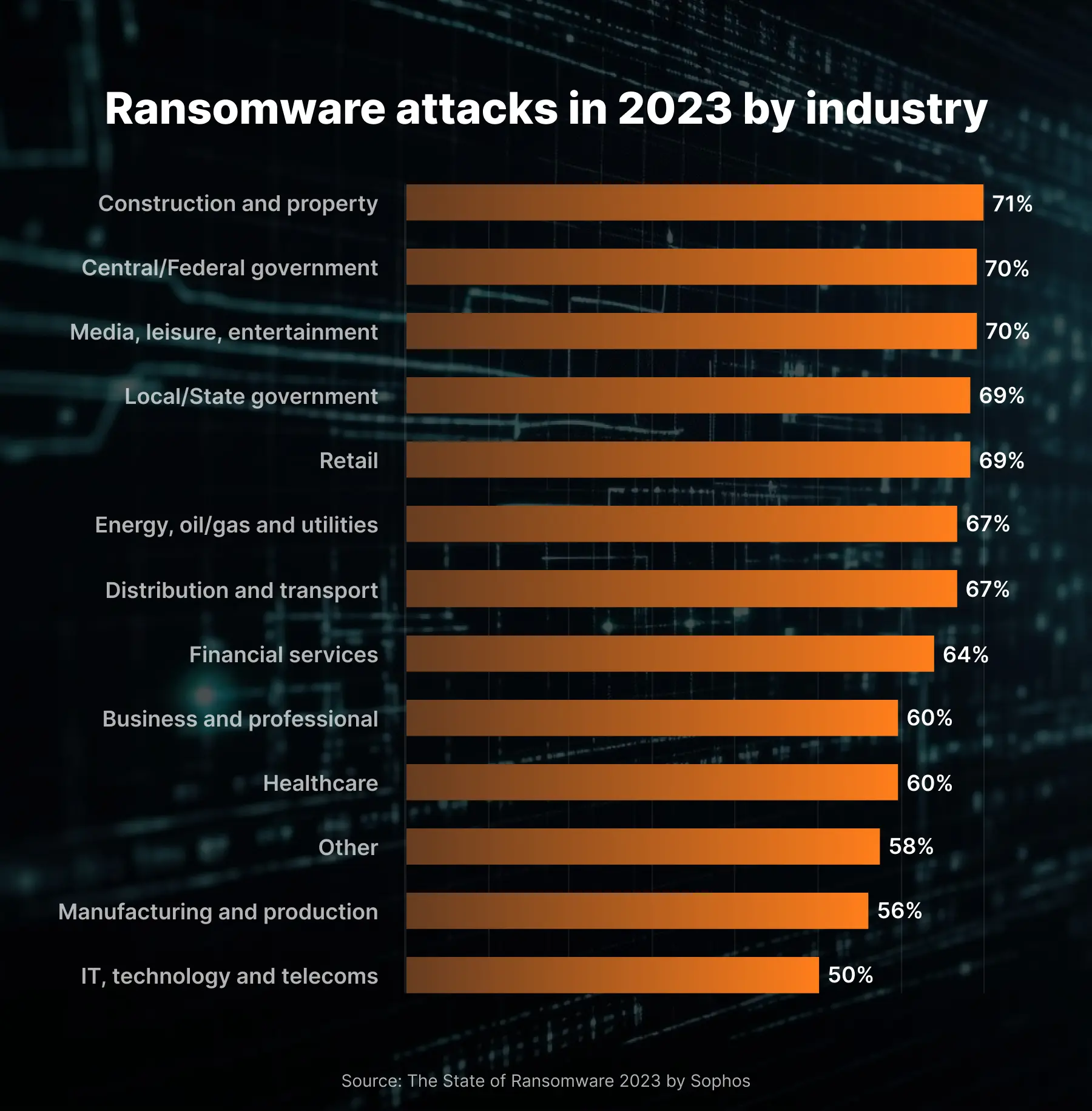
Who was the target for ransomware in 2023
Unfortunately, considering the dynamics, any business is vulnerable to ransomware. So, it’s not a matter of if but when your organization will experience an attack. As anticipated, the business sector took the most hits in 2023, with construction, government, and media sectors topping the list.
The most popular ransomware techniques in 2023
First, let’s clarify that before demanding ransom, attackers must infiltrate the victims’ systems and infect them with malicious software. So, the most common ransomware attack vectors are:
- Phishing
- Remote Desktop Protocol (RDP) and credential abuse
- Exploitable software vulnerabilities
- Malvertising
- Drive-by downloads
- Social engineering
- Social media, and messaging apps
One of the widespread ransomware techniques is using double extortion, where attackers threaten to not only encrypt the victim’s data but also leak it online if the victim does not pay the ransom. Another one is targeting supply chain vulnerabilities where attackers target a vendor or supplier of a larger organization to gain access to the larger organization’s network.

The increasing number of ransomware attacks, driven by the profitability of these crimes, underscores the urgency of taking action to avoid significant financial, operational, and legal damages.
Why current security measures don’t work: The urgent need for better detection capabilities
You may be wondering why all that breaches and attacks still happen, while there are so many technologies and tools available on the market. Well, the truth needs to be told. Many companies have in-house SOCs, various security solutions installed, etc. So, what’s the problem here?
How SOC teams work now
Most Security Operations Centers typically rely on endpoint security solutions that primarily focus on detecting known Indicators of Compromise (IOCs). The IOCs are artifacts or patterns derived from previously documented cyberattacks. However, this approach has limitations, as it primarily detects attacks that have been seen before and documented.

What SOC teams are missing

That’s why more SOC teams recognize the need to go beyond the traditional model. They are adopting detection capabilities that leverage Indicators of Behavior (IOBs) to detect more subtle signs of an attack. IOBs encompass the chains of behaviors exhibited by human and machine entities, allowing for the identification of malicious activities that may not have been previously documented. By doing so, modern SOCs can detect attacks at their earliest stages before they escalate into major breach events. Adopting managed SOC services or even more comprehensive MDR services can further enhance your organization’s cybersecurity defenses.
6 things to do now to guard your business against ransomware attacks
1. Security awareness training for all employees

Security awareness training is vital to protect your business from ransomware. It educates employees about various cyber threats, like phishing and suspicious downloads, enabling them to identify and respond to potential threats effectively. Fostering a culture of cybersecurity awareness adds an extra layer of defense and significantly reduces the risk of ransomware. Last but not least, security awareness training must be conducted regularly.
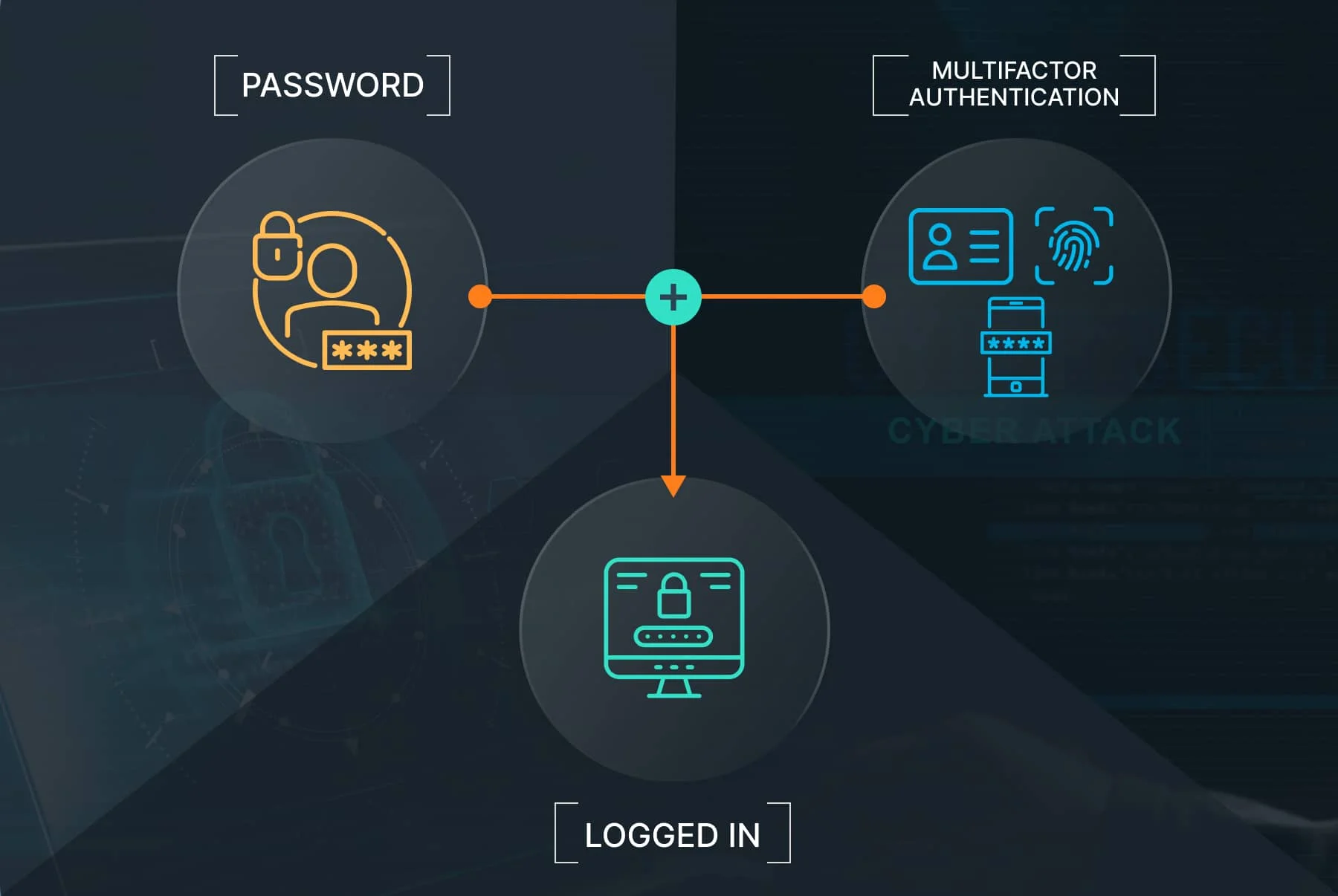
2. Multi-factor authentication
3. Tested and validated IR and recovery plan
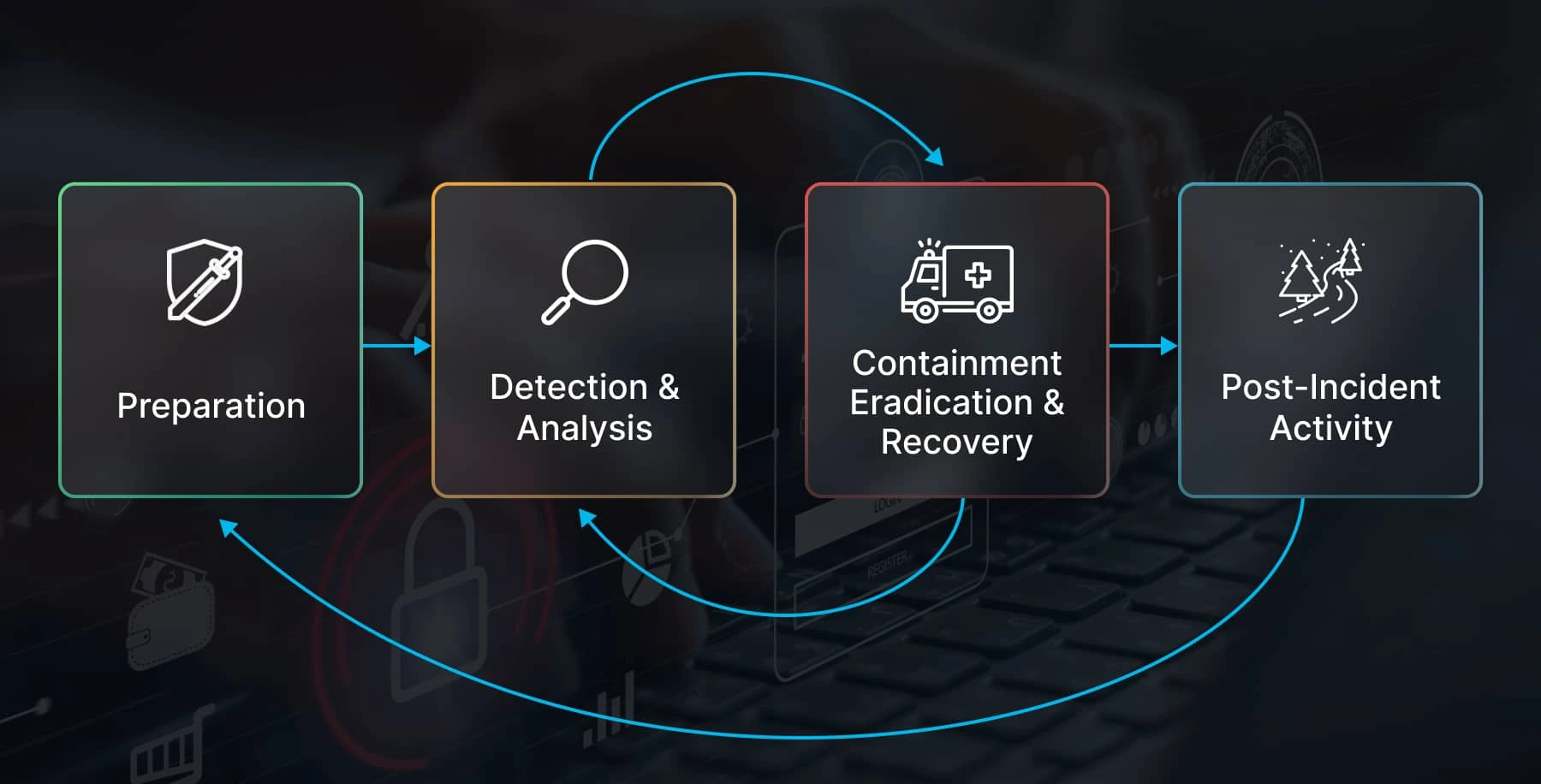
A tested and validated IR and recovery plan should cover the following areas:
- Incident detection: How your organization will detect a cybersecurity incident.
- Incident response: Actual steps to contain, investigate, and eradicate a cybersecurity incident.
- Recovery: What your staff should do to restore systems and data after a cybersecurity incident.
However, keep in mind that creating an incident response (IR) and recovery plan is only half the battle. It’s equally important to test and validate it to identify weaknesses, provide training opportunities, and allow for necessary adjustments. Regular testing, at least annually, keeps the plan up-to-date and ensures your team is ready to act. Explore professional incident response services to enhance the effectiveness of your cybersecurity strategy. Consider incorporating penetration testing or ethical hacking services into your strategy for thorough evaluation and continuous improvement.
4. Better use of threat intelligence platforms

Threat intelligence platforms (TIPs) like UnderDefense MAXI security-as-a-service platform are a valuable tool for businesses to improve their security posture. TIPs collect, analyze, and correlate data from various sources, providing companies with a comprehensive view of the threat landscape. But we don’t stop here, and with UnderDefense MAXI you gain additional benefits. In the event of a ransomware attack, the platform provides threat containment automation to prevent ransomware from spreading. Plus, you receive in-depth insights into the ransomware type and all the actionable context to make informed decisions quickly.

One of the best ways to use a TIP is to automate security processes like alert triage and threat hunting. UnderDefense MAXI also allows you to automate notifications in case of suspicious activities and receive them via Slack, MS Teams, and other solutions. By doing so, you can free up your in-house security teams and let them focus on more complex tasks, such as investigating and responding to high-priority threats.

5. 24/7 monitoring and security tool consolidation
Cyber threats do not adhere to a strict schedule. They can occur at any time, day or night. And who does protect your organization from 5 pm to 8 am? The need for continuous monitoring is undeniable, as it is one of a few ways to give cybercriminals less time to exploit vulnerabilities.
As a part of continuous monitoring, effective log management involves collecting, storing, and analyzing logs from various sources, such as servers, applications, and security devices.
Considering the evolving threat landscape, organizations rush to buy and integrate various security tools to protect their digital assets. These tools include Security Information and Event Management (SIEM) systems, Endpoint Detection and Response (EDR) solutions, firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS). But all those disconnected tools don’t provide a unified, real-time view of corporate defenses, and security experts need to switch between dozens of consoles and correlate all the alerts manually. Such an approach is time-consuming and depressing. For a more streamlined and efficient solution, consider a managed SIEM service that offers comprehensive and unified security management.
Consolidating these tools along with 24/7 monitoring and log management within one platform like UnderDefense MAXI offers several advantages:
- Continuous security monitoring
- Enhanced threat detection and response
- A comprehensive security view to spot suspicious activity in real-time
- Lower risk of cyberattacks
- Reduced costs associated with security incidents
6. Automated, continuous external risk assessment
External risk assessment involves monitoring all digital assets exposed online to detect potential threats to an organization’s digital security instantly. What does that mean? For example, UnderDefense MAXI automatically analyzes your dark web appearance, non-compliant passwords, compromised user identities, and more. Additionally, the platform calculates your financial risks and potential loss caused by ransomware or other threats. This information allows organizations to do the following:
- Dark web monitoring helps proactively detect if a company’s sensitive data or employee credentials are being traded or discussed on hacker forums.
- Compromised user identity analysis shows if employees’ login credentials have been compromised and are at risk of being misused.
- Leaked credentials monitoring helps quickly determine if their employees’ credentials are available online.
Admittedly, external risk analysis can be performed manually. In this case, analysts search for information about the organization on the dark web and other public sources. However, such an approach is costly and too often it offers limited results.
Make your business ransomware-proof in 2024 and beyond
Ransomware remains a pervasive threat, and organizations worldwide increasingly invest in robust business ransomware protection measures to safeguard their critical data and operations. Cyber adversaries are continually evolving, and the rise of ransomware-as-a-service means attacks won’t decrease anytime soon. While the tips provided here are essential, remember that comprehensive protection goes beyond the basics.
By adopting proactive measures, promoting continuous education, and establishing a resilient security framework, you can step into 2024 well-equipped with awareness and caution and stay ransomware-resistant.
If you have any questions or concerns about your business ransomware protection, UnderDefense is here to be your trusted ally in protecting your digital assets. Don’t wait for an attack to strike. Contact us today to proactively secure your future.
More from UnderDefense:
Questions about cyber security?
Read more
Read more about Managed Detection and Response Service (MDR)

Download MDR Datasheet

Read more about our Incident Response Service

Discover all features of our UnderDefense Security-as-a-service MAXI platform